Faster Audits, Stronger Compliance Case Study
Discover how Cloudaware helped to automate AWS compliance, achieve 94% best-practice alignment, and reduce audits by 60%
This case study demonstrates how a global cybersecurity provider managing 188 AWS accounts and 7.12M assets, leveraged Cloudaware Compliance Engine to achieve 94% compliance with AWS security best practices, align with ISO 27001, NIST 800-53, and GDPR standards, and reduce audit preparation time by 60%.
About The Customer
Company S is a leading global cybersecurity provider headquartered in Texas, USA, with several offices in Europe. Originally founded in the 1990s as an IT reseller, the Company now offers a comprehensive suite of security solutions, including data loss prevention, cloud access security broker (CASB), firewall technologies, AI-driven data classification, insider threat prevention, and data detection and response (DDR). The Company S serves more than 12,000 customers worldwide, including governments and enterprises in over 150 countries.
AWS Footprint:
- 188 AWS accounts
- 7,276 Amazon EC2 instances
- 2,100 Amazon S3 buckets
- 480 Amazon RDS instances
- 900 IAM roles and policies
- 120 Amazon VPCs with cross-region connectivity
Infrastructure Assets: 7.12M
Asset Types: 798
Problem Statement
The Company S operates a large-scale AWS deployment with over 180 AWS accounts and more than 7,000,000 configurable assets.
As a global cybersecurity provider, the Company S manages sensitive customer data and mission-critical services across AWS environments. While its core focus is on delivering security solutions, maintaining internal compliance in AWS is equally critical. The Company S must ensure that its cloud infrastructure aligns with strict regulatory frameworks (such as ISO 27001, NIST 800-53, and GDPR) and customer contractual requirements. Due to the scale and dynamic nature of its cloud infrastructure, ensuring regulatory compliance and internal governance was increasingly challenging.
Manual auditing of resource configurations, inconsistent tagging, and delayed detection of non-compliant assets created potential risks for data breaches, regulatory violations, and operational inefficiencies. Up to 45% of AWS resources were not consistently tagged, which increased the risk of mismanagement and complicated audit processes. With thousands of resources deployed globally, challenges such as enforcing consistent tagging policies, monitoring security controls, and automating remediation across accounts become complex.
The main challenges were:
- Complete visibility into AWS inventory across multiple accounts and regions
- Compliance with regulatory standards for AWS environment
- Maintaining internal tagging standards and tag consistency
- Automation and streamlining of remediation activities
Solution
To address these challenges, the Company S leveraged the Cloudaware Compliance Engine and CMDB.
Cloudaware integrates with AWS Organizations for account discovery and management, using CloudFormation templates for seamless permission and resource setup. These templates include the permissions required to automatically discover and collect customer data from key AWS security and monitoring services, including:
- AWS Security Hub: securityhub:Des*, securityhub:G*, securityhub:L*
- Amazon GuardDuty: guardduty:Des*, guardduty:G*, guardduty:L*
AWS Config: config:Describe*, config:List* - AWS CloudTrail:, cloudtrail:DescribeTrails, cloudtrail:GetTrailStatus, cloudtrail:LookupEvents
AWS IAM: iam:Get*, iam:L*, iam:GenerateCredentialReport
These permissions enable Cloudaware to automatically collect AWS asset data into the CMDB, providing a unified, up-to-date view of resources. The Compliance Engine uses the CMDB as a central hub, reducing AWS API calls.
By combining the Compliance Engine with BI analytics and automation tools, the Company S gained a 360-degree compliance management solution.
Architecture
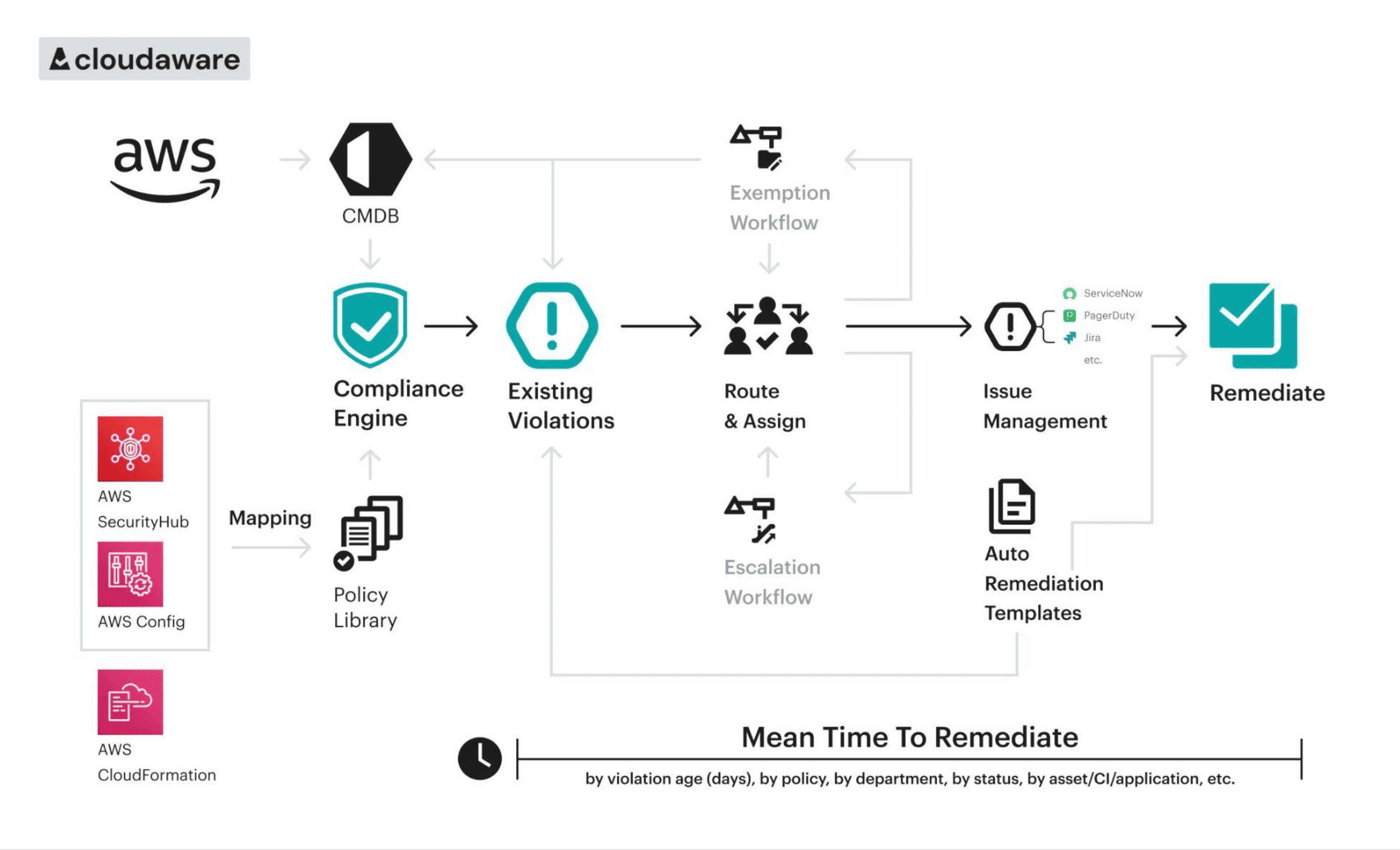
Compliance Engine
The Cloudaware Compliance Engine integrates AWS security frameworks such as AWS Foundational Security Best Practices (FSBP) and CIS Benchmarks, enabling continuous assessment of AWS environments. By ingesting data from native AWS services such as AWS Config, Security Hub, and CloudTrail, Cloudaware allows customers to measure compliance against policies aligned with FSBP, CIS, NIST, and ISO.
Policy mappings example:
| NIST SP 800-53 | Cloudaware CE Policies | AWS Security Hub |
|---|---|---|
| NIST CSF v1.1 → PR.AC-7: Users, devices, and other assets are authenticated (e.g., single-factor, multi-factor) commensurate with the risk of the transaction (e.g., individuals' security and privacy risks and other organizational risks | AWS Account Root User MFA is not enabled. AWS Account Root User Hardware MFA is not enabled | IAM.5 MFA should be enabled for all IAM users that have a console password. IAM.6 Hardware MFA should be enabled for the root user |
Policy Library & Editor
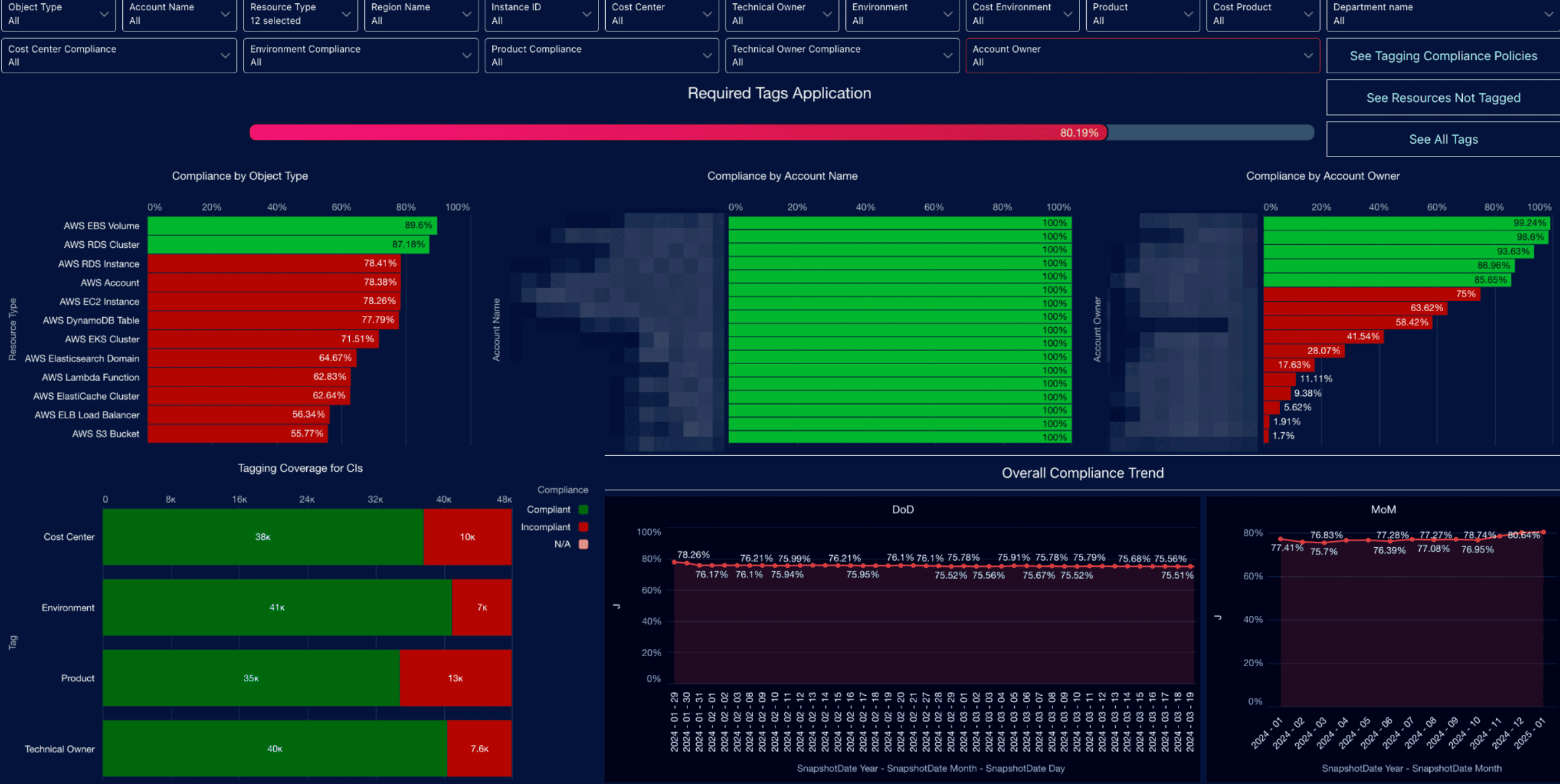
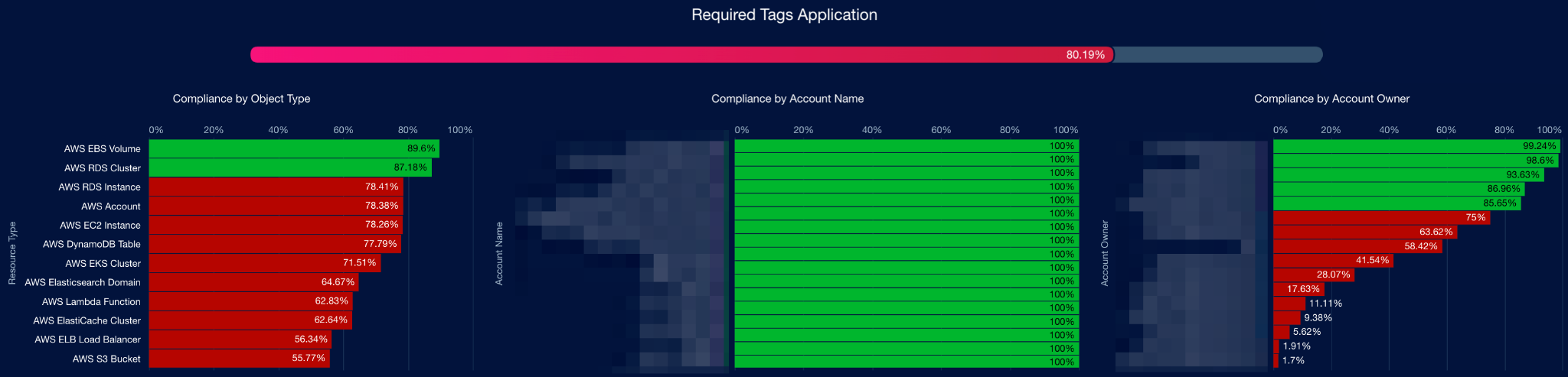
The solution includes the built-in Compliance Engine Policy Library and Editor. Using the Editor, the Company S collaborated with Cloudaware to design and implement custom policies for ensuring tagging compliance. These policies defined mandatory tags – such as Account Owner, Application, Product, etc. – across different resource types, including EC2, S3, RDS, and Lambda.
Cloudaware also delivered a tagging compliance dashboard that enabled the Company S to monitor remediation progress.
Custom tagging policy example (the Application tag):
inputType: "CA10__CaAwsInstance__c"
conditions:
# Checking that the required tag exist
- status: "COMPLIANT"
currentStateMessage: "Required tag is present on the resource."
check:
TAG_EXISTS:
name:
BYTES: "Application"
otherwise:
status: "INCOMPLIANT"
currentStateMessage: "The resource doesn't have the required tag."
remediationMessage: "Ensure that the required tag is present and valid: Application."
Tagging compliance dashboard example:
Workflows
Jira was integrated with the Compliance Engine to automate compliance enforcement. Checks for the most critical policies were configured to automatically create tickets for the responsible teams.
Once a fix was applied, Cloudaware updated the compliance status, closed the Jira ticket, and recorded a timestamped resolution, ensuring full traceability and audit readiness.
Automation
Lambda-based remediation processes were deployed by Cloudaware to automatically apply tags defined by the Forcepoint's tagging compliance standards, while escalation workflows ensured unresolved issues were addressed promptly by the responsible teams.
Analytics
Cloudaware provided a Unified Compliance Framework dashboard based on a set of common controls for internal and external audits.
The Cloudaware Compliance Engine leverages a one-to-many mapping methodology connecting each common control to multiple compliance frameworks. By selecting a specific control ID, audit teams could navigate the overlaps between compliance and security frameworks, distill and interpret relevant controls, and harmonize regulatory requirements for the organization. As a result, the Company S was able to measure adherence to internally approved regulatory guidelines.
Unified compliance dashboard example (NIST 800-53 Rev4 is selected in filters):
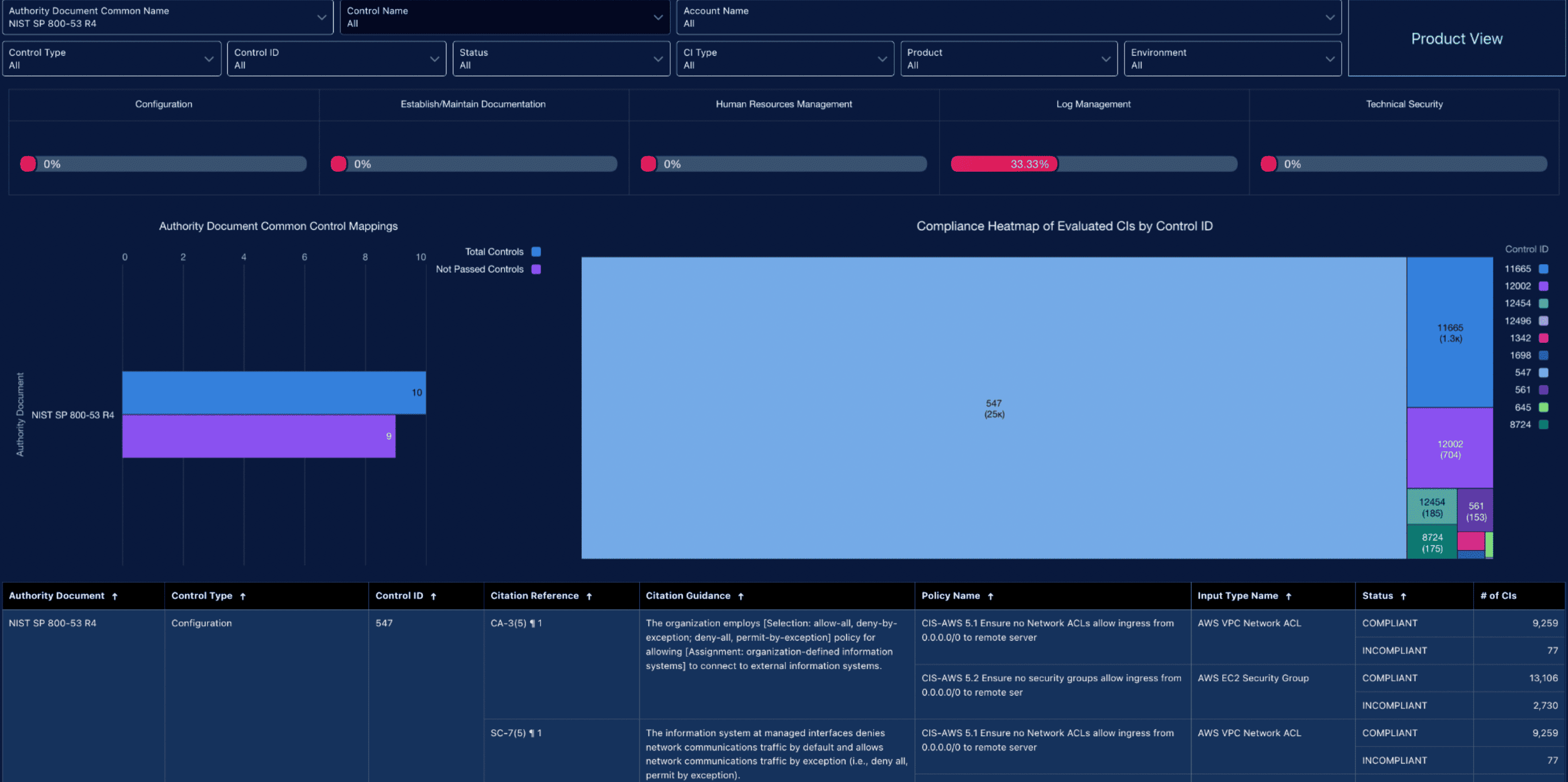
Implementation
Week 1: CMDB setup – the Company S imported AWS inventory into Cloudaware CMDB.
Week 2-3: The solution deployment – Cloudaware enabled the Compliance Engine, which contains over 500 pre-built compliance policies, including CIS. The unified Cloudaware compliance framework, which cross-references ISO 27001, SOC 2, NIST, and other standards, was also introduced.
Week 4-5: Exception tuning – the Company S customized rules for specific VPCs, accounts, and services to avoid false positives.
Week 6: Customizations – custom policies for tagging compliance were implemented by Cloudaware, along with a comprehensive dashboard generated for executives and teams.
Week 7-8: Automation activation – Cloudaware enabled automated remediation for recurring misconfigurations.
Results
The Company S increased compliance with AWS Foundational Security Best Practices (FSBP) from 72% to 94%, and with CIS AWS Benchmarks from 70% to 92% across all accounts.
The average compliance percentage across AWS resources improved from 71.95% to 83–87%.
The average compliance percentage across AWS resources tagged with Account Owner improved from 48.63% to 75–80%.
The average compliance percentage across AWS resources tagged with Application improved from 69% to 80%.
Mean Time to Remediate (MTTR) dropped by 67%, from roughly 30 days to 10 days.
Approximately 85% of detected violations are fully remediated within five weeks after the solution implementation.
The number of recurring misconfigurations, e.g., open security groups, public S3 buckets, and unused IAM keys, decreased by 65%.
80% reduction in inactive IAM keys was achieved through compliance monitoring and automatic deactivation workflows.
90% alignment of IAM roles with least-privilege access standards was achieved.
The manual audit efforts were reduced by 60%, as estimated by the Company S.
Privacy Controls
Using Cloudaware’s unified compliance framework, the Company S quickly identified sensitive Amazon S3 and RDS resources, enforced mandated encryption, and automated lifecycle policies across AWS services.
- 98% of sensitive data assets were identified and classified through automated tagging.
- Lifecycle and backup policies were applied to over 95% of resources to ensure alignment with GDPR and internal policies.
- 100% of sensitive datasets secured with multi-region KMS-based encryption.
As a result, the Company S significantly strengthened its privacy and data protection posture.
Regulatory Compliance Outcomes
Using Cloudaware Compliance Engine, the Company S:
- strengthened key controls to improve audit readiness and maintain ISO 27001 certification
- enabled automated continuous monitoring of NIST 800-53 controls enterprise-wide
- achieved and demonstrated over 99.5% GDPR compliance across all EU operations
- reduced audit preparation time by 60% through automated evidence collection and reporting
Testimonial
“With Cloudaware, we streamlined our compliance processes, achieving 94% alignment with AWS best practices and strengthening our security posture. The solution saved our teams hours, allowing them to focus on higher-value initiatives”, – Company S Company S's Chief Information Security Officer.
Conclusion
Cloudaware automated compliance monitoring, enforced tagging policies across the Company Soint's business applications, and integrated real-time alerts for misconfigurations or missing security controls. Using the Cloudaware Compliance Engine, the Company S strengthened its internal security posture, ensured adherence to industry standards, and maintained trust with customers by demonstrating rigorous cloud governance aligned with its own cybersecurity principles.
If your organization is facing similar challenges in securing your public cloud infrastructure, we encourage you to explore how Cloudaware can help. Contact us today to schedule a demo and learn more about our solutions.
