Intrusion detection system across entire OSI stack
Make contextualized assessments to detect security breaches and minimize further damage. Use CMDB data to prioritize suspicious activity.
Read-only permissions required
No credit card needed
Automated and guided setup
30-day free trial
Read-only permissions required
No credit card needed
Meet the best intrusion detection system
Use the CMDB context to prioritize and analyze malicious activity in real time
Create custom detection rules in a simple editor that pulls CMDB fields and log attributes
Use curated rule packs for containers and clouds to auto-flag threats. Refine incident routing with CMDB tags
Meet PCI, HIPAA, and SOC 2 security controls with file integrity and log inspection. Export audit-ready reports
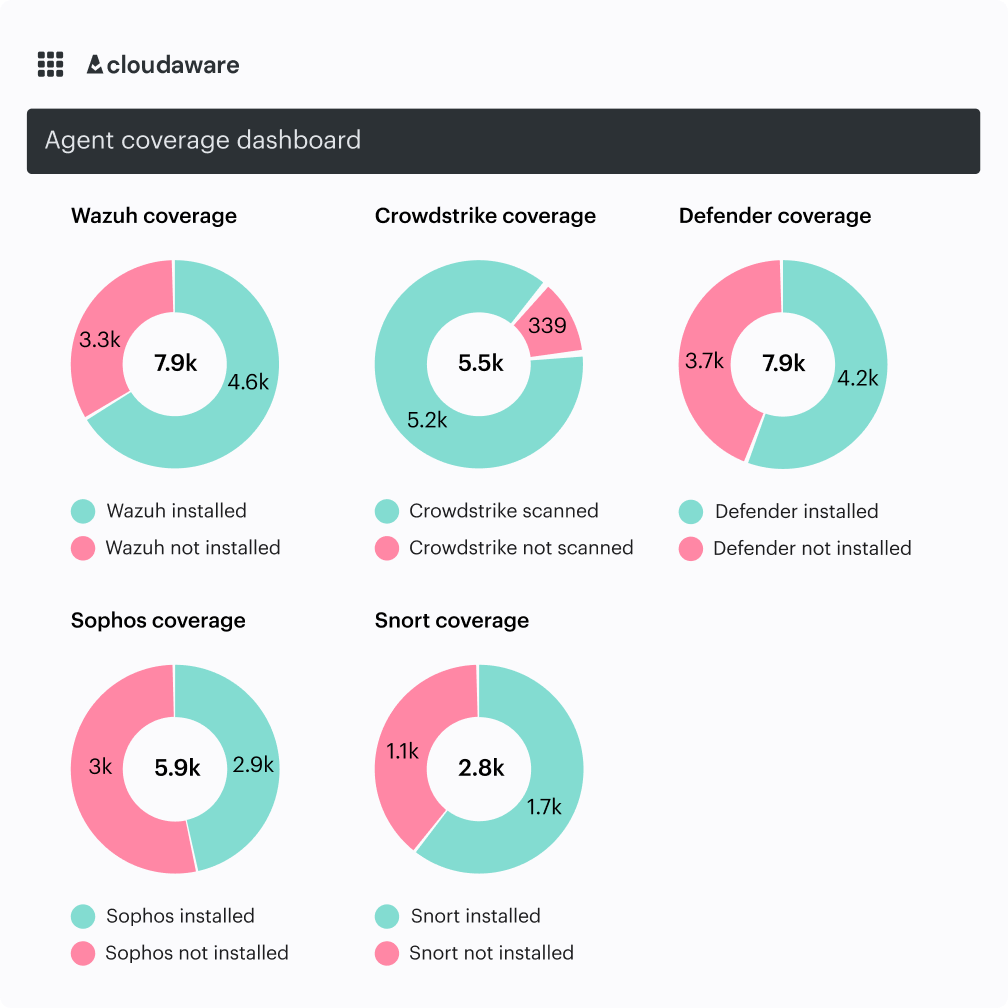
Verify 100% coverage. Know what’s monitored and what isn’t
With CMDB at the core, Cloudaware’s IDS automatically matches your actual inventory. Ready-made integrations enable monitoring across AWS, Azure, GCP, Oracle, Alibaba, and Kubernetes. The Breeze system quickly deploys IDS at scale for on-premises environments. Status updates automatically as assets spin up or retire. Guided automations close the gaps.
Prioritize high-signal alerts ranked by business impact
Correlate host, cloud, and network signals using Cloudaware’s IDS. Enrich the signals with CMDB context and rank them by risk to prioritize real threats. Policy-matched rules open incidents only when necessary. As a result, your IDS pipeline will run with fewer false positives and faster decision-making.
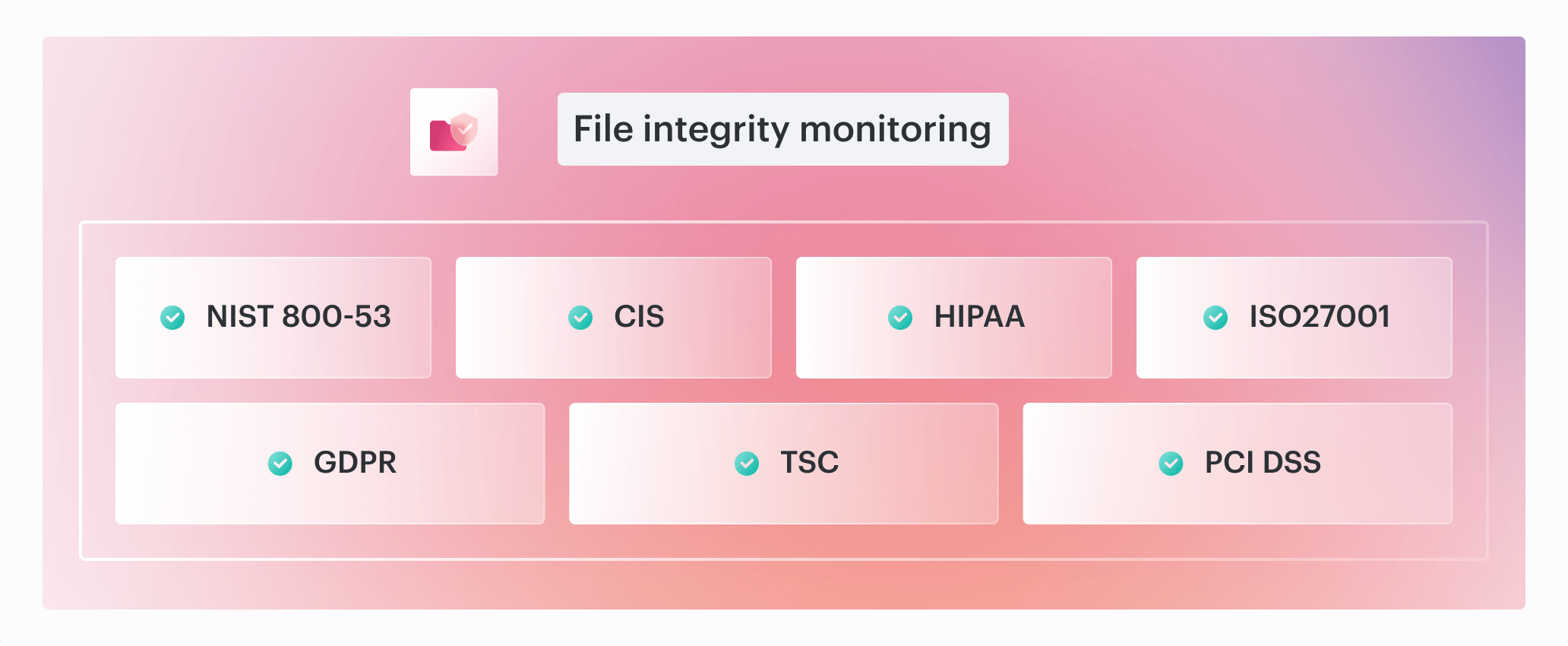
Demonstrate accountability with file integrity monitoring
Meet regulatory requirements with evidence on demand
Turn alerts into assignments
Neutralize threats on autopilot
Strengthen security posture with intrusion detection software
Stop threats sooner, limit the blast radius, and demonstrate the presence of controls. Prioritize alerts by risk using context from the CMDB. Automate containment with policy-driven workflows.
$15.7B
in managed spending across 5 cloud providers
99.995%
historical uptime for Cloudaware CMDB
63
CMDB integrations with industry leading tools
3,000+
supported cloud services and CI types
Get all the intrusion detection tools you need in one platform
Each patch is tied back to a CI, so you always know who owns the risk. The patch management tool provides the full context of ownership, role, and criticality. All in one place.
A host-based intrusion detection system (HIDS) monitors OS and app files. It scores read and write operations by identity and flags malware, rootkits, and unauthorized installations.
Cloudaware's host intrusion detection system creates and closes alerts directly in Jira, ServiceNow, Slack, PagerDuty, or email.
Create custom dashboards and audit-ready reports by owner, application, or environment. Export or share the view.
Monitor hosts and containers in a single view with native Docker Engine integration. It flags privileged mode, in-container shells, vulnerable apps, and volume changes.
Cloudaware’s intrusion detection solution supports PCI and HIPAA compliance through file integrity monitoring, log inspection, and policy enforcement. It provides auditable trails and covers PCI DSS controls 11.5 and 10.x.
Deploy IDS quickly and consistently across all operating systems with one repeatable template. Maintain uniform coverage across clouds, regions, and on-premises.
Bring network traffic inspection into the picture. With Snort integration, you get signature, protocol, and anomaly inspection with packet analysis.
Intrusion detection system FAQs
What is the intrusion detection system?
What is the difference between IDS and firewall?
How does IDS reduce false positives and prioritize real threats?
What problems should an intrusion detection solution solve?
What’s the difference between a network IDS and a host based intrusion detection system?
How fast can we roll out coverage across AWS, Azure, GCP, Oracle, and on-premises?
How does IDS handle ephemeral infrastructure, such as autoscaling?
Updated Sep 2025







