Enrich your SIEM system with CMDB data context
Automatically discover and organize log sources from your cloud and on-prem environments with SIEM software. Prioritize SIEM events using business context and asset criticality.
Read-only permissions required
No credit card needed
Automated and guided setup
30-day free trial
Read-only permissions required
No credit card needed
Automate threat detection using the best SIEM
Aggregate logs from AWS, Azure, GCP, Oracle, Alibaba, hosts, networks, and identity services into one place
CMDB-enriched events tagged with owner, environment, and app metadata. Accelerate investigation and response
Anomaly detection reveals the riskiest patterns. This allows teams to stop chasing noise and focus on what matters
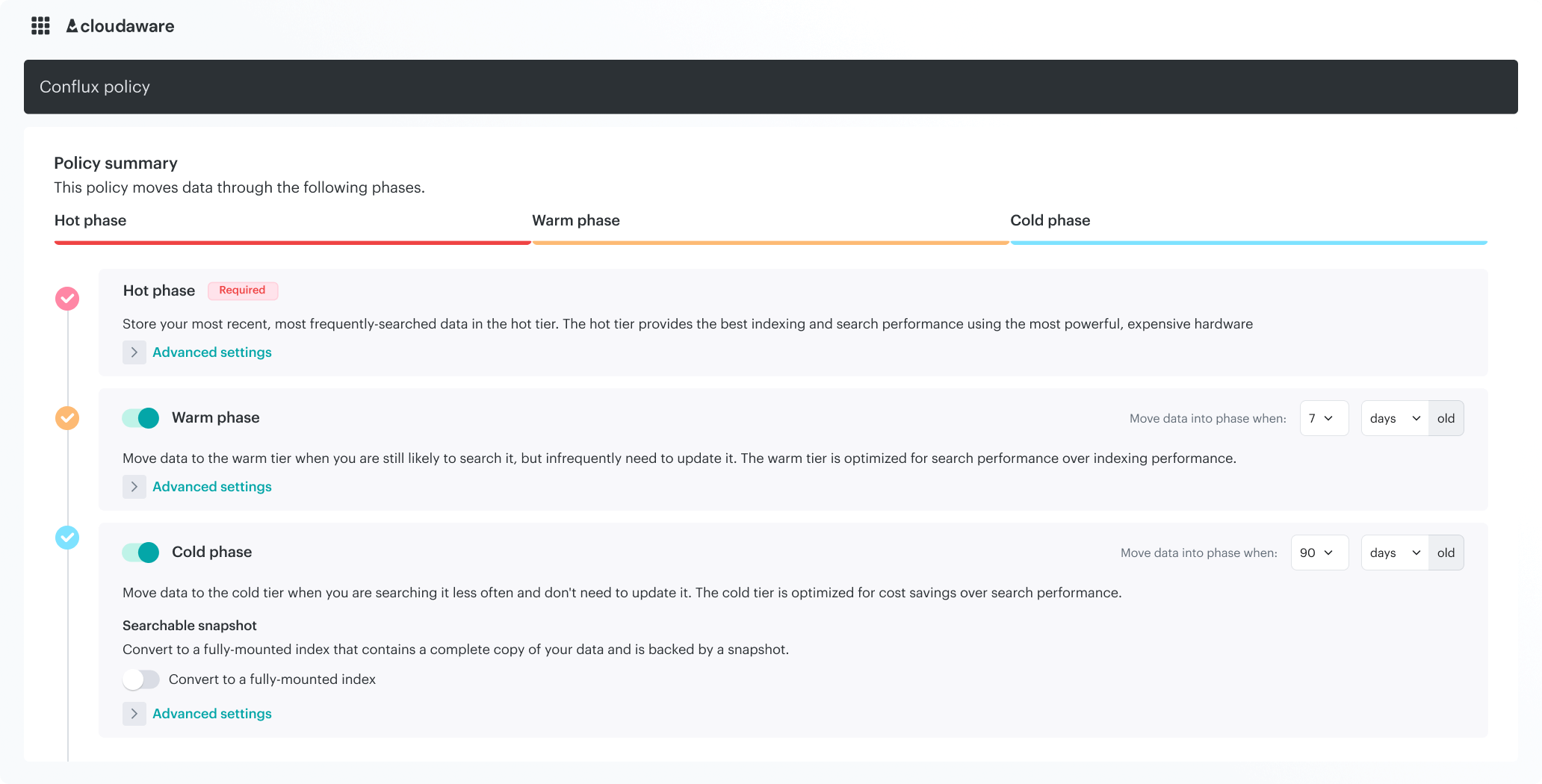
Keep recent logs searchable in real time, while older data is auto-archived to storage that’s 20x cheaper. Need data from a year ago? Just request it back
Auto-discover every log source
Cloudaware SIEM tool automatically identifies log sources across AWS, Azure, GCP, Oracle, and Alibaba Cloud. This eliminates the need for manual source configuration. These sources include CloudTrail, S3 access logs, ELB, VPC Flow Logs, Azure Activity Logs, and GCP Audit Logs. Each log is normalized and organized by service class, making them ready for lightning-fast correlation, regardless of the source.
- Autodetection of cloud-native logs across AWS, Azure, GCP, and Oracle
- Native support for on-prem log sources using Syslog and Beats
- Agentless ingestion via S3 buckets and cloud APIs
- Centralized storage with high-performance indexing by service type
- Built-in integrations ensure that logs are ready for querying
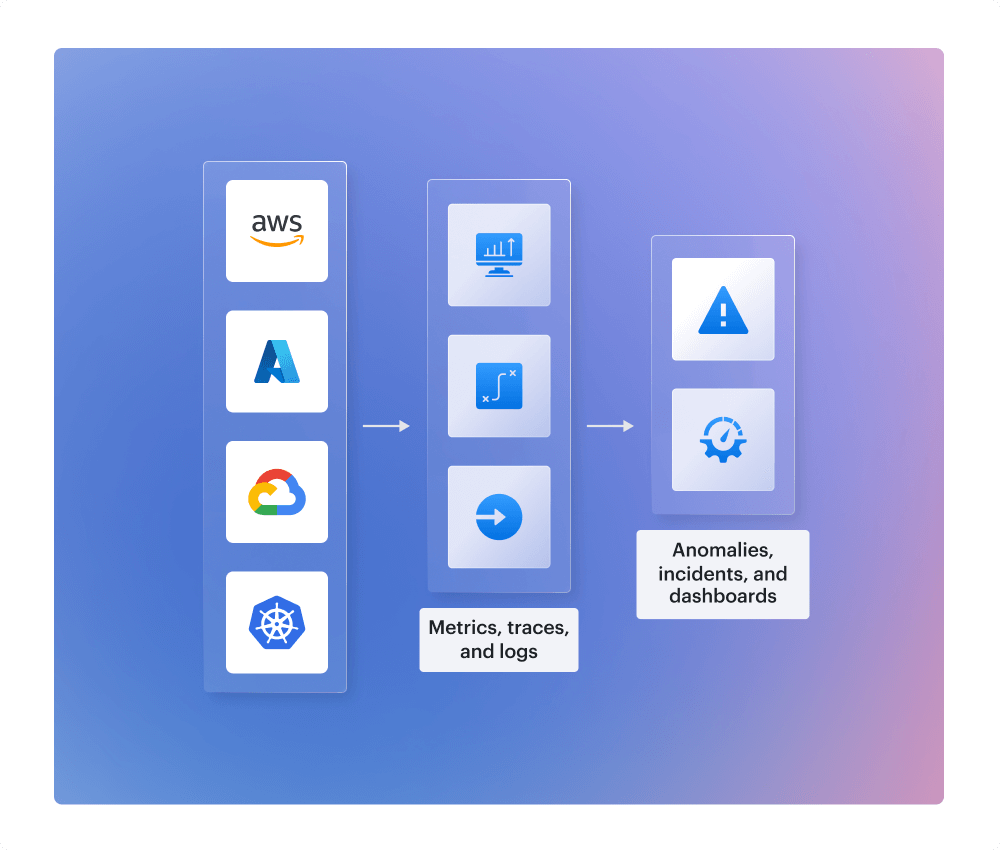
Detect threats in real time
Cloudaware’s SIEM solution filters out irrelevant info before it hits your queue. Built-in rules, pattern matching, and anomaly detection surface the important info. This includes unexpected geo access, suspicious logins, and configuration events. Our SIEM tool quickly identifies VPC traffic spikes, access anomalies, and API throttling, providing the necessary context for escalation.
What powers it:
- Pull logs from cloud services, containers, and on-prem systems without throttling
- Add owner, app, environment, and asset relationships to every log event for accountability
- Standardize the fields across sources and combine related events into a single storyline
NASA case study
Learn how Cloudaware helped NASA attain complete cloud visibility and secure cloud infrastructure.
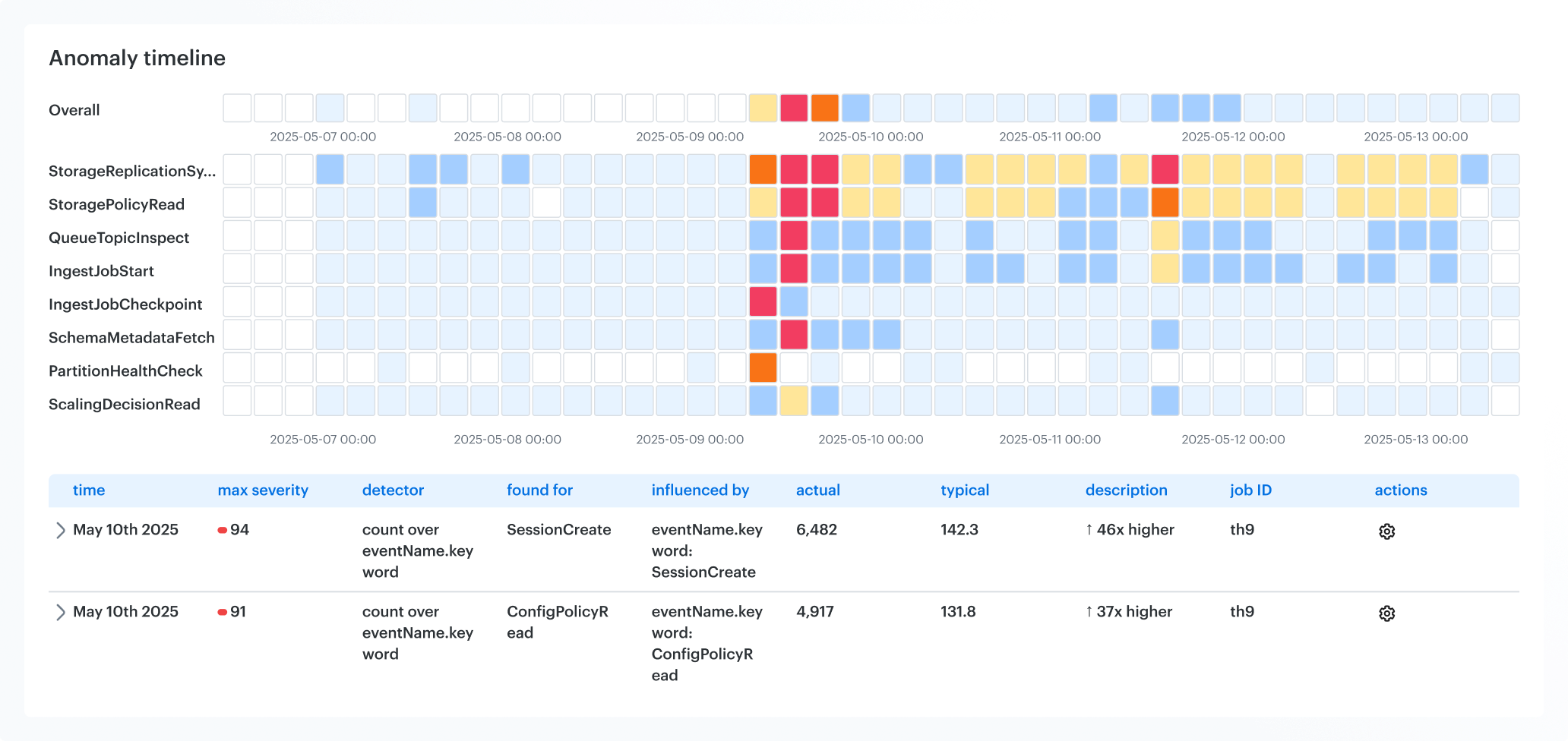
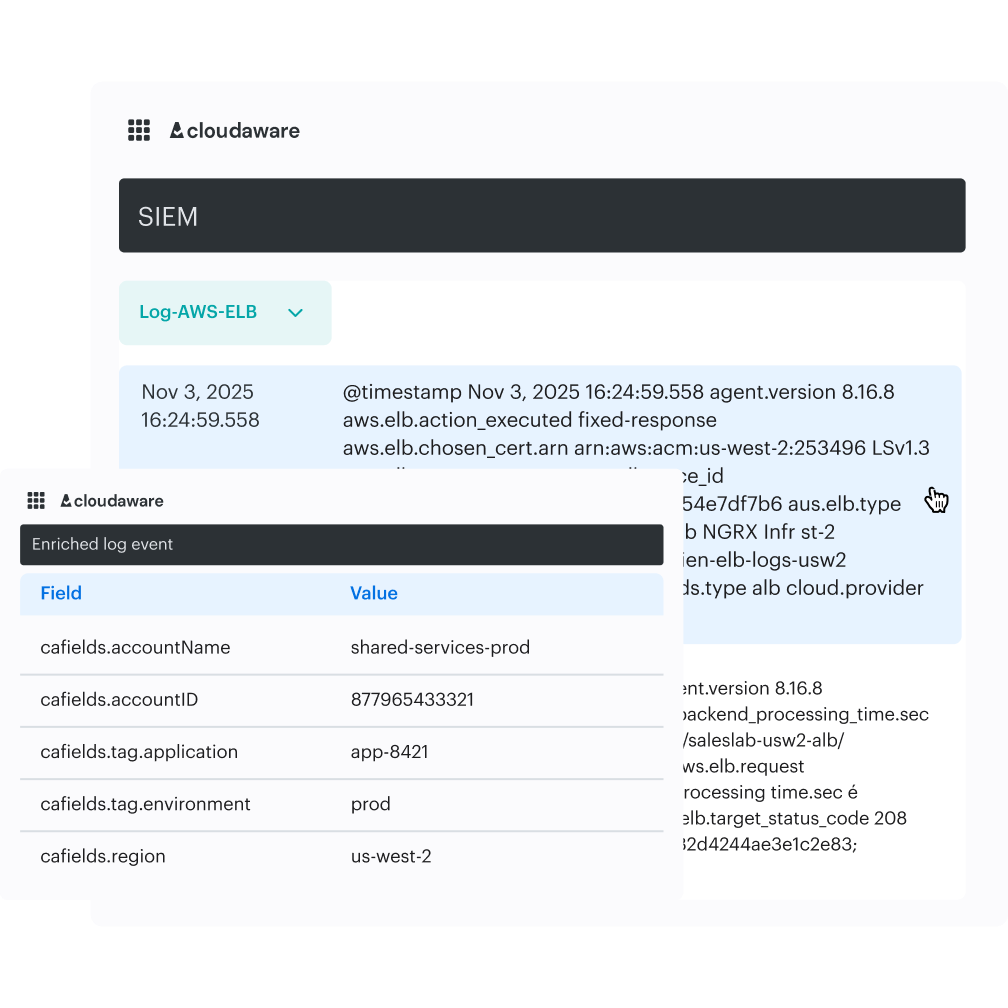
Analyze events with a CMDB context
Cloudaware’s SIEM system, Conflux, provides instant clarity on every cloud event, enriched with CMDB data. Access information about the owner, app, environment, and region. No guesswork, no digging. Use the search function to filter by any CMDB field and quickly trace issues. Timeline views and related-item grouping make it easy to establish the impact of issues or isolate anomalies.
What powers the analysis:
- CMDB tags are applied to log events at the point of ingestion to provide full context
- Deep search across cloud services and applications
- Cross-cloud and hybrid traceability with multi-index queries
- Logs are auto-grouped by service class
- Fast drilldowns with filters that make sense
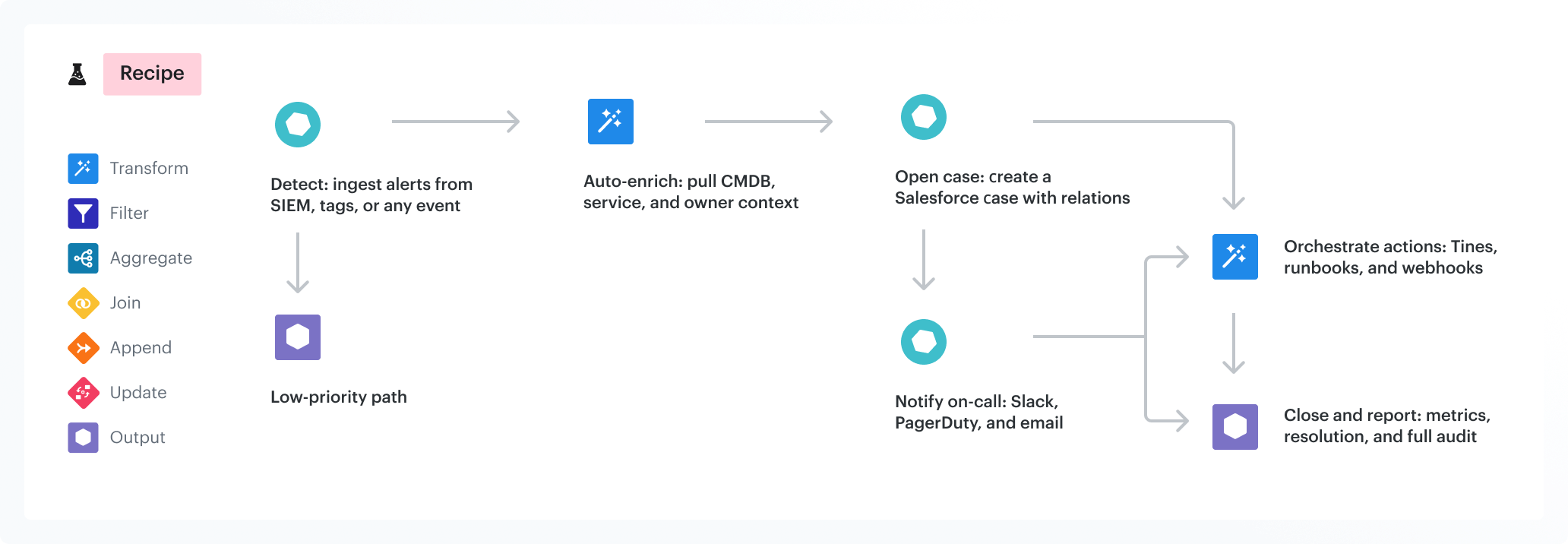
Respond automatically to critical changes
Avoid alert fatigue and manual escalations. Cloudaware's SIEM security software turns detection into action with native automation. As soon as a rule is triggered, Conflux can notify a service owner, open a ticket, enrich the alert, or even automatically resolve the issue. It all depends on the criteria you define. Use real response automation, powered by tags, service classes, and CMDB data. This ensures that the correct fix is deployed immediately.
What powers it:
- Native Tines integration for creating and executing remediation workflows
- Notifications and ticket creation via tools like PagerDuty, Jira, ServiceNow, and Rally
- Trigger-based automation from any alert, tag, or condition
- Role-based guardrails to control who can approve or auto-execute actions
- Full-lifecycle workflows: enrichment, escalation, and resolution
Transform raw logs into audit-ready proof
Every log is retained, versioned, and linked back to its source. It comes with the tags and context needed to show ownership, scope, and response. Get clean lineage from event to action. Do you want to know who triggered what, when, and where? It’s already logged and exportable. Metrics on MTTR, MTTD, and alert volume are tracked by default. Demonstrate what is and isn't working.
What powers it:
- Built-in log retention. The current month + 2 full months hot. Auto-archived beyond that
- Full traceability across alerts and actions thanks to the immutable event history
- Role-based access to log data and audit controls to align with SOC 2, ISO, PCI, and HIPAA
- Audit-ready reports with full event lineage, tags, and service class groupings
- Metrics tracking for MTTD, false-positive rates, and alert resolution
Explore SIEM solutions for SecOps teams
Discover more Cloudaware tools
Transform the way you discover and organize log sources with SIEM capabilities
Cloudaware helps security operations (SecOps) teams centralize logs, identify threats, and automate responses across multi-cloud and on-prem environments.
$15.7B
in managed spending across 5 cloud providers
99.995%
historical uptime for Cloudaware CMDB
63
CMDB integrations with industry leading tools
3,000+
supported cloud services and CI types
SIEM system FAQs
What is a SIEM tool?
What makes Cloudaware the best SIEM for AWS and hybrid environments?
Which SIEM capabilities can you offer?
What approach do you take to SIEM automation?
How does Cloudaware measure up against New Relic and other traditional tools?
Which log sources does the Cloudaware SIEM support?
Does the Cloudaware SIEM solution include reporting and dashboards?
Updated Sep 2025







