Tackle security debt with vulnerability management software
Stop managing endless vulnerability backlogs. Use CMDB context to group vulnerabilities into actionable tasks. Deliver measurable reductions in business risk.
Read-only permissions required
No credit card needed
Automated and guided setup
30-day free trial
Read-only permissions required
No credit card needed
The best vulnerability management software
Identify and mitigate software vulnerabilities across cloud, on-prem and desktop environments
Accelerate remediation and shorten incident response cycles with automated scanning and reports
Skip building tools to connect Tenable, Qualys, Wiz, etc. Cloudaware integrates with all your scanners
Cloudaware integrates scanner data into your CMDB and change workflows — turning vulnerability findings into real, trackable action
Already using Nessus, Wiz, or Crowdstrike vulnerability scanner?
Seamlessly integrate your existing vulnerability scanning solution with Cloudaware to gain a complete risk context across all scanners. Align with frameworks like CIS, PCI DSS, and HIPAA. Turn fragmented scan data into actionable, prioritized insights.
Secure every cloud asset with vulnerability management software
Identify and remediate hidden vulnerabilities with Cloudaware’s always-on asset discovery and risk assessment. Strengthen your security posture, reduce mean time to remediation (MTTR), and maintain audit-ready compliance through asset-level vulnerability management. Gain complete visibility into all cloud assets—known and unknown—including:
- Multi-cloud resources
- Remote endpoints
- Dynamic workloads
- Shadow IT
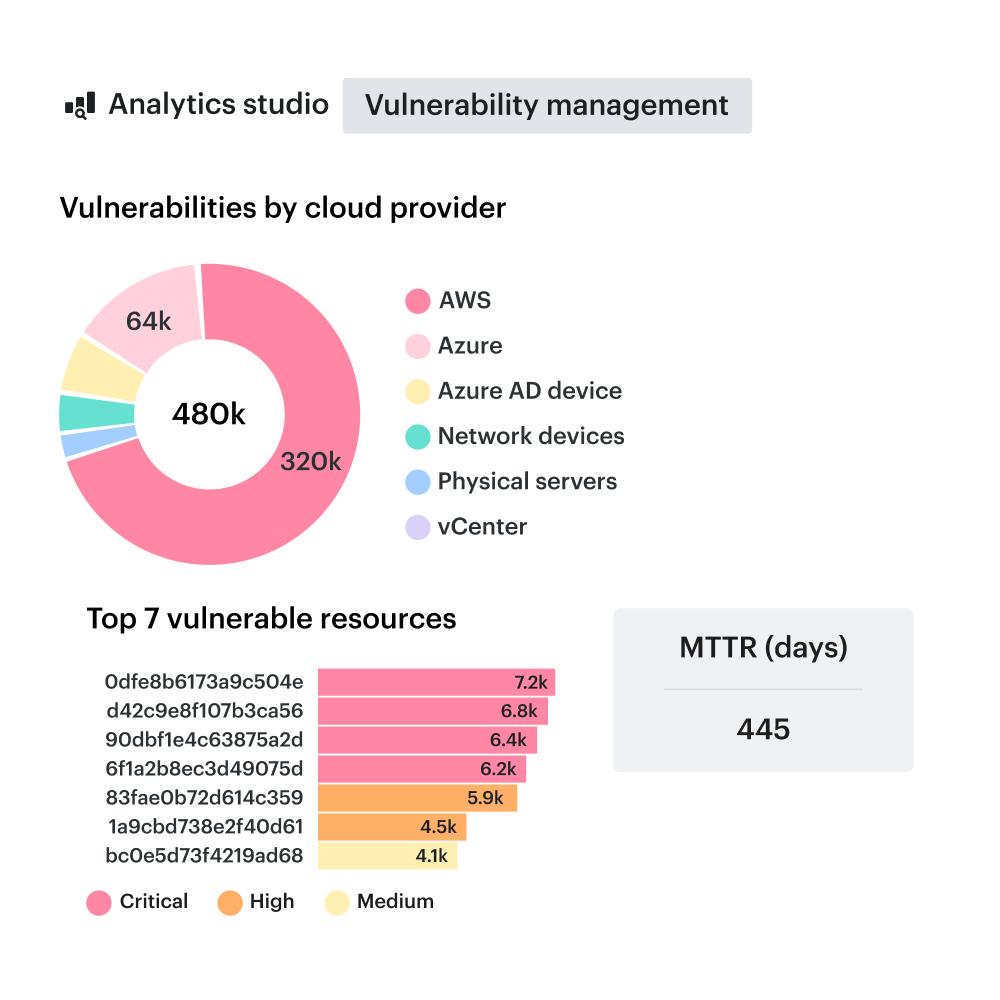
End-to-end vulnerability insights
Identify vulnerabilities across every layer of your cloud environment with continuous assessment. This includes everything from source code and Git repositories to container images, virtual machines, and deployed applications.
- Agent and image based scans aligned with CISA and industry standards
- Network-based scanning with IP-level coverage
- Web application testing using OWASP Top 10 vulnerability scanning
- Container security with Docker image analysis
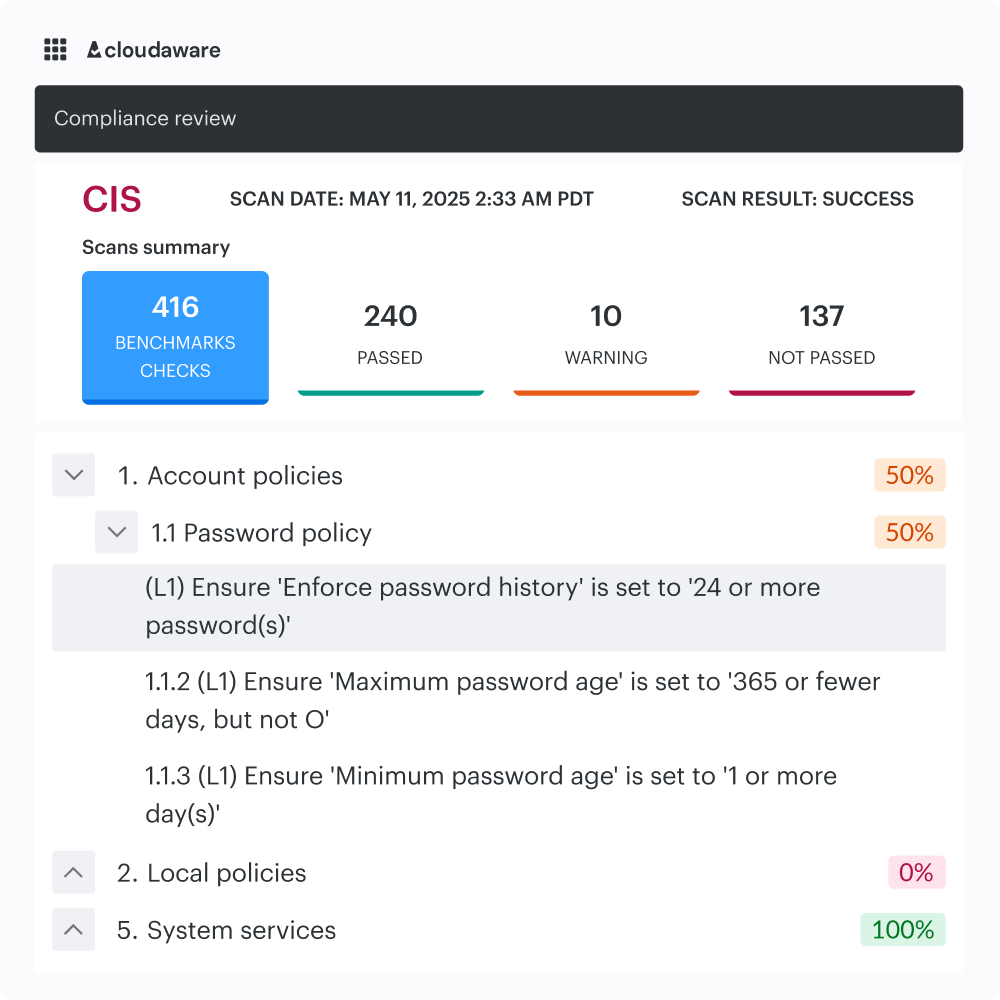
Compliance and threat detection
Cloudaware’s vulnerability management software helps enforce cloud compliance standards and detect threats in real time. Maintain continuous alignment with industry benchmarks.
- Automated compliance checks for HIPAA audits, CIS Benchmarks, DISA STIGs, and PCI DSS
- Patch management and malware detection
- Coverage for critical vulnerabilities like Spectre, Meltdown, WannaCry, and more
- Container security with Docker image analysis
- PHI and PII data leaks with TNS content inspection
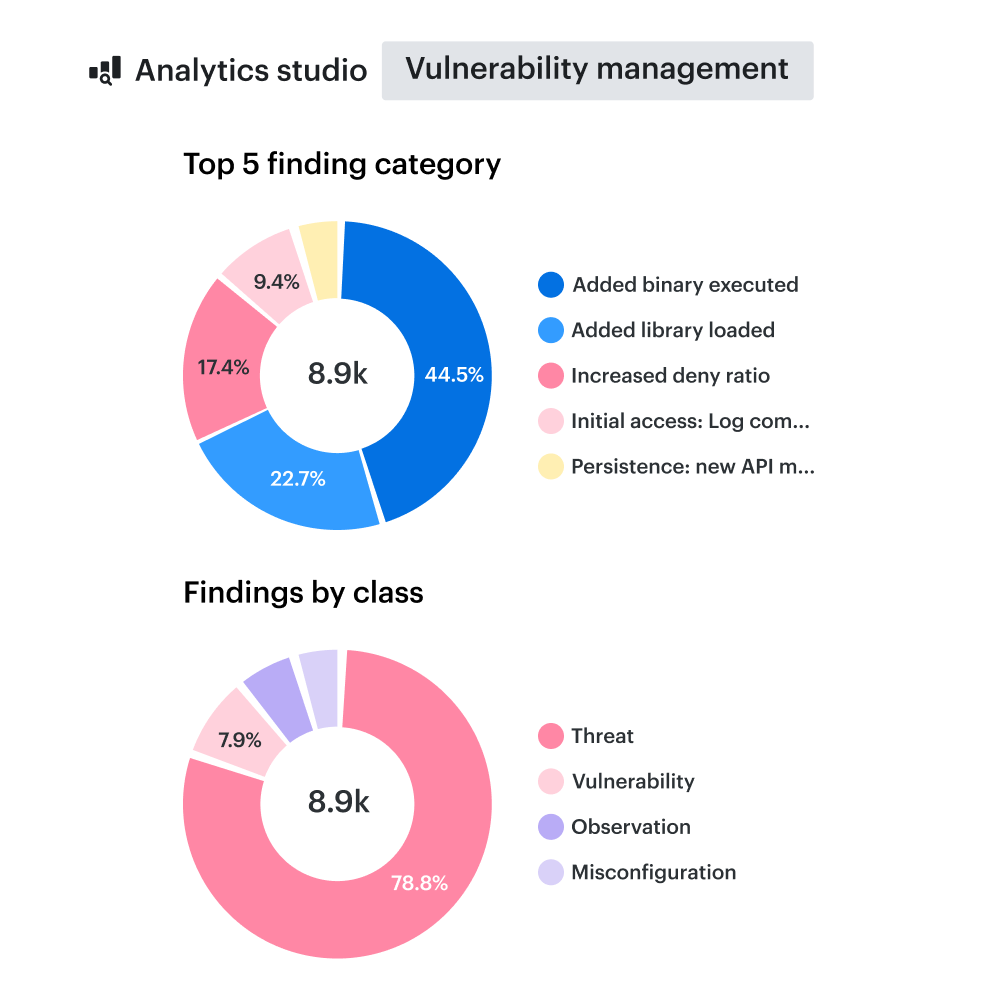
Unified security dashboard
Centralize risk management and asset intelligence with a unified security dashboard. Track cloud assets, map dependencies, and measure impact with a structured, CMDB-enhanced view of your risk exposure.
- Unified dashboard for full cloud asset inventory and security posture
- Automated dependency mapping for risk-aware decision-making
- Custom tags and filters to simplify triage and reporting
Close scan coverage gaps
Cloudaware delivers flexible, cloud-native vulnerability scanning with both agent-based and agentless options. Achieve continuous visibility across cloud instances containers, and on-prem infrastructure.
- Agentless and agent-based scanning for hybrid and multi-cloud environments
- Continuous vulnerability scanning every 15 minutes
- Full coverage across VMs, Docker containers, and Kubernetes workloads
Caterpillar case study
Learn how Caterpillar leveraged Cloudaware to achieve FinOps success and cloud governance at scale, saving $627,000 in annual cloud costs.
Proactively contextualize threats
Prioritize the most critical issues. Link vulnerabilities to key risk factors, such as external exposure, misconfiguration, and malware. Leverage real-time context and asset intelligence to take action where it matters most.
Leverage asset-level context to identify and rank vulnerabilities based on their business impact. Vulnerabilities may include public exposure, outdated configurations, or critical usage patterns. Map each threat to its environment for smarter prioritization.
Automatically filter out irrelevant findings and focus only on vulnerabilities tied to high-value services as defined in CMDB. Increase efficiency and streamline remediation with real-time, risk-aware scanning. Cut through noise to act on real, exploitable threats.
Use CMDB-driven intelligence to trace cloud or hardware vulnerabilities back to their source. Vulnerabilities may result from an outdated packages, misconfigured services, or mismanaged access. Focus your patching and remediation efforts on the root cause, not just the symptoms.
Prioritize vulnerabilities that matter
Cloudaware’s risk-based vulnerability management uses CMDB context to prioritize real threats. By mapping vulnerabilities to your actual IT services, it highlights what truly matters — like exploitable risks in publicly accessible, business-critical systems.
Cloudaware uses factors such as severity, exploitability, asset exposure, and business context to score vulnerabilities. This enables your teams to minimize false positives, eliminate distractions, and focus resources on threats that pose the greatest risk to operations, compliance, and security.
Vulnerability management with Amazon Inspector
Watch this webinar to learn how Amazon Inspector and Cloudaware work together to address vulnerabilities. Explore how top security teams achieve full scan coverage and quickly remediate vulnerabilities across complex cloud environments.

Automate vulnerability remediation at cloud scale
Accelerate remediation with automated workflows and real-time ticketing integrations. Keep your security and DevOps teams aligned across all cloud environments to ensure that vulnerabilities are assigned, tracked, and resolved faster.
Create custom workflows that auto-assign remediation tasks based on vulnerability severity, status, or asset type. Notify the right teams instantly and reduce time-to-action with real-time orchestration.
Integrate with ServiceNow, JIRA, or PagerDuty to generate and update tickets as vulnerabilities are discovered or resolved. Align remediation efforts with your cloud security protocols and ensure nothing falls through the cracks.
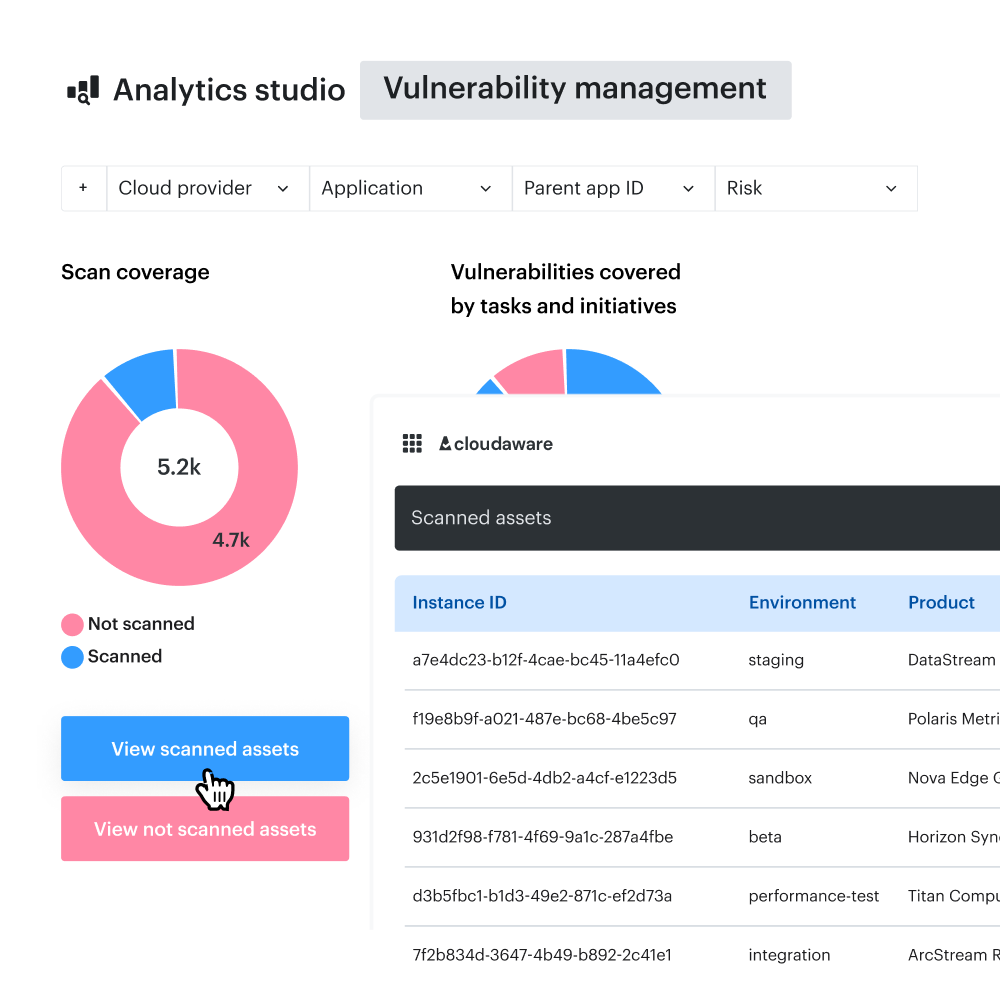
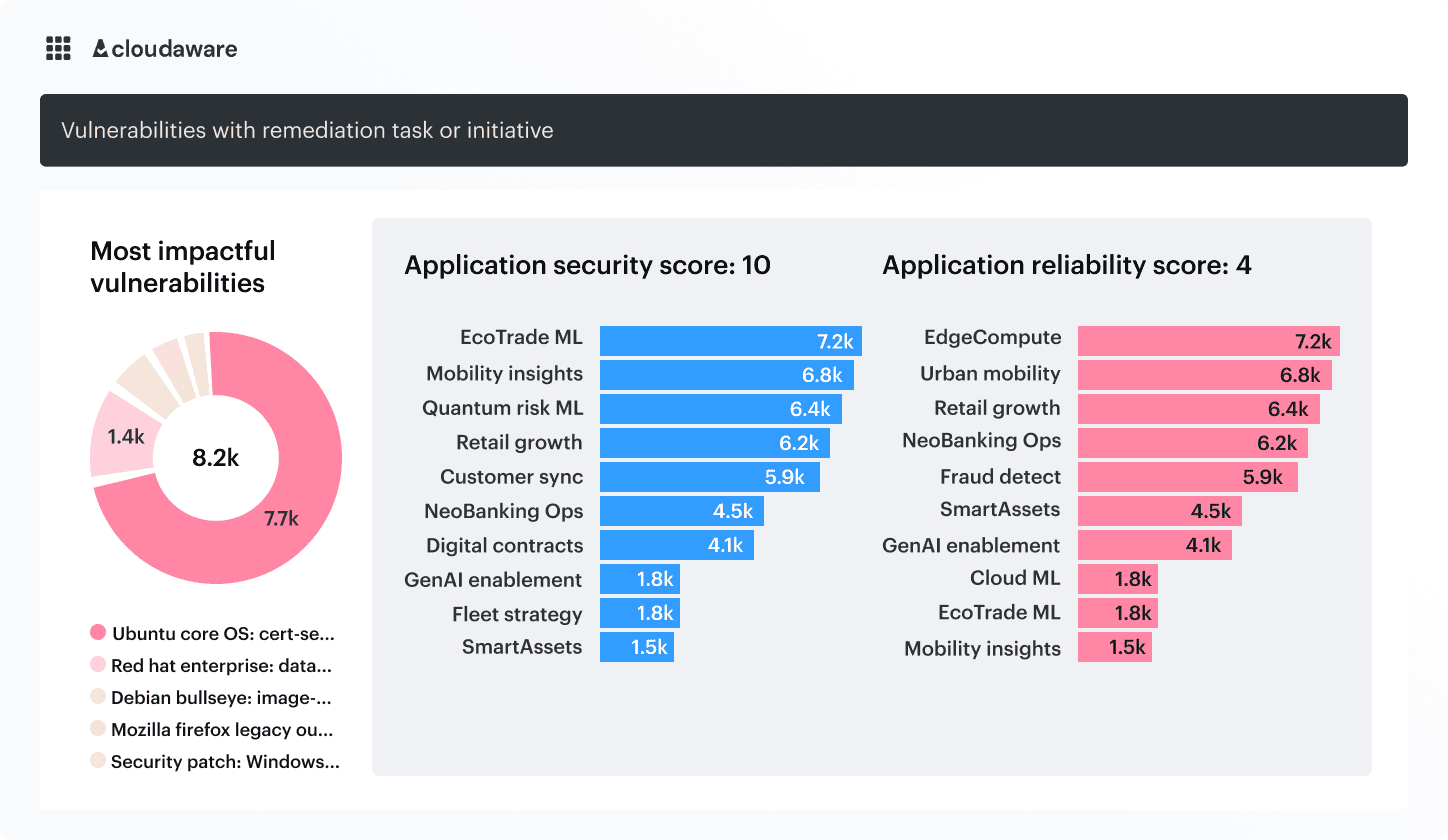
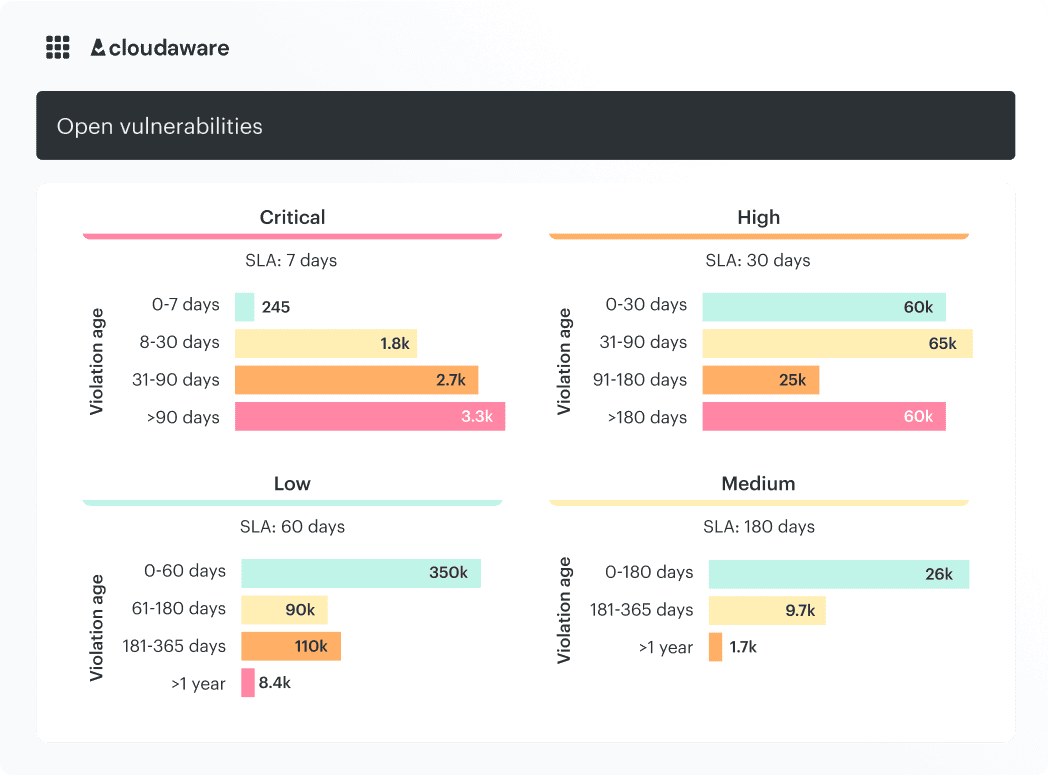
Visualize vulnerabilities with dashboards and custom reports
Use real-time dashboards to track what matters most: scanning coverage, vulnerability age, and asset exposure. Drill down into remediation status and security gaps. Filter by tags, apps, or cloud accounts.
Connect assets, vulnerabilities, and third-party tools for a unified view of your security posture. See where issues intersect to prioritize response across teams and systems.
Create detailed reports to track unscanned assets, identify critical vulnerabilities by age or severity, and isolate CVEs by asset type. Build reports for compliance, triage, or executive visibility.
Maximize security with Cloudaware vulnerability management features
Cloudaware empowers security and DevOps teams with a powerful set of enterprise vulnerability management tools. Identify, prioritize, and remediate risks faster. These tools are backed by cloud-native coverage, automated workflows, and real-time visibility across your infrastructure.
Automatically identify and catalog all cloud and on-prem resources in real time to gain full visibility into your environment, enhancing cloud vulnerability management.
Cloudaware’s dashboards provide visual reports on vulnerability data. This makes it easy for teams to track risks and monitor remediation efforts, improving application vulnerability management.
Use trend analysis tools to track vulnerabilities over time, spot patterns, and proactively adjust your security strategy with managed vulnerability scanning.
Automatically route tasks to the right teams based on predefined criteria. This improves response times and efficiency in managing vulnerabilities.
Extend vulnerability management with Cloudaware’s modules
Vulnerability management software FAQs
What is meant by Cloudaware vulnerability management?
What is risk-based vulnerability management?
Can you do on-demand scans?
Does the agent run on a private machine?
Do you support docker image scanning?
What does Cloudaware do to protect my data?
Updated Sep 2025







