Automate CSPM with CMDB-aware policies
Go beyond cloud configurations with a no-throttling CSPM. Cloudaware merges CMDB data with multi-cloud and on-prem checks to give you enforceable guardrails.
Read-only permissions required
No credit card needed
Automated and guided setup
30-day free trial
Read-only permissions required
No credit card needed
Meet the leader in CSPM tools
CMDB-enabled compliance visibility
See every cloud and on-prem finding in one view, decorated with apps and owners
3x faster remediation
Auto-route findings to Jira, ServiceNow, and email. Assign owners from CMDB and auto-close tickets when fixes land
Frameworks on autopilot
Run ongoing assessments for CIS, NIST, ISO, PCI, and HIPAA. CMDB-aware policies interpret tags, scopes, and exceptions
Audit-ready compliance
Slash preparation time from weeks to days with automated and continuous CIS, NIST, ISO, PCI, and HIPAA checks
Don’t limit yourself to cloud-only checks
Cloudaware evaluates all IT configurations and tools, regardless of their hosting location. CMDB-aware guardrails use this comprehensive overview to enforce policies that other companies cannot even express.
- Use our ready-made policies and benchmarks, or add your own CMDB-aware controls (e.g., production Linux VMs must run IDS and have daily backups)
- See every EC2, VM, and container, as well as the tools that manage them. There's no need to guess which instance a tool actually covers
- Each finding contains the owner, app, and environment from the CMDB. This means that tickets are auto-assigned to the correct team with clear severity levels
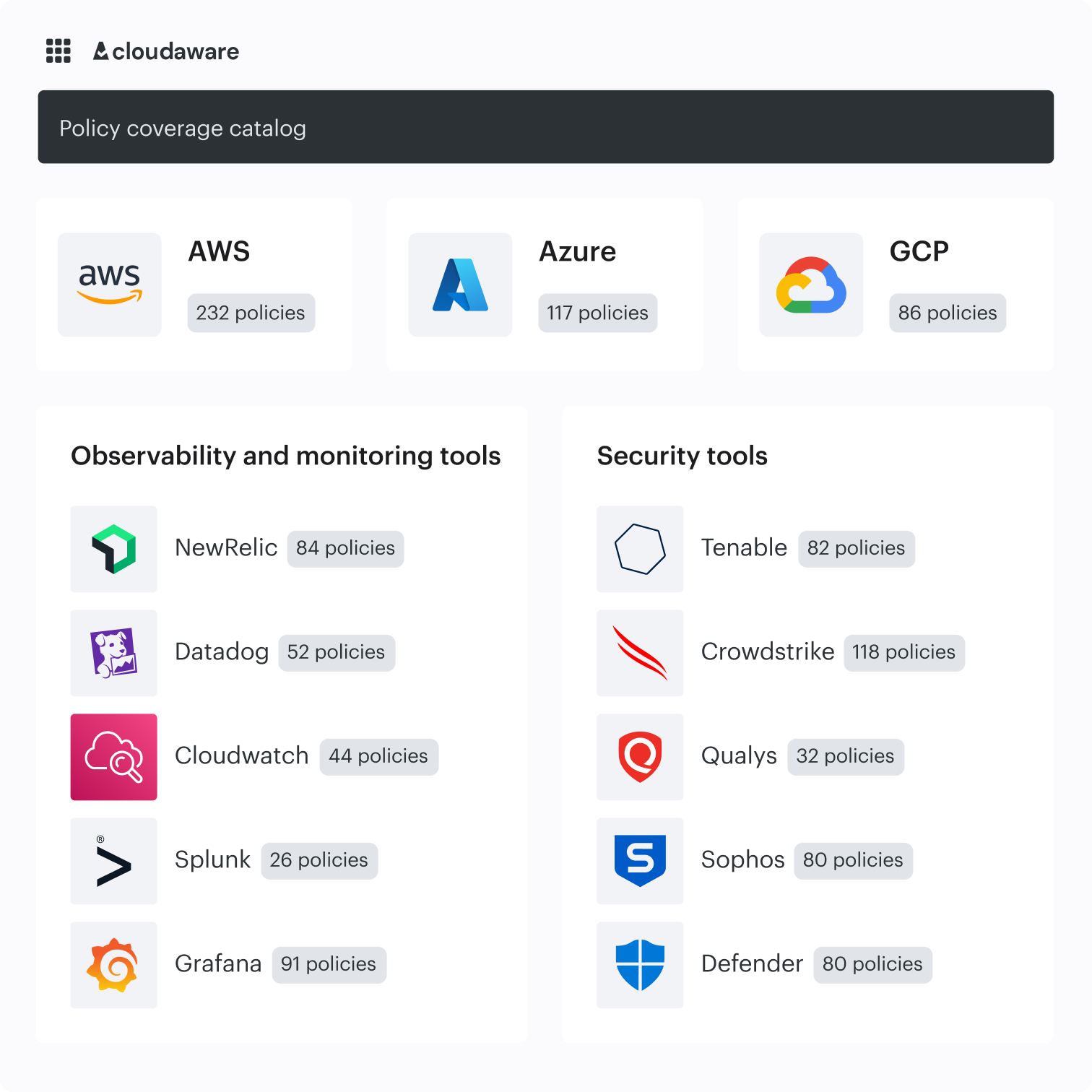
Discover your clouds and set compliance boundaries
Auto-discover cloud and on-prem CIs. Scope controls by app, environment, or risk from day one. Cloudaware ensures that every CSPM security examination is performed in the right context.
- Map every account and region into a single CSPM view
- Set boundaries per app/env (prod, stage, and dev) with built-in CMDB ownership
- Use boundary badges on services to prevent drift before it starts
- Get started with automated tagging and built-in organization for instant clarity
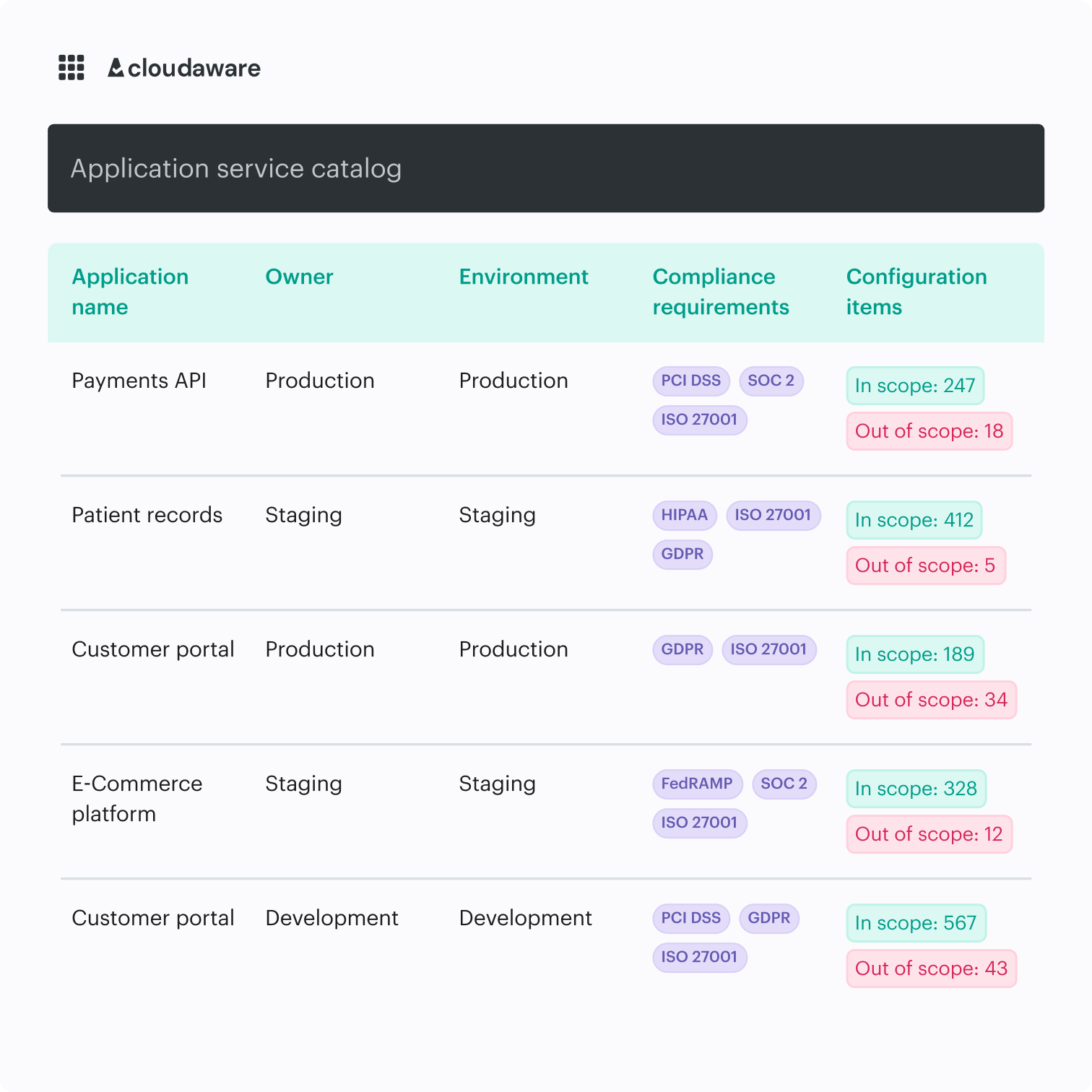
Measure everything that matters for CSPM security
Maintain an accurate inventory and scope with ready-to-share snapshots.
- Track the percentage of assets in scope vs. out of scope
- Monitor the discovery of new resources and boundary violations over time
- Compare compliance coverage across business units
- Track teams' progress in fixing CSPM violations over time
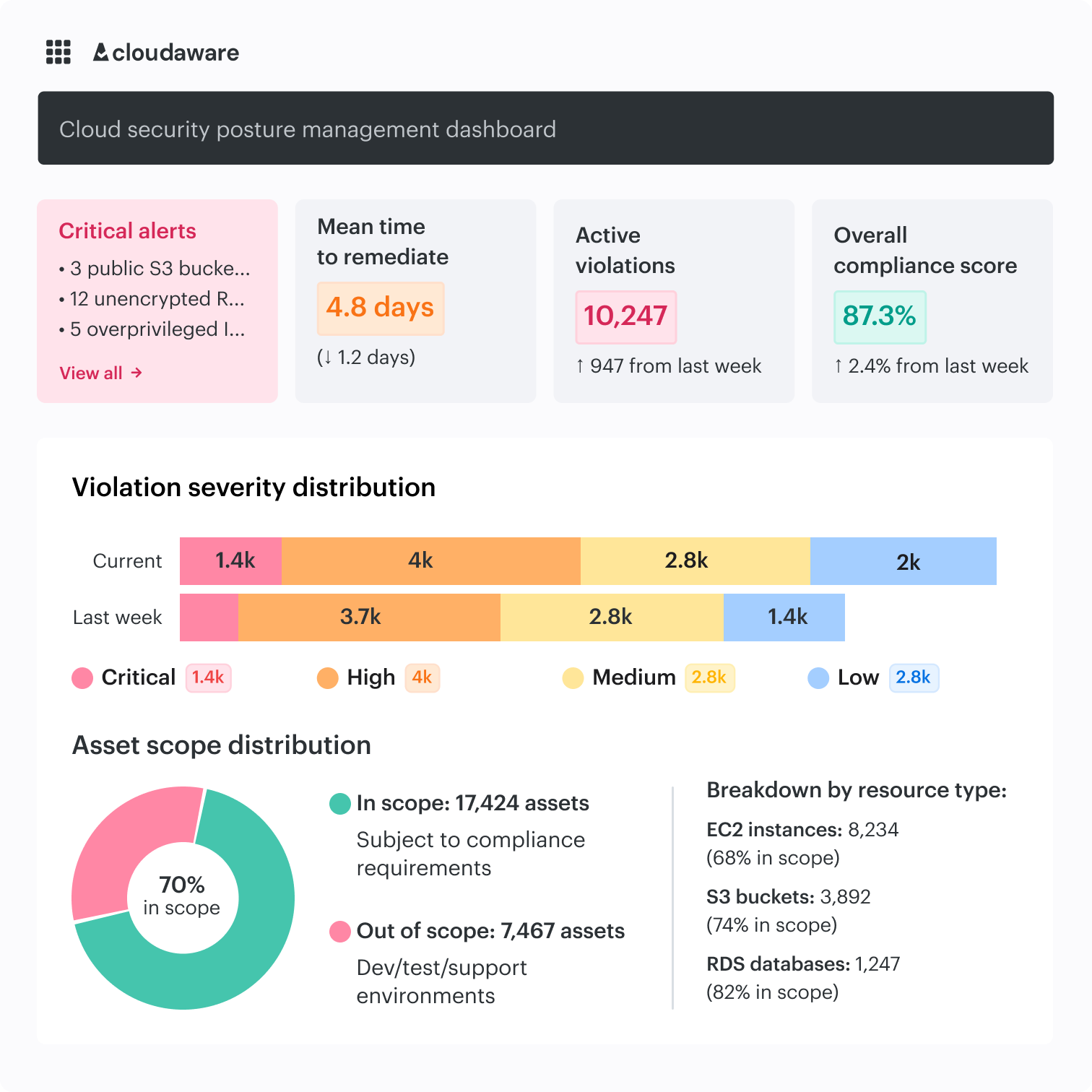
Automated conformance to CIS, NIST, ISO, and PCI
Perform ongoing CIS, NIST, ISO, PCI, and HIPAA assessments. Use UCF-enabled dashboards to map these assessments to the authoritative documents relevant to your industry.
- Use over 900 UCF authority documents to see which standards and articles apply
- Turn on baseline packs, tune by account or tag in minutes
- Get custom checks with Policy Development as a Service
- Author in-house with a YAML-based policy language
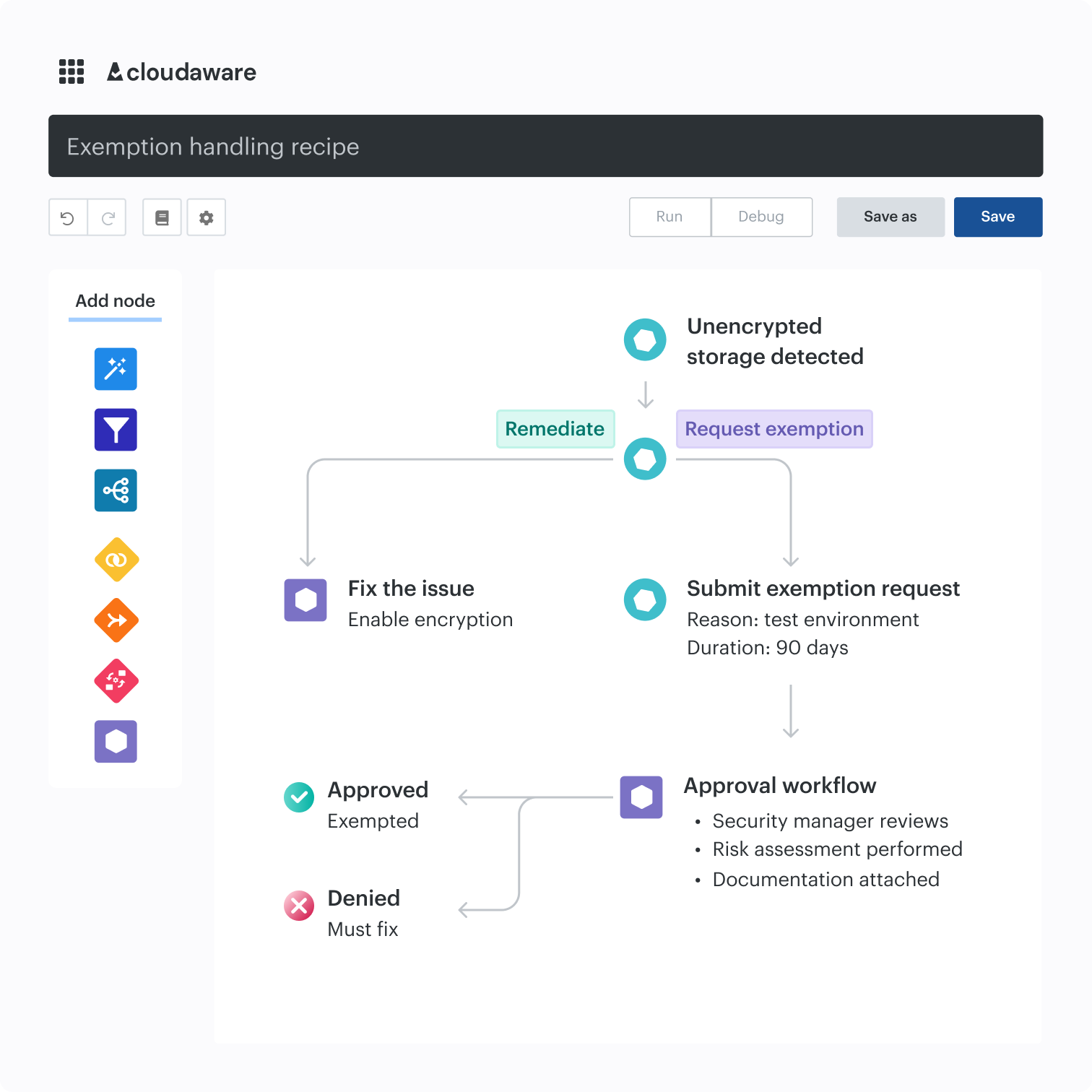
Prioritize risks and formalize exemptions
CSPM software ranks misconfigurations by owner, exposure, and blast radius. Use exemption handling to document legitimate deviations and ensure that true violations are never overlooked.
- Reduce noise with CMDB data context
- Group related items to understand the impact across accounts and regions
- Formalize exception lifecycles with review and approvals
- Focus efforts on the areas that will minimize the risk of breaches and outages the fastest
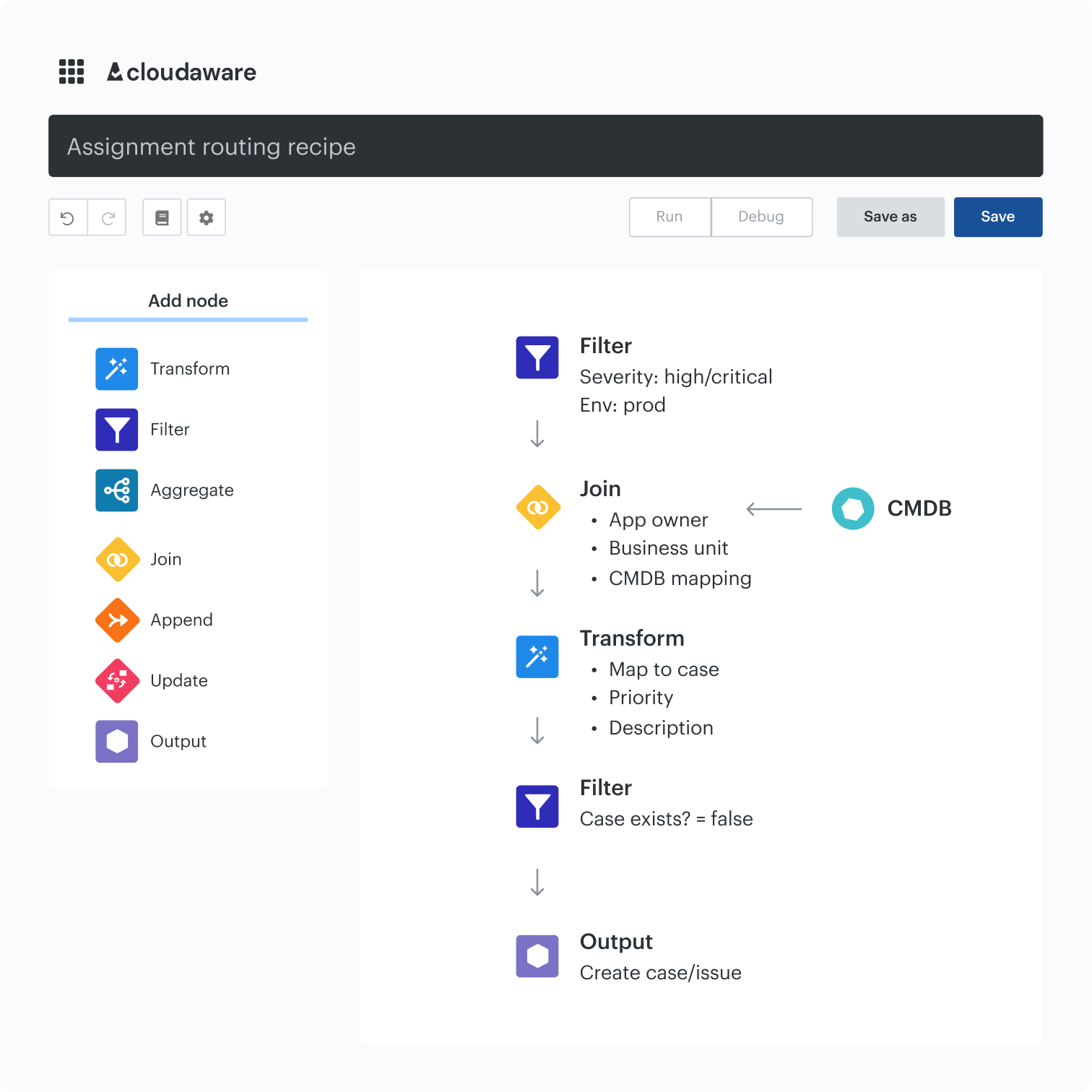
Route to owners and auto-remediate
Transform your findings into finished work. Violation routing uses the CMDB service catalog to assign the right team. Auto-remediation resolves issues. Ticketing integrations allocate tickets.
- Auto-create tickets with the app. Use CMDB data to pre-fill team owner tags
- Bidirectional sync keeps ticket statuses and CSPM violations in lockstep
- Use trigger automation playbooks to auto-fix common misconfigurations
- Escalate by SLA and environment to ensure that the MTTR continues to decrease
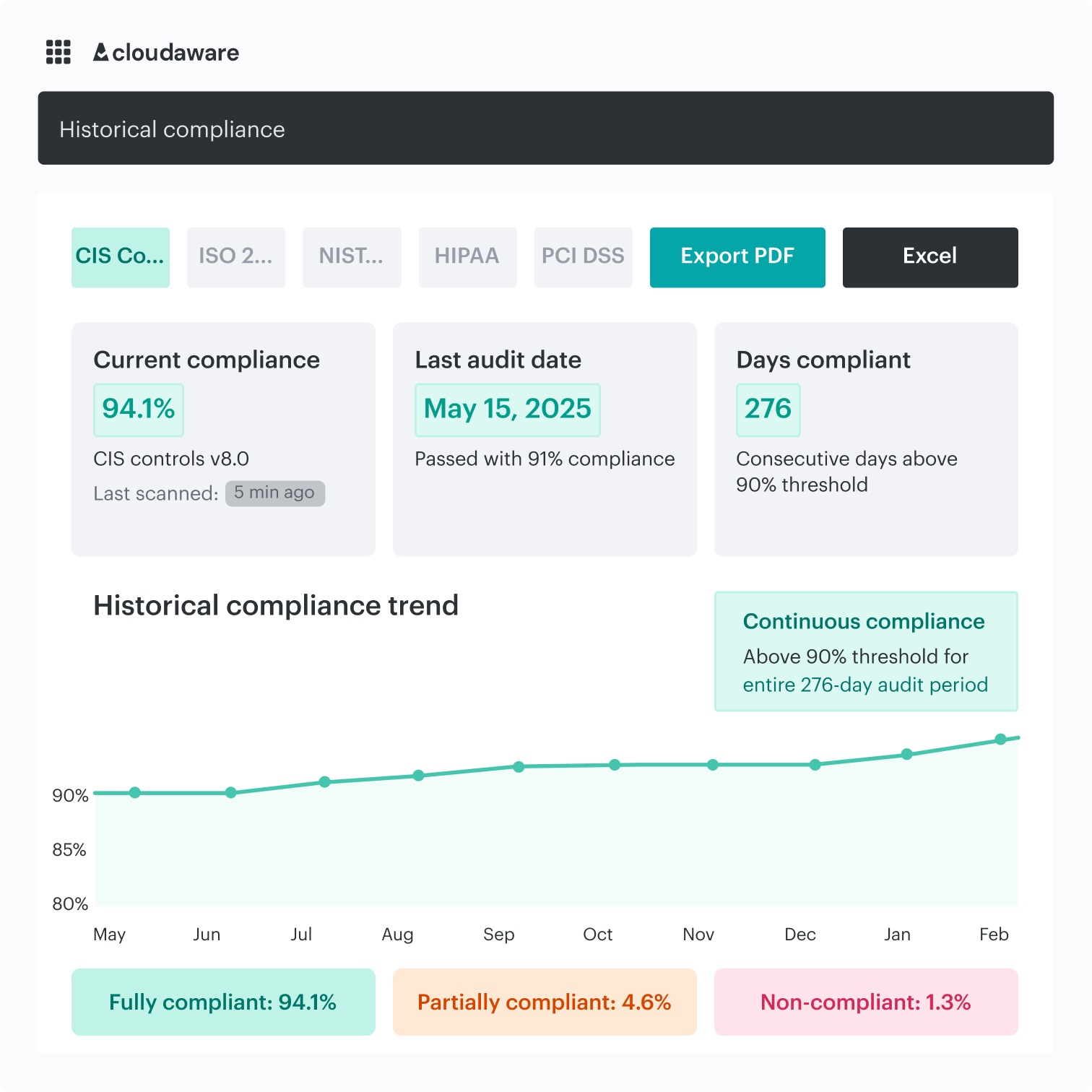
Audit-ready evidence
The CSPM platform provides everything you need: coverage, exemptions, owners, timestamps, and policy differences. UCF dashboards make attestation easy.
- One-click exports for auditors. Scope → finding → remediation trail
- Framework scorecards for CIS, NIST, ISO, PCI, and HIPAA
- Versioned diffs across policy updates to show change safety
- Ready-made exec views for posture and SLA compliance
Explore CSPM solutions for your team
NASA case study
Learn how Cloudaware helped NASA attain complete cloud visibility and secure cloud infrastructure.
Discover more Cloudaware tools
Prevent cloud misconfigurations and data breaches with CSPM
Cloudaware allows your SecOps and DevOps teams to automate framework compliance and assess risk using CMDB context. Free up time for teams to focus on what really matters most.
$15.7B
in managed spending across 5 cloud providers
99.995%
historical uptime for Cloudaware CMDB
63
CMDB integrations with industry leading tools
3,000+
supported cloud services and CI types
CSPM FAQs
What is CSPM, and how does it work in Cloudaware?
Why choose Cloudaware over other vendors?
Which standards and regulations should we align with?
How does Cloudaware reduce noise and handle acceptable deviations?
Can Cloudaware automate the remediation process and close tickets?
Will it fit into our existing reporting and governance stack?
How quickly can we see value after connecting our clouds?
Updated Sep 2025







