Virtual machines running mission-critical workloads. APIs stitching together services. That old database still holding customer records. A fleet of Kubernetes clusters orchestrating deployments. The software tools securing endpoints. Even that SaaS subscription someone forgot to cancel.
All of them? They’re IT assets. The lifeblood of your infrastructure, silently powering operations, scaling workloads, and — when left unchecked — becoming budget leaks, security gaps, or compliance headaches.
That’s why tracking isn’t just about knowing what you own. It’s about control, efficiency, and risk mitigation. Lose sight of an IT asset, and you might lose more than just money — you’re looking at vulnerabilities, downtime, and shadow IT creeping into your stack.
So, how do you make IT asset management work in 2025? This article unpacks asset categories, IT asset visibility, and best practices for management across hybrid and multi-cloud environments. Need clarity? Keep reading — or contact our experts when things get messy.
What is an IT asset?
An IT asset is any piece of technology — hardware, software, or cloud resource — that powers your infrastructure, supports operations, or holds business value. If it can be deployed, tracked, or optimized, it’s an asset.
Think of Configuration Items (CIs): your EC2 instances, Kubernetes clusters, RDS databases, and API gateways humming in AWS. Your firewalls, load balancers, and network appliances direct traffic across hybrid clouds. Your SaaS solutions and software licenses keep teams productive.
Even rogue shadow IT services sneak into the stack, often unnoticed.
Every IT asset must have key characteristics to be properly managed. It has:
- identifier (a unique name or tag),
- ownership (who is responsible for it),
- lifecycle status (active, deprecated, archived),
- dependencies (what other systems it connects to),
and cost association (its financial impact).
If any of these elements are missing, the IT asset becomes harder to track, optimize, or secure.
In Cloudaware CMDB, this information is enriched with real-time metadata, usage statistics, compliance checks, and security insights. This means every IT asset isn’t just cataloged — it’s actively monitored and analyzed for risks, inefficiencies, and optimization opportunities.
Here is how it looks like: 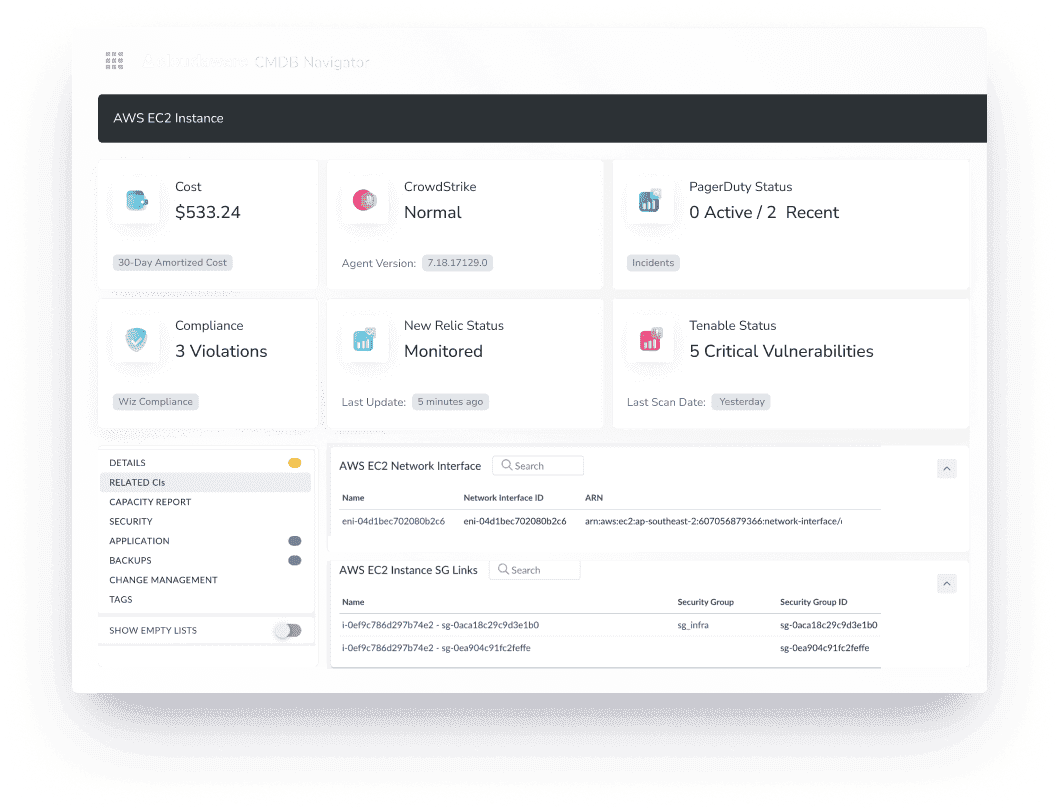
Without IT asset tracking, you’re blind to cost leaks, compliance gaps, and security risks. That’s where IT asset management and Configuration Management Database step in. They map dependencies, monitor usage, and keep IT assets from turning into liabilities.
So, what exactly qualifies as an IT asset in your environment? Let’s break it down with some real-world examples.
Real-World IT assets examples in Hybrid Multi-Cloud Environments
Asset IT isn’t just about physical hardware — it’s the backbone of your cloud infrastructure. Every workload, data store, and networking component is part of a complex system that needs management. Some IT assets are well-documented, others are forgotten, but all play a role in your operations.
Let’s talk about three common IT assets in hybrid multi-cloud environments.
1. The Ghost VM: Compute Resources That Never Die
Somewhere in your AWS account, an EC2 instance has been running far longer than intended. It was meant for temporary testing, but no one shut it down. Over in Azure, a detached virtual disk lingers, consuming storage despite being forgotten after an autoscaling event. Meanwhile, an abandoned Google Cloud Compute Engine VM still has IAM roles assigned — an unnoticed security risk.
Compute resources are some of the most common IT assets in hybrid multi-cloud setups. Whether it’s virtual machines (VMs), containerized workloads, or serverless functions, these assets exist across multiple platforms. They hold data, execute workloads, and, when unmanaged, silently drain budgets.
2. The Lost Object Storage Bucket: Forgotten but Holding Critical Data
Cloud services rely on storage, but not all of it is properly accounted for. In AWS, an S3 bucket still contains logs from a decommissioned application. In Azure, a Blob Storage container is holding customer reports from two years ago. Over in GCP, a Cloud Storage bucket remains accessible but hasn’t been updated in months.
These storage buckets are critical IT assets because they hold business and operational data. Sometimes, they actively support applications. Other times, they’re untagged, outdated, and left with open permissions. Without tracking, they become security risks — especially when sensitive data is involved.
3. The Kubernetes Cluster That Keeps Growing
Your organization relies on Kubernetes, but not all clusters are well-managed. In AWS, an EKS cluster is running workloads that should have been migrated. In Azure, an AKS cluster has persistent volumes attached to long-terminated pods. Meanwhile, an on-prem OpenShift deployment is consuming double the expected resources.
Kubernetes isn’t just a compute layer — it’s a dynamic IT asset that interacts with networking, storage, and security policies. Every node, pod, and deployment impacts costs, performance, and compliance. Without software-driven monitoring, scaling gets messy, and costs spiral out of control.
Hybrid multi-cloud environments are packed with IT assets — some active, some forgotten, all influencing infrastructure efficiency. From compute instances to storage buckets to Kubernetes clusters, these assets shape your cloud reality.
4 types of assets within your infrastructure
Every IT asset has a role. Some actively process workloads, some silently manage communication, and others control who and what gets access. But here’s the thing: these assets aren’t all the same. They function differently, require different management strategies, and introduce different risks when left unchecked.
Let’s break down four distinct types of IT assets that shape your operations and why tracking them is non-negotiable.
1. Cloud & Compute Assets – The Workforce of Your Infrastructure
These are the powerhouses that run workloads, whether they’re in the cloud, on-prem, or somewhere in between. They actively process applications, execute tasks, and scale with demand.
Examples of Compute Assets:
- Virtual Machines (EC2, Azure VMs, GCE). Traditional workloads running in cloud or on-prem hypervisors.
- Kubernetes Clusters (AWS EKS, Azure AKS, GKE). Orchestrating containerized applications.
- Serverless Functions (AWS Lambda, Azure Functions, Cloud Functions). Running event-driven automation without managing servers.
- Bare Metal Servers & Edge Devices. Supporting low-latency, high-performance use cases.
Compute assets are highly dynamic, frequently spinning up and shutting down. They require constant IT asset tracking to prevent orphaned VMs, unused functions, and overprovisioned resources.
2. Network & Security Assets – The Gatekeepers of Your Stack
Compute alone isn’t enough — networking assets ensure applications, users, and services can talk to each other securely and efficiently. Unlike compute, these assets don’t process data — they route traffic, enforce security, and define boundaries.
Examples of Network & Security Assets:
- Virtual Private Clouds (VPCs) & Subnets. Defining cloud network segmentation.
- Firewalls, Security Groups, & WAFs. Controlling inbound/outbound traffic.
- Load Balancers (AWS ALB/NLB, Azure Load Balancer, GCP Load Balancing). Distributing traffic across applications.
- API Gateways (Amazon API Gateway, Apigee, Azure API Management). Managing service-to-service communication.
Unlike compute, which is short-lived, network assets are long-lived and require ongoing validation to avoid misconfigurations, security holes, and performance bottlenecks.
3. Software & Application Assets – The Brains of Your Infrastructure
What’s running inside your infrastructure? Software and applications — and they need as much tracking as your physical and cloud IT assets.
Examples of Software Assets:
- Containerized Applications (Docker Images, Helm Charts). Running inside Kubernetes clusters.
- CI/CD Pipelines (Jenkins, GitHub Actions, GitLab Runners). Automating code deployments.
- Monitoring & Observability Tools (Datadog, Prometheus, ELK, CloudWatch). Keeping infrastructure performance in check.
- API Endpoints & Microservices. Exposing application functionalities.
Software assets depend on compute to run, networks to connect, and storage to retain data. Without IT asset management, they can introduce security gaps, performance issues, or unexpected failures.
4. Identity & Access Assets – The Underrated Security Risk
Nothing moves without identity & access assets. These aren’t physical or computational, but they define who and what can interact with your infrastructure. Unlike the other asset types, they don’t consume storage, compute, or networking — but they control everything that does.
Examples of Identity & Access Assets:
- AWS IAM Roles, Azure RBAC Policies, and Google IAM Service Accounts. Granting permissions to users and services.
- Federated Identity Providers (Okta, Azure AD, AWS SSO). Connecting on-prem identity with cloud authentication.
- Service Account Keys, SSH Keys, & API Tokens. Providing programmatic access.
- Multi-Factor Authentication (MFA) & Access Logs. Enhancing security controls.
These IT assets don’t process workloads or route traffic, but if misconfigured, they become the weakest security link. A single overprivileged IAM role can expose entire cloud environments to attack.
Every IT asset in your environment serves a different purpose. Compute assets run workloads, network assets route traffic, software assets execute logic, and identity assets control access.
Read also: IT Asset Management Process: 6 Workflow Steps You Can’t Ignore!
Why assets tracking is a must in 2025
Your cloud workloads are scaling, your on-prem systems are holding steady, and your software stack is evolving. But without IT asset tracking, you’re not running an infrastructure — you’re chasing ghosts. The bigger your hybrid multi-cloud environment, the harder it is to know what’s deployed, what’s consuming resources, and what’s quietly setting you up for security, compliance, or budget nightmares.
And trust me, I’m not just throwing worst-case scenarios at you. These are real-world ITAM insights straight from Cloudaware clients — enterprises running thousands of cloud accounts across AWS, Azure, and GCP, all while juggling on-prem legacy technology assets. When you oversee millions of IT assets, patterns start to emerge.
And those patterns? They tell a story of why tracking isn’t optional anymore — it’s survival.
1. The Ghost Assets: Costing You in the Shadows
You’re running a hybrid multi-cloud infrastructure. AWS, Azure, and GCP are all in play, and between autoscaling policies, temporary workloads, and on-the-fly provisioning, new IT assets are constantly being created.
Now, imagine running an audit and finding an EC2 instance that’s been sitting idle for months. Or a detached Azure managed disk still racking up storage costs. Or a Cloud SQL instance in GCP, configured for high availability, even though no one’s connected to it in weeks.
These orphaned assets aren’t just burning money. They could still have IAM roles attached, network access enabled, or outdated configurations that no one is monitoring. Untracked, they become both financial drains and security risks — a ticking time bomb in your operations.
2. Shadow IT: The Risk You Didn’t Approve
Not every IT asset in your environment was deployed by IT.
A finance team might spin up a SaaS solution, connecting it to live production data without telling anyone. A developer might test a personal Kubernetes cluster in a cloud sandbox and forget to delete it. A marketing department might buy a third-party data analytics tool and integrate it directly with customer records.
No approval. No compliance check. No visibility.
Shadow IT happens when teams move faster than IT governance, and without automated asset discovery and dependency mapping, these rogue assets stay invisible — until they cause a breach, a compliance violation, or an unexpected budget spike.
3. Software Rot: When Code Starts to Decay
Not all risks come from forgotten VMs or rogue applications. Some IT assets start clean but decay over time.
A containerized application running on OpenShift hasn’t been updated in over a year. An API gateway managing traffic between microservices is still running outdated TLS settings. A Lambda function is tied to IAM roles that no longer align with new security policies.
This is software rot — the slow, silent breakdown of stability and security. Without version control tracking and lifecycle monitoring, outdated assets accumulate until they cause failures, security gaps, or massive inefficiencies.
4. Compliance Audits: Scrambling Is Not a Strategy
You get a compliance audit request. They need proof of IT asset ownership and security controls. And suddenly, you’re scrambling — pulling reports from five different teams, cross-referencing spreadsheets, and hoping you haven’t missed anything.
Regulations like SOC 2, GDPR, and ISO 27001 don’t just require policies — they require proof. If your IT asset data is scattered, reporting is a nightmare. Without real-time IT asset tracking, you’re stuck manually compiling asset records across multiple cloud providers and systems — a process that’s slow, painful, and full of gaps.
5. IT Service Disruptions: When One Missing Asset Breaks Everything
Hybrid multi-cloud infrastructures are fragile in ways most teams don’t expect. A single forgotten asset can break an entire workflow.
- A cloud firewall rule that wasn’t updated? Blocked API traffic, taking down customer services.
- A deprecated Azure load balancer still handling requests? Slowed application performance, frustrating end users.
- A misconfigured Kubernetes ingress controller? Prevented auto-scaling, leading to outages under load.
Without IT asset tracking, you don’t know what’s active, what’s connected, or what’s waiting to fail. And when something does go down, troubleshooting takes longer because no one has a clear map of how IT assets interact.
The solution? Track everything. Monitor every asset, map every dependency, and automate what you can.
Because the cost of not knowing is always higher than the cost of tracking.
Achieve 100% visibility of your IT assets with Cloudaware
Your infrastructure is growing — across clouds, across accounts, across teams. Every day, new IT assets are spun up, modified, or forgotten. Some are running mission-critical workloads. Others? They’re silently accumulating costs, creating security gaps, or operating outside compliance.
You can’t manage what you can’t see. That’s why Cloudaware gives you complete, real-time visibility into every asset — where it lives, how it’s configured, and what’s changing.
How Cloudaware Puts You in Control
🚀 Automated Discovery. Map every IT asset across AWS, Azure, GCP, and on-prem. No blind spots.
🔎 CI Enrichment. Pull deep metadata to understand relationships, dependencies, and risks.
🏷 Tagging & Classification. Organize assets by function, cost, or compliance for smarter tracking.
⚡ Change Tracking. Get alerts on unauthorized modifications before they cause an incident.
🔄 Workflow Automation. Automate asset lifecycles, approval flows, and remediation.
🛡 Compliance & Security Monitoring. Ensure assets meet regulatory and internal security standards.
💰 Cost Optimization. Identify unused resources, control spending, and improve efficiency.
100% visibility. Zero guesswork.
