You ever chase a failed deployment across three clouds, only to realize the root cause was a forgotten S3 bucket tied to a stale IAM role... and no one even knew it was still in prod? Yeah. That’s what happens when your CMDB CIs are half-baked or missing entirely.
When your ITIL configuration items aren’t tracked, verified, or mapped, you’re not managing services — you’re guessing. And in a world of auto-scaling chaos, misfired pipelines, and compliance audits that hit harder than they should… guessing costs more than just time.
In this article, we’re breaking down exactly
- what a configuration item is,
- how it fits into your service architecture,
- why CI relationships matter,
- and what it actually takes to manage CIs across environmentsl without spreadsheets, without tribal knowledge, and without losing sleep over drift.
Let’s get into the details that keep your stack standing when everything else starts shaking.
What is Configuration Item
A Configuration Item (CI) — or in ITIL speak, an ITIL CI definition — is anything in your infrastructure that needs to be tracked, managed, or audited to deliver a service. That’s the core of configuration management: every component that could impact stability, cost, security, or compliance is a CI. If it has a lifecycle and can go sideways, it’s part of the CMDB CI universe.
You’ve probably worked with CIs more times than you’ve cursed at a broken deployment — they just weren’t labeled that way.
That EC2 instance running a backend job? CI.
The Kubernetes pod hosting your staging environment? CI.
That flaky Azure SQL database someone spun up for reporting and forgot about? CI.
Even the S3 bucket holding prod logs or the Terraform module managing IAM policies — all of them are configuration items.
Let’s look at CMDB CI meaning presented in practice
In a typical multi-cloud setup — think AWS, Azure, GCP, with a splash of legacy on-prem — you’re dealing with thousands of assets and configuration items spinning up and down daily. No spreadsheet or tribal knowledge can keep up with that kind of infrastructure chaos.
That’s where Cloudaware CMDB jumps in. It handles CI discovery via APIs, CloudTrail, Config, tags, and asset metadata. Each discovered asset becomes a managed CI with detailed attributes like Region, Owner, Compliance Status, Last Patch Date, plus relationship mapping to show what it’s connected to — like "uses", "hosted on", or "depends on". You get visibility into all CI types — cloud-native, custom, hybrid — and how they interact.
Ec2 image
This isn’t some shiny dashboard you slap on a status report. It’s the operational nerve center. Behind the scenes, it can auto-reboot an EC2 marked Unhealthy, kick off patching for Stale AMIs, or fire alerts the moment a Public S3 Bucket pops up where it shouldn’t — especially in restricted zones or non-compliant business units.
And the real win? You’re not wasting hours spelunking through AWS, Azure, and GCP consoles just to trace what broke. With smart CI discovery, clean relationships, and well-managed attributes in the CMDB, you’ve got the full picture — fast. So you can get back to scaling uptime, hardening routes, or tweaking lifecycle hooks like a boss.
Read also: IT Asset Management Process: 6 Workflow Steps You Can’t Ignore!
Don’t mix it up with IT asset 👇
Configuration item vs Asset
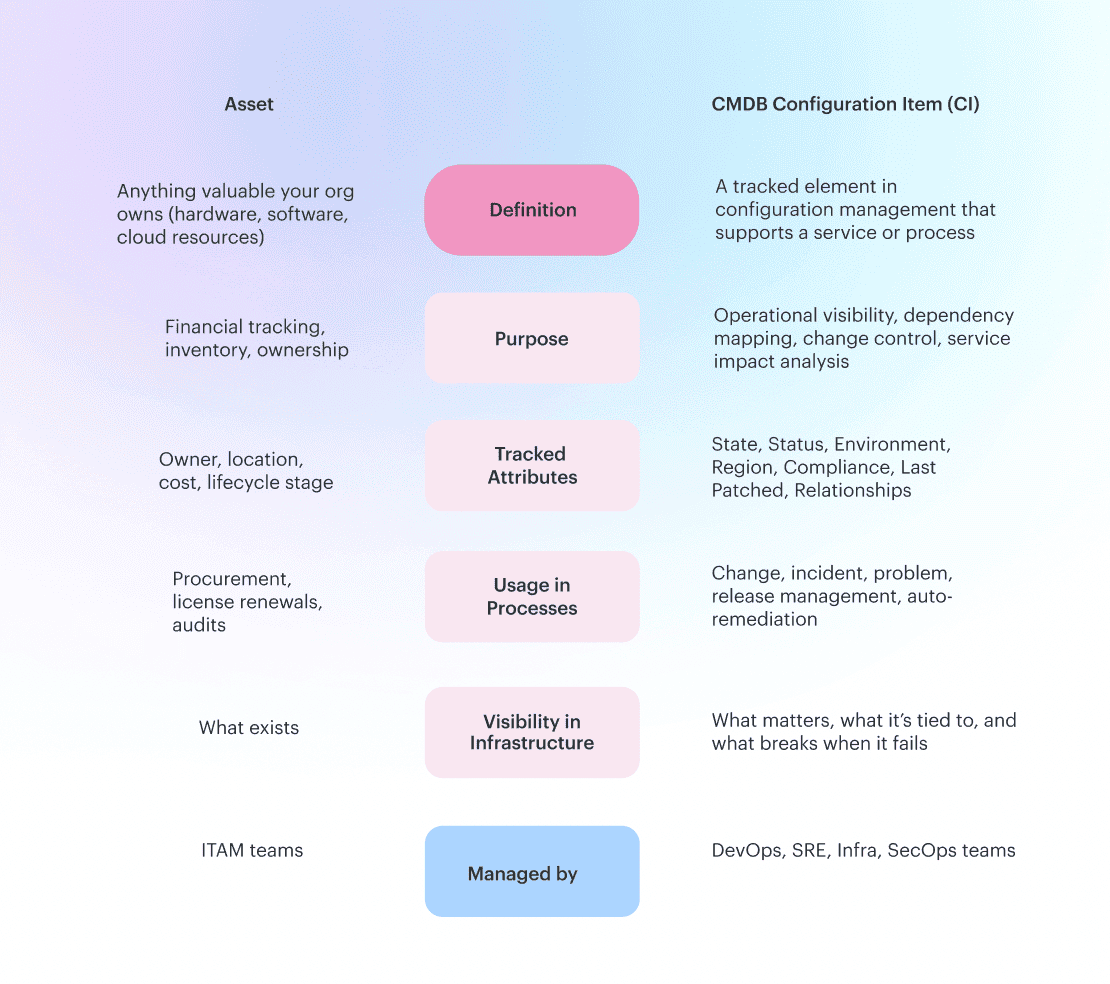
Here’s the tea on configuration item vs asset — because yes, they overlap, but they don’t walk the same beat.
In configuration management, an asset is something you own — like that GCP project or your fleet of EC2s. But once it’s being tracked for impact, tied to a service, monitored for change, and plugged into a process like incident or change management? It becomes a CMDB configuration item.
So that prod-db-03 EC2 running customer billing? That’s not just an asset. It’s a CI, fully managed in the CMDB with mapped dependencies, attributes like AMI ID, Patch Status, Environment, and linked to processes like Backup Validation or Disaster Recovery.
In big, tangled infrastructure, the CMDB helps you see which configuration items matter most to uptime, compliance, and cost. Assets show ownership. CIs show accountability. And friend, when something goes sideways, you’ll want that clarity.
Read also: Key Differences CMDB Vs Asset Management (ITAM): Why You Need Both
Top 5 reasons why CMDB and CI management matter
CI management isn’t just another checkbox in your ops workflow. When you’re juggling hundreds of services across clouds, regions, and teams, the difference between a documented CMDB CI and an invisible one can be the difference between smooth ops… and a 2 a.m. wake-up call.
We’ve seen it firsthand at Cloudaware — teams trying to scale without configuration management end up chasing ghosts across their infrastructure. No context, no traceability, and way too many surprise failures.
But when your configuration items are properly discovered, mapped, and managed in the CMDB?
Everything changes. Automation gets smarter. Change risk drops. Compliance becomes routine. Here are five battle-tested reasons why tracking CIs in your CMDB isn’t optional — it’s the backbone of a stable, scalable cloud operation:
1️⃣ You always know what’s running — and why
Organizations waste up to 30% of cloud spend on unused or forgotten infrastructure assets. One Cloudaware customer found over 200 orphaned EBS volumes and idle NAT gateways across 40+ AWS accounts.
By tracking configuration items — aka CIs in IT — in the CMDB, they exposed the waste. Everything was documented, managed, and either optimized or decommissioned.
That cleanup saved them $38K every quarter.
2️⃣ Faster incident response, fewer escalations
IT downtime costs $5,600 per minute on average (Gartner). One Cloudaware client hit a wave of 500s after a Load Balancer started misrouting to a flaky Nginx pod. With complete CI discovery and relationship mapping, the CMDB CI setup showed exactly how the pieces connected — from Route 53 to ASG to the app node.
The team had full configuration management context and restored service in minutes — without escalation.
3️⃣ Scoped, safe, and surgical changes
70% of outages come from poorly planned changes (Uptime Institute). A fintech client uses CI tracking to analyze change risk before every Terraform plan. They rely on CI attributes — like Environment, Patch Status, and Service Owner — plus CI relationships to scope every deployment.
Every affected configuration item is managed and accounted for. Changes hit only where they’re supposed to, with no blast radius surprises.
5️⃣ Automation that doesn’t shoot in the dark
A SaaS customer had remediation playbooks firing on Unhealthy CIs, but stale or misclassified data caused automation to hit the wrong environments. After realigning their CMDB CI structure and standardizing attributes like Environment and Last Updated, their CI automation started behaving. Now, only production workloads are touched.
Dev and test environments? Left alone.
This is how CI CMDB data fuels real, safe automation across hybrid infrastructure.
5️⃣ Compliance and audits on autopilot
In regulated environments, configuration management isn’t optional — it’s survival. A Cloudaware banking client tracks all their EU-based EC2s in the CMDB, with CIs marked CIS Level 1: Passed, Encryption: true, and Last Patched < 30 days.
These aren’t just assets — they're verified, mapped, and managed configuration items. What once took three weeks of audit prep is now a live dashboard. Always ready. No spreadsheets. Just real-time trust in your data.
Read also: Expert Review of Top 10 It Inventory Management Software For 2025
TOP 5 Examples of Configuration Items Types
Not all cis are built the same. Some run production workloads. Others quietly control access or configurations behind the scenes. And a few? They’re just floating around, untagged, until something breaks and you’re stuck figuring out what the hell it even was.
That’s why knowing your configuration item types is everything. Each one tells a different story — of ownership, risk, automation potential. And when they're all discovered, mapped, and managed in your CMDB, they stop being noise and start becoming control.
1. Infrastructure CIs
These are the backbone. Think EC2, AKS node groups, Load Balancers, VMs, and those ancient on-prem Hyper-V machines no one dares decommission. They're high-volume, high-impact, and always at the center of uptime conversations.
We had a client with hundreds of untagged prd-* instances that weren’t showing up in their Patch Management flows. Turned out the tagging was inconsistent. But since Cloudaware auto-discovers CIs by config, not just tags, the CMDB CI view exposed them all — along with Region, AMI ID, and Compliance Status. Problem solved. Cost controlled.
2. Application CIs
These include deployed workloads — Lambda Functions, ECS Services, App Services, K8s Deployments. They’re classic ITS CIs, directly tied to user-facing features.
We helped a team trace user latency back to svc-login-v1-lambda. Looked clean in the logs — until the CMDB CI relationships showed a degraded connection to redis-cache-dev. With clean mapping of dependencies, the team locked in the root cause in one glance.
3. Network CIs
These get overlooked often, but misconfigured assets like sg-open-ssh-prod, vpc-mgmt-core, or nacl-deny-all can bring everything down.
One client had a port left open — again. Once these were defined as configuration items in Cloudaware’s CMDB, they used relationship mapping to show exactly what that rule touched. Alerts kicked off a Change Management process before anything hit prod.
4. Policy & Configuration CIs
IAM roles, S3 bucket policies, SSM docs, Org-level controls. These aren’t flashy, but they determine who can launch, read, write, delete, or escalate.
In one GDPR audit, a client spotted a risky bucket-client-data-prod with public ACLs wide open. Since it was defined as a configuration item with linked attributes, the CMDB auto-kicked a Jira ticket, pushed the policy update to Git, and documented the whole flow.
This wasn’t just asset tracking. It was full lifecycle management of a critical security control — start to finish.
5. Software & Package CIs
This CI type includes Apache, OpenSSL, log4j-core, and other libraries or agents living inside your stack. Think of them as deeply embedded configuration items that come into play during any security event.
When Log4Shell dropped, a client used Cloudaware’s CMDB to pull every log4j version and location across 4,000+ nodes. These configuration items examples were already tracked by version, owner, and install path. Instead of starting from scratch, they just filtered the CI table. Targeted, fast, and 100% traceable.
Read also: 15 Software Asset Management Tools: Features & Pricing Compared
Each of these CI types plays a different role — but once they’re properly discovered, mapped, and managed in your CMDB, they shift from chaos to clarity. You’re no longer guessing which asset is causing the incident or what policy change broke the app.
You’re tracking your full infrastructure, understanding CI relationships, and letting your configuration management system power real workflows — ITSM CI insights, automation triggers, compliance dashboards, and proactive controls.
This isn’t just “nice to have.” It’s how modern teams get ahead of issues before they even surface. And the CMDB? It’s not just a repository. It’s your context layer for everything that moves.
CI Attributes: The Key to Smarter Configuration Management
At its core, a CI attribute is a specific piece of data that defines or describes a configuration item. It’s what turns a generic cloud resource into something meaningful you can actually manage, automate, and troubleshoot. Think of CI attributes as the vital signs of your infrastructure — without them, your CMDB is just a catalog of names and vibes.
Basic CI attributes & what they tell you
- CI Name – The unique identifier (like
ci-prod-db-usw2-rds01) so you know exactly what you’re looking at. - CI Type – Is it a
VM,Database,IAM Role,K8s Pod, orSecurity Group? This tells the CMDB how to treat it. - Environment – Flags if it’s in
prod,stage,test, orsandbox— so you don’t accidentally nuke production. - Owner – Who’s responsible for this CI? Critical for approvals, escalations, and cost accountability.
- Patch Status – Tells you if the resource is current, outdated, or non-compliant with security baselines.
- Region & Account ID – Where it lives and which cloud it belongs to — especially useful in multi-account chaos.
- Compliance Status – Whether the CI aligns with frameworks like CIS, HIPAA, ISO.
- Created Date – Great for lifecycle tracking and identifying long-forgotten zombies.
- Tags – Business, cost center, app name, team — these help with reporting and filtering.
These are just the starters. Depending on the CI type, you might also track Service Tier, Backup Enabled, AMI ID, CPU Util, Instance State, or Encryption Status.
Now let’s bring it to life.
Let’s say we’re looking at an RDS instance: ci-db-prod-usw2-rds01.
Once Cloudaware discovers it, the CI in CMDB doesn’t just say “yep, it exists.” It records dozens of CI elements that give you real-world insight into how this thing fits into your environment.
When those attributes are clean, you can slice, filter, and automate with precision. We had one customer flag every Patch Status: outdated EC2 across prod with Owner: null. That single query pulled in 300+ neglected CIs. They rolled it into their Patch Management flow — no manual audit needed.
And we’re not just talking isolated fields.
Your CMDB also builds relationship attributes — so you don’t just know what a CI is, but what it’s connected to.
That same ci-db-prod-usw2-rds01 might be tied to:
- A
Node.js appCI - A
Redis clusterCI - A
Security GroupCI with custom ingress rules - A
CloudWatch alarmCI with no notification target
Put that together, and you’re not just looking at a list of disconnected resources — you’re seeing how your configuration items operate in context. You know what talks to what, what breaks when something fails, and who’s responsible for cleaning it up.
But here’s the thing: it only works if your CI attributes stay accurate, complete, and aligned across your CMDB. And that takes more than auto-discovery. It takes intentional, ongoing management.
So how do you keep your CI data clean when you’ve got thousands of moving parts across clouds, teams, and tools? Let’s break down how smart teams stay ahead of the drift — and keep their CMDB as useful on day 300 as it was on day one.
How to Manage CI Attributes (Straight from a Real-World Pro)
Theory is great. But when you’re juggling thousands of CIs, pushing changes in prod, and prepping for yet another compliance check, you don’t want generic advice — you want battle-tested instruction from someone who lives this.
1️⃣ Know Your Attribute Sources
Me: Let’s start simple — how do you know which attributes to trust?
Daria: First rule: own the source. Every CI in CMDB needs to have traceable origins. Some attributes come from cloud-native tools like AWS Config or Azure Resource Graph. Others, like Business Unit, Data Classification, or Service Tier, usually need enrichment — pulled from external systems or mapped via rules.
For every attribute, I ask: Where is this coming from? Is it API-discovered, mapped, or manually entered?
That’s how we separate reliable CI data from risky guesses.
2️⃣ Normalize and Enrich Your CI Attributes
Me: What do you do when half the fields are blank or messy?
Daria: Classic hybrid mess. That’s where normalization kicks in. I use rules based on OU, VPC, Subnet, and Account ID to enrich missing fields. Example: if ci-vm-hr-payroll-01 sits in the HR OU, we assign:
Environment = prodBusiness Unit = HRCompliance Status = high
That logic lives in the CMDB attribute management policy, not someone’s head.
We also use fallback tagging strategies to bring in missing context across CIs — cloud, on-prem, wherever.
3️⃣ Keep It Fresh With Aging Rules
Me: So how do you keep it from going stale?
Daria: We run a weekly CI aging report. If a CI’s Last Updated is older than 30 days, it gets flagged. Especially for sensitive CI types like IAM Roles, K8s Pods, or External-facing EC2s.
Bonus tip: we use relationship attributes to detect mismatches. If a Web App CI says App: marketing, but its DB dependency says App: finance, something’s off. And it’s usually a misconfigured relationship map, not a human error.
4️⃣ Standardize the Schema Across Tags
Me: Let’s talk about the tagging chaos.
Daria: Don’t get me started — env=prod, ENVIRONMENT=production, enviroment=prd... I’ve seen it all. That’s why we created a CI attribute mapping policy in our CMDB. It translates every external tag into a clean internal schema.
So no matter how bad the input is, the output always lands as Environment = prod. We also define required fields per CI type — if a new RDS instance is missing Owner, Cost Center, or Data Sensitivity, it won’t pass validation. It’s incomplete. Period.
5️⃣ Integrate with ITSM for Context-Driven Ops
Me: How does all this tie into real workflows?
Daria: This is where CI in ITIL gets real. We use our CMDB to feed Incident, Change, and Problem Management processes with clean, contextual CI data.
Picture a Change Request for ci-app-checkout-v2. The approver instantly sees:
- It’s in
prod - Owned by
Team Web - Depends on
ci-db-payments-prod - Is tagged
Compliance: critical - Has open CVEs
That’s not just helpful — it’s the reason approvals don’t stall and rollbacks don’t explode.
Read also: The best configuration management software: Top 10 tools review
Understanding Relationships Between Configuration Items
You can track all the CIs in your CMDB, tag them like a pro, automate your patching flow, and still miss the big picture if you don’t understand how those CIs actually relate to each other. And that’s when stuff breaks.
I’ve seen teams restart ci-app-frontend-prod because CPU spiked, only to realize later it was throttling because the ci-db-prod-rds01 had hit a connection limit. The app was never the problem. The relationship was.
So yeah — knowing your CI attributes is one thing. But knowing how your configuration items are linked? That’s where real operational clarity starts. It's what turns your CMDB from a directory into a decision-making engine.
Let’s break down the core relationship types I’ve seen used (and abused) across hybrid environments, so you can tighten your configuration management game and finally stop guessing what breaks what.
1. Depends On / Supports
This is your upstream/downstream relationship. One CI leans on another to function.
ci-app-checkout-v2depends onci-db-payments-prod- That
RDSCI supports the checkout service
In ITSM CI workflows, this is gold. When the database goes down, you don’t just fix the DB — you notify the app team before Slack melts.
2. Hosted On / Runs On
This one’s critical when you're working with compute or containerized workloads.
ci-jenkins-mainruns onci-ec2-pipeline-node-02K8s deployment-ci-user-serviceis hosted oneks-nodegroup-dev-eu-west-1a
This matters when ASGs scale in, or a node fails in a zonal outage. If you don’t track what’s running where, your rollback plan’s toast before it starts.
3. Secured By / Monitored By
These are your control plane relationships.
ci-s3-logs-prodsecured byiam-role-archive-access-onlyci-web-api-v1monitored bycloudwatch-alarm-latency-spike
One of our clients found out their most sensitive assets weren’t connected to any WAF or security config. Thanks to discovery and mapping, the gaps showed up clearly, and remediation didn’t wait for a red flag alert.
4. Part Of / Aggregates
These model logical groupings or service bundles.
ci-api-auth,ci-api-profile, andci-api-sessionare part of theci-service-user-management- Multiple IAM roles are aggregated into a compliance control group
This is where knowing what a CI is tied to helps streamline change approvals and reduce unintended impact during rollout.
5. Connects To
This one’s all about data flow and network paths.
- A public Application CI connects to
ci-db-reader-replica ci-api-gateway-euconnects toci-lambda-processor-v1
One client used this to trace latency from edge to origin. The relationship mapping revealed a rogue route across regions, costing both performance and budget. Fixed in hours once the full chain was visible.
When CIs live in isolation, you're left playing detective every time something breaks. But when your CI CMDB captures the real relationships between configuration items, based on smart types, tags, and cross-cloud context — you finally start seeing your system as it really works.
That’s the difference between managing configs and mastering service architecture. And if you ask any architect who’s lived through a 3 a.m. outage without a relationship map, they’ll tell you — never again.
5 Expert advice on how to manage CMDB CIs
It’s one thing to understand what a CI is. It’s another thing entirely to manage it at scale — across clouds, regions, teams, and tools.
The truth? Most CMDBs fall apart not because of bad intent, but because they rely on manual upkeep, loose tagging, or shallow discovery. And when you're dealing with thousands of dynamic configuration items, that just doesn’t cut it.
That’s why we asked our internal Cloudaware pros — the folks who’ve seen it all in customer environments — to drop their non-generic, deeply practical tactics for managing CIs. These are the moves that keep your CI in CMDB usable, trusted, and genuinely operational.
Not theory. Not buzzwords. Just five real strategies that actually work in production — built for teams that care about clean data, fast decisions, and tight relationships between the things that matter most.
Recover Attributes Automatically from Cloud Logs
Mikhail Malamud, our GM
Make CI Relationships a Guardrail, Not a Diagram
Technical Account Manager Iurii Khokhriakov:
Assign a Real-Time Risk Score to Every CI
Create Composite CIs for Logical Service Views
Anna, ITAM expert
Use Daily Tag-Scoped CI Inconsistency Reports
Kristina S., Senior Technical Account Manager at Cloudaware
Discover and Visualize CI Relationships with Cloudaware
Цhen something breaks in prod, it’s rarely just one thing. It’s a ripple. And if you don’t see how your CIs are connected, you’re chasing symptoms instead of fixing the root.
That’s why teams at places like Coca-Cola and NASA use Cloudaware CMDB — not just to track configuration items, but to understand them in context. Coca-Cola streamlined governance across hundreds of AWS accounts. NASA uses Cloudaware to stay audit-ready across both cloud and on-prem.
And every team using it? Gets one thing fast: all the data about CI data - its vulnerabilities, change history, cost, security, compliance, etc.
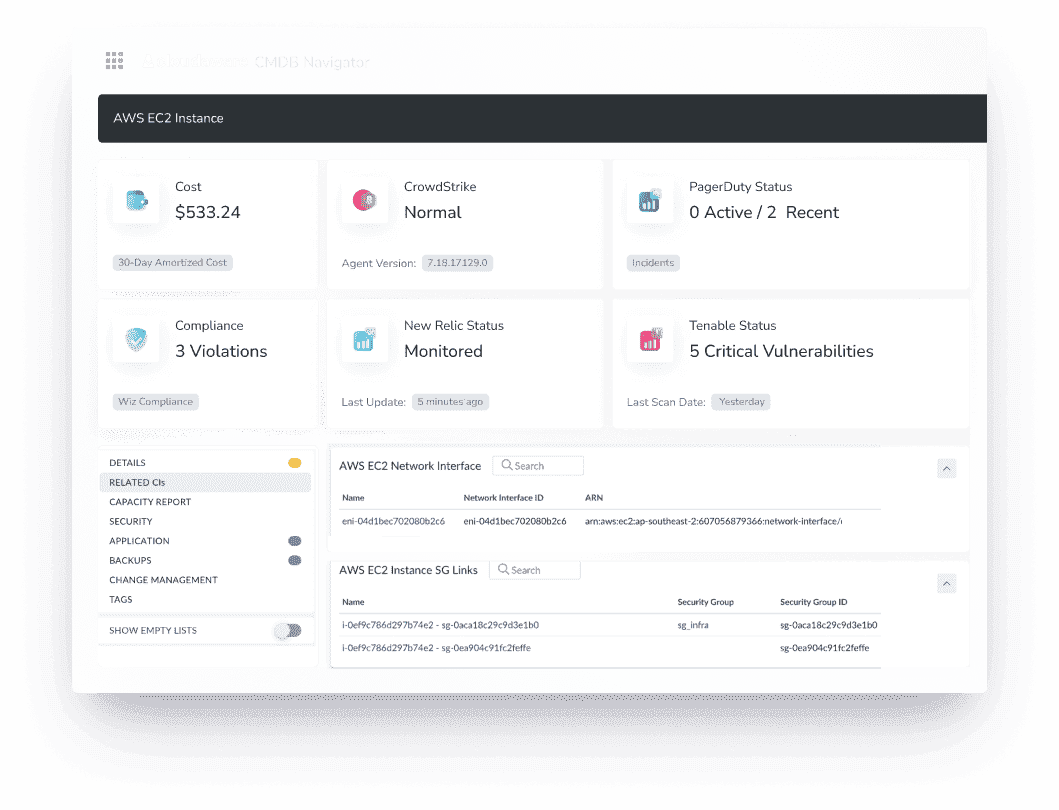
One customer spotted a slowdown between their app and database by looking at the CI relationship map — not their monitoring dashboard. Another caught a misconfigured IAM policy before deployment, because the CI in CMDB flagged a broken dependency right in the pipeline review.
With Cloudaware, every CI is automatically discovered, enriched with clean attributes, and mapped to show how it really fits into your stack — across environments, accounts, and providers.
What you get (out of the box):
- Multi-cloud and hybrid CI discovery
- Real-time mapping of relationships across all CI types
- Full-stack views with composite application CIs
- Auto-tagging and ownership detection with metadata-based attributes
- Impact visualizations for incidents, changes, and drift
- Support for CI ITIL and configuration item ITIL tracking
- Seamless CMDB management and tight integration with ITSM workflows
- Visibility into even the messiest legacy assets
You don’t need another inventory. You need a CMDB that works like your team does — fast, visual, and built to scale.
FAQs
What’s the difference between a configuration item and an asset?
An asset is typically tracked for ownership, procurement, and financial purposes. A CI, on the other hand, is tracked for operational context.
Here’s the difference: a VM might be an asset in your ITAM tool, but when that same VM is tied to a production app, tagged with a Compliance: High flag, and monitored for patch drift — it becomes a CI in your CMDB.
Assets are about “what you have.” CIs are about “how it’s working, who it affects, and what could go wrong.”
What is a configuration item in ITIL?
A configuration item in ITIL is any component that needs to be managed in order to deliver an IT service. ITIL treats CIs as the backbone of configuration management — because if you can’t track what supports a service, you can’t manage change, fix incidents, or pass an audit.
Cloudaware supports CI ITIL practices by automatically discovering, categorizing, and tracking CIs across environments — cloud, on-prem, and hybrid.
How are CIs discovered in a CMDB?
In Cloudaware, discovery happens via real-time integrations with cloud APIs (AWS, Azure, GCP), plus agentless syncs with tools like CloudTrail, AWS Config, Azure Resource Graph, vCenter, and more.
You don’t need manual imports or spreadsheets. CIs get pulled in with full metadata — region, resource ID, platform, tags, last modified date — and mapped automatically using prebuilt logic or your own custom rules.
Can custom attributes be added to CIs?
Absolutely. You can define and manage custom attributes per CI type — whether it’s Business Owner, Data Classification, RTO Tier, or anything your security or audit teams care about.
Cloudaware lets you use calculated fields too. So you can create logic like: “If Patch Status = Outdated AND Environment = Prod → Risk Score = High” This gives you way more than static data — it gives you context you can act on.
How often should CI data be updated?
As often as your environment changes — which, let’s be real, means constantly.
In Cloudaware, updates run continuously via API polling and event-driven triggers. So if a tag is removed, a role is rotated, or a resource is recreated in a different region, your CMDB reflects it in near real time.
We also recommend running scheduled data quality reports — weekly at a minimum — for verifying stale attributes or relationship drift.
How do CI relationships impact service management?
CI relationships are everything. They show which app relies on which DB, which policy controls access, and what fails when something else goes down.
Without mapped relationships, your CMDB is just a list of parts. With them, you can do impact analysis, route incidents, approve changes faster, and trace root cause like a pro.
Cloudaware builds and maintains relationship maps automatically, so you know exactly how your infrastructure is stitched together — across clouds and services.
What are configuration items?
A configuration item, or CI, is basically anything in your environment that’s worth keeping an eye on — because it can impact how your systems run. That might be an EC2 instance, a Kubernetes node, an IAM role, an RDS cluster, a VPN gateway... or yeah, even that forgotten S3 bucket someone spun up during a sprint and never tagged.
If it can affect uptime, security, cost, or compliance? It’s a CI. And the moment you map it in your CMDB, you stop treating it like a black box and start managing it like part of your system.
What is the role of CI verification?
CI verification is your reality check. It’s how you make sure what’s in your CMDB isn’t just technically there — but actually right.
We’re talking about things like: does this CI have an owner? Is the environment field filled in? Is it still active? Does it have valid relationships mapped? If that info’s missing or stale, good luck running clean automation or making smart decisions.
