Ever feel like you’re putting out fires all day instead of actually managing your IT operations? When you’re juggling thousands of accounts, servers, and a hybrid infrastructure across multiple clouds, it’s easy for chaos to creep in. Misplaced dependencies between IT assets, untracked applications, and "surprise" downtime become the norm. And let’s not forget those frantic moments when you’re asked to identify the root cause of an issue yesterday.
A lack of clear visibility into the relationships between IT assets creates operational inefficiencies, turns compliance audits into nightmares, and leaves you guessing when it comes to troubleshooting.
That’s where CMDB application mapping steps in to save the day. By visually connecting applications to their dependencies, it delivers crystal-clear insights into your IT ecosystem, making it easier to troubleshoot, optimize, and scale with confidence.
In this article, we’ll explore CMDB application examples, dive into CMDB application mapping best practices, and share actionable strategies to tame your IT environment.
First, let’s check if we’re on the same page about the theory 👇
What is CMDB application mapping?
At its core, CMDB application mapping is the process of linking your configuration items (CIs) to the applications running on them. This connection lives in your configuration management database, giving you a clear view of how everything in your IT environment is related.
Think of it like drawing a map that shows how your servers, applications, databases, and network components are connected and how they depend on each other. With this in place, you can spot issues before they escalate, optimize resources, and manage risk more effectively.
How Does It Work?
Let’s break it down with an example that might look familiar to you. Imagine a custom business application running on a virtual machine (VM). That VM is supported by an NGINX web server farm running on Kubernetes, and the app's data is stored in a MySQL database installed on a dedicated server.
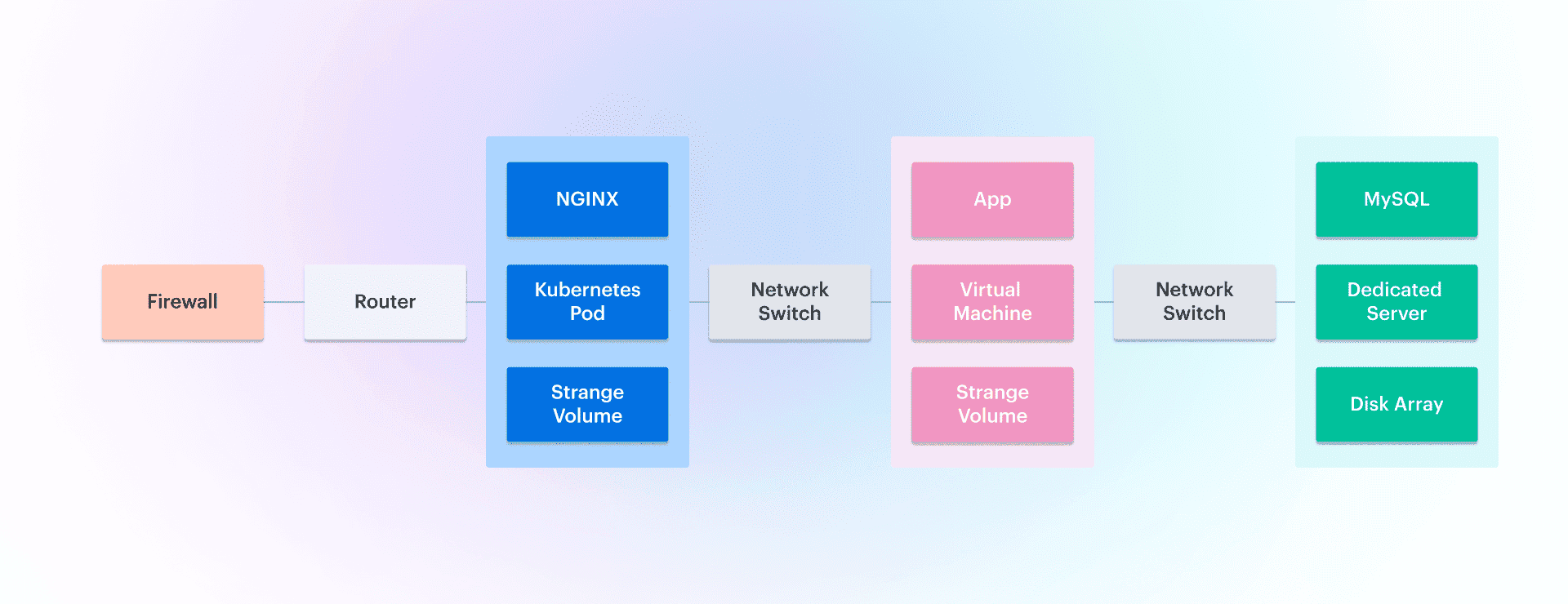
This is your environment — a mix of physical, virtual, and cloud-based components all working together.
With CMDB application mapping, each of these components is discovered and connected:
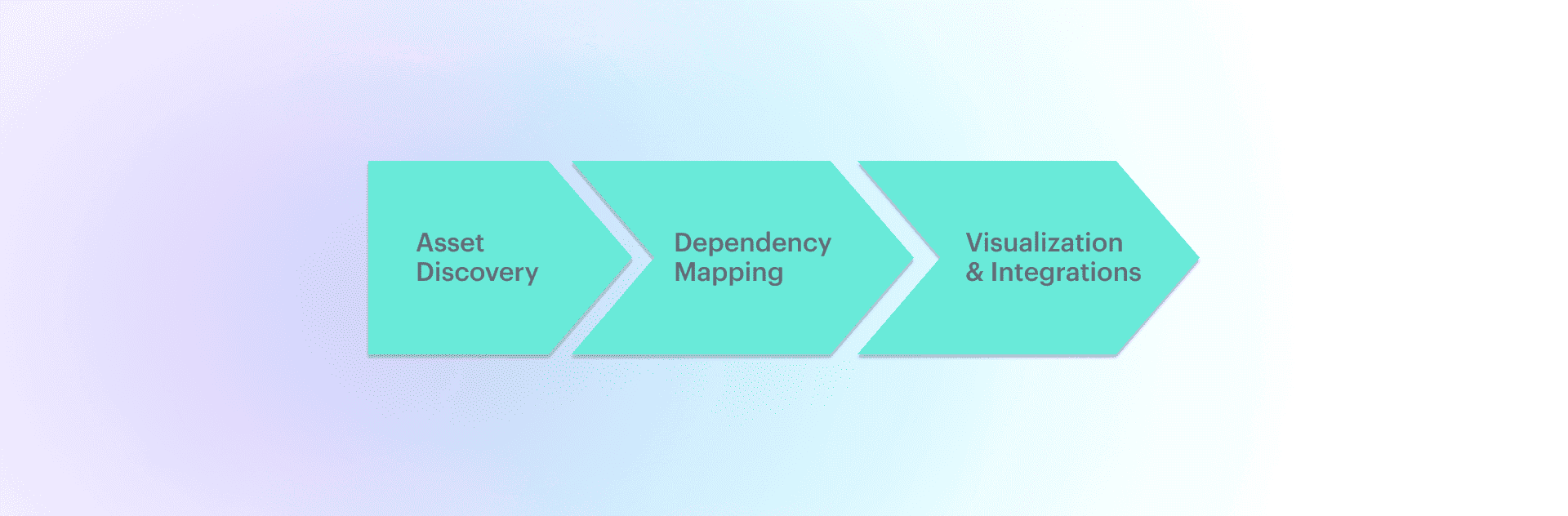
- First, your tool discovers all the CIs in your environment, like VMs, operating systems, middleware, databases, and servers. This is like taking an inventory of your IT ecosystem.
- Then, the tool identifies how these components are related — say, which virtual machine is running which application, or which server is hosting the database. It does this by monitoring things like communication flows (TCP/UDP) between endpoints. It’s like drawing lines between related pieces of your IT puzzle.
- Once everything is discovered and mapped, you can see all the dependencies between systems elements in a dashboard or import them into other tools for tasks like vulnerability assessments or configuration management. It's like opening a clear, interactive map of your entire infrastructure.
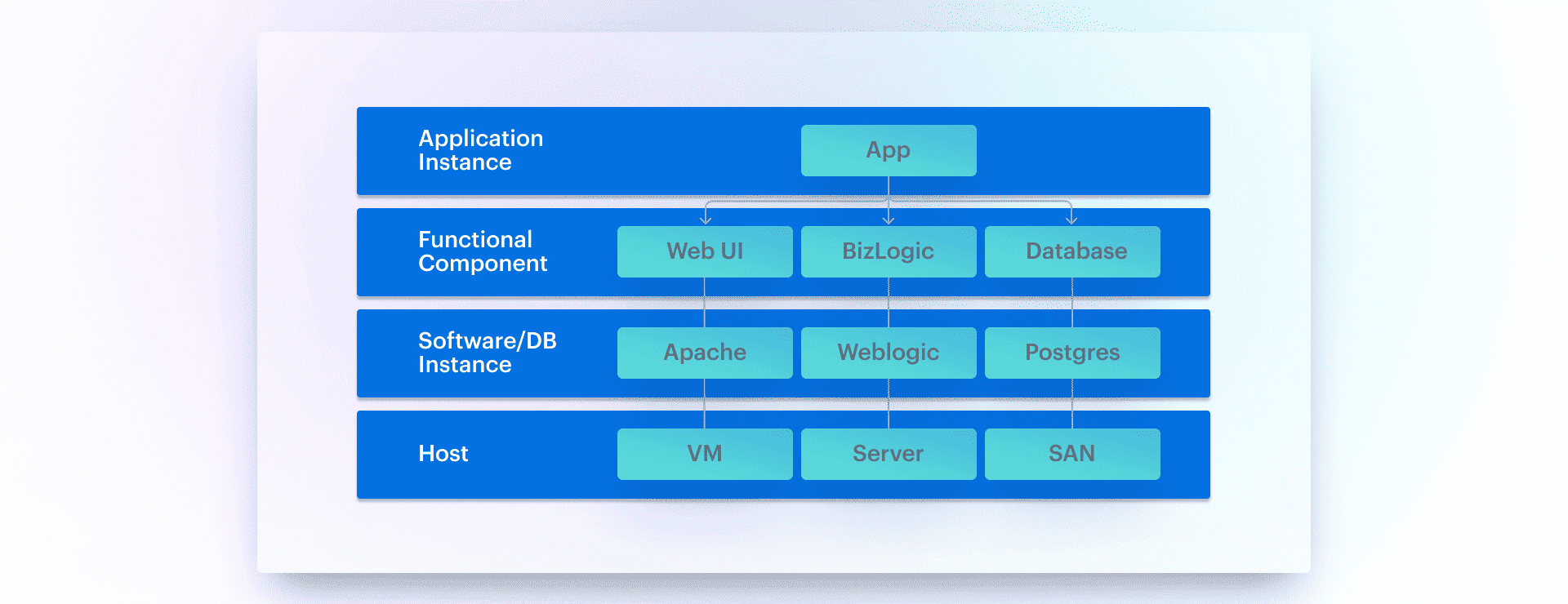
Elements of CMDB Application Mapping
CMDB application mapping covers several key components in your IT environment:
- Physical Infrastructure. Servers, switches, routers, firewalls — basically the hardware powering your network.
- Virtual Infrastructure. Virtual machines, operating systems, hypervisors, and middleware. These are your software-based building blocks.
- Data Components. Databases and storage systems that hold all your valuable data.
- Services. These include services that are dependent on or powered by your applications and data.
By organizing these components and their relationships into a hierarchy or other formats (think mind maps, flow diagrams), you create a clear, visual mapping that helps you understand how everything connects.
Surely, it differs in every CMDB software, but the key principle is like this:
Why does it vital for your business in 2025?
By 2025, the ability to map applications and infrastructure efficiently is no longer a “nice-to-have”. It’s a must. Here’s why:
- Pinpointing Dependencies between CIs. In hybrid environments, they can get a little... messy. Without a solid CMDB application mapping, trying to figure out what’s connected to what is like trying to clean a junk drawer.
You know the one – it’s full of random stuff, but it’s impossible to find what you actually need when you’re in a pinch. But with proper mapping? You can instantly see how everything’s linked together. No more wasted time hunting down what’s broken or why something’s not working.
Look at Coca-Cola — they’ve been able to significantly improve how they identify and manage dependencies between elements of their infrastructure. With Cloudaware’s mapping, they avoid those “wait, what’s actually connected to what?” moments, keeping their systems running smoothly and preventing downtime from being an issue. - Faster Incident Response. The faster you can identify the issue and fix it, the less impact it’ll have on your users or customers. Cloud-aware organizations that use automated configuration-based discovery are 30% quicker at identifying and resolving issues — imagine how much smoother your day would be if you had that kind of edge.
Take Charles Schwab. They were able to cut down their incident resolution times significantly by using Cloudaware’s CMDB mapping. This isn’t just a “nice-to-have”; in a fast-paced business, speed like that can be a game changer. - Cost Savings. No one likes wasting money, especially when it comes to cloud and on-prem resources. The trouble is, if you don’t have visibility into your IT assets, it’s way too easy to let those underutilized servers and applications keep racking up costs. But with CMDB application mapping, you get the full picture. You can identify exactly where resources are being underused and optimize your infrastructure to cut out the waste.
NASA, for example, used Cloudaware’s CMDB to get a clearer view of their resources, cutting unnecessary costs. It’s like finding out that you’ve been paying for a gym membership you haven’t used in months — once you see it, you can make a change. They saved big by fine-tuning their resource allocation. - Compliance Readiness. As cloud environments expand, so do regulations. Keeping up with that can feel like trying to juggle while riding a unicycle. But with CMDB application mapping (especially the kind that’s configuration-based and agentless), it becomes a lot less chaotic. Real-time visibility into your IT assets means you’re always prepared for audits, and you won’t be scrambling at the last minute.
ServiceChannel nailed this by adopting Cloudaware’s CMDB application mapping. They were able to keep everything in check and reduce audit-related headaches. When the regulators come knocking, they’re ready — no more scrambling for paperwork or scrambling for answers. - Scalability. Whether you’re managing a handful of servers or thousands, scalable application mapping helps you stay on top of your infrastructure as it grows. Think of it like setting up your organization with a system that evolves with your needs. You don’t want to start with a blueprint for 10 servers and end up drowning in a sea of chaos as you scale.
So, why’s it vital for your business in 2025? Simple: without CMDB, you risk falling behind in a landscape where speed, efficiency, and compliance aren’t just important — they’re the foundation of success.
Use cases for CMDB application mapping
There are five key purposes of configuration that directly align with CMDB application mapping. Here's how you can apply them:
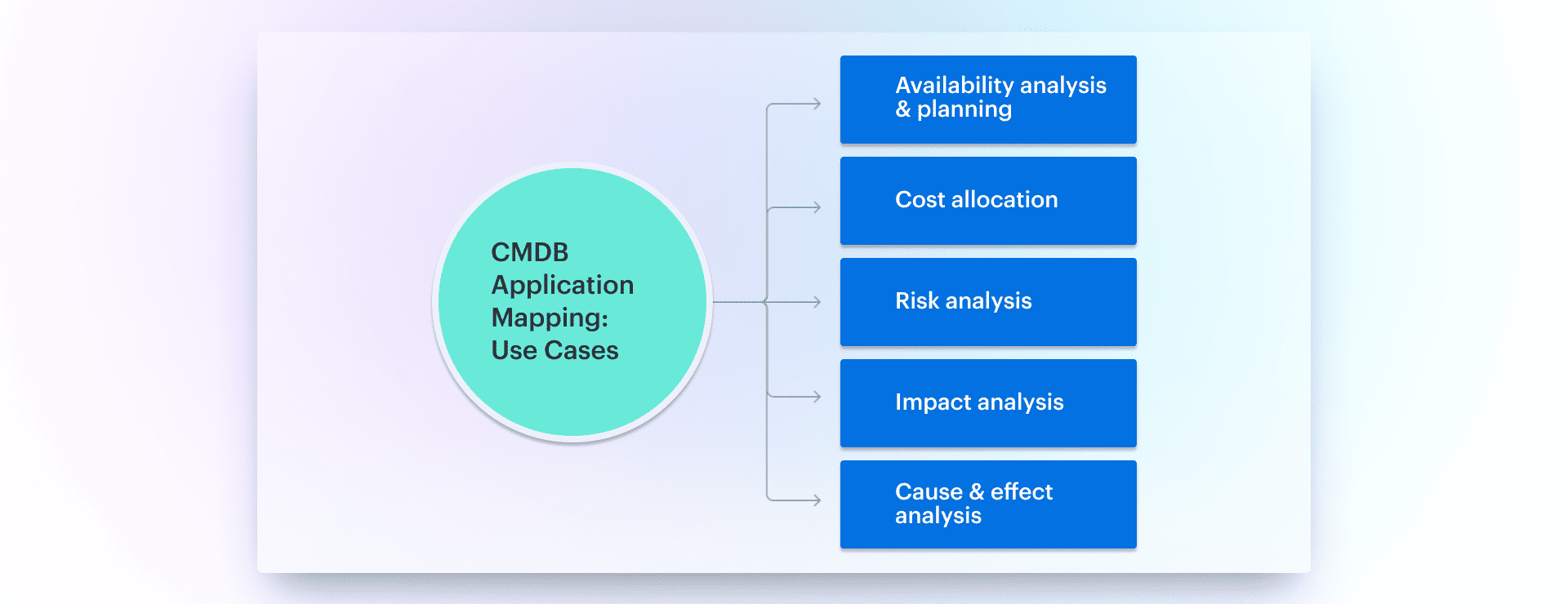
Analyze and Plan for Availability
Imagine you’re in the middle of a critical service outage. The team is scrambling, everyone’s pointing fingers, and the clock is ticking. Now, picture this: you pull up your CMDB application map and, boom, you immediately see the single point of failure that caused the issue.
No more running around in the dark — this mapping lets you pinpoint exactly where things went wrong.
This use case is all about ensuring that your applications are available when your users need them. By leveraging your CMDB application map, you can:
- Pinpoint causes of unavailability. See which specific application or component is causing issues.
- Identify critical components. Locate the dependencies between assets that, if they go down, will bring the whole system with them. You can then prioritize fixing or duplicating those components to avoid future outages.
For example, in a scenario where a large financial institution had an application go down during peak trading hours, their CMDB application mapping showed them that a single server in the backend was responsible for handling 80% of the data requests.
With this insight, they implemented redundancy around that server, ensuring that a failure wouldn’t impact operations again.
Cost Allocation
Alright, let’s talk money. When it comes to IT budgets, everyone’s always trying to justify the spend. But how do you prove where the money should go or where you can cut back? The answer is your CMDB application map. By visualizing the relationships between applications and infrastructure, you get a clear picture of where costs are stacking up.
- Tracking costs. Want to see where your resources are being used the most? The CMDB application map helps you track how much is spent on each application and what components are consuming the most resources.
- Optimizing spending. The map lets you identify underutilized or over-provisioned assets. If you’ve got a bunch of expensive cloud servers running 24/7 but your application only uses them a few hours per day, you’ll know where to optimize.
Take the case of a large e-commerce platform — by using the discovery tools within their CMDB, they found out that a substantial chunk of their cloud services were being underutilized during off-peak hours. By resizing their infrastructure to fit actual usage, they saved a ton of cash without compromising performance.
Identifying Vulnerabilities
Let’s face it — no one likes to talk about risk, but everyone wants to avoid it. Risk analysis is crucial to keeping your business safe and secure, and CMDB application mapping is your best friend when it comes to identifying those risks.
- Identify vulnerabilities. View of your entire infrastructure and spot weak points that could be vulnerable to attacks or failures.
- Determine threat factors. Trace how different services and applications interact and assess potential risks at each layer of your infrastructure. If one component fails, what’s the ripple effect across the system?
For example, a healthcare organization used CMDB application mapping to identify a critical vulnerability in their patient management system. They found out that a single outdated database was exposed to the internet, which could potentially compromise patient data. With this info from their CMDB application mapping, they patched the issue before it turned into a breach.
Assessing the Impact Before You Act
Changes happen all the time in IT — new features, software updates, infrastructure changes — but before you hit the green light on any change, you need to know how it’ll affect your environment. That’s where the CMDB application mapping comes in.
- Assess impact. Before making a change, you can use the map to visualize which applications and services are dependent on the components you're modifying.
- Avoid unintended disruptions. By seeing exactly what could be affected, you avoid causing outages or performance issues in parts of the system you didn’t even realize were connected.
For instance, a tech company rolled out an update that accidentally disrupted their customer-facing portal. Thanks to their CMDB mapping, they quickly identified which backend applications were impacted and could fix the issue without affecting other parts of the infrastructure.
Read also: Master Cloud Configuration Management: Tools & Tips
Pinpointing Cause and Effect
Things go wrong. It’s inevitable. But when something breaks, you need answers. Fast. That’s when the CMDB application map shines as the ultimate detective tool.
- Diagnose the root cause. Whether it's a service outage or degraded performance, you can trace back to what happened, where it happened, and why it happened.
- Root out the culprit. With a clear map, you can follow the chain of events to identify the specific component or configuration that caused the issue.
In a case with a global logistics provider, an unexpected outage in one of their data centers caused major disruptions in tracking shipments. By referencing their CMDB application mapping, they pinpointed that a network switch had failed, which caused a domino effect throughout the network. The map allowed them to get the issue fixed quickly, ensuring business continuity.
Read also: Top 7 CMDB best practices for your 2025 [Tech Expert Review]
Top 7 CMDB application mapping techniques
When it comes to CMDB application mapping, there’s no one-size-fits-all approach. In fact, combining multiple techniques is the best way to ensure you get the most accurate, complete, and reliable data possible. Let me walk you through the key techniques we typically use, with some real-world examples to keep things grounded.
1. Agentless Discovery
Imagine you’ve got a huge IT environment with hundreds or thousands of devices. Installing agents on every device could take months — no one has time for that, right? This is where agentless discovery comes in. It lets you remotely access devices (using SSH for Linux or Powershell Web Access for Windows) and gather key info like running processes, open ports, and more.
Pros:
- It saves time because you don’t have to install anything.
- It can discover devices that may have missed the agent installation due to oversight or policies.
Cons:
- Not every device is remotely accessible (some might have remote access disabled for security).
- Some hidden or protected endpoints may still slip through the cracks.
For example, a Cloudaware client used agentless discovery to scan and map hundreds of remote devices across different systems. This was essential for uncovering assets that were missed in earlier discovery efforts.
2. Agent-Based Discovery
Now, let’s talk about agent-based discovery. Think of it like hiring a personal assistant for each host. These agents are lightweight programs installed on each host that can pull all kinds of detailed info from configuration files, installed apps, and much more.
Pros:
- They can get info from devices that are turned off (yes, even your laptop that’s never on when you need it).
- Great for capturing data from servers that might be offline for security.
Cons:
- Installing and maintaining agents across thousands of devices takes time and effort (this is where the headache can kick in).
- They’re not perfect — some devices might still not be covered.
One of our Cloudaware clients used agent-based discovery to ensure their entire infrastructure, including devices that weren’t always online, was covered in their CMDB, providing an extra layer of reliability.
3. API Discovery
APIs are like treasure maps to your IT infrastructure. Platforms like Kubernetes, VMware, or NetApp have APIs that can be queried to pull in all sorts of juicy info — perfect for CMDB mapping.
Pros:
- APIs provide super detailed info about your environment — think of them as the x-ray vision for your IT.
- If your CMDB platform integrates well with your infrastructure, you’re golden.
Cons:
- Using APIs can require some software development skills, especially if you’re integrating it with a non-standard system.
- In real life, Cloudaware clients leveraged APIs to pull deep configuration data from their infrastructure platforms. It saved them time by giving them a more accurate, automated way of gathering data about their configuration.
4. NetFlow
When you need to understand how your network traffic is flowing, NetFlow is your go-to. It captures packets traveling across the network, pulling in information about IP addresses, ports, and other details.
Pros:
- You get a good idea of what’s going on between endpoints based on network traffic.
- It’s useful for discovering applications based on their source and destination ports.
Cons:
- NetFlow doesn’t capture every bit of information (it’s not as detailed as some other tools).
- High traffic environments can cause NetFlow to miss short-lived flows.
Businesses used NetFlow to pinpoint unexpected communication flows between devices. By analyzing this data, they were able to avoid downtime and pinpoint potential vulnerabilities across their service network.
Read also: Decoding configuration management vs change management in a multi-cloud environment
5. NMAP: The Port Scanner
NMAP is the classic tool for scanning open ports on servers and firewalls. It’s been around forever and still gets the job done — fast.
Pros:
- It's free and gets you some key info about your IT environment (think port numbers and application names).
- It’s quick and stable — perfect for a speedy overview.
Cons:
- It relies on assumptions, meaning it can misidentify applications if ports are reconfigured.
- It can be CPU-intensive, especially when scanning thousands of ports.
6. Packet Capture: The Deep Dive
When you need to get granular about network traffic, Packet Capture is where you go. This technique looks at the entire packet — not just the headers, but also the payload. It’s like peeking inside every data packet that travels across your network.
Pros:
- Provides way more detail than NetFlow because it analyzes the entire packet.
- Ideal for security-focused environments where you need deep insights.
Cons:
- Implementing this requires serious infrastructure — if you don’t already have packet capture appliances, it’s a big project to set up.
7. Tagging: The Smart Labeling System
Finally, there’s tagging — a simple but powerful way to track assets in cloud environments. Tags are free-form key-value pairs that can contain all kinds of useful info about your assets (think team, department, or application).
Pros:
- Easy to set up and flexible — great for modern environments.
- They integrate seamlessly with infrastructure-as-code and CI/CD models.
Cons:
- Tags can be inconsistent (people forget to add them, typos happen, etc.).
- If not enforced properly, they might not be the most reliable source of truth.
Cloudaware clients used tagging to help their teams keep track of which assets were affiliated with different departments, which improved their overall application mapping strategy and ensured no assets were overlooked.
Best practices for application mapping
If you're diving into CMDB application mapping for a hybrid or multi-cloud environment, let me share a few hard-won tips from experience that can make all the difference. Trust me, you don’t want to spend weeks, months, or even years setting things up, only to realize your CMDB strategy isn’t keeping pace with your evolving infrastructure.
Start by mapping the mission-critical applications first
It’s easy to get lost in the weeds of hundreds or thousands of configuration items. So don’t. Start by mapping the mission-critical applications first. Think about the ones that have the highest impact on the business — those that need up-time to keep things running smoothly.
By focusing on these, you get a quick win and, more importantly, set a solid foundation for the rest of your application mapping.
Make Your Mapping Dynamic
No one has time for static mapping anymore. The whole point of a CMDB application mapping is to track what’s happening in real-time as environments constantly evolve.
So, if you’re relying on manually entering data, it’s time to rethink.
Invest in dynamic mapping from the get-go. It’s a bit more work up front, but once it’s set up, the system does the heavy lifting, keeping track of those fast-moving dependencies between system components for you. Automated discovery is your best friend here.
Decide which use cases to tackle first
Not all CMDB use cases are created equal. You’ve got service management, security management, data center migrations, regulatory compliance, audit readiness, and more on your plate. So, which one should you start with?
- If security is top of mind, start with dependency mapping to ensure you’ve got full visibility into every asset’s access points.
- If you’re preparing for a data center migration, you’ll want to start with understanding how your applications interact and where communication flows need to be adjusted.
Tailoring your CMDB application mapping strategy to these specific use cases will help ensure your CMDB delivers maximum value right out of the gate.
Ensure you choose the right CMDB platform
When choosing your CMDB platform, make sure it supports automated discovery across hybrid multi-cloud environments. You need a tool that integrates with public cloud services, on-prem servers, and even older devices.
And, most importantly, the platform should handle agentless discovery, so you can get the information you need even if you don’t have agents installed on every device. Cloudaware CMDB automated discovery, for example, easily handles this. Thus, your application mapping is always up-to-date without breaking a sweat 😉
Read also: The best configuration management software: Top 10 tools review
CMDB application mapping requires stakeholder support
Let’s say you're working on a CMDB application mapping project for your organization’s hybrid multi-cloud environment. You’ve got the technical know-how to create a solid discovery plan, but as you dive into the process, you quickly realize this isn’t something you can do solo.
This is where stakeholder support comes in. And trust me, it’s more important than you might think.
🌟 Collaboration Across Teams
When you first start mapping, it seems like it’s all about the technical stuff. But then you realize something crucial — CMDB isn’t just an IT project. You need input from security, operations, and business teams to figure out which applications to prioritize.
Without them, you’re just mapping random configuration items. You need their expertise to ensure you’re focused on the services that actually matter to the business. They’re the ones who can tell you which applications are mission-critical and where to focus your efforts first.
🌟 Maintenance and Updates
Now, the real challenge begins — keeping your CMDB application mapping updated. The cloud moves fast, and if you don’t stay on top of it, your CMDB will quickly become outdated. This is where stakeholders truly shine.
With their backing, you have the resources to continuously update your maps, run discovery tools regularly, and ensure dependencies between IT assets and applications are properly tracked. And with automation in place, your map updates automatically whenever changes are detected, so you’re never playing catch-up.
🌟 Incident Response and Risk Management
Then, one day, disaster strikes. A service goes down, and you need to act fast. This is where having those stakeholders in your corner really pays off.
Since they’ve helped prioritize the applications that matter most, you can quickly trace back through the dependency map and figure out what went wrong. With their insights, you can fix the issue quickly and minimize downtime. They also help you identify risks early on, ensuring you’re not blindsided by the next problem.
🌟 Aligning with Business Goals: Driving Decisions
At the end of the day, it’s not just about IT — this CMDB application mapping affects the whole business. Stakeholders make sure your work aligns with broader business objectives. Whether it’s managing cost allocation for services or ensuring compliance, their support helps ensure that your mapping project actually drives value for the company.
Read also: What Is Configuration Management? Definition. Processes. Recommendations
Where to start?
Alright, so you're ready to dive into CMDB application mapping. But where do you start? Let’s break it down in a way that actually makes sense.
- Identify Key Applications. First off, figure out which applications are critical to your business. Don’t get lost in the weeds. In a hybrid multi-cloud setup, you could have hundreds of configuration items, so focus on the ones that are vital to your service delivery. Start with the mission-critical apps — the ones that keep the lights on.
Cloudaware’s platform helps you do this by allowing you to easily track and map dependencies between CIs across cloud and on-prem environments. So, get that foundation right. - Automate Discovery. The beauty of Cloudaware’s discovery tools is they help you automatically identify your applications and dependencies between them across different environments.
The best part? It’s agentless — no need to worry about installing agents on every single device. This means you’ll capture the real-time data on how apps are connected and interdependent, without the hassle of constant manual updates. - Map Dependencies between infrastructure components. Once you have your applications sorted, start building out the dependency map. This is where the magic happens. The more accurate your mapping, the easier it is to manage services, prevent outages, and understand the impact of changes.
Cloudaware’s platform automatically updates your maps, so you can rely on them for real-time insights. - Iterate and Improve. Mapping is never a one-and-done deal. As your environment evolves, your CMDB application mapping should evolve too. Keep it updated with automation, and ensure you’re regularly auditing to catch any gaps.
In short, start with the essentials, automate everything you can, and keep iterating.
Understand how your IT assets work together with Cloudaware CMDB
Ever wonder how your IT assets are working together across multiple clouds and on-prem environments? With Cloudaware CMDB, you get the full picture — automatically.
Here’s how it helps you get a grip on your complex IT landscape:
- Automated Discovery. Quickly discover and map all your configuration items (CIs) across hybrid environments, from servers to services.
- Real-Time Visibility. See how applications and infrastructure dependencies between CIs interact, so you can avoid disruptions and outages.
- Dynamic Mapping. Forget static maps — your application mapping is constantly updated with real-time changes.
- Deep Integration. Cloudaware integrates seamlessly with AWS, Azure, GCP, Oracle clouds and on-prem systems, making it easy to manage diverse environments.
- Comprehensive Reporting. Get detailed insights into your IT assets and service impact, helping you make informed decisions.
