This article presents an expert-guided DevSecOps architecture reference model grounded in real-world failure patterns and proven design trade-offs. It explains how security fits across code, CI/CD, runtime, and governance, shows why common approaches break down, and provides a practical structure teams can adapt to cloud and Azure environments.
It is written for platform engineers, multi cloud security leads, cloud architects, and DevOps managers responsible for designing or governing delivery systems.
Why DevSecOps architecture matters more than tools
In DevSecOps, tools execute checks, but architecture determines whether those checks are effective. The same scanner behaves very differently depending on where it runs: a SAST tool in CI can block unsafe artifacts, while the same tool run after release mostly produces noise, just as an IaC policy evaluated before apply prevents risk but turns into an audit finding when reviewed post-deployment.
Most real failures follow this pattern, with code vulnerabilities persisting when scanning happens after merge and misconfigurations causing larger incidents because infrastructure is replicated automatically across environments. Moving security “left” without changing architecture only shifts effort, not outcomes.
Architecture matters because it fixes decision points by defining which risks are deterministic and blockable in CI, which depend on environment context in CD, and which can only be observed at runtime, allowing automation to scale without constant exception handling.
Read also: Top 13 Cloud Monitoring Tools Review: Pros/Cons, Features & Price
The core DevSecOps architecture layers
DevSecOps fails when different risks are treated the same way, even though code defects, misconfigurations, and runtime abuse surface at different moments and require different controls. A DevSecOps architecture exists to place decisions where each class of risk is cheapest to detect and safest to contain, rather than forcing everything into a single pipeline stage.
A practical model separates security into layers with clear responsibility:
- Code and dependency layer. Introduction of logic errors and inherited open-source risk
- CI security controls. Detection of known vulnerabilities, secrets, and policy violations before builds are created
- Artifact and supply-chain layer. Establishment of integrity, provenance, and component visibility
- CD and deployment gates. Here risk changes based on environment, exposure, and change scope.
- Runtime and cloud security. Here identity misuse, configuration drift, and abnormal behavior appear only after release
- Governance and evidence layer. Continuous capture of ownership, policy compliance, and audit signals
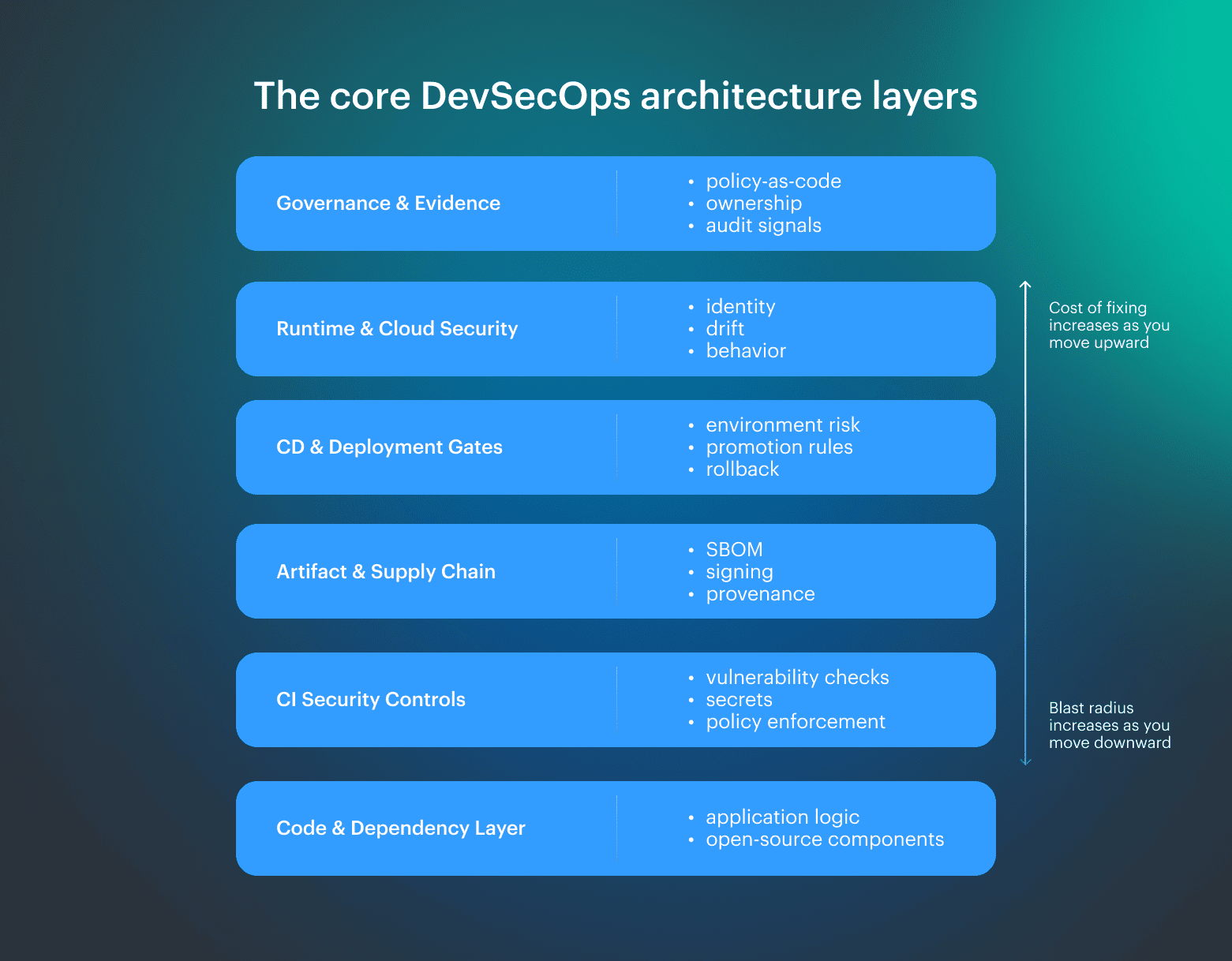 Early layers focus on prevention, where issues can be removed cheaply, middle layers constrain what is allowed to progress, and runtime layers observe behavior that cannot be predicted in advance.
Early layers focus on prevention, where issues can be removed cheaply, middle layers constrain what is allowed to progress, and runtime layers observe behavior that cannot be predicted in advance.
DevSecOps reference architecture (high-level view)
A DevSecOps reference architecture defines where security decisions occur and how they persist over time, focusing on decision points, required inputs, and traceability as changes move through the system rather than on tools or checklists.
In a working model:
- Code and infrastructure enter with ownership already defined
- CI applies baseline checks before artifacts exist
- Artifacts move forward with trust signals attached
- Deployment evaluates risk based on environment context
- Runtime exposes identity use and configuration drift
- Governance links decisions to approvals and outcomes
The value comes from consistency: when the same decisions are made in the same places, automation holds and evidence accumulates naturally, but when decision points shift between pipelines or teams, controls fragment and DevSecOps turns into pipeline-by-pipeline improvisation.
CI pipeline security architecture
CI is the last stage where security decisions can be cheap and fast, because once an artifact exists, risk multiplies through promotion and reuse. The role of CI security is intentionally narrow: to stop unsafe artifacts from existing at all, not to judge runtime or business risk.
A correct CI boundary is simple:
- Block known vulnerabilities, leaked secrets, unsafe dependencies, and invalid IaC
- Allow only checks with a clear pass or fail
- Record what was checked as evidence
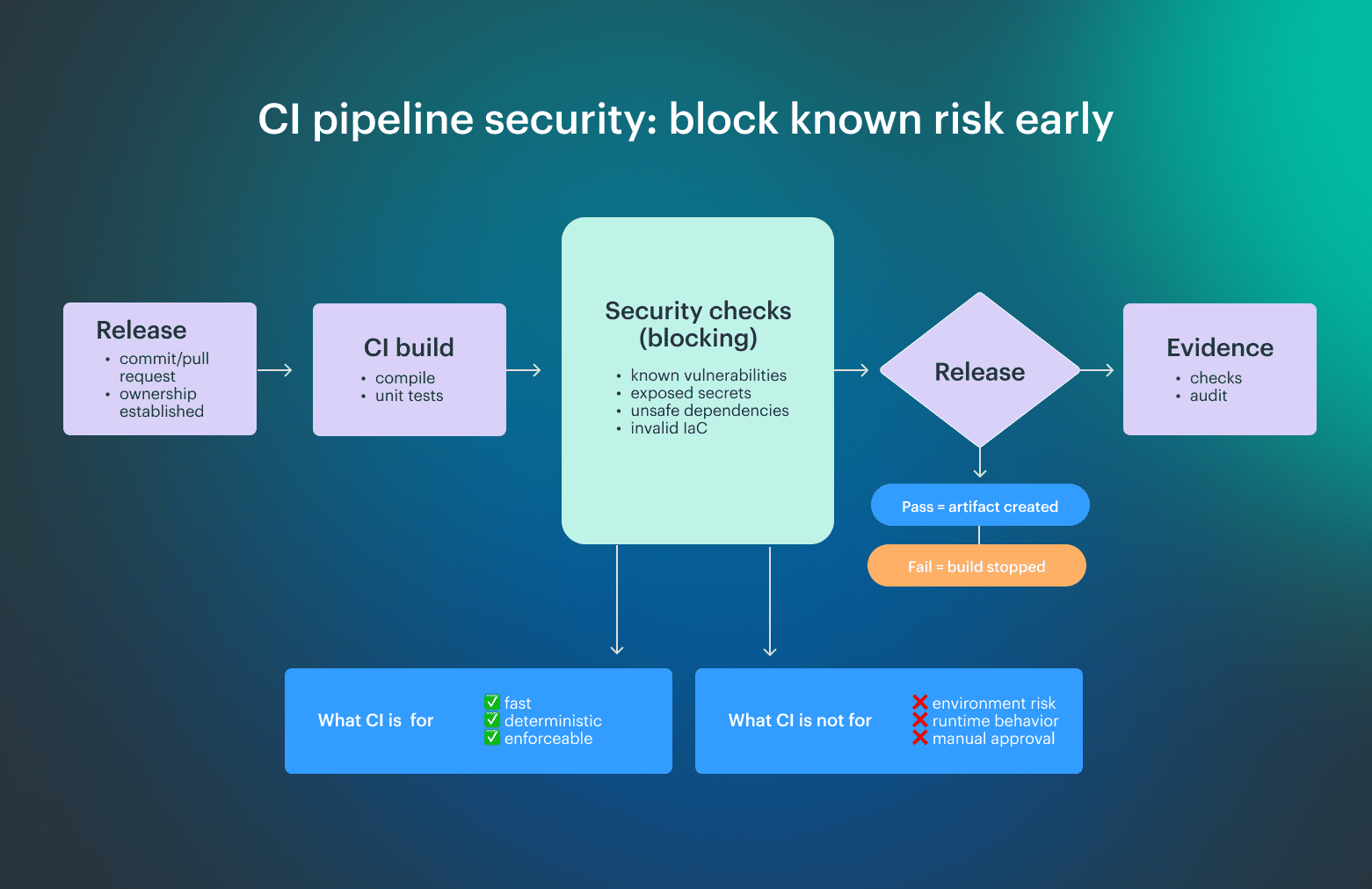
CI should not evaluate environment exposure, runtime behavior, or exception logic, because those decisions depend on context CI does not have. When teams push contextual or manual judgment into CI, pipelines slow down, false positives grow, and controls get bypassed.
Effective CI security draws a clear boundary by blocking what is provably unsafe, recording what was checked, and pushing everything else downstream, where risk can be evaluated with the context CI does not have, which is what allows CI security to scale without becoming noise.
Artifact, SBOM, and supply-chain security layer
After a build completes, risk becomes persistent. Artifacts are copied, promoted, cached, and reused across environments. The supply-chain layer exists to preserve trust as artifacts move, instead of re-evaluating risk at every stage.
Architecturally, this layer fixes artifact identity by producing immutable outputs that are identified, signed, and shipped with metadata, so promotion decisions reference what the artifact is and what was proven about it rather than where or when it was built. Rebuilding to resolve risk breaks traceability, while promotion preserves it.
This layer enforces separation of duties by design: CI proves what was checked, the supply chain proves what is being deployed, and CD controls where it may run, because without this boundary teams fall back to rebuilds, repeated scans, and trust based on timing instead of evidence.
Why SBOMs must be first-class architecture components
SBOMs are control inputs, not reports. An SBOM binds an artifact to its components, licenses, and known exposure at build time. Signing and provenance attach that SBOM to the artifact, creating a verifiable chain of custody aligned with SLSA.
When SBOMs are first-class, teams can answer operational questions without rescanning or rebuilding: what is running, what changed, and what risk was accepted. Promotion becomes a policy decision over known artifacts, not a race to recreate them.
CD and deployment security architecture
CD decides where an artifact may run, not whether it is safe to exist, since CI already answered that question. At deployment time, risk depends on context such as environment, exposure, and blast radius, which is why production differs from staging and external differs from internal, and CD applies those differences consistently.
A workable model separates artifact trust from environment risk. Only verified artifacts are allowed to move forward, then promotion is evaluated based on impact, data sensitivity, and rollback options, which keeps delivery predictable while tightening controls only where failure would matter most.
CD security breaks when judgment replaces rules. When promotion depends on ad-hoc review, enforcement drifts and pipelines slow. Clear rules, applied the same way every time, are what make CD scale.
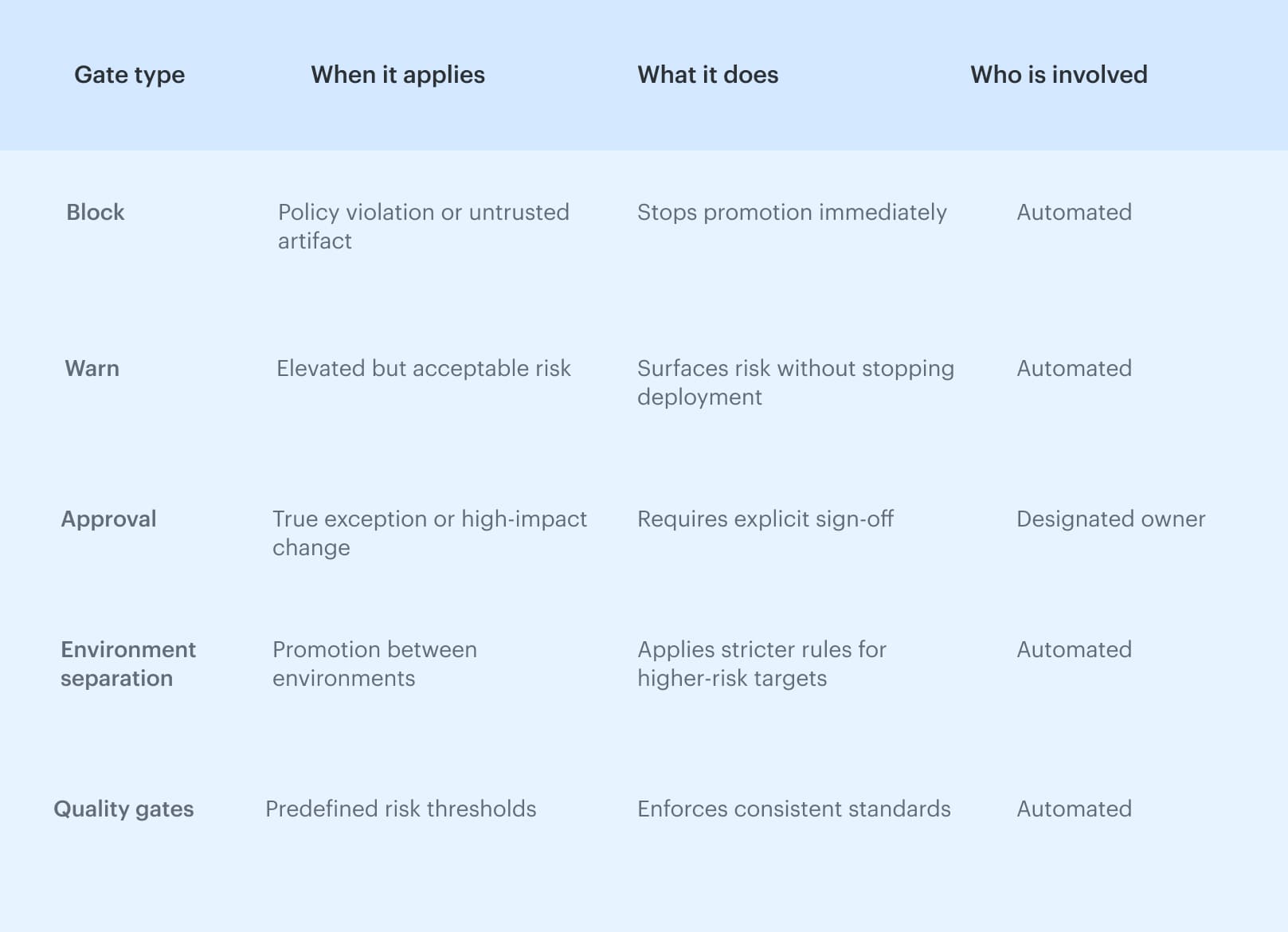
Designing deployment gates that don’t slow teams down
Deployment gates work when they are predictable and applied consistently. The goal is not to stop delivery by default, but to enforce clear rules based on risk, environment, and trust level, with automation handling normal paths and approvals reserved for exceptions.
Runtime and cloud security architecture
Runtime is where intent meets reality, because while CI and CD validate what should happen, runtime shows what actually happens once identities are resolved, permissions are applied, and services interact in live environments.
Most runtime failures follow the same patterns:
- Identity misuse from over-privileged roles or leaked credentials
- Configuration drift from emergency fixes or platform changes
- Unexpected exposure created by network or policy changes
These issues cannot be fully detected earlier because they depend on live context: active tokens, real network paths, and effective permissions.
Effective runtime security does not stop deployments. It records behavior, links it to the artifact, the promotion decision, and the identity involved, and feeds that signal back into policy and backlog. That feedback loop is what keeps DevSecOps corrective instead of reactive.
Infrastructure as Code (IaC) security architecture
IaC amplifies risk by design. One change can roll out across accounts, regions, and environments in minutes. That speed is why cloud incidents are often configuration-driven: mistakes are copied, not contained.
In DevSecOps, IaC is a first-class security surface, not a helper layer. Security must act before resources exist:
- Scan before apply to catch unsafe definitions
- Evaluate policy early to block forbidden states
- Standardize patterns so the same risk is not redeployed under new names
IaC anchors runtime security by defining intent through declared state, so anything outside that state is treated as drift. This makes emergency fixes, console changes, and unmanaged updates visible actionable instead of leaving runtime alerts without context.
Treating infrastructure as code means treating security as code
If infrastructure is versioned, tested, and reviewed, security must be too. Controls enforced outside the IaC flow disappear as environments change.

Azure DevSecOps architecture example
Azure is not presented here as a recommended stack, but as a clear example of how a DevSecOps architecture can stay intact over time. The architecture Azure teams work with is organized around identity, policy, and environment boundaries rather than individual pipeline steps, which helps security decisions remain stable as systems evolve.
In practice, this allows Azure teams to promote artifacts instead of rebuilding them, enforce policy automatically rather than through ad-hoc approvals, and collect security signals continuously instead of reconstructing evidence for audits. The result is an Azure DevSecOps architecture that remains stable as systems scale.
Mapping the reference architecture to Azure building blocks
- Identity: Entra ID defines users, workload identities, and trust boundaries
- Source control: GitHub or Azure Repos provide versioning, ownership, and history
- CI/CD: Azure Pipelines or GitHub Actions run builds and enforce early checks
- Secrets: Azure Key Vault keeps keys and certificates out of code and pipelines
- Artifacts: Azure Container Registry stores signed images for promotion
- Compute: AKS runs workloads with identity-aware admission controls
- Policy: Azure Policy enforces guardrails across subscriptions and clusters
- Signals: Defender for Cloud and Microsoft Sentinel surface runtime findings
Governance, evidence, and compliance architecture
Governance breaks when it is added after delivery. Reviews turn manual, evidence is rebuilt from logs, and audits slow teams down. In DevSecOps, governance works only when evidence is produced by default, as part of delivery.
This layer does not add controls. It connects outputs from existing ones into a single trail with ownership and retention:
- CI → SBOMs, scan results
- Supply chain → attestations, provenance
- CD → approvals, deployment records
- Runtime → drift and configuration findings
Together, these form a continuous audit trail. Compliance stops being a project and becomes a property of the system.
| Evidence type | Produced where | Used for |
|---|---|---|
| SBOM | CI / build | Exposure analysis |
| Attestations | Supply chain | Provenance |
| Approvals | CD | Change control |
| Drift findings | Runtime | Compliance |
How architecture enables auditability without slowing delivery
Auditability improves when decisions are consistent and automated. Evidence is captured once, close to where it is created, and reused across reporting, investigations, and compliance reviews. This is where platforms like Cloudaware focus in practice: tying change, policy decisions, and runtime reality into audit-ready records without inserting manual steps into delivery.
## DevSecOps architecture diagram: how to read and reuse it
A DevSecOps diagram is a decision map, not a system diagram, and it should be read by tracing where trust is established, constrained, or only observed. If it clearly explains why a change passed, failed, or required review, it is doing its job; if it only shows tools or arrows, it is not.
The diagram should function as a shared contract, where security, platform, and leadership arrive at the same answers without extra explanation.
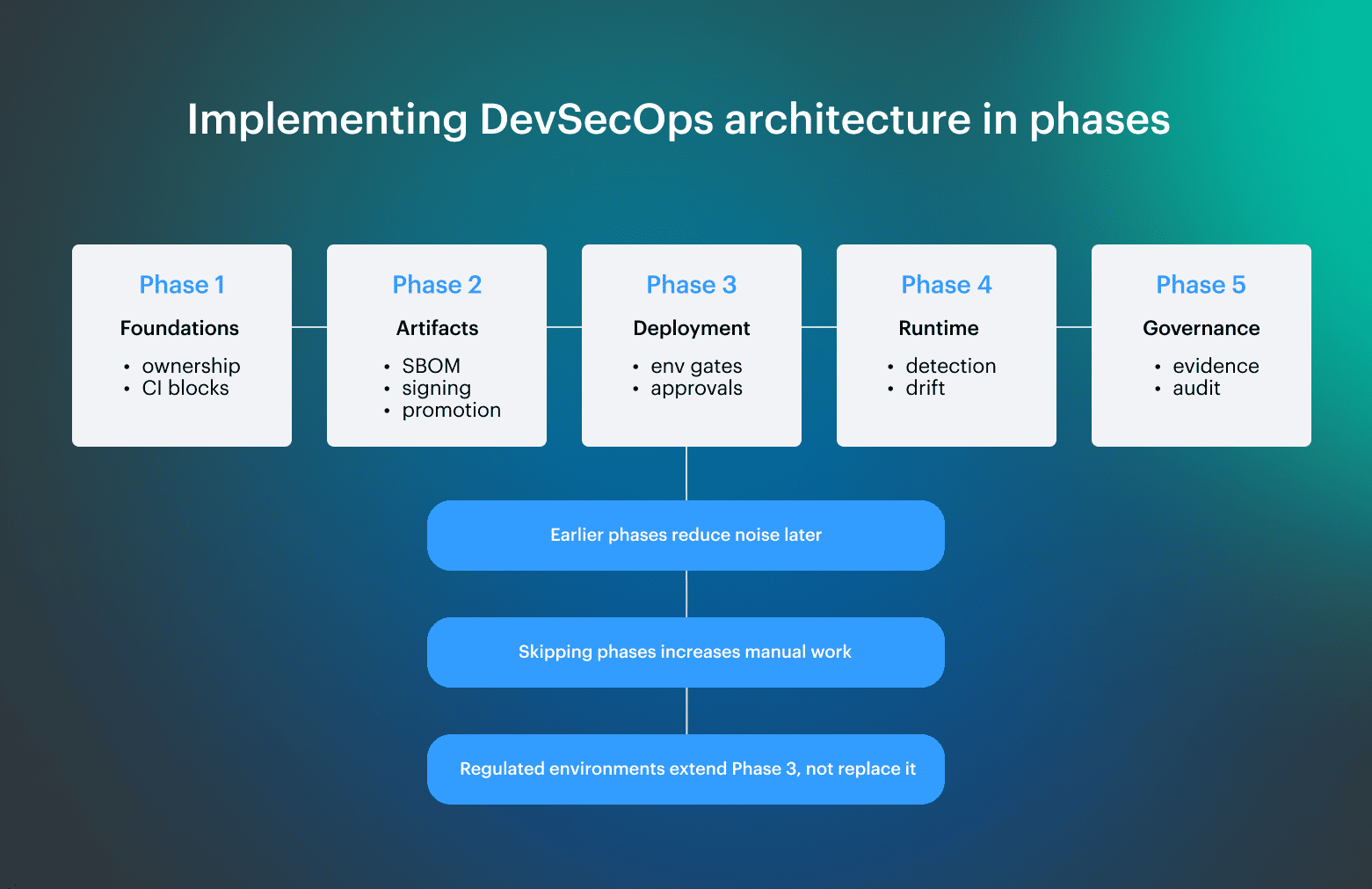
Turning architecture diagrams into operational assets
Use the diagram to drive specific actions:
- Follow decisions, not stages. Identify where checks are blocking, where they warn, and where they only observe
- Explain risk, not tools. Strip vendor names and walk leadership through trust, exposure, and evidence flow
- Change safely. Replace tools freely, but keep decision points fixed. If two layers answer the same question, remove one
Operating DevSecOps architecture at scale
DevSecOps breaks when delivery moves faster than visibility. Pipelines still run, but ownership becomes unclear, findings lose service context, drift has no attribution, and approvals turn into empty signals. Teams can no longer explain who owns a change, why it was allowed, or whether runtime still matches intent.
At scale, the DevSecOps process only holds when ownership, promotion, and drift handling are enforced by architecture, not convention.
DevSecOps practices that keep the architecture from collapsing
At scale, the architecture holds only if three things stay true:
- Ownership is explicit (service, team, environment)
- Intent stays comparable to reality (declared vs live state)
- Decisions remain traceable (why something passed or changed)
Manual setups fail because they cannot preserve these links continuously:
- Ownership inferred from repos, not runtime
- Drift detected without change context
- Approvals recorded without scope or rationale
Cloudaware is used where DevSecOps must extend beyond pipelines, keeping a live model of resources, identities, changes, and policies so architectural intent stays visible as systems evolve. Without that, DevSecOps degrades into manual governance, even with “best practices” in place.
