When teams say they want DevSecOps automation, they usually mean “fewer manual reviews” and “faster releases,” but the real win comes from automating decisions and the proof behind them.
Running more scanners is easy, turning signals into a clear outcome is harder: does this change pass, does it need approval, or does it stop the line?
The difference is whether security controls are wired into CI/CD gates with policy-as-code and whether every outcome leaves durable evidence you can trace back to the change.
In this guide, you will learn where automation fits across CI/CD gates, how to express policy-as-code without stalling delivery, and how to generate evidence continuously, so compliance no longer hijacks sprints.
What DevSecOps automation is (and what it isn’t)
DevSecOps automation is the ability to run security controls automatically at the points where delivery decisions are made, so a change produces a repeatable outcome, not a debate.
It means security checks are embedded across the pipeline and expressed as policy-as-code, so CI/CD gates can consistently decide whether something is allowed, needs approval, or must stop before it reaches production.
What DevSecOps automation is not: adding more tools, collecting more alerts, or shifting manual reviews earlier in the sprint. If automation only increases signal volume without tightening the decision model, teams ship slower and learn less.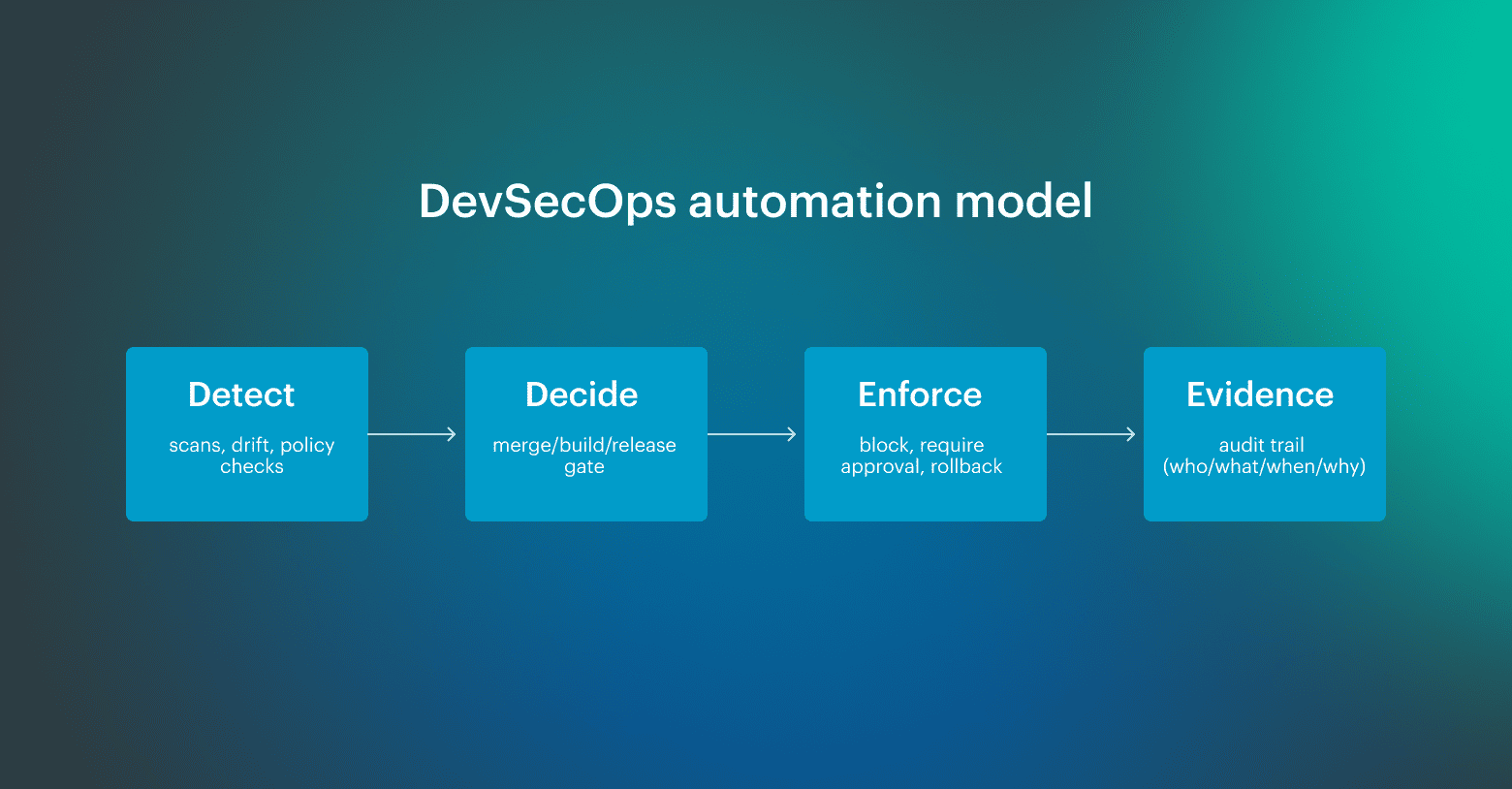 A control finds a condition, a gate returns a clear outcome, enforcement applies it, and evidence collection preserves what happened, when, and why. In mature setups, a control plane ties those gates to ownership and keeps the evidence linked to the exact change, so decisions remain explainable long after the pipeline run is gone.
A control finds a condition, a gate returns a clear outcome, enforcement applies it, and evidence collection preserves what happened, when, and why. In mature setups, a control plane ties those gates to ownership and keeps the evidence linked to the exact change, so decisions remain explainable long after the pipeline run is gone.
Three bottlenecks that force DevSecOps automation
Teams try to automate DevSecOps when the pipeline turns into a waiting room.
- Review queue: a few people become the approval choke point, and releases start slipping for reasons that have nothing to do with engineering work, which is how decision latency quietly becomes your default operating mode.
- Alert fatigue: if findings are duplicated, poorly scoped, or land without an owner, they stop being signals and turn into background noise, and then everyone learns the same bad habit: treat “security passed” as a checkbox instead of a decision with consequences.
- Audit scramble: when evidence lives in screenshots, Slack threads, and exports someone ran once, every audit request becomes a mini-incident, because you are reconstructing approvals and control results from memory after the fact, instead of pulling a traceable record tied to the change.
Read also: 9 DevSecOps Benefits for Security Leaders [With Proof]
DevSecOps automation framework you can reuse
After you have operated a few pipelines at scale, you stop looking for the “right DevSecOps toolchain” and start looking for a repeatable decision model. A reusable model is a way to describe what you check, where you decide, how you allow exceptions without losing control, and how you keep evidence attached to the exact change.
Treat it as a thin layer you can map onto any CI/CD stack, whether you run GitHub Actions, GitLab CI, Jenkins, or something homegrown. Use this table as the backbone: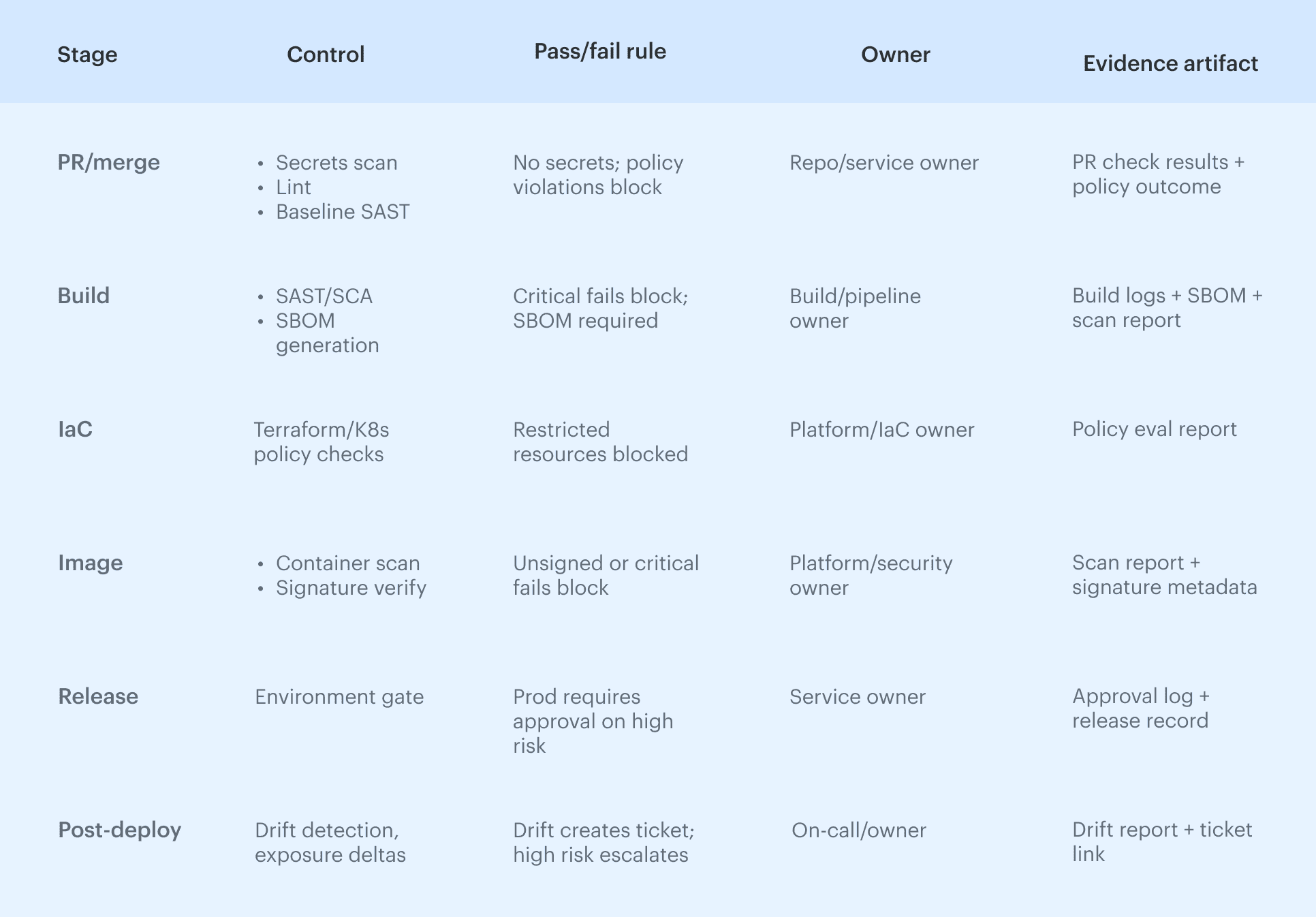 The table is the skeleton. The notes below are the rules that keep it from collapsing into “we ran the checks” without a clear gate outcome, a real owner, or evidence you can still trace when the pipeline run is gone.
The table is the skeleton. The notes below are the rules that keep it from collapsing into “we ran the checks” without a clear gate outcome, a real owner, or evidence you can still trace when the pipeline run is gone.
- Controls. Not all checks are equal; some should stop the line, while others should create managed work for triage instead of blocking delivery
- Gates. A signal becomes a decision only at a gate, and the outcome must be deterministic (block/warn/allow) with a named owner
- Exceptions. Speed without loss of control requires exceptions to be managed objects with scope, TTL, approver, reason, and re-check
- Evidence. Evidence must be linkable and survive longer than a single pipeline run, so approvals and scan results stay tied to the exact change and release record
A specific example of the control-plane idea: if a high-risk change touches a production service, the system should identify the owner, require the right approval, and store the decision. Plus evidence in one place that stays queryable long after the pipeline run is gone.
Read also: 10 DevSecOps Best Practices That Actually Survive Production
Where each tool belongs in the framework
Most teams already have scanners. The failure mode is that they are not wired into the same decision model, so you get signals without a consistent gate outcome and evidence that is scattered across UIs. Treat tools as interchangeable sources here.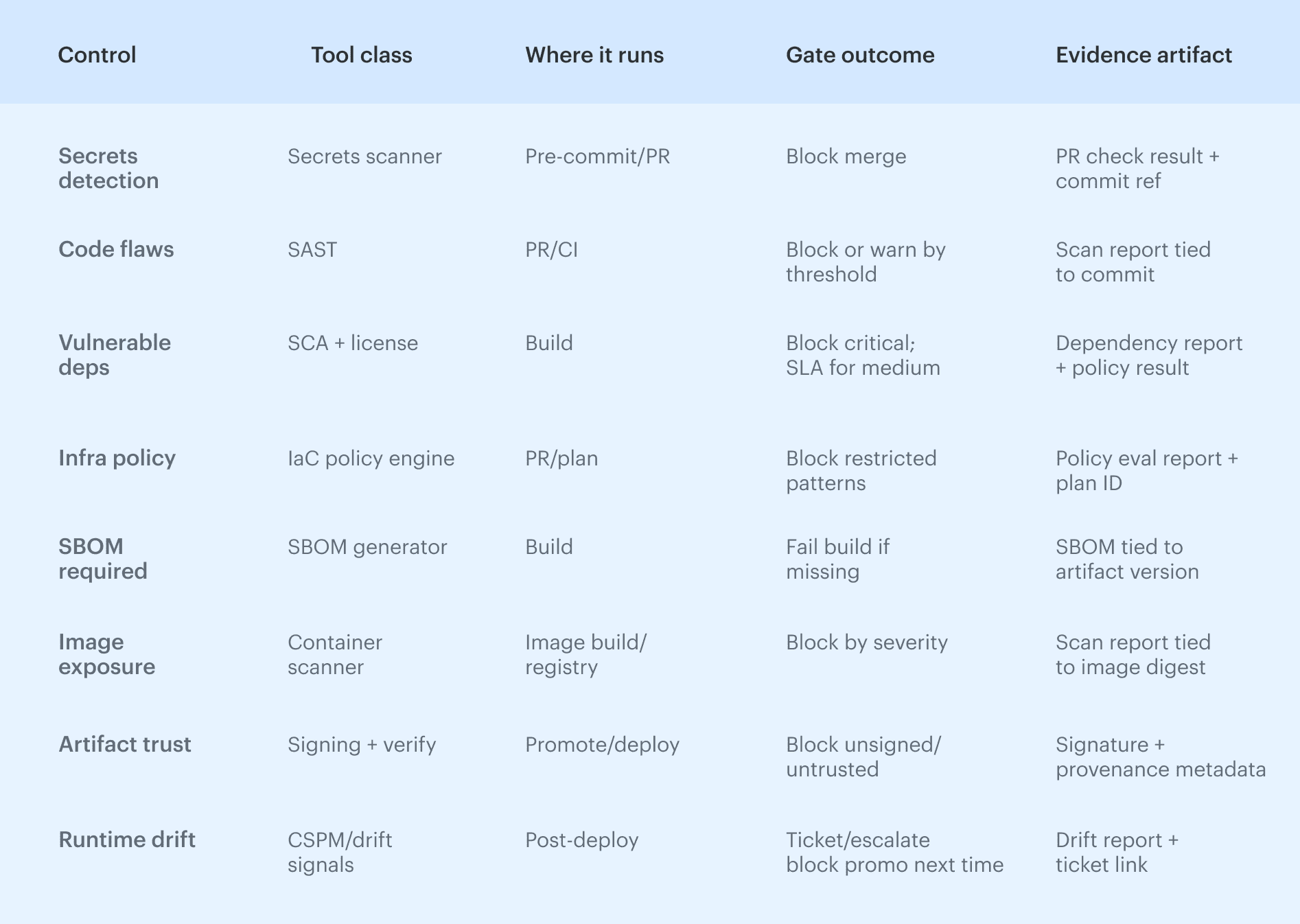 If you keep this mapping stable, you can swap tools without rewriting policy, and you stop arguing about “which scanner is right” because the pipeline enforces the same decision criteria and produces the same evidence every time.
If you keep this mapping stable, you can swap tools without rewriting policy, and you stop arguing about “which scanner is right” because the pipeline enforces the same decision criteria and produces the same evidence every time.
Read also: 15 DevSecOps Tools - Software Features & Pricing Review
Pre-commit and PR: automate security checks
Use this as a quick map of the six CI/CD stages where automation should produce a deterministic gate outcome and durable evidence, then drill into each stage below.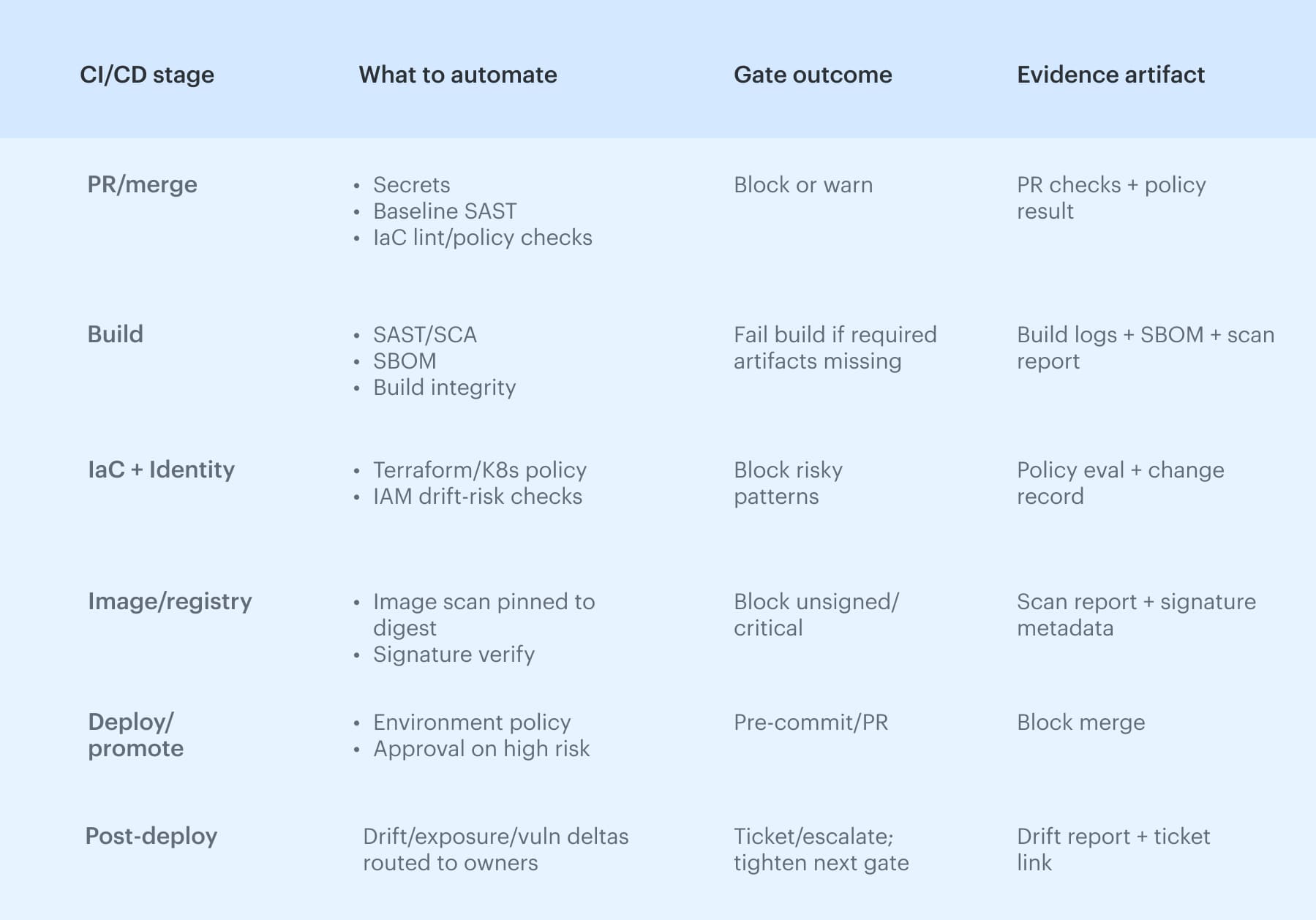 To automate security checks in the DevSecOps pipeline without turning every commit into a debate, start with pre-commit and PR. Secrets detection belongs here because it is high-signal, and lint rules can catch risky patterns before they harden into production defaults.
To automate security checks in the DevSecOps pipeline without turning every commit into a debate, start with pre-commit and PR. Secrets detection belongs here because it is high-signal, and lint rules can catch risky patterns before they harden into production defaults.
PR merge rules are the first real gate: they encode who can approve what, which branches can merge, and which policy checks are non-negotiable. The stage only works with routing and traceability, so the PR carries change metadata, maps to an owner, and later links to the artifact that shipped, which is why automated DevSecOps workflows scale.
Build automation: SAST/SCA, SBOM, artifact integrity
The build stage is where “security checks” either become enforceable or turn into noise, because this is the first point where you can tie results to a specific artifact version. Run SAST and SCA here, but treat the output as input to a build integrity gate: the build either produces what your downstream stages require, or it does not ship.
At minimum, a serious build should output an SBOM, capture dependency inventory, and stamp artifact versioning in a way you can trace later.
Add checksums and provenance metadata so you can answer basic questions under pressure:
- Which commit produced this image?
- Which dependencies were inside it?
- Has anything changed since it was signed and promoted?
Reproducibility matters because if you cannot rebuild the same artifact, you cannot prove what you shipped.
Read also: Inside the DevSecOps Lifecycle - Decisions, Gates, and Evidence
Cloud security and DevSecOps automation: IaC and identity as the control plane
In cloud environments, misconfigurations behave like code bugs: a bad Terraform module, an overly permissive security group, or a Kubernetes manifest that exposes a service can replicate across accounts and clusters in minutes.
That is why IaC checks belong in the same decision path as application controls, with explicit environment boundaries so “prod-like” cannot silently inherit production risk.
The control plane is identity. If role trust is widened, wildcard permissions appear, or a policy change expands access to critical resources, the risk profile shifts even when no application code moves. Gates should treat identity deltas as first-class changes and stop promotion when privilege expands outside the approved intent.
Automated vulnerability scanning: severity rules, false positives, and exception debt
Pipelines rarely fail because they cannot run vulnerability scanning; they fail because nobody agrees on what the results should do. Container scanning only holds up when it is pinned to an image digest, not whatever “latest” resolves at deploy time.
This way, record findings against the digest, treat the registry as part of the trust boundary, and watch base image drift. Signature verification is the enforcement step: unsigned images or signatures that do not match the expected provenance should not be promotable.
To automate security checks in DevSecOps pipeline stages reliably, you need deterministic severity thresholds, SLAs by class, and a false-positive path that does not turn into permanent blind spots. Tie results to the artifact version, not a repo or a vague “build,” and manage waivers with a waiver TTL, scope, and approver. Track exception debt as a metric, because that backlog is usually where the next incident starts.
Read also: DevSecOps vs DevOps: What’s the Difference [Explained by a Pro]
Deploy automation: promotion gates, environment policy, and change approval
Deploy is where automation either holds the line or gets bypassed. If teams can “just rerun” a deploy with a slightly different input, you do not have a gate; you have theater.
This is also where DevSecOps automation needs a clean release record: what was promoted, to which environment, under which policy outcome, with whose approval.
A practical high-risk workflow is straightforward:
- Detect that the change affects a production service and crosses a risk threshold
- Identify the correct owner based on service scope and environment boundaries
- Require approval from the right group rather than “whoever is online”
Then record the decision, the approver, and the reason (with a TTL if it is an exception), and link the approval plus evidence artifacts to the exact release record so it stays auditable later.
Read also: DevSecOps Statistics (2026): Market, Adoption, and AI Trends
Post-deploy signals that keep approvals honest
DevSecOps observability security automation is where you stop treating runtime as a separate world and start using it to keep delivery controls honest. The goal is not “more telemetry,” it is a feedback loop that turns real production signals into updated gates, ownership routing, and faster decisions the next time a similar change ships.
Signals worth wiring into the loop include:
- Deploy events (what changed, where, and when)
- Permission and trust changes (role drift, new policy edges)
- Exposure deltas (new public endpoints, widened network paths)
- Vulnerability deltas (new CVEs from base image or registry drift)
DevSecOps automation strategies: minimum viable setup
DevSecOps automation strategies that hold up in real pipelines focus on decisions and evidence first, then expand coverage without creating bypass behavior.
- Start with deterministic outcomes. Define what blocks, what warns, and who owns each path, so teams do not negotiate risk at deploy time.
- Use hard gates only for high-confidence controls. Secrets, unsigned artifacts, and critical policy violations are worth stopping the line for; noisy checks are not.
- Route soft gates with SLAs, not “FYI” alerts. If a finding is actionable but ambiguous, assign it to an owner with a deadline and a clear escalation rule.
- Treat exceptions as expiring objects. Waivers need scope, approver, TTL, and re-check, or they turn into permanent drift disguised as process.
- Standardize evidence artifacts early. Tie scan results to artifact versions, approvals to release gates, and changes to a traceable history, so audits stop hijacking sprints.
Minimum viable setup then becomes a small set of hard gates, a larger set of routed soft gates, managed exceptions, and consistent evidence artifacts.
