You know that moment when the change window is tonight, and you’re staring at three clouds plus a couple of “we’ll retire it next quarter” on-prem boxes… and nobody can answer the simplest questions?
Not “how do we fix it.”
Just: what do we actually have.
Because in a multi-cloud DevOps setup, asset sprawl doesn’t show up as a neat list. It shows up as a surprise NAT Gateway bill, an orphaned Kubernetes cluster that still has admin creds floating around, a license renewal you didn’t budget for, and a “who approved this?” workload that’s now in scope for compliance.
So yeah. Who owns what?
Which team is on the hook when that EC2 fleet is patched late, that Azure VMSS image is three months behind, or that on-prem SQL box is still running with a local admin from 2019?
This is where ITIL asset management stops being “process theater” and starts being a control system.
An “asset” here isn’t only a server with a sticker on it. It’s the AWS account that contains the server. It’s the AMI version, the EBS volume, the security group rules, the certificate expiring in 14 days, the dependency chain that turns a tiny change into a production outage. When you treat all that as a first-class asset set, you get something you can govern.
Skip that structure and your CMDB turns into that sad spreadsheet graveyard: half stale, half guessed, and completely useless the minute someone autoscaled.
In this guide, we’ll unpack
- what ITIL asset management actually means for modern environments,
- what “good” looks like (think ownership fields you can enforce,
- lifecycle states you can trust, change history you can audit, and normalization so AWS/Azure/on-prem roll up into one report),
- where DevOps teams accidentally sabotage themselves,
- and the practices that keep your inventory lean enough to be real… and strict enough to be accountable.
Before we go further, quick terminology check 👇
What is ITIL asset management
Let’s translate this out of framework-speak and into how your week actually goes.
ITIL asset management is how you keep assets from turning into “mysterious stuff that exists in prod and costs money.” ITIL itself is a set of service management practices. Not a religion. More like a shared playbook for running IT in a way that doesn’t collapse the moment one team changes something.
Here’s the key shift: plain old inventory tracking tells you what you have. Asset management in ITIL forces the harder question: what service is this asset supporting, who owns it, and what should happen to it next? That’s the difference between “we have 4,218 things” and “these 73 things are keeping checkout alive, these 140 are leftovers from last quarter’s migration, and these 19 are one policy breach away from becoming a weekend.”
So asset management ITIL is lifecycle-driven. You’re managing assets from the moment someone requests them, through onboarding, operation, change, renewal, and retirement. Which sounds tidy, until you remember the real world includes:
- A SaaS contract that auto-renewed because nobody was the “owner,” and finance only noticed after the second invoice.
- Cloud resources that look active because they’re running, but nobody can tell you which team needs them.
- Licenses that are “assigned” in a spreadsheet and “unused” in reality.
- On-prem gear that’s still powered on because decommissioning requires three approvals and a small miracle.
In a hybrid multi-cloud environment, assets aren’t just laptops and servers. They’re cloud instances, databases, containers, load balancers, SaaS seats, certificates, images, even accounts. The mess usually isn’t that they exist. The mess is that they exist without context. No service tie-in. No lifecycle status you can trust. No accountability you can point to without starting an argument in Slack.
That’s why this discipline matters. When you do it right, you stop treating your CMDB like a museum of outdated entries and start treating it like operational truth. You can answer “_what do we own, what does it power, what does it cost, what risk does it carry, and what happens if we change it_” without assembling a detective squad.
And yes, now we can talk about the chaos. Because that’s where asset management ITIL earns its keep.
How does asset management in ITIL work
You know the moment. Everything looks stable. Then one small change lands in prod and suddenly you’re triaging three different “unrelated” problems that are absolutely related.
Here’s the version you’ll recognize. You’re the cloud architect for a hybrid setup: AWS, Azure, and that VMware cluster nobody wants to touch because it still runs something revenue-adjacent. A DevOps team deploys a new microservice to EKS. Ten minutes later, latency climbs. The database starts timing out. Meanwhile an on-prem backup job kicks off at the worst possible time and saturates the link. Finance flags an overage. Security drops a compliance escalation. Leadership wants a narrative and they want it before lunch.
Without IT asset management ITIL, this becomes archaeology. You grep Terraform. You scroll Slack. You open Confluence and immediately regret it. Ownership is fuzzy. Service impact is guesswork. The question “why does this exist” turns into a meeting.
With asset management in ITIL, the flow changes because your CMDB and asset register are built to answer operational questions, not just store records.
You do three things, fast.
1️⃣ Identify the asset in context, not in isolation.
You pull up the EKS cluster and you don’t stop at “cluster exists.” You see which service it supports, what environment it belongs to, and who is on the hook for it. The record isn’t cute metadata either. It includes the stuff you actually use when you’re debugging impact.
- CI owner or team alias, not “DevOps”
- environment tag you trust, not “prod-ish”
- dependencies like DB endpoints, queues, IAM roles, load balancers
If the asset can’t be tied back to a service, it’s already a risk. In a decent asset management ITIL setup, that’s not a philosophical statement. It’s a rule.
2️⃣ Trace relationships so the root cause doesn’t hide in plain sight.
This is where ITIL asset management stops being “inventory management with better manners.”
The microservice talks to a database instance. That DB is tied to a legacy app. The legacy app is tied to a contract, a maintenance window, and a retirement date that’s been “next quarter” for two quarters. The on-prem backup job is supposed to run Sundays at 02:00, but it’s firing during peak because someone edited a script and never updated the schedule record.
When relationships are modeled, you don’t guess. You follow the chain.
3️⃣ Act through lifecycle controls, not hero work.
Now you can do the boring fixes that prevent the next fire:
- throttle or reschedule the backup job because it’s outside its approved window
- right-size or move the noisy workload because it’s violating cost guardrails
- pin ownership and create a change record because that legacy DB is a dependency you can’t ignore
- document the compliance exposure in the same place the asset lives, so security isn’t chasing screenshots
This is why asset management ITIL works in practice. It gives you a repeatable path: discover, classify, assign ownership, map to services, track lifecycle status, enforce policy, and retire cleanly. You stop relying on tribal knowledge.
And the outcomes are measurable, not vibes. When you can answer “_what is this, who owns it, what does it support, what changed, what does it cost, what risk does it carry_” in minutes instead of days, the whole org calms down. Cost spikes become explainable. Audit evidence stops being a scavenger hunt. Performance issues get solved at the dependency layer, not with random retries and hope.
That’s it for ITIL asset management in the trenches. Less panic. More control.
7 benefits of ITIL it asset management
After working with Cloudaware clients and closely monitoring the IT industry, I’ve noticed a clear pattern — organizations struggle with asset visibility, cost control, and security risks in their multi-cloud hybrid environments.
Whether it's AWS, Azure, or on-prem, unmanaged IT assets lead to budget overruns, compliance headaches, and operational bottlenecks.
Here’s what I’ve seen firsthand:
1. Financial prudence
Without a structured ITAM approach, organizations often find themselves bleeding money on unused or redundant assets. Implementing IT asset management can lead to significant savings.
According to the ITAM Forum, companies have reported up to a 30% reduction in IT costs within the first year of implementing ITIL asset management practices.
For instance, a situation with my fried Helen, a Cloud Architect. Once, she was having a terrible morning. The CFO had just sent a furious email about the unexpected $300,000 overage in AWS costs — again. Scrambling for answers, she opened Cloudaware CMDB, searching for anomalies.
Then she saw it: hundreds of orphaned EC2 volumes and unattached EBS snapshots left over from past projects. No one had decommissioned them. No alerts, no tracking, just silent money leaks.
With IT asset management, Lena configured an automated lifecycle policy to detect and remove unused resources after 30 days. The CFO’s next email? A relieved thank-you.
2. Enhanced security posture
In a multi-cloud environment, shadow IT can proliferate, introducing security vulnerabilities. IT asset management in ITIL provides a clear inventory of all assets, enabling proactive security measures. As noted by LogMeIn,
"Your ITAM can even notify you of unusual events or patterns, based on historical network data, that have been correlated with cyberthreats."
Consider a scenario when during a late-night security review, Mark, a DevOps Engineer, noticed an alert: an old unpatched Tomcat instance running on a forgotten Azure VM — exposed to the internet. His stomach dropped.
This wasn’t just shadow IT — it was a ticking time bomb. A quick ITAM lookup revealed the service hadn’t been used for months, but its open ports made it an easy ransomware target.
One Slack message to the Cloud Security Team, a quick CMDB check, and the VM was shut down before an attack could happen. Disaster avoided.
3. Streamlined Compliance and Audit Readiness
Compliance isn’t scary because of the rules. It’s scary because audits show up when your data is messy.
ITIL asset management helps you stay audit-ready by treating “proof” as part of the asset lifecycle, not as a frantic side quest. The minute an auditor asks, you’re not stitching together evidence from screenshots, purchase emails, and five different tools. You’re pulling one defensible story: what’s deployed, what it runs on, who owns it, what you bought, and what changed.
The ITAM Forum makes a point I wish more teams internalized: strong ITAM isn’t only about licenses. It also helps validate that hardware and software assets are legitimate, then supports continuity planning with real asset intelligence.
Here’s what “audit readiness” looks like when it’s real, not a slide deck:
- Your entitlement data is attached to the software asset record, with purchase dates, terms, and renewal owners. No “someone in procurement might have it.”
- Deployments are reconciled to reality. You’re not trusting a spreadsheet, you’re looking at what’s actually running, where it’s running, and how it’s configured.
- Exceptions live in the system with a reason and a timestamp. That weird legacy box isn’t a mystery. It’s documented risk with an owner.
- Evidence is exportable. You can produce a clean effective license position report without a week of prep.
Here is a case from our client: One Monday, an IT Asset Manager at a customer got the email nobody likes: “_We’re initiating an Oracle license audit._” The fear wasn’t theoretical. A six-figure exposure is common when you can’t prove usage versus entitlements quickly, especially in hybrid setups where virtualization and sprawl make counting “installs” meaningless.
John (name is changed) didn’t panic. He opened Cloudaware and pulled an audit pack that answered the auditor’s first questions in one pass:
- where Oracle workloads were running (cloud plus on-prem)
- what compute footprint they were tied to
- which instances looked idle or over-provisioned
- which license entitlements were mapped to those deployments
That package is what changes the dynamic. Auditors stop driving the process because you can validate claims fast. The internal conversation changes too. Instead of “are we compliant,” you get to ask, “why are we paying for capacity we’re not using,” and fix it before renewal season.
4. Operational Efficiency and Informed Decision-Making
Operational pain usually isn’t “we lack tools.” It’s “we can’t see what’s real, fast enough to act.”
When it asset management ITIL is working, your asset register stops being a list and turns into a decision surface. You can answer boring but expensive questions without guesswork. Which workloads are tied to revenue paths. What’s safe to scale down. Who owns the thing that’s burning budget. Atlassian frames it simply:
"Asset management keeps information updated, so teams eliminate waste and improve utilization."
Now the real-life version.
Tom, an infrastructure engineer, had an Amazon Web Services Kubernetes cluster pegging CPU for weeks. Autoscaling kept adding nodes. Latency still spiked at peak. Everyone blamed “traffic” because that’s the easiest story to tell.
He checked the ITAM view in Cloudaware and filtered by two signals that always surface the truth: resources with no active owner, and anything tagged non-production that’s still running in production-sized capacity. The culprit wasn’t an advanced performance bug. It was abandoned test workloads. Old namespaces, no ticket, no team alias, CPU requests set like it was Black Friday. They were quietly eating about 60% of the cluster’s capacity.
One message in Slack to the right DevOps channel, a decommission script scheduled for end-of-day, and the cluster calmed down. CPU headroom came back. Node count dropped. The next morning, Tom didn’t have to “optimize” anything heroic. He just had clean data, plus the authority to act on it.
That’s the efficiency win people miss. Not faster clicks. Faster decisions, backed by a trail you can defend.
5. Improved Vendor Management and Negotiation Leverage
Vendor renewals get weirdly emotional for something that should be math.
The rep shows up with a confident number. “You need 1,500 seats.” Someone on your side shrugs because, honestly, who can prove otherwise in real time? That’s how shelfware turns into a line item you stop questioning.
ITIL asset management changes the tone of that call. Not because it makes procurement “tougher.” Because it gives them evidence. Usage. Ownership. Timing. The stuff you can defend when a vendor tries to anchor you to last year’s peak headcount.
This is also where ITAM Forum’s point matters in practice:
Good ITAM helps validate that assets and software are legit, and it produces the kind of business intelligence you lean on when continuity planning stops being theoretical.
Now the real-life scene.
Jessica (name is changed), procurement lead, is on a renewal call with Microsoft for Office 365. The rep insists the company needs 1,500 licenses. Jessica doesn’t argue. She opens her ITAM data and checks three things that almost always expose the gap between “assigned” and “used.
- First, sign-in activity. She flags accounts with no usage in 60–90 days, because people leave, contractors roll off, and mergers create ghosts.
- Then, duplicates. Same human, two identities. It happens after domain changes, SSO shifts, “temporary” accounts that never die.
- Finally, service accounts and shared mailboxes that got licensed like full users because someone clicked the default option six months ago.
The report shows 300 inactive users and 200 duplicated accounts. Not a vibe. A list with timestamps and identifiers.
She goes back to the negotiation with a clean ask: 1,000 seats, not 1,500. The delta isn’t small. If those are E5 seats with a couple of add-ons, that cut can easily mean around $2M over three years.
The pushback comes, of course. Jessica doesn’t debate licensing philosophy. She sends the report, plus the remediation plan and the date the unused accounts will be removed. Silence. Then the revised quote.
That’s the leverage you get from asset management in ITIL. You don’t “negotiate harder.” You show up with reality.
6. Facilitating digital transformation
Digital transformation isn’t the hard part. It’s the hidden dependencies that bite you right when you’re about to celebrate.
ITIL asset management makes transformation safer because it keeps your asset data usable during change. Not “accurate in theory.” Usable when someone says, “we’re cutting over tonight.” You know what’s connected, what’s still on-prem, who owns it, and what the blast radius looks like if one piece doesn’t move with the rest.
IBM talks that intelligent asset management "puts data and AI to work to optimize critical asset performance and automate enterprise operations."
I remember a customer where the CTO was pumped about moving legacy apps to Amazon Web Services and running them on EKS. The plan looked clean on the slide. Ahmed, the cloud migration lead, still had that “this feels too quiet” vibe.
He ran a dependency scan in Cloudaware and immediately saw the problem: the app tier was ready for Kubernetes, but a critical database was still sitting on-prem. Not “optional.” Not “nice to have.” The kind of dependency that turns a cutover into a production outage and a long, awkward rollback.
So he paused the switch. Added a migration sequence that matched reality. Replication first, then network paths and security rules, then a controlled app config change, then cutover with a rollback plan that wasn’t just “pray.” A few extra hours of planning saved them a day of damage control. The CTO got the smooth launch they wanted. Ahmed got to keep his weekend.
7. Enhanced disaster recovery planning
In the event of a system failure, knowing what assets exist and where they are deployed is critical for swift recovery. IT asset management provides a detailed map of your IT landscape, aiding in effective disaster recovery strategies.
As highlighted by the ITAM Forum,
"ITAM can also help to verify the authenticity of hardware and software assets to make sure they are what they claim to be and help to provide business intelligence to support business continuity planning."
Example: At 3 AM, the incident response team’s phones exploded with alerts. A ransomware attack had locked 50% of production VMs.
Ethan, the IT Support Lead, rushed to his laptop, heart pounding. Checking the CMDB backup logs, he saw that Cloudaware ITAM had automatically logged and mapped every asset’s recovery path.
Within hours, the team restored everything from clean snapshots, avoiding weeks of downtime.
7 challenges you may face in ITIL asset management
After years working in the cloud industry, I’ve seen the same IT asset management challenges surface across different organizations — whether they’re managing AWS, Azure, or hybrid environments. Some struggle with service management inefficiencies, while others find themselves buried in unnecessary costs and security risks.
So here, I’m sharing real stories from my experience helping companies clean up their IT asset messes. (Names have been changed, but the situations? 100% real.)
If you’re an IT Cloud Architect or DevOps Engineer, these scenarios will hit close to home — but more importantly, you’ll see how ITIL asset management turns chaos into control.
The phantom asset problem – when CMDB is lying to you
Sam, a Cloud Engineer, was confident that his company’s AWS infrastructure was optimized — until a Cloud FinOps report exposed an unexpected $250K in monthly cloud spend.
He checked Cloudaware’s ITAM dashboard and found the culprit: 400 orphaned EC2 instances and unused EBS snapshots across multiple AWS accounts. These assets had no owner, no service attached, and had been running silently for months.
Why it happens: Lack of ITIL-aligned lifecycle management for cloud resources.
Impact: Uncontrolled IT costs, compliance risks, and wasted budgets.
Fix: Automated IT asset tracking, lifecycle policies, and clear ownership tagging.
By implementing automated decommissioning policies, Sam’s organization slashed its cloud waste by 40% in a single quarter.
The shadow IT nightmare – when security is always a step behind
Maya, a security analyst, is doing the usual scan review. Not dramatic. Just triage, coffee, dashboards.
Then she spots it. A PostgreSQL database sitting on an unauthorized Microsoft Azure VM. Publicly reachable. No encryption at rest configured. Backups missing. Access controls basically “whoever has the URL.” If you’ve ever had to explain that kind of setup to audit, you already know how that meeting ends.
The worst part is the reason. It wasn’t malice. A product team needed a database fast, so they spun it up outside ITIL asset management. No service record. No owner in the CMDB. No tags that tie it to a cost center. No guardrails. It existed in the exact blind spot where policy breaches grow legs.
Why this happens: Speed wins when governance is slow. Teams bypass asset controls because the approved path feels like a ticket queue and a calendar invite. Self-serve cloud makes it easy to create “just one VM,” and suddenly you’ve got production data on something nobody is managing.
What it breaks: The risk isn’t abstract. You get unmanaged exposure, configuration drift, and a pile of unknowns. Who patches it. Who rotates creds. Which data lives there. Whether it’s even supposed to exist. That’s how a simple misconfiguration becomes a security problem you discover late.
What actually fixes it:
- Start with discovery that doesn’t rely on humans remembering to log assets.
- Pull asset data straight from cloud APIs on a schedule. Minutes, not quarters.
- Reconcile what you find into the CMDB, then flag anything with no owner, no service mapping, or missing tags.
- Add governance that’s hard to dodge. Tag policies, account/subscription boundaries, approvals for public endpoints, encryption requirements by default.
- Feed it into your security signals so “unknown asset” is treated like “high priority,” not “someone will clean it up later.”
With real-time discovery in Cloudaware, Maya’s team found and removed 35 unauthorized workloads and cut the attack surface by 25%. No heroics. Just fewer places for surprises to hide.
The compliance panic – when auditors show up unannounced
Jake got the email that ruins your day before it even starts. “We’re initiating an Oracle license audit.” No warm-up. No grace period. Just a deadline and that polite tone that means, “prove it.”
He opens the ITAM view in Cloudaware and sees the real problem immediately. About 50 Oracle Database instances scattered across VMware, Amazon Web Services, and Microsoft Azure. The estate exists. The entitlements are… somewhere. There’s no centralized record that ties deployments to the licenses they’re supposed to be covered by. That gap is where six-figure penalties are born.
This is the compliance trap in ITIL asset management. You can be doing “asset tracking” and still be unprepared for an audit because audits don’t ask, “do you have a list.” They ask, “can you prove effective license position, by environment, by version, by usage pattern, with evidence you can reproduce.”
Why it happens: SAM is often manual and optimistic. Someone updates a spreadsheet when they remember. ITSM compliance fields get filled out inconsistently because they’re not connected to what’s actually deployed. Hybrid makes it worse. Virtualization, clones, golden images, short-lived test environments, shadow subscriptions. All of it creates install and usage drift faster than humans can document it.
What it costs: The fine is only one part. The hidden cost is the freeze. Engineers stop doing normal work because everyone becomes an audit assistant. Change slows down. People avoid touching systems because they’re afraid of making the picture messier. Leadership gets nervous and starts asking for “daily status updates,” which helps nobody.
What fixes it in real life: You want asset management in ITIL that treats licensing as a living control, not an annual scramble.
- Automatically discover where the software is running across on-prem and cloud.
- Normalize and count what matters for licensing. Edition, deployment type, cores, virtualization context.
- Map entitlements to installations so you can show coverage, not just inventory.
- Monitor continuously so you catch drift before an auditor does.
Jake’s team used automated ITIL asset management practices to pull a defensible compliance picture together fast enough to avoid a $1.2M hit. Not because they argued with the auditor. Because they showed the evidence.
The asset lifecycle black hole – where old hardware never dies
This is a story of a Data Center Engineer who found a fully powered rack of servers in a supposedly decommissioned colocation facility. A quick CMDB lookup? No owner, no attached services, but still pulling power.
Why it happens: No structured IT asset lifecycle management process.
Impact: Wasted operational costs, security risks from unsupported software.
Fix: Automated end-of-life tracking, ITSM workflows for asset decommissioning.
After deploying automated IT asset lifecycle tracking, Lena’s company decommissioned over $3M worth of legacy hardware — without impacting operations.
The vendor lock-in trap – when you’re paying for what you don’t use
Jessica, a Procurement Lead, was locked in a tough negotiation with Microsoft over an Office 365 renewal. Microsoft insisted her company needed 3,000 licenses — but Jessica had ITAM data that proved otherwise.
She ran a usage report in Cloudaware and found:
- 500 inactive user accounts.
- 300 duplicated licenses assigned to employees who had already left.
- Another 200 licenses tied to deprecated services.
Why it happens: Lack of real-time IT asset tracking in software asset management.
Impact: Millions wasted on unused SaaS licenses.
Fix: ITIL-driven contract optimization, usage-based license tracking.
Jessica cut the contract by 1,000 seats, saving $2.5M over three years.
Disaster recovery confusion – when an outage turns into chaos
A major Azure outage hit a critical production region, and David, an Incident Response Lead, needed answers — fast.
Which VMs were affected? Which services were down? What’s the recovery priority?
Problem? The CMDB was outdated, asset dependencies were missing, and recovery times dragged on for hours.
Why it happens: Poor IT asset mapping, outdated disaster recovery workflows.
Impact: Longer downtimes, lost revenue, frustrated leadership.
Fix: ITIL service dependency mapping, real-time recovery workflows.
With ITIL-based IT asset dependency mapping, his team reduced future recovery times by 60%.
The IT budget black hole – when cost optimization is an afterthought
Every quarter, Ethan, the Cloud FinOps Lead, had to explain why AWS costs kept spiraling.
A deep dive into Cloudaware ITAM revealed the issue:
- Ghost Kubernetes nodes running at 4x the needed capacity.
- Idle EC2 instances tagged as "critical" — but never actually used.
- Duplicate SaaS subscriptions spread across different teams.
Why it happens: Lack of real-time cost tracking in IT asset management.
Impact: Millions wasted, frustrated leadership, constant firefighting.
Fix: Automated cloud cost monitoring, ITSM-integrated rightsizing recommendations.
By deploying real-time IT asset cost tracking, Ethan’s company cut cloud spend by 30% in just three months.
What’s the biggest IT asset nightmare you’ve faced? Let’s talk. 🚀
5 Best Practices for IT Asset Management within ITIL
After working with Cloudaware’s CMDB team and helping clients navigate multi-cloud hybrid infrastructures, I’ve seen how IT asset management within ITIL can make or break IT operations. Cloud sprawl, security risks, compliance gaps, and budget overruns are common, but when teams apply the right ITIL-aligned strategies, they gain visibility, control, and efficiency.
Here are five expert-backed best practices that have transformed how organizations handle IT asset management in ITIL.
1. Real-time asset discovery prevents costly blind spots
One of the biggest ITAM failures I’ve seen is when organizations rely on static CMDBs. In fast-moving multi-cloud environments, where AWS Lambda functions scale up instantly and Kubernetes nodes come and go, asset records go out of date within hours if they’re not dynamically updated.
To fix this, I recommend event-driven asset discovery that integrates with AWS Config, Azure Policy, and Kubernetes API to capture changes as they happen. Real-time IT asset management ensures that every server, container, and cloud function is accounted for, giving teams the visibility they need to optimize resources.
2. Mapping every asset to a business service eliminates chaos
An asset list is nice. It’s also useless the second something breaks.
ITIL asset management gets real when you can take any CI and answer one question without guessing: what business service does this support? If the answer is “uh… not sure,” you don’t have a CMDB. You have a storage unit.
I’ve watched teams burn hours on outages because their records stopped at “EC2 instance exists” or “VM exists.” No service link. No dependency chain. No ownership. So every incident becomes a group chat where five people say, “not my system,” and one person starts tailing logs like it’s 2012.
Here’s how asset management in ITIL removes that chaos. You turn the CMDB into a service map that’s actually usable in the moment:
- Service first. Create a business service record like “Checkout API” or “Customer Portal.” Give it an owner and a criticality tier.
- Attach what runs it. Map app tier, data tier, queue, DNS, load balancers, KMS keys, IAM roles. The boring stuff that causes real outages.
- Model dependencies. “This EKS namespace talks to that RDS cluster through this security group.” Now you have causality.
- Make it dynamic. The map updates as the environment changes, or it becomes a lie within a sprint.
Tooling-wise, this is where Cloudaware CMDB paired with AWS Service Catalog and Azure Resource Graph helps. You’re pulling relationships from the sources of truth the cloud already has, then stitching them into a model that matches how services behave in production.
The payoff is immediate. Incident response becomes a shorter path: identify affected service, see dependencies, ping the right owner, change the right thing. You stop treating outages like a scavenger hunt.
3. Automating asset lifecycle management prevents resource hoarding
I once opened a cloud account and it felt like walking into an abandoned office building with the lights still on.
Hundreds of VMs. Outdated images. No owner tag. Some of them running versions that should’ve been dead two patch cycles ago. Nobody shut them down because nobody wanted to be the villain who breaks “something important.” That fear is how sprawl becomes a budget line. It’s also how unpatched systems survive long enough to become a real security story.
This is where ITIL asset management has teeth. You don’t ask humans to remember lifecycle steps. You encode them.
In asset management in ITIL, every asset should have a lifecycle state you can trust: requested, approved, provisioned, in use, change pending, retired. If you can’t tell what state an asset is in, you can’t manage it. You can only pay for it.
What I recommend is lifecycle enforcement that’s automated and boring, in the best way.
- Set expiry on non-prod by default. When a developer spins up a test VM or an EKS node group for an experiment, it gets a TTL. 7 days. 14 days. Whatever matches your sprint rhythm. No TTL, no deploy. Use Terraform to make this a required variable, not a suggestion.
- Make “unused” a trigger, not a hunch. Define what unused means. CPU under 1–2% for 14 days. No inbound connections. No deploys. Then flag it automatically and start an approval workflow before decommissioning.
- Track end-of-life like you track incidents. If an OS image or database version hits EOL, that asset should flip into a noncompliant state with an owner attached. Patch plan or retire. Choose one. Enforce it through policy.
On AWS you can pair this with guardrails and automation around Auto Scaling and scheduled policies. Microsoft Azure has similar options via Azure Automation for scheduled runbooks and remediation. The specific tooling matters less than the principle: lifecycle rules should execute without waiting for a quarterly cleanup campaign.
Do that and you get three wins at once. Spend drops because zombies don’t live forever. Security improves because old software stops hanging around in dark corners. Your environment stays understandable, which is underrated until you’re on call at 2 a.m.
4. Integrating ITAM with security prevents shadow IT risks
A major problem I’ve encountered is security teams finding assets they never knew existed — unauthorized cloud databases, rogue Kubernetes clusters, or unsecured SaaS accounts. Without IT asset management integrated with security, these risks go undetected.
I’ve seen massive improvements when organizations sync their ITAM solutions with SIEM tools like Splunk, AWS Security Hub, and Azure Sentinel. Automating security compliance checks based on real-time ITAM data helps teams catch:
- Unapproved assets before they create vulnerabilities.
- Misconfigured cloud resources that expose sensitive data.
- Expired ACM certificates and outdated software before they cause compliance failures.
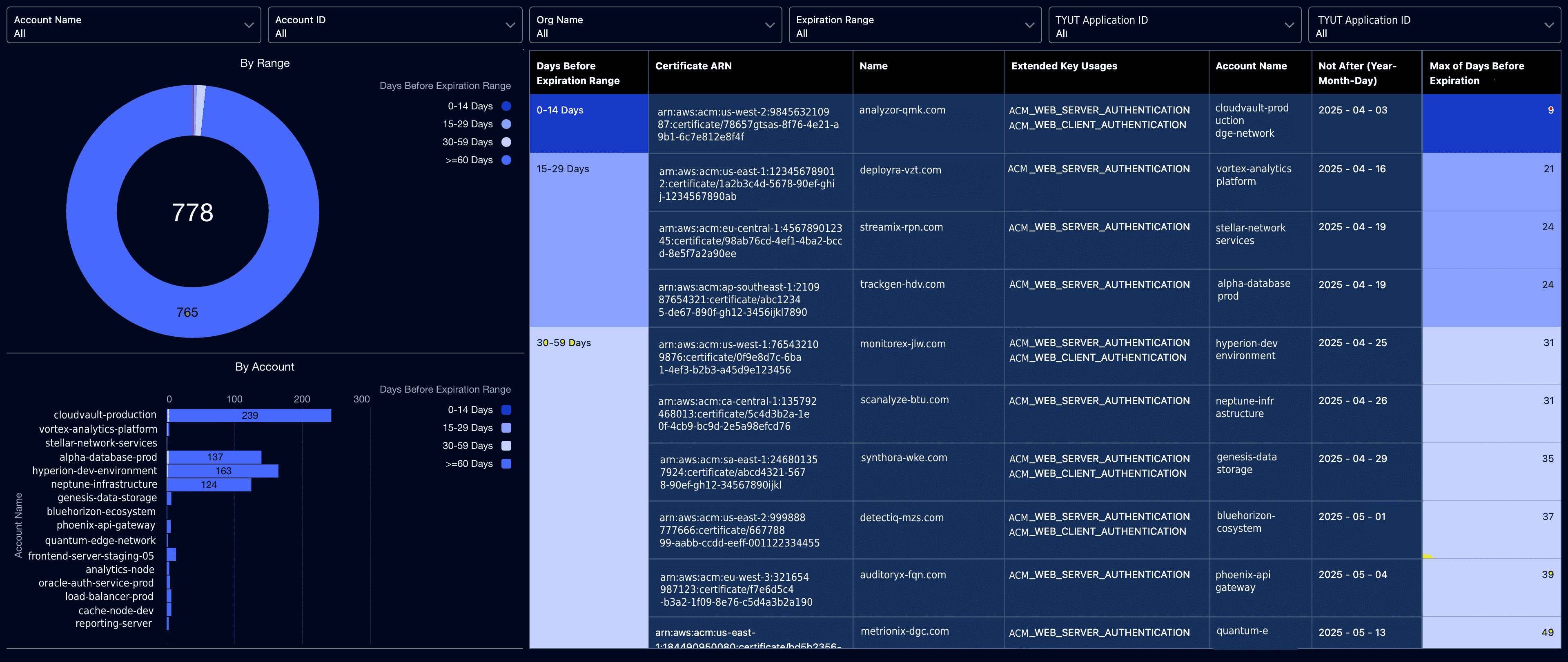
Aligning IT asset management with security solutions eliminates blind spots before they turn into security breaches.
5. Treating cost optimization as a continuous process stops budget surprises
Budget surprises don’t happen because finance is picky. They happen because cloud spend is a real-time system and most teams review it like a monthly statement.
In ITIL IT asset management, cost control works when it’s wired into the same lifecycle logic you use for ownership and change. You don’t wait until the invoice lands. You notice drift while it’s still small, then you fix the cause, not the symptom.
Here’s what I push teams to do when they want less “why is this so high” and more “yep, we expected that.”
- Give every service a spending boundary that makes sense for its tier, then alert on weirdness. Not “AWS is expensive,” but “Checkout jumped 18% week over week and the change started after Tuesday’s deploy.”
- Look for quiet waste in the places that scale without asking permission: oversized VMs, Kubernetes node groups with high requests and low actual usage, old load balancers nobody points to anymore, licenses assigned to humans who left three months ago.
- Make tagging non-negotiable. If you can’t tie spend to an owner and a business service, you can’t govern it. You can only argue about it.
Tooling is the easy part. Pull in cost signals from Amazon Web Services and Microsoft Azure native cost views, then connect those signals to your asset records and service map so anomalies have context. That’s the move. Spend without context is noise.
One customer using Cloudaware cut their AWS bill by about 30% after they enforced automated cost tagging and anomaly detection. No dramatic re-architecture. They just stopped paying for things nobody could name, justify, or even find.
What’s the nastiest cost surprise you’ve had recently, and where did it hide?
ITIL-Compliant Asset Management Software
Cloudaware
Keeping track of assets across multi-cloud plus on-prem isn’t “hard.” It’s noisy. Three portals, five naming conventions, tags that mean different things to different teams, and an inventory that’s out of date the moment someone applies Terraform.
This is where ITIL asset management either becomes useful, or it becomes paperwork. The useful version needs two things: fast discovery and enough context to make a decision without opening six tabs.
Cloudaware is built for that reality. It auto-discovers and normalizes inventory across Amazon Web Services, Microsoft Azure, Google Cloud, plus Oracle Cloud and Alibaba Cloud, and it can pull in on-prem via API and direct network discovery.
The coverage isn’t just “we see EC2 and a few basics.” Their CMDB discovery is positioned as supporting thousands of cloud services, which matters when you’re trying to govern what teams actually use, not what your CMDB template expected in 2018.
What I like is the emphasis on enrichment. It’s not “CI exists.” It’s “CI exists and here’s why you should care.”
So if you click into an Amazon EC2 instance, you’re not stuck with a dumb record. You’re looking at something closer to an operational profile:
Platform / account: AWS, production account, region, VPC, subnet
Ownership signals: tags, cost center, app or service name, team alias
Spend context: month-to-date + projected cost, plus what’s driving it (compute vs storage vs data transfer)
Related items: load balancer it sits behind, security groups, volumes, IAM role, Kubernetes node group association if it’s part of a cluster
Risk hints: stale patches, public exposure via security group rules, missing encryption on attached storage, policy breaches against your baseline
Here’s an example in the same spirit as your draft, but with the kind of details you actually use:
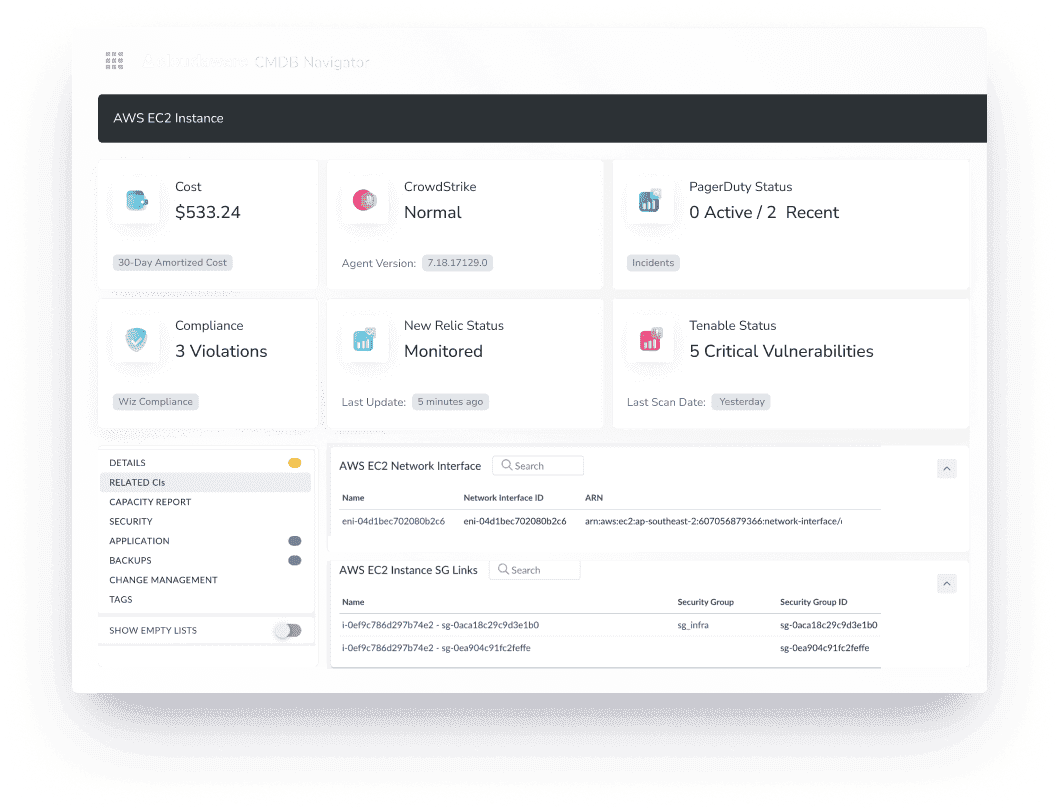
That’s the point. You don’t just know it exists. You know what it’s connected to, what it costs, and what might bite you later.
And because this is tied to day-to-day management, the add-on modules become less “features” and more “how you run the place”:
✅ FinOps work lands faster when spend is attached to real owners and services, not a mystery account.
✅ Vulnerability management gets practical when you can trace risky assets back to the team that can fix them.
✅ CSPM becomes less noisy when policies evaluate assets with context, tags, and environment boundaries.
✅ SIEM and compliance visibility improve when logs and asset context meet in the same system, so investigations don’t start with “which account was that in?”
Pricing
Cloudaware follows a server-based pricing model, starting at 50 servers and 1 user. Managing 100 servers? Expect around $400/month. Need to scale? Check out Cloudaware's pricing calculator to customize your plan.
Want to see how it works in your environment? Take advantage of the 30-day free trial and experience real-time configuration management without the commitment.
Pros & Cons of Cloudaware IT Asset Management
✅ Unmatched Multi-Cloud Support: Manage AWS, Azure, Google Cloud, and on-prem from a single platform.
✅ Deep Asset Intelligence: More than just discovery — it enriches each CI with billing, security, and compliance data.
✅ Seamless Hybrid Integration: Connects cloud and physical infrastructure into a unified view.
⚠️ Initial Learning Curve: With so many advanced features, some users need time to adjust. But Cloudaware's support team helps tailor the setup to fit your needs.
ServiceNow
Managing complex IT environments is no small task — especially when you’re juggling on-prem, hybrid, and multi-cloud assets. That’s where ServiceNow steps in. This enterprise-grade configuration management tool provides a centralized view of all IT assets, simplifying tracking, compliance, and service dependency mapping.
ServiceNow is trusted by large enterprises, tech leaders, and healthcare organizations for its ability to scale, integrate, and automate IT asset management workflows. With built-in security features like encryption and role-based access, it also ensures that your configuration data remains protected.
If your business runs on a hybrid cloud setup with multiple accounts, ServiceNow delivers flexibility and scalability to match your infrastructure’s growth.
Core Features of ServiceNow’s Configuration Management Tool
🔹 Automated Asset Discovery. Continuously scan and identify IT assets across cloud and on-prem environments.
🔹 Dependency Mapping. Visualize how configurations relate to services, making troubleshooting easier.
🔹 Incident & Change Management. Seamlessly integrate with ITSM processes to improve service stability.
🔹 Cloud & On-Premise Support. A hybrid-ready solution that tracks assets across your full IT ecosystem.
🔹 Real-Time Data Syncing. Get live updates to maintain an accurate and current CMDB.
🔹 Customizable Dashboards. Tailor visual reporting and asset insights to fit your organization’s needs.
🔹 Enterprise-Grade Security. Encryption and role-based access control ensure data integrity and compliance.
ServiceNow isn’t just about tracking assets — it’s about creating an organized, resilient IT environment where service disruptions are minimized, compliance is maintained, and configuration management is effortless.
Pricing
ServiceNow follows a subscription-based pricing model that varies by organization size and the number of configurations managed.
💲 Estimated costs:
- Basic plans start at $10,000 per year.
- A mid-sized company managing 1,000 assets can expect to pay between $20,000 and $30,000 annually.
Not sure if it’s the right fit? ServiceNow offers a 30-day trial, so you can explore its features before committing to a full deployment.
Pros & Cons
✅ Feature-Rich & Scalable. Handles massive IT environments without breaking a sweat.
✅ Seamless ITSM & Cloud Integrations. Works effortlessly with IT service management platforms and major cloud providers.
⚠️ Limited Support for Emerging Resource Types. Not as flexible for cloud-first, DevOps-driven architectures.
⚠️ Can Feel Heavy for Agile Teams. More suited for structured enterprise workflows than fast-moving cloud operations.
⚠️ Steep Learning Curve. New users may find the interface complex, requiring additional training.
For enterprises with expanding IT infrastructure, ServiceNow is a proven, reliable solution that scales with your organization’s needs.
Read also: Cloudaware CMDB vs. ServiceNow
Device42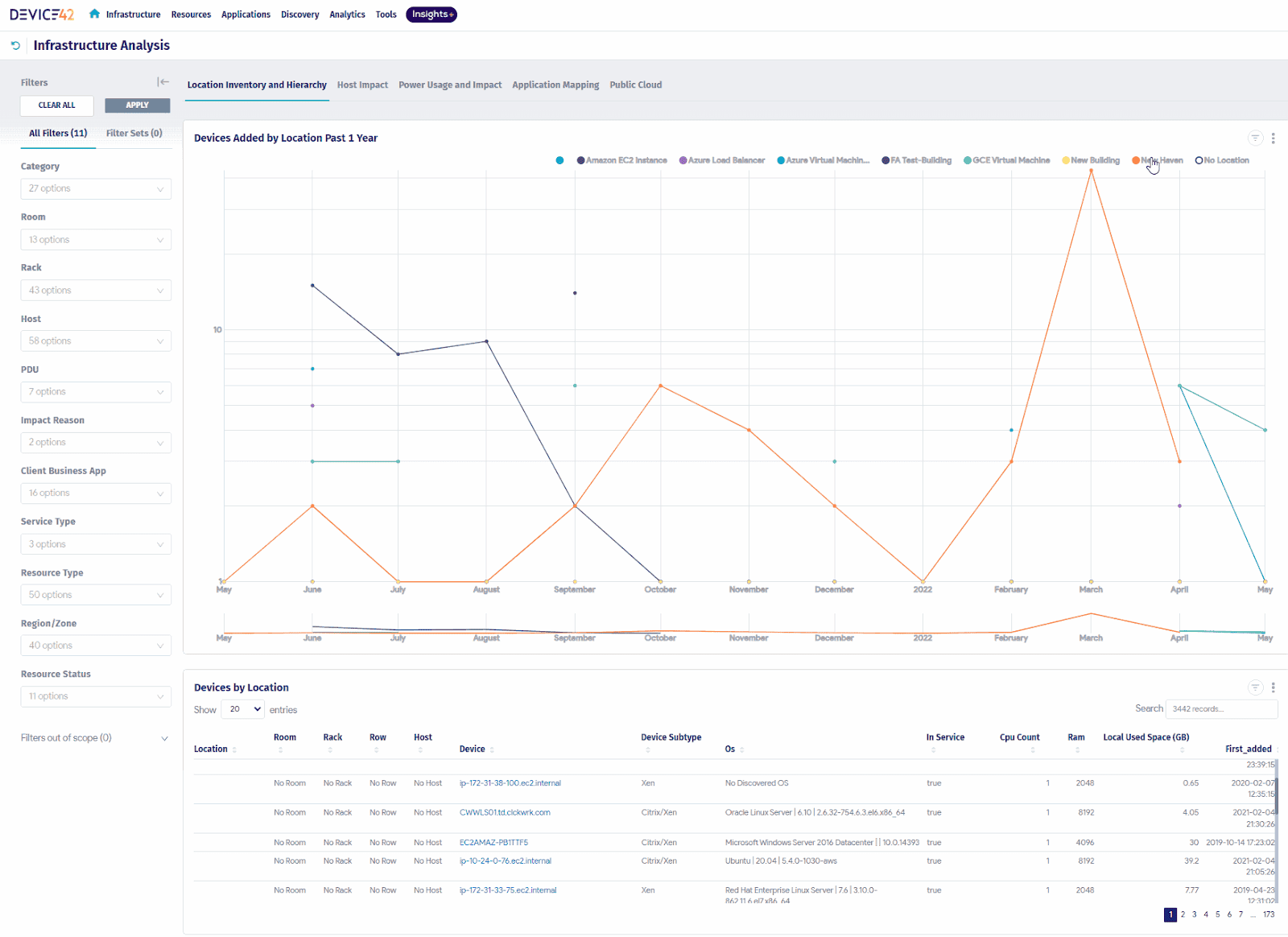
Managing multi-cloud and hybrid environments is no easy feat — especially when IT teams need visibility across thousands of devices, applications, and dependencies. Device42 steps in as a powerful configuration management tool that unifies cloud, on-prem, and virtual assets into a single, structured view.
Designed for Data Center Managers and IT Operations teams, Device42 simplifies IT asset tracking, ensures compliance, and helps prevent configuration-related failures. Whether you’re dealing with AWS, Azure, VMware, or physical data centers, Device42 ensures that everything is accounted for and optimized.
With real-time asset discovery and dependency mapping, teams gain full transparency into their IT landscape, leading to faster troubleshooting, smarter decision-making, and reduced downtime.
Features
🔹 Automated Asset Discovery. Scans AWS, Azure, and on-prem environments to build a real-time asset inventory.
🔹 Hybrid Infrastructure Mapping. Tracks physical servers, VMs, and cloud workloads for complete visibility.
🔹 Application Dependency Mapping. Connects applications to infrastructure components, ensuring seamless migrations and updates.
🔹 License & Compliance Management. Keeps teams audit-ready with automated software tracking.
🔹 Security & Misconfiguration Detection. Flags vulnerabilities and compliance gaps before they become problems.
🔹 Change Management Tracking. Logs every modification to your environment, reducing unplanned outages.
🔹 API Integrations. Connects with ITSM tools like ServiceNow, Jira, and Splunk for a smoother workflow.
🔹 Dynamic Dashboards. Provides real-time insights into performance, capacity, and risks.
With Device42’s holistic IT asset management, teams stay ahead of potential risks, reduce inefficiencies, and gain full control over their infrastructure.
Pricing
Device42 follows a flexible pricing model based on the number of assets you manage.
💲 Estimated costs:
- Starting at $3,500 per year for smaller teams.
- $5,000–$8,000 per year for organizations managing 500+ devices, with advanced automation and visualization features.
Want to explore Device42 before committing? Take advantage of the 30-day free trial to see how it fits into your IT asset management strategy.
Pros & Cons
✅ User-Friendly Interface. Highly rated for its intuitive navigation and ease of use.
✅ Excellent Customer Support. Fast, responsive support teams help with implementation and troubleshooting.
✅ Comprehensive Asset Tracking. Covers cloud, on-prem, and networking infrastructure.
✅ Remote Access. Teams can update asset data from anywhere, making IT management more flexible.
⚠️ Complex Task Execution. Some workflows require multiple steps, slowing down certain actions.
⚠️ Limited Backup Customization. Backup features are pre-configured, limiting user-defined options.
⚠️ No Command Line Access. Admins have no direct CLI control over the system or remote collectors.
Read also: Find the Best Hybrid Multi-Cloud CMDB: Cloudaware vs. Device42
How to choose the right one
Picking an asset discovery tool is basically choosing how you want to suffer for the next two years.
Some tools look polished and still behave like a spreadsheet with a login screen. Others “discover” by hammering your network until someone in ops asks who just DDoS’d the internal VLAN. Then there are the ones that technically work, but only if you babysit agents forever.
If you’re doing ITIL asset management, the tool has one job: keep your asset truth current enough that people trust it when things break.
Here’s what separates “usable” from “we regret this purchase.”
1. Agentless discovery, unless you enjoy agent babysitting. Agents turn into a second fleet you maintain. They fall behind on versions. They break after OS upgrades. Someone blocks them. Your CMDB quietly rots. What you want is agentless collection wherever possible. Cloud APIs for AWS and Azure. Virtualization inventory for VMware. Network and directory sources for on-prem. Fast, quiet, repeatable.
Quick test: ask how they discover 10,000 assets across hybrid without agents. If the answer is “install this everywhere,” you already know how your next quarter looks.
2. Updates that match the pace of change. Last week’s data is a bedtime story. Your environment changes daily. Sometimes hourly. A tool can claim “real time” and still only refresh once a day. That’s not real time. That’s a snapshot. In asset management in ITIL, you want changes reflected fast enough that a security team isn’t chasing assets that no longer exist, and a platform team isn’t debugging a service map from yesterday.
Quick test: ask for their default refresh intervals by source. Cloud API sync. On-prem discovery. Relationship updates. If you can’t tune it without professional services, that’s a red flag.
3. Relationships, not just a list of things. Inventory alone doesn’t shorten incidents. Relationships do.
When an alert fires, you need to go from “this asset is unhappy” to “this service is impacted” without detective work. That means the tool can model dependencies like app tier to DB, cluster to node group, load balancer to target group, IAM role to workload. Not perfectly. Just reliably enough that you can trust the blast radius.
Quick test: pick one production service and ask them to show you its dependency chain end to end. If the demo stops at “here are the servers,” you’re buying an address book.
4. Integrations that don’t trap your data. You already have an ecosystem. ITSM, ticketing, cloud providers, security scanners, identity, cost management. Your discovery tool should fit into that flow instead of becoming another silo that only its own UI can interpret.
Look for clean API access, export options, and stable connectors. “We integrate” should mean “we can sync bi-directionally and keep IDs consistent,” not “we can send a CSV.”
Quick test: ask what happens when an asset is renamed, moved accounts, or re-created. Do they maintain identity across changes, or do you get duplicates forever?
5. Automation that enforces hygiene, not automation theater. Manual tagging, manual compliance checks, manual reports. That’s how you end up with good intentions and bad data.
A strong ITAM tool can automate the boring parts: enforce required tags, flag orphaned resources, open tickets for missing owners, detect unused assets by policy, trigger approvals before decommissioning. It should support your lifecycle states, not just store them.
Quick test: ask them to show an automated rule that finds “no owner + public exposure + prod” and routes it to the right team with context. If it can’t do that, you’ll be writing custom scripts for everything.
6. Security and audit controls that treat the CMDB like the crown jewels. Your CMDB is a map of your infrastructure. If it leaks, an attacker gets a blueprint. If it’s editable without traceability, your auditors will have questions you don’t want.
Baseline expectations: encryption, RBAC that’s granular enough for real teams, audit logs that show who changed what, and separation by environment where it matters.
Quick test: ask to see the audit trail for one CI. Creation, updates, who did it, what changed, when. If that’s missing or flimsy, you’re building compliance risk into your source of truth.
Where to start
ITIL asset management is more than just tracking hardware and software — it’s about optimizing costs, improving security, and ensuring compliance in your multi-cloud and hybrid environments. The right IT asset management (ITAM) strategy helps eliminate waste, reduce risks, and streamline operations through real-time discovery, automation, and integration with IT service management (ITSM) tools.
Where to start?
- Assess your current asset visibility. Do you know what’s running where?
- Automate discovery & tracking. Avoid outdated, manual records.
- Align ITAM with ITIL best practices. Ensure compliance and efficiency.
Still unsure? Talk to an expert for free and get tailored advice! 🚀
More useful info
📌 Top 11 IT Asset Management Best Practices from ITAM expert
📌 15 Software Asset Management Tools: Features & Pricing Compared
📌 What is CMDB Discovery: 10 best practices for cloud infrastructure
📌 9 Configuration Management Best Practices for Multi-Cloud Setups
📌 Top 8 CMDB Benefits: Why Companies Use Multi-cloud CMDB in 2025
📌 What is service mapping: How It Works. Best Practices for IT Teams
