Most of us ship, not shut down.
We roll out workloads, wire up services, and push code. Every day.
Cleanup? That’s a backlog item… until finance flags idle resources or an auditor wants destruction proof that doesn’t exist. Then you spot the “retired” VMware datastore still alive. Or a disk no one ever wiped.
Across AWS, Azure, GCP, VMware, and on-prem, lifecycle models drift. Evidence scatters — consoles, spreadsheets, ticket comments. Without a unified control plane, IT asset disposition turns into vibes, not verification.
This piece is a practical end-of-life runbook: discover → approve → sanitize → document → prove. We’ll get specific — NIST SP 800-88 wipe methods, CMDB state transitions, R2/e-Stewards chain of custody, Jira/ServiceNow approvals, evidence hashing, and automated guardrails that help you pass audits and kill zombie costs.
What you’ll learn — answered through the problems that actually hurt:
- Which retired CIs are still incurring quiet costs and how to surface them in minutes.
- Where decommissioning breaks first: ownership, sanitization, or proof, and how to bulletproof each step.
- How to enforce “Pending Decom → Sanitized → Disposed” with policies, not hope.
- How to collect and bind Certificates of Destruction, wipe logs, and approvals into one exportable evidence bundle.
- Who should own license reclamation when a CI goes dark, ITAM or procurement, and how to track the savings.
- How to prevent recoverability via snapshots, versions, replicas, or stray KMS keys.
- How long to retain artifacts and how to guarantee immutability.
But first, let’s check if we are on the same page about the basics.
What Is IT Asset Disposition (ITAD)?
When people ask what IT asset disposition is, they usually think about the physical part, like someone picking up old servers and sending them to recycling. That is part of it, but the real work starts long before any hardware leaves the building.
IT asset disposition, or ITAD, is the process of identifying, approving, sanitizing, and documenting the retirement of technology assets. It covers everything from virtual machines to software licenses. In regulated environments, information technology asset disposition also includes storing the records that prove every asset was wiped and disposed of according to policy.
ITAD also applies to non-physical assets: cloud snapshots, storage buckets, unattached volumes, IAM accounts, and SaaS entitlements. Treating them differently is one of the most common reasons audit findings appear.
In regulated environments, cloud artifacts must follow the same data sanitization and evidence process as physical hardware.
So what actually happens in an ITAD process? Usually four things:
- Inventory and ownership: Discover and assign owners.
- Data sanitization: Execute and record NIST SP 800-88 methods.
- Lifecycle update: Move CI through clear states in the CMDB.
- Evidence collection: Store approvals, hashes, and CoDs in one place.
Retention is another critical element. Most organizations keep ITAD evidence for 3–7 years depending on audit and data classification requirements. Consistent retention is what turns ITAD from a one-off cleanup into a provable control.
If one of these steps is missing, things start to break down. In large organizations, missing even one of these checkpoints can invalidate an entire audit trail. In environments managed through multiple CMDBs or cloud consoles, keeping one consistent ITAD process means you can trace every asset’s end-of-life without jumping between tools.
Before we go any further, it's helpful to clear up some terms that are often mixed up 👇
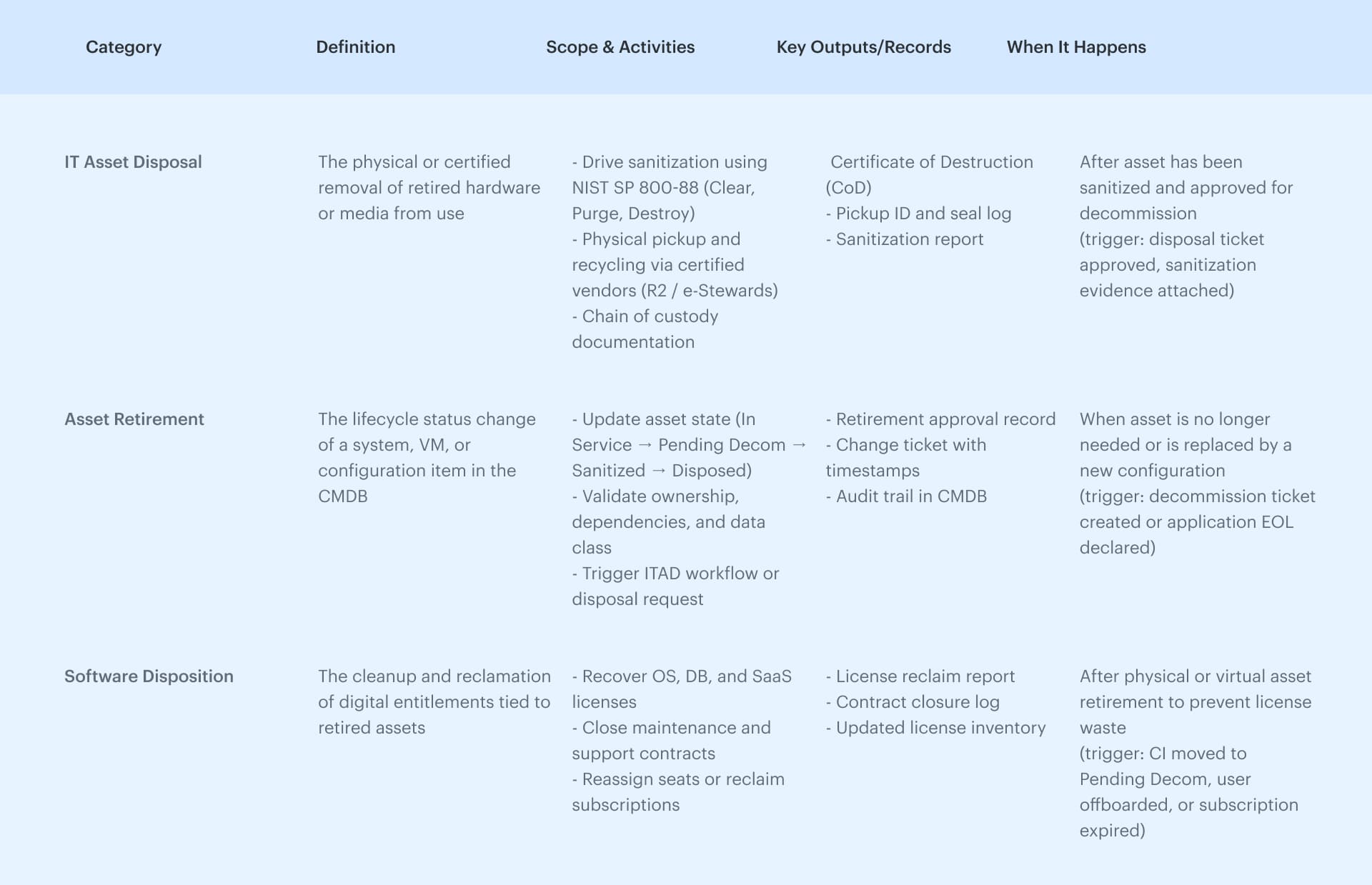
IT Asset Disposal vs Asset Retirement vs Software Disposition
These terms describe different steps in the same lifecycle. Understanding where each fits helps keep records clean and compliance evidence easy to find.
In practice, these three stages often overlap, especially in hybrid environments where hardware, virtual machines, and SaaS licenses retire on different timelines. A clean ITAD process ensures that all three stay synced, so nothing falls through the cracks.
Best practice from Kristina, Senior ITAM expert at Clodaware:
Another key control point is state transition enforcement, where assets shouldn’t move to “Disposed” unless they have linked sanitization evidence and zero dependencies.
This approach doesn’t replace certified destruction, but it ensures that lifecycle data, ownership, and verification remain consistent across clouds and data centers, even when physical and virtual disposal happen on different timelines.
How Cloudaware helps:
Cloudaware serves as the visibility and data-governance layer connecting all these stages.
- Every CI in the Cloudaware CMDB reflects its real-time cloud state and stores metadata like disappearance time to confirm when it was removed.
- Through custom fields and automation rules, organizations can track approvals, attach evidence, or flag missing data.
The IT Asset Disposal Process: How it works
A structured IT asset disposal process makes the difference between an organized decommissioning and a costly cleanup later. Most teams follow the same basic flow, but the strength is in the consistency. The goal of any information technology asset disposal program is simple — remove assets safely, document every action, and prove compliance afterward.
In a hybrid cloud environment, this process becomes asynchronous. A VM may retire today, its storage buckets next week, and related licenses months later. Without automation, tracking all these moving parts across clouds is almost impossible.
That’s why mature ITAD programs standardize every step and tie them back to a single CMDB record.
Here’s how that works in practice:
- Identify candidates. Identify idle or orphaned assets, like volumes that aren't attached to anything, IPs that aren't being used, or instances that haven't been active in weeks.
- Approve changes. Track who gave their approval and when the retirement was made. These approvals are frequently triggered by change tickets or workflow tools like Jira and ServiceNow.
- Sanitize data. Use NIST SP 800-88 "Clear," "Purge," or "Destroy" depending on the type of data. Make sure to delete dependent snapshots or versioned objects for cloud storage. For hardware, ensure that sanitization reports include the method used to wipe, the version of the tool, and the operator ID.
- Physically dispose or recycle. Partner with certified recyclers (R2 / e-Stewards) to handle hardware and collect Certificates of Destruction (CoD).
- Store evidence and close the record. Store all of your CoDs, sanitization logs, and approvals in one location. Teams typically store this in a governance system or CMDB to facilitate audits.
Once you complete this step, you begin to take ownership of it. The reason is that there should be clear accountability at every step. Roles, RACI, and guardrails help keep ITAD the same across teams and environments.
Read also: IT Asset Management Process: 6 Workflow Steps You Can’t Ignore!
1. Build control and accountability in ITAD process
Without clear ownership and asset disposition management, even the best IT asset disposal process can fail. Someone must decide when an asset is retired, who approves the change, and who signs off on the data's deletion.
In large environments, responsibility is often split: ITAM tracks inventory, Security defines sanitization standards, GRC validates compliance, and Operations handle the hands-on part.
This way the same asset can appear in four systems, each with a different status.
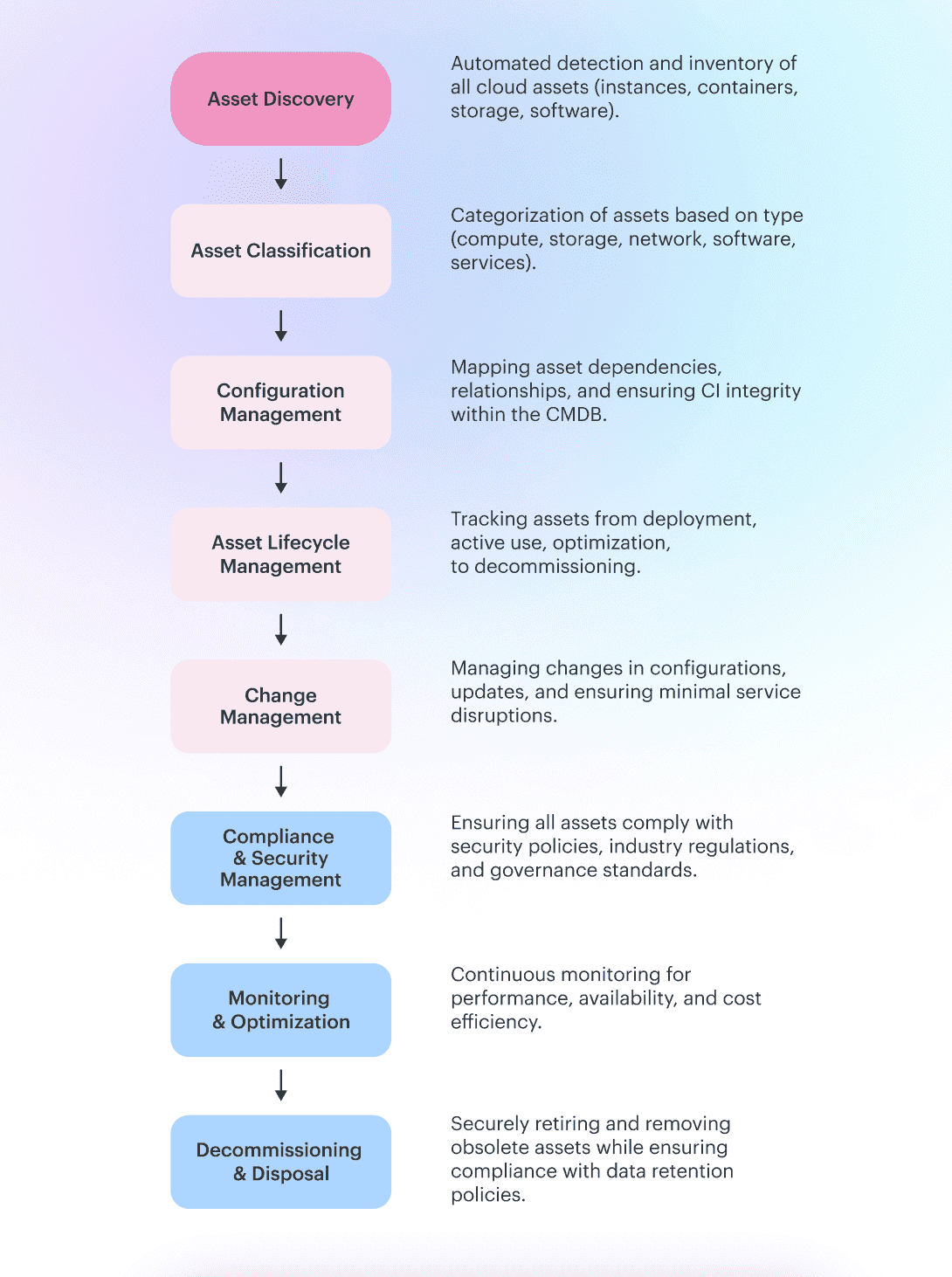
Figure: IT Asset Lifecycle Flow
The best practice is to document this flow as part of your asset management and disposal policy. For example:
- Who initiates retirement. Usually the service owner or application team.
- Who approves. Security or GRC validates that the asset can be retired, confirms data classification, and enforces sanitization method.
- Who executes. Operations or Cloud Operations handle the actual decommissioning, media wiping, workload termination, and device shipping.
- Who verifies and closes. GRC reviews the evidence package and updates the CMDB or system of record to “Disposed.”
This flow must be policy-driven, not personality-driven. It should work the same way no matter who’s on duty. That’s how you prevent half-retired systems from lingering in reports or invoices.
How Cloudaware helps:
Cloudaware enables teams to establish role-based access control (RBAC), allowing them to control who has the ability to view or modify assets. Jira and ServiceNow integrations automatically update the audit trail by syncing ownership information and approvals to the appropriate CI.
Read also: 9 parts of IT Asset Management Policy That Works for Hybrid Setup
2. Ensure data handling and compliance
Secure data handling sits at the core of any information technology asset disposal program. You can’t prove compliance if you can’t prove how data was wiped, who performed it, and where that evidence lives.
Every standard, including ISO 27001, SOC 2, and NIST SP 800-88, requires that enterprises display this chain in a transparent and understandable manner.
The foundation of secure disposal of IT assets is media sanitization. Each asset should have a defined data classification and a mapped sanitization method.
Here are key areas to control:
1. Define your sanitization policy. Sort the data and use one of the three NIST SP 800-88 methods:
- Clear: Resetting or overwriting internal, low-risk data makes sense.
- Purge: Erasing at the cryptographic or block level for workloads that are regulated.
- Destroy: Physically shredding or degaussing devices that are no longer in your control.
In practice, most teams struggle with two extremes: some overwrite drives but never record details, while others outsource destruction but never verify certificates. The only reliable model is evidence-based: the sanitization method is selected per asset, executed, logged, and linked back to its lifecycle record.
2. Verify execution and logging. Every wipe or destruction event should include method, operator ID, timestamp, and tool version. Many audit failures occur when these logs are missing or incomplete.
3. Eliminate dependency sprawl. Before you mark a resource as "disposed," make sure there aren't any cloud dependencies left over, such as snapshots, object storage buckets, or encryption keys. These remnants can hold sensitive data or add unnecessary costs.
4. Secure your evidence. Keep all disposal tickets, CoDs, and sanitization logs in one location for the necessary period of time.
How Cloudaware helps:
Teams can view all of their compliance records in one location thanks to the platform.
- Each CI can have vendor reports, wipe logs, or CoDs attached.
- The Deleted From (disappearance time) field confirms when an instance or volume was actually removed.
- Custom policies or reports help identify missing sanitization data and flag assets that still have related items.
3. Reclaim licenses and software after asset disposal
The process of disposing of assets involves more than just hardware. Any associated licenses, contracts, or support subscriptions should also be rescinded or transferred when a server, database, or SaaS account is no longer in use.
Companies continue to pay for licenses that are inactive or not being used if this step is omitted, which is a common source of idle resources.
Typically, a complete software and license reclamation flow consists of:
- Discovery and mapping: Find out which software assets are linked to each CI, from OS services to SaaS accounts.
- Validation: Make sure that workloads, users, or hosts are no longer active.
- Reclamation: Get back seats, move entitlements, or end contracts.
- Financial cleanup: Show those savings in your cost reports or showback.
Common real-world pain points:
- SaaS accounts stay licensed long after user offboarding.
- Databases are decommissioned, but support renewals auto-extend.
- OS and backup licenses are forgotten in enterprise agreements.
- Teams use free-tier replacements but never reclaim paid seats.
A good practice from Mikhail Malamud, Cloudaware GM:
How Cloudaware helps:
Cloudaware turns software reclamation into a measurable, reportable step within your ITAD workflow.
- It connects to AWS License Manager and other integrations to show you what licenses are available in your environment.
- Dashboards help to identify licenses that aren't being used by displaying which CIs still have linked entitlements.
- The system displays reclaimed value in cost analytics, which is useful for FinOps.
Read also: What Is Asset Management Software? ITAM Pro Explanation
4. Finalize ITAD and prepare audit evidence
The final stage of IT asset disposal is all about proof.
By this point, the data is wiped, the hardware is gone, and the licenses are reclaimed. But until the evidence is complete and verified, the process isn’t really closed.
Usually, audit findings don’t come with bad intent. They come from missing proof. Someone retired a server but forgot to attach the Certificate of Destruction. Another team wiped drives but didn’t log the NIST SP 800-88 method they used.
Without documentation, even a fully compliant IT asset disposal procedure looks incomplete to auditors. A proper close-out bundle usually includes:
- Approval record: Who approved and when.
- Sanitization proof: Logs for Clear, Purge, or Destroy.
- Pickup and logistics: Pickup ID, seal numbers, CoD or CoR.
- Before-and-after inventory: Match what was removed.
- License and contract closure: Confirm reclaimed entitlements.
Before closure, GRC verifies hashes, timestamps, and dependencies. This way audit queries like “Show all regulated assets disposed in the last 12 months with CoD and sanitization reports” will take minutes.
How Cloudaware helps:
Cloudaware centralizes and structures your audit evidence workflow.
- Single record per CI: Each configuration item keeps all related approvals, sanitization reports, and CoDs in one place.
- Full change history: Every state change and field update is logged automatically for traceability.
- Quick exports: Teams can download the full evidence set as a CSV or report bundle for audits.
Read also: IT Asset Management Audit For Hybrid Setup: 9-Steps Checklist
How Cloudaware CMDB automates ITAD
When teams talk about ITAD, what they really need is control. The ITAD market has evolved from simple hardware recycling to full lifecycle control, where automation and verifiable data handling define maturity.
Cloudaware acts as the control plane that connects all these layers and keeps the entire disposition lifecycle in one place.
Discovery & inventory
Cloudaware lets you find CIs all the time on AWS, Azure, Google Cloud Platform, Oracle Cloud, Alibaba Cloud, and on-premises environments.
The platform takes data from these sources in real time with no limitations and adds context from the CMDB. This gives the ITAM, GRC, and FinOps teams a real-time, complete, and accurate picture of all the IT assets.
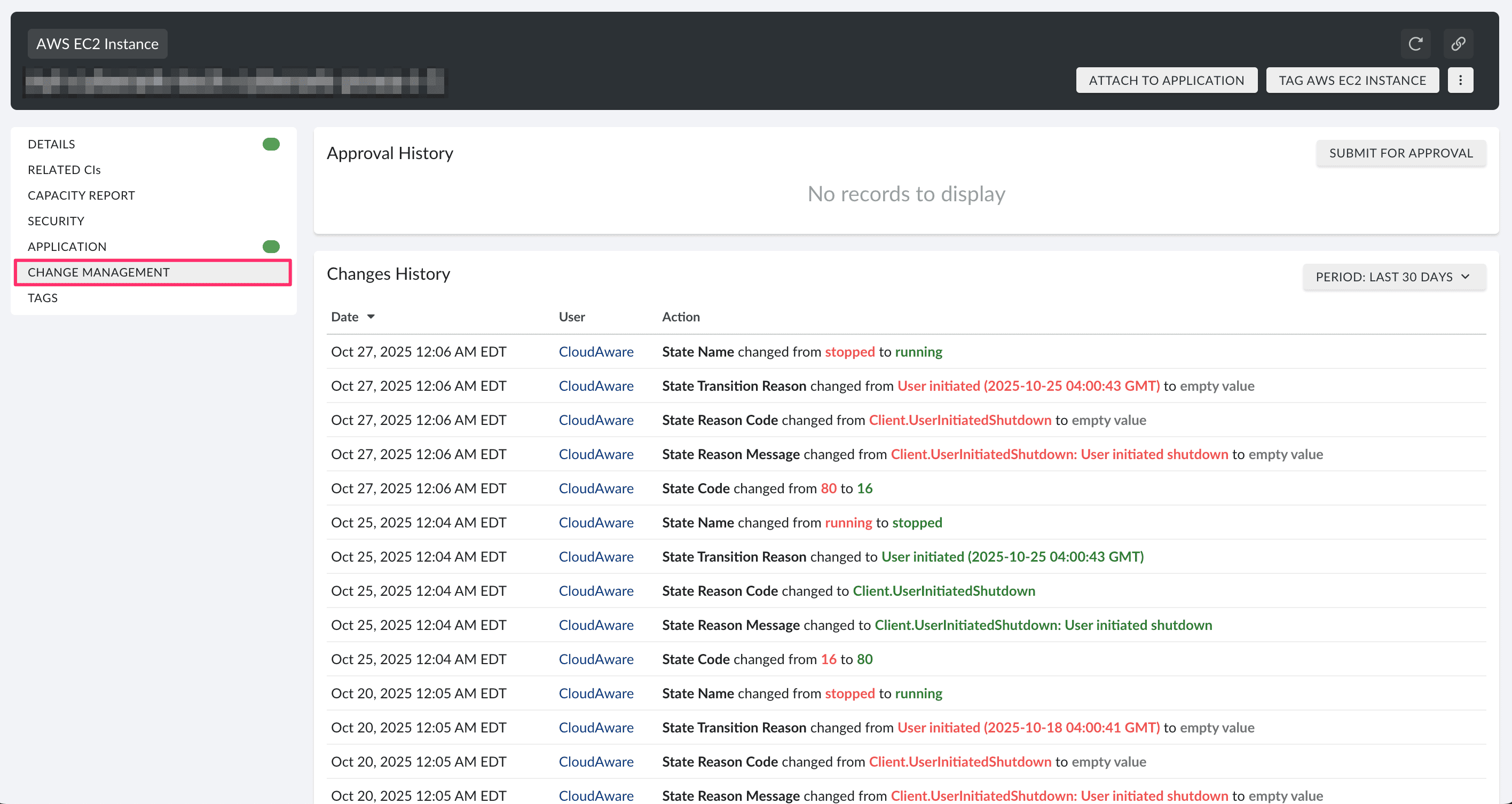
Change control
Change History in Cloudaware keeps track of every change in the system, including who approved it, what was changed, and when. This way, teams can keep track of changes to IT assets in hybrid environments.
Integrations with Jira and ServiceNow allow syncing approvals, decommission requests, and change tickets directly with CMDB records.
Evidence and documentation
Cloudaware lets you create custom fields that can be added to CIs to record IDs, timestamps, or vendor details for audit reporting and compliance tracking.
License and contract visibility
Cloudaware visualizes software entitlements and license usage from integrations like AWS License Manager. This helps identify unused or idle licenses associated with retired assets and supports FinOps reporting.
Dashboards and real-time analytics
Built-in dashboards allow ITAM and FinOps teams to view the health, lifecycle stages, and compliance status of assets in real time.
By filtering reports by owner, environment, or CI type, teams can find idle or orphaned resources and enhance decommissioning plans.
