Ever spend your Friday chasing down a missing license key? Only to find it buried in a spreadsheet last updated three quarters ago? Or try to explain to audit why your CMDB shows 112 instances of the same app — none with clear ownership?
We’ve been there. From broken software request workflows to inconsistent CI naming conventions, the risks in IT asset management sneak in through the cracks. Quiet, small, and deadly.
At Cloudaware, our team works with some of the most complex hybrid multi-cloud environments out there. Thousands of assets. Thousands of accounts. Multiple clouds. And one messy stack of software contracts, license entitlements, and configuration items that don’t always line up.
This article is everything we’ve learned. 7 IT asset management risks that cause real damage and how to prevent them with smarter SAM processes, better CMDB hygiene, and rock-solid data relationships 👇
Wasting budget on unused or duplicate IT assets
You know that quiet feeling when a cost anomaly shows up in your dashboard, but no one's screaming yet — so you just flag it for Monday? That’s exactly how one of our clients first noticed they were bleeding budget through duplicate assets. Not broken ones. Not even misconfigured.
Just... extra.
Turns out, it was one of the more subtle software asset management risks that had slipped under everyone’s radar.
They had three different business units using the same third-party monitoring software. Each had procured their own license. Separate vendors. Separate contracts. No shared visibility.
The wild part? All three teams thought they were saving money by handling procurement independently. In reality, they were paying for the same tool — three times over.
And that was just the start. We uncovered multiple CIs tied to applications with zero usage in the past six months. No alerts, no dependencies, no linked service.
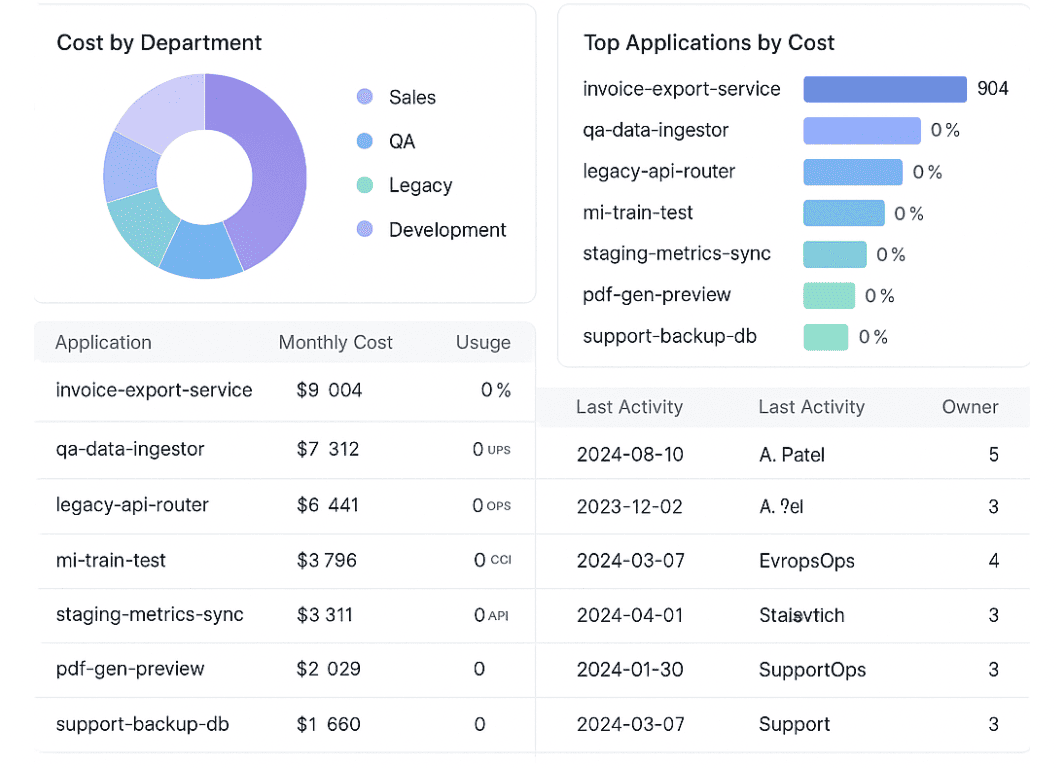
Example of the FinOps report, data is changed.
Just unused assets hanging around like old post-its — quietly eating into their OPEX.
That advice helped the team restructure their asset management process. Procurement got a seat at the table. Request approvals were tied directly to deployment data. No more blind spots.
This wasn’t just an IT asset management issue. It was a visibility problem — a sign that key players across the lifecycle of an IT asset weren’t syncing. And when that happens, small gaps become expensive fast. Especially when finance starts asking questions — or worse, when a cyber audit hits and you don’t even know what’s installed where.
Read also: IT asset Lifecycle Management From Day One to Done
Risking data leaks or cybersecurity incidents
You know how it goes — security flags a suspicious connection, and suddenly everyone’s combing through logs like it’s a crime scene. One of the most overlooked software asset management risks? Thinking you’ve got full visibility when you don’t. It’s not always a big, flashy incident.
Sometimes the threat is silent — hidden in the blind spots.
It usually starts with a forgotten piece of software. Not malicious, not even misconfigured — just quietly outdated, left running under the radar with more access than it should have. The kind of thing no one notices until something pings an external scanner or sets off an alert at 2 a.m.
One of our enterprise clients ran into this exact issue. A dev tool had been spun up mid-migration and then forgotten.
The CI was missing from active tracking. It hadn’t been patched in months. Credentials were stored locally, no MFA, and it was still exposed to the internet. Classic unmanaged assets slipping through the cracks.
By the time they caught it, the risk had already become a reality. Not a meltdown, but enough of a scare to trigger a full cybersecurity sweep and rewrite some critical processes.
That week, my teammate Kristina broke it down perfectly during our ITAM review:
In IT asset management, it’s not just about tracking licenses — it’s about owning the full lifecycle. Otherwise, even a well-meaning project can become an unexpected IT asset exposure.
Truth is, most threats don’t come kicking in the front door. They walk in unnoticed, wearing your badge. Which is why having a partner that helps you stay ahead of your environment isn’t just helpful — it’s essential.
Read also: Find It, Track It, Own It: Multi-Cloud IT Portfolio Management
Skipping regular upkeep that leads to bigger issues later
First it gets postponed. Then forgotten. And just like that, a routine review becomes a root cause. This is one of those IT asset management risks that doesn’t scream — it just waits. And when it hits, it hits everything at once.
It usually starts with outdated software. Not broken. Just sitting there quietly with elevated permissions and no one's name on it. If it’s still marked “active” in your systems, guess what — it still counts.
In any fast-moving management environment, backlog grows faster than attention. Patching gets deprioritized. Contract renewals slip. Service tags go stale. Then one automation job runs — and things fall apart.
We had a company in the middle of a massive CI rollout. Their assets were scaling fast. Containers, workloads, shadow tooling — normal chaos. They skipped one software audit cycle. Then two. A deprecated app stayed live and connected to production.
The cleanup script flagged it as unused and removed it. That app was still tied to two services. Both went down. No one caught it because it wasn’t marked critical in their asset management flow.
Recovery took 19 hours. Two war rooms. One very frustrated compliance lead. And a whole lot of “how did this happen?” That’s what makes IT asset management so high-stakes — you don’t get warnings. You get outages.
And the root cause? A forgotten IT asset still registered as “in use,” but unmanaged for over 90 days. No lifecycle updates. No owner. No validation.
It’s also a cyber liability. Because anything unmanaged is also unpatched. And anything unpatched is basically standing on a rooftop waving to threat actors.
Here’s how Iurii Khokhriakov, Technical Account Manager, put it during our internal ITAM review:
This wasn’t just a single risk that caused downtime. It exposed a whole chain of missed checks, weak governance, and reliance on tribal knowledge.
When those blind spots grow, they don’t just become threats — they start shaping your failure pattern. Especially when you’re operating at enterprise scale, where the margin for error is thinner than ever.
If you don’t want to learn this the hard way, don’t go it alone. Find a partner that knows how to connect process, data, and visibility before the next outage does it for you.
Unexpected outages that disrupt operations
Outages don’t always come from failed deployments or massive bugs. Sometimes, they’re born from silence.
A CI that hasn’t been reviewed.
A script no one remembers owning.
A software component left active in name only.
In the world of IT asset management risks and controls, this is the kind of threat that gets overlooked — until it stops your systems cold.
It’s dangerous because it hides in the spaces between teams and management layers. A missed tag here, an unlabeled dependency there. These are small fractures in process that slowly erode the foundation.
And when that foundation slips, you don’t lose just a tool — you lose access, uptime, trust. Especially when those unknown assets are running critical automation behind the curtain.
We saw it firsthand with a client who thought they’d retired an internal module. The CI looked inactive. But it was still tied to asset management scripts in their release pipeline. When a connected component was patched, the orchestration broke. No one caught it — until staging, monitoring, and pre-prod all crashed within 15 minutes.
In IT asset management, the danger isn’t just what’s running — it’s what’s still wired in. The CI had no owner, no recent update, and no flags in the CMDB. But it was tied to an IT asset still processing deployment logic.
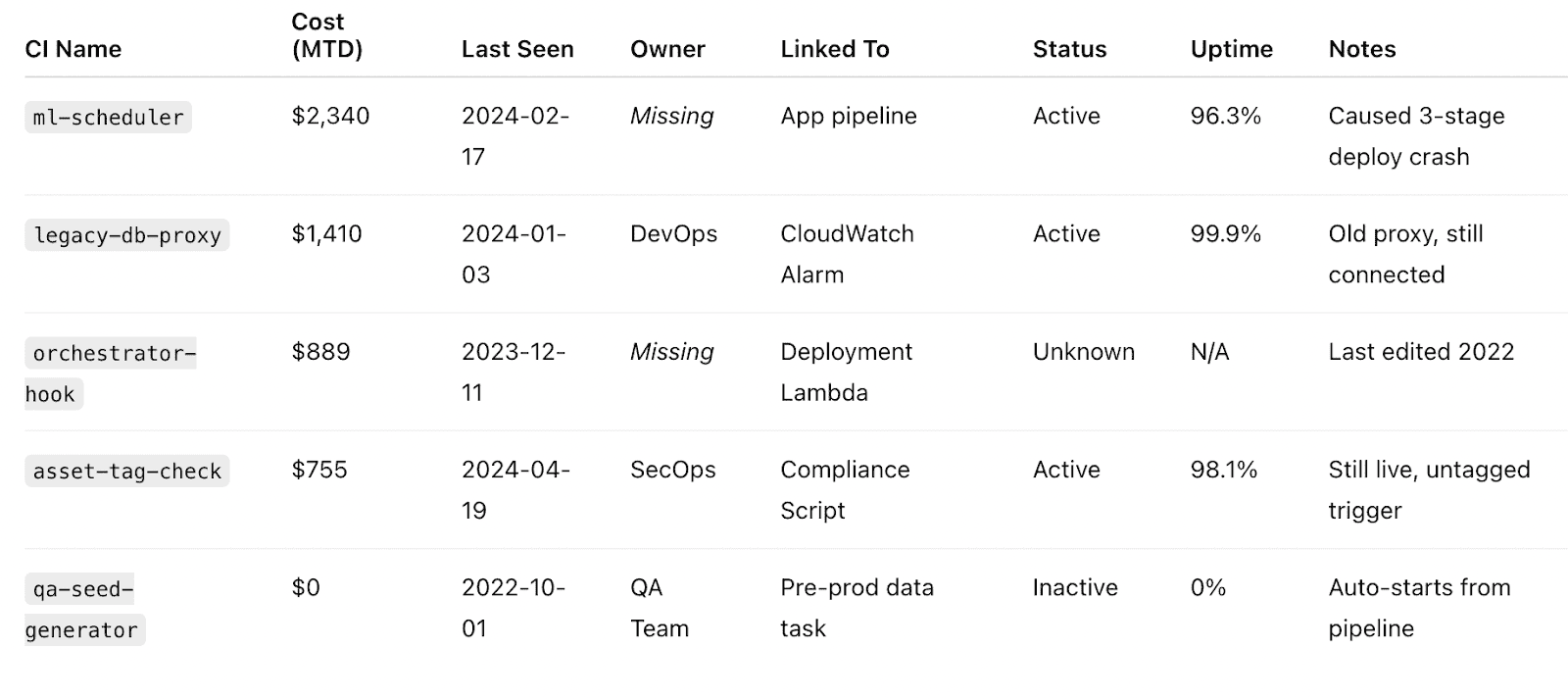
Worse? That asset was externally exposed. No MFA. Stored creds. Now you’ve got an operational gap and a cyber surface you didn’t know existed. A double hit.
Mikhail Malamud, Cloudaware GM, said it best:
Because when data stops flowing, people notice. But when processes stall because of an invisible dependency, it’s not just a downtime issue — it’s a visibility one. And no one wants to explain to leadership that a forgotten piece of technology brought down the release cycle.
Getting hit with fines, penalties, or rising insurance costs
It starts quietly. No alarms. No system crashes. Just a routine vendor email — until you open it and realize it's an audit notice with significant financial implications. In software asset management, the most expensive risks often stem from compliance oversights rather than technical failures.
Why is this dangerous? Because it impacts multiple facets:
- Financial Penalties. Non-compliance can lead to substantial fines. For instance, NASA incurred approximately $20 million in unnecessary spending on software penalties over five years due to inadequate software asset management practices.
- Legal Consequences. Violations of software licenses can result in legal actions, further escalating costs and damaging the organization's reputation.
- Increased Insurance Premiums. Unmanaged risks can lead to higher insurance costs as the organization's risk profile worsens.
We worked with a client operating a widely-used analytics platform across multiple teams. Without centralized license tracking and with disparate approval processes, each request was handled independently, and updates to the CMDB were neglected. When the vendor conducted an audit, they discovered the organization was 174 licenses over their entitlement, spanning two years. This oversight led to significant financial repercussions and strained vendor relationships.
Anna, ITAM expert at Cloudaware, emphasized the solution:
In IT asset management, the real risk lies not in what you lack, but in what you can't account for.
Read also: Top 10 Enterprise Asset Management Software: Features & Pricing
Holding onto outdated hardware long past its prime
It hums along in the corner, runs quietly, and hasn’t thrown an alert in months. Feels safe, right? But that aging server, that end-of-life firewall, that legacy switch you’ve duct-taped into one more sprint — those are time bombs.
Holding onto outdated hardware isn’t about nostalgia. It’s one of the most overlooked risks in IT asset management. When hardware reaches the end of its vendor support, you lose more than a patch schedule. You lose:
- Firmware updates
- Compatibility with newer systems
- Validation under modern load and usage
Even worse? That forgotten CI might still be tied to key services in your VPC or running middleware dependencies inside a production subnet.
And the financial impact? Organizations with poor lifecycle tracking see up to 10% higher total IT costs, largely from outdated infrastructure eating up budget and uptime.
We worked with a client still running a core billing API through a five-year-old appliance hosted in a private cloud zone. Not flagged, not tracked — just listed as a generic “CI-host-17” in their CMDB technology with no lifecycle metadata. Then one day it failed. Not gracefully. Not in a staging environment. It collapsed mid-transaction processing, locking up queues downstream.
That outage cost real money. It also killed trust with ops and exposed a cyber risk tied to unpatched firmware with a known CVE sitting unresolved.
Here's how Daria, our ITAM expert, breaks it down:
Because in modern environments, outdated tech isn’t old. It’s invisible — until it breaks everything.
Stay Ahead of IT Asset Management Risks with Cloudaware technology
Built for modern infrastructure, Cloudaware delivers real-time discovery of your entire IT ecosystem — software, hardware, cloud workloads, and on-prem systems. No throttling. No blind spots. Just accurate, always-fresh data across AWS, Azure, Google Cloud, Oracle, on-prem, and even Alibaba environments.
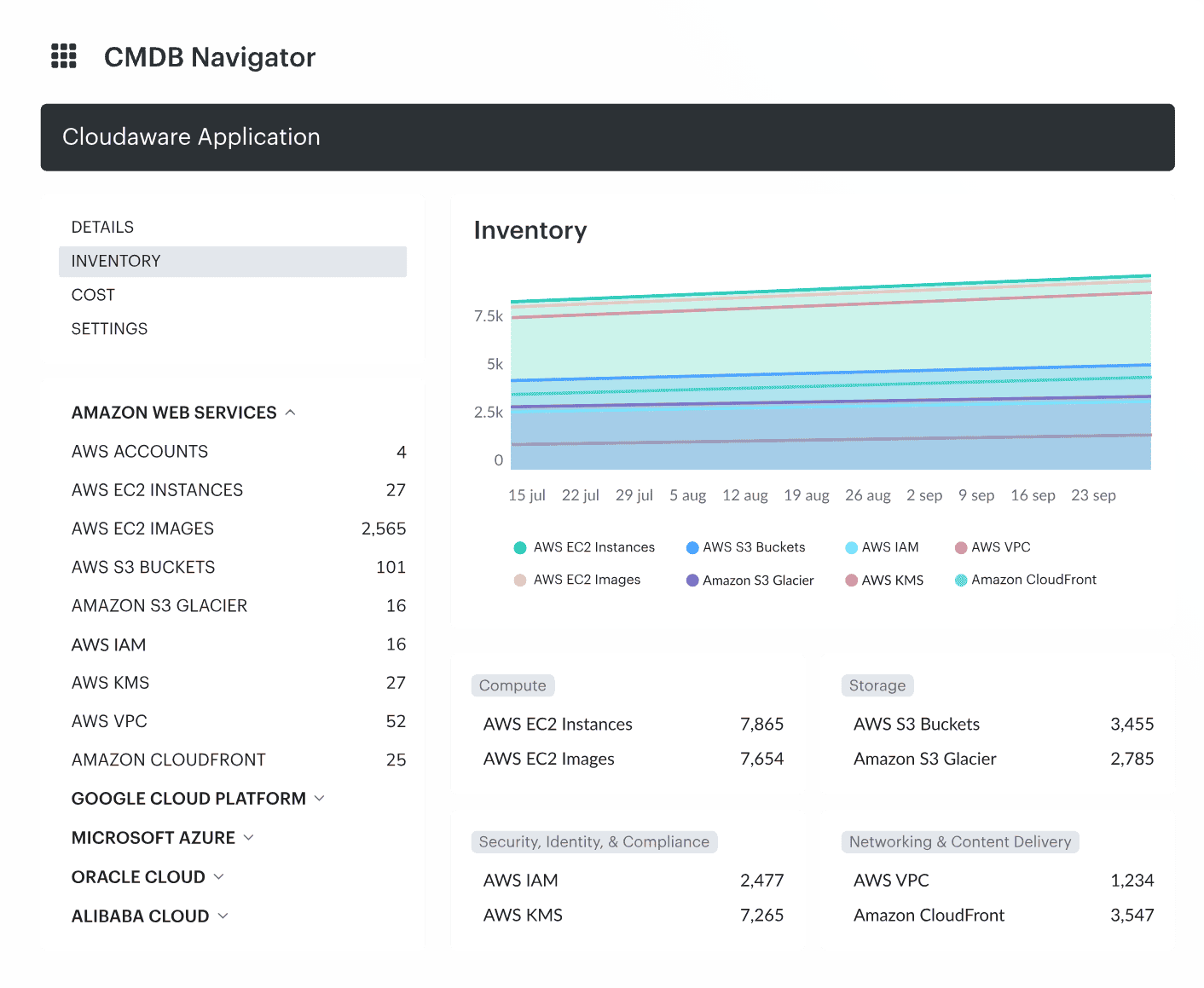
It’s more than inventory. Cloudaware gives you smart management of your configuration items — linking usage, cost, compliance, and lifecycle data in one place. You’re not just tracking assets — you’re managing risk at scale.
With Cloudaware, you can:
- Discover and manage software and hardware across all platforms
- Enrich it with data about related items, cost, vulnerabilities, and much more.
- Automate license checks and end-of-life tracking
- Flag outdated or unverified assets in real time
- Enforce clean, audit-ready asset management processes
- Integrate with ITSM, procurement, and security workflows
