When you think of configuration management, what comes to mind? Managing assets, tracking changes, updating configurations, and ensuring that everything is aligned and running smoothly.
Simple enough, right? But here's the catch: without the right strategy, these seemingly straightforward tasks can quickly turn into a chaotic game of whack-a-mole. One moment, you're happily updating configurations, the next, you realize an entire cluster of servers is out of sync because a small oversight went unnoticed. It happens.
Take this scenario: A multi-cloud setup, with instances spread across AWS, Azure, and on-prem — sounds like a dream, right? But without proper tracking, a change in one environment could ripple through, causing a cascade of unexpected outages across others. Been there, done that.
After nine years working with Cloudaware clients as a CMDB implementation expert, I've seen it all. The same mistakes pop up time and time again: mismanaged dependencies, overlooked changes, and tangled cloud environments.
But don’t worry — I’ve gathered these lessons, and now sharing the best practices for configuration management that will save you from the pitfalls.
Let’s dive into the top nine configuration management best practices for your multi-cloud environment.
Align people & processes in business before diving into configuration management
Before you jump into configuration management, let’s take a breath and ask: Are your people and processes in sync? You might be tempted to dive straight into configuring your tools, but trust me — if you don’t get this foundational part right, it’ll be like building a house without a blueprint. It’ll look okay for a while, but eventually, everything will come crashing down.
Step 1: Define roles clearly (because chaos isn’t cool)
When you’re managing thousands of endpoints across multi-cloud and hybrid environments, things get messy fast if everyone isn’t on the same page. Here’s who needs to be involved:
- Configuration Manager a.k.a. the “master of the CMDB universe.” They’re the ones keeping the big picture in focus — making sure configurations are documented, changes are tracked, and everything stays compliant. Think of them as the heart of ITIL configuration management best practices.
- IT Engineers. They’re the ones who make things happen. From maintaining configurations to rolling out updates and patches, they’ll need to be comfortable with your configuration management tools.
- DevOps & Cloud Architects. These folks work to make sure the systems are talking to each other smoothly. They’ll help you integrate your CMDB with your CI/CD pipeline and automate that pesky configuration drift detection across your clouds and on-prem.
- Security Team. Let’s be real — security is non-negotiable. The security team ensures that your configurations meet those compliance standards (ISO 27001, NIST, etc.), keeping your infrastructure locked down.
- Business Stakeholders. Not all heroes wear capes, and not all stakeholders sit in IT. Get business leaders involved from the start, so their goals are reflected in your configuration management practices, from meeting SLAs to aligning with broader strategic initiatives.
Step 2: Build solid processes (before you break anything)
With the right people in place, it’s time to build processes that actually work at scale. Here’s where you lay down the law:
- Configuration Baselines. The baseline is like the ‘golden standard’ for what your systems should look like. (I’ll tell about it in details below in this article.)
- Continuous Monitoring & Compliance. Let’s face it, you’re not going to manually check 10,000 endpoints every day. That’s where your monitoring tools like Cloudaware CMDB come in. Automate the tracking of configuration changes and catch drift before it becomes a problem.
- Patch Management. Security patches are inevitable, but they don’t have to be a nightmare. Use tools like Cloudaware, Red Hat Satellite or WSUS to manage patches across your infrastructure, and make sure nothing slips through the cracks.
- Emergency Response. Misconfigurations happen. It’s a fact of life. But when they do, you need to react fast. Set up a protocol for quick fixes. Tools like Splunk, Cloudaware, or Elastic Search can help you pinpoint issues, and automation tools can help you push fixes out quickly.
Step 3: Keep everyone talking (seriously, this is key)
Anna, ITAM expert at Cloudaware:
"Config management only clicks when your people and playbooks are in sync. I’m talking cloud security leads, platform owners, AppSec, and the folks chasing down drift at 3 AM. If they're not all looking at the same config data and escalation matrix, you’ll spend more time firefighting than automating.
Before you spin up another Lambda to auto-remediate non-compliant S3 buckets or trigger a patching runbook from Opsgenie, ask:
💡 Who’s the DRI when config fails the baseline check on a crown jewel system?
💡 What’s the comms path when a patch rollback breaks PCI posture?
💡 Are your compliance checks running in the CI pipeline or just sitting idle in a forgotten repo?
We’ve seen this too often — folks start with tooling, not trust. You need that shared reality first: RACI defined, escalation mapped, alerts routed, and SLAs realistic. Otherwise, your CMDB will turn into a graveyard of stale records, and your SecOps team will be flying blind.
Nail the human mesh first. When Sec, Dev, and Infra trust the config source of truth and the escalation flow is muscle memory, that’s when automation hums. You can scale across orgs, clouds, and edge fleets without feeling like you’re duct-taping BGP leaks at 2 AM."
Read also: ITIL configuration management best practices
Choose a configuration management database that meets your needs
I’ve tested 20+ CMDB tools that claimed to “solve configuration management,” and I’ve sat with DevOps leads post-incident who said, “We thought this would catch it.” Spoiler: it didn’t.
Configuration management that scales isn’t just about what tool you pick — it’s about how that tool supports your real-life workflows, pipelines, and best practices.
If you’re serious about choosing a CMDB that works in fast-moving, multi-cloud environments, focus on these key features:
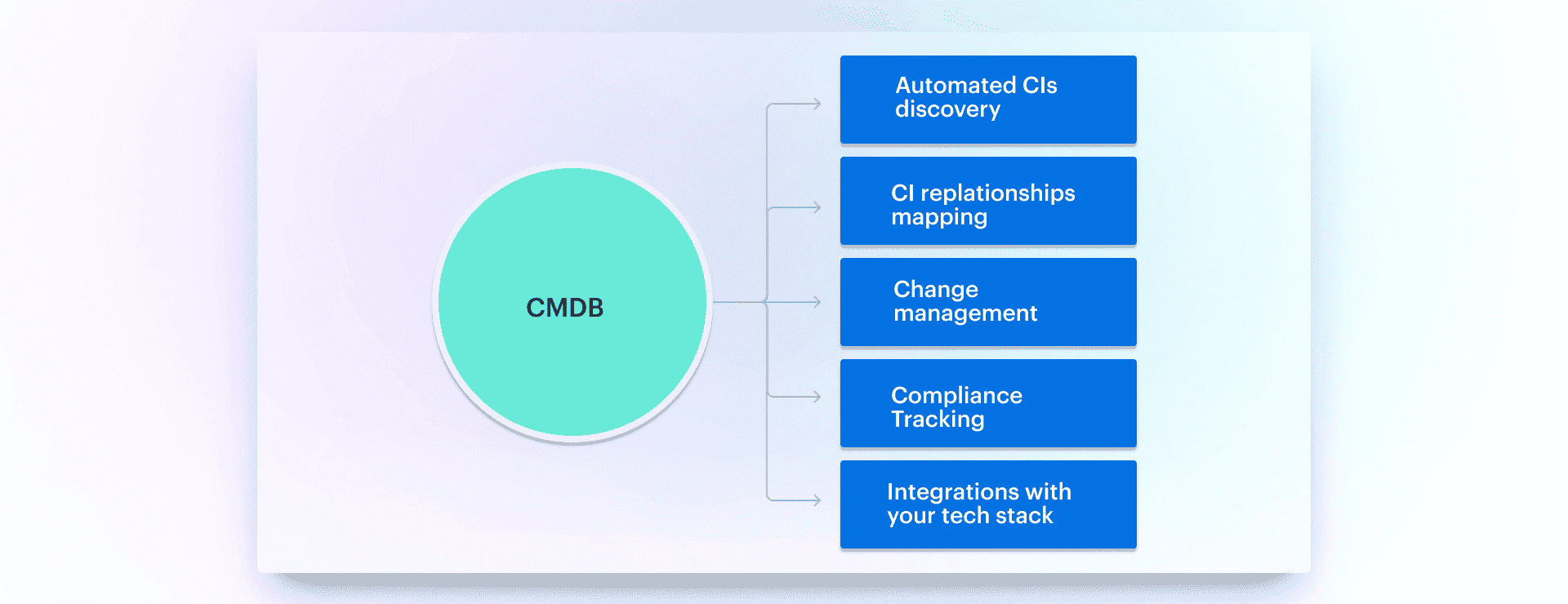
- Native Integrations. Best practices start with visibility. Your CMDB should ingest config data from AWS Config, Azure, GCP, Terraform Cloud, PagerDuty, and your favorite scanner — continuously. No batch imports, no brittle scripts.
- Real-Time Configuration Discovery means you catch shadow infra, policy drift, and “who launched that?” moments before they snowball.
- CI Enrichment from External Systems. It’s not enough to log config. Enrich it with cost data, CVE severity from your vuln tools, patch compliance, asset ownership, and lifecycle tags.
- Change Tracking + Ownership. Every configuration change should be linked to its source — Git commit, CI/CD job, Jira ticket. Track who changed what, when, and why — no more playing detective during root cause.
- Compliance + Baseline Management. Hardcoded controls don’t cut it. Codify best practices and compliance rules (CIS, PCI, custom configs) into your system. Track violations, trigger alerts, and automate enforcement before audit season sneaks up.
- Tagging & Dynamic Grouping. Configuration without metadata is noise. Group CIs by business unit, cost center, region, or SLA tier.
- Alert Automation. When config goes off-script, don’t just log it. Open a ticket, ping a Slack channel, trigger remediation. Best practices mean acting fast, not just observing.
- FinOps Integration. Link your config data with cost metrics. Spot idle resources, flag budget overruns, and clean up ghost infra before it shows up on the cloud bill.
- Custom Dashboards & Reports around your workloads, your tagging schema, your reporting cadence. Show the right data to the right team at the right time.
If your configuration management doesn’t reflect how your infra actually works — it’s just shelfware. Choose a CMDB that moves at the speed of your pipelines and enforces the best practices your teams already live by.
Automate сonfiguration management
Manual config is what burns you at 3AM. A drifted IAM policy here, a missing tag there — and boom, someone’s on-call with zero context. If you’re still relying on tribal knowledge or post-deploy checklists, you’re already behind on configuration management.
For example, as your infrastructure changes, the CMDB reflects those changes instantly. You can also build automation flows based on config state: define what triggers the flow, and what action should follow — like alerting, tagging, or kicking off remediation.
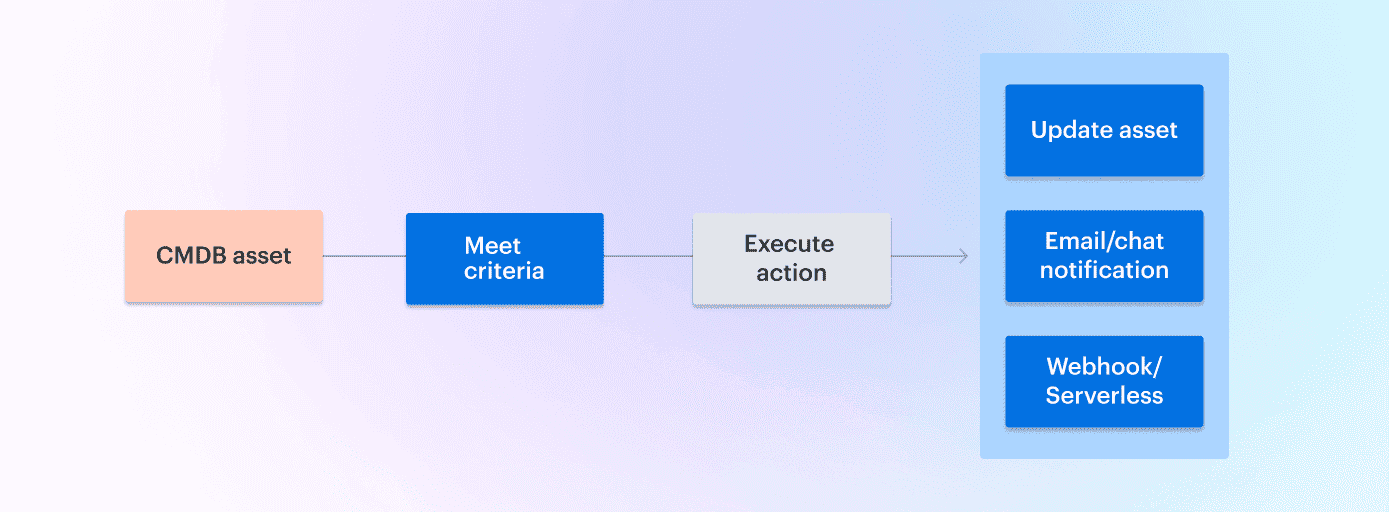
Here is an example of how asset management automation works in Cloudaware:
One of our clients had the usual soup: Terraform in place, dozens of AWS accounts, but half the configuration was out-of-band. Shadow changes, misaligned tags, compliance violations — all showing up after things broke. That’s where solid DevOps configuration management best practices kick in.
Mikhail Malamud Cloudaware GM:
"We helped them automate configuration management top to bottom. Baselines were codified in Git — encryption, tag schemas, public access rules — and synced with Cloudaware’s real-time config state.
Then we wired up detection policies: if a CI drifts from baseline, Cloudaware fires off alerts with context. For minor stuff like tag mismatches, it calls a Lambda to fix metadata. For riskier misconfigs — like open security groups — we trigger SSM automation to quarantine the resource.
Every action is scoped by CI attributes: env, SLA tier, owner. So prod doesn’t get the same playbook as dev. Slack pings the right team. Jira auto-fills with everything they need to act.
They stopped firefighting and started enforcing — automatically, and with zero guesswork."
That’s configuration management that scales. These aren’t just good intentions — they’re baked-in best practices that make your infrastructure more secure, compliant, and hands-free. It’s not just about detection — it’s about doing something when configuration drifts. Quiet, clean, reliable. The kind of automation your pager will thank you for.
Lock in strong change management practices
You know the drill: a pipeline runs, a resource config gets tweaked, and two hours later, prod’s on fire — but no one knows what changed. No ticket, no audit trail, no rollback target. DevOps doesn’t break because of too much change. It breaks when change is invisible.
That’s why locking in strong change management is non-negotiable — not for process’s sake, but for survival. It’s one of those ITIL configuration management best practices that actually pays off when things go sideways.
Kristina, Seniour ITAM expert at Clodaware:
"One of our clients — a platform team running multi-account AWS with CI/CD via GitHub Actions and Terraform — kept getting hit with post-deploy issues no one could trace. A firewall rule would shift, IAM permissions would spike, or cost tags would vanish… and there was no unified view of why the change happened.
The fix? Don't treat change as something to clean up after. Company devops team build it into the process from the start. By connecting Cloudaware CMDB to their Git repos, pipelines, and Jira flows, they had every config change — from a Terraform apply to a quick console tweak — captured automatically.
On top of that, there was info about commit hash, ticket ID, and approval state.
High-risk changes were tagged by environment, SLA tier, and CI criticality. Then we set up automations: if an unapproved change hit prod, Cloudaware triggered a webhook to alert Slack.
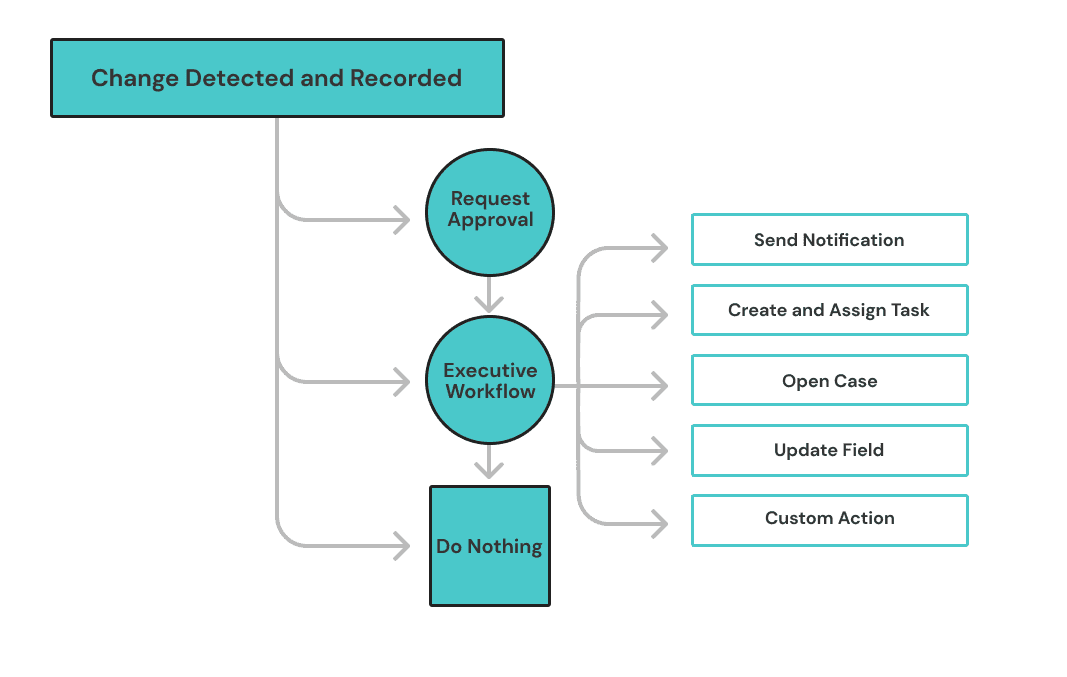
Their CMDB became more than a config log — it became part of service delivery, supporting real-time decision-making, clean RCA, and proactive compliance. That’s what real configuration management looks like when change is done right."
Change fast. Track smarter. Sleep better. Let your CMDB carry the context, not your memory.
Read also: Decoding configuration management vs change management in a multi-cloud environment
Set configuration baselines
A classic IT headache — configurations all over the place. One server is running an outdated OS, another has custom firewall rules, and someone, somewhere, thought it was a great idea to disable security settings "just for testing" (and then forgot to turn them back on). Now, when something breaks, troubleshooting turns into a scavenger hunt.
What’s the standard setup supposed to be? No one really knows.
This kind of inconsistency isn’t just annoying — it’s a ticking time bomb. Without configuration baselines, your organizations are exposing their assets to unnecessary risks. Performance issues, security vulnerabilities, and compliance failures start piling up, making everything harder to manage.
The fix
At Cloudaware, we make configuration management simple, standardized, and fully automated. Here’s how:
- Define Baselines. Set clear, standardized configurations for your servers, applications, and services. Cloudaware lets you create templates that align with configuration management best practices, security policies, and industry standards from day one.
- Enforce Standards Automatically. No more “I forgot” moments. CMDB continuously checks your infrastructure against your defined baselines and flags any deviations in real-time.
- Audit & Remediate. Run automated scans to spot drift and fix it fast. If a setting changes outside your approved baseline, Cloudaware can trigger alerts to help you get things back in line — before it becomes a problem.
- Data-Driven Compliance. Your CMDB isn’t just a storage space for configuration details. It’s a powerful tool that ensures every system meets internal policies and external regulations while keeping your data secure.
With Cloudaware, your configuration management goes from reactive to proactive. No more chasing down rogue configurations or firefighting unexpected issues — just a stable, secure, and well-oiled infrastructure. Set your baselines, lock them in, and let automation do the rest.
Take control of every endpoint with configuration management db
This scenario hits home for many IT teams: you’re trying to manage thousands of servers, cloud instances, and VMs, but endpoints are slipping through the cracks. Maybe someone adds a new server, a rogue endpoint, or an unmanaged device — but because there’s no central tracking, it goes unnoticed.
Eventually, an issue arises, and guess what? You can't even find the endpoint that’s causing the problem. It's like looking for your car keys in a pile of clothes — you know they’re somewhere, but finding them is a whole other story!
The Problem: caps in visibility
- Some assets or endpoints aren’t discovered or tracked.
- Changes to infrastructure are made, but there’s no way to confirm they’ve been applied across all systems.
- Rogue or forgotten endpoints slip through, creating security risks or performance issues.
Here's the thing: with hybrid environments (on-prem + multiple clouds), it's easy for endpoints to get lost, and the idea of tracking them manually is a nightmare. If you're missing 10-15% of your data or endpoints, you're running on borrowed time. Especially with teams working remotely, that gap only gets wider. It's not just about visibility — it's about control. Without proper configuration management practices in place, organizations can face major vulnerabilities.
How Cloudaware can help?
At Cloudaware, we focus on infrastructure visibility — we help you track every configuration item, whether it's a server, a virtual machine, or an application. Our CMDB integrates with both your cloud and on-prem infrastructure, ensuring that all your assets are automatically discovered and tracked.
If something’s not tracked properly or if a change doesn’t align with your policies, Cloudaware flags it. Whether it's a new server added to your cloud infrastructure or an on-prem update that’s out of sync, Cloudaware ensures your CMDB stays current.
Our solution follows ITIL configuration management best practices, ensuring the right level of governance and accuracy for your IT environment.
The result?
- Real-time updates on configuration changes.
- Immediate alerts when something’s amiss.
- Full visibility of both cloud and on-prem systems in one place, ensuring seamless configuration management.
Take back control of your assets — track, validate, and secure everything from your servers to your VMs. With Cloudaware, you get the tools to keep everything under control, no rogue endpoints left behind.
Manage potential costs overruns proactively
You know that moment when the cloud bill hits and someone says, “Wait, what’s running in ap-southeast-2?” That’s the sound of passive cost management failing. It’s not about a few overprovisioned EC2s — it’s misaligned tagging, missing lifecycle data, and idle resources that no one owns until it’s too late to shut them down without risk.
Here’s the real best practice: bake cost visibility into your configuration management. Every CI should carry metadata — owner, cost center, lifecycle stage, SLA tier. Then use that configuration data to flag potential overruns before the spend happens. It’s not a finance process. It’s config hygiene — and one of the most practical configuration management best practices an organization can adopt to control spend without slowing down delivery.
Iurii Khokhriakov, Technical Account Manager at Cloudaware, put it best when they helped a team running fast-moving infra across AWS, Azure, and GCP:
"These guys had spot fleets, short-lived containers, DR assets always standing by — and cost visibility was fragmented. We helped them use Cloudaware to tag every CI with business unit, environment, and lifecycle. Then we layered in policies that detected missing cost tags or idle resources based on usage metrics.
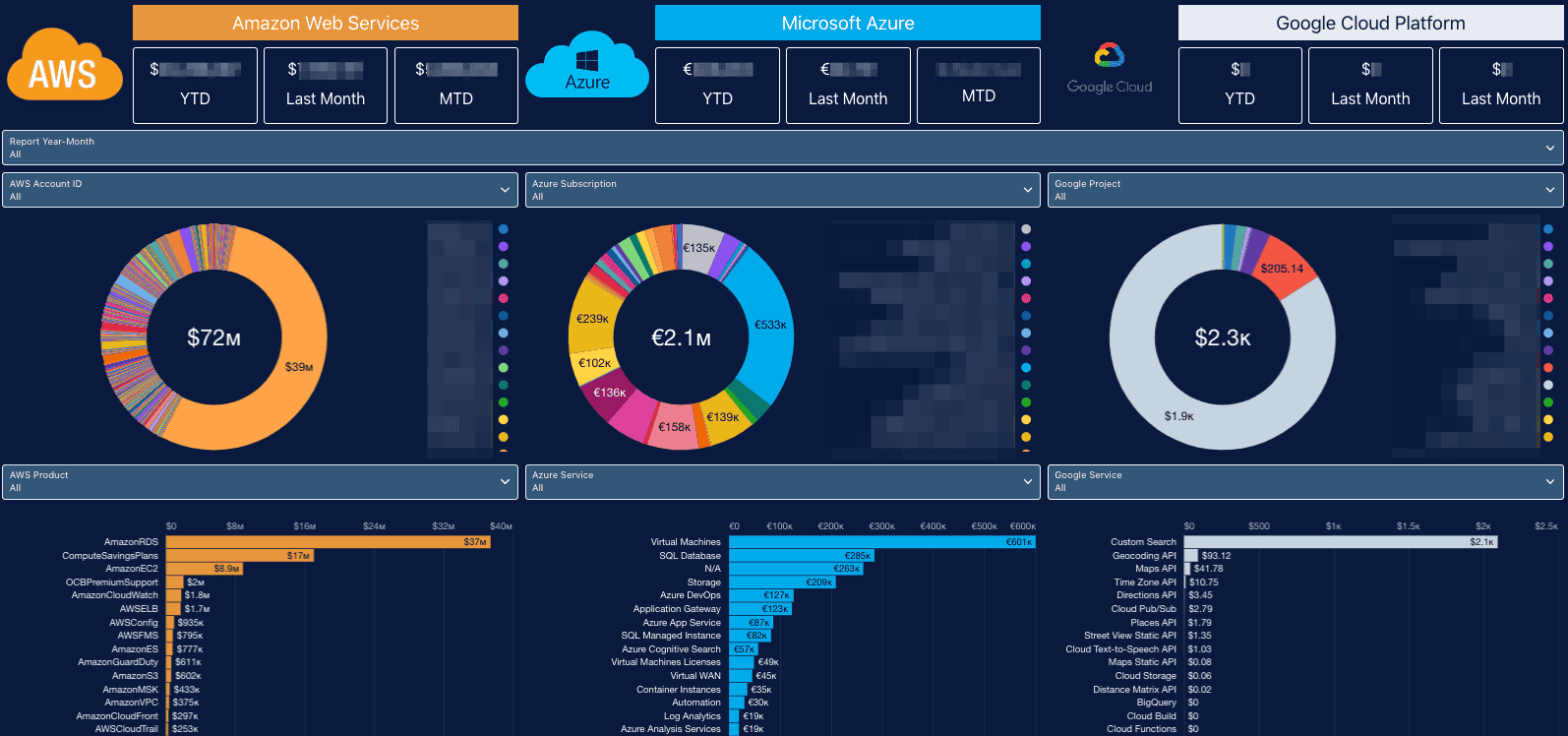
Cloudaware flagged those issues instantly — pinged Slack, opened a Jira, attached full CI context. They wired those alerts into their existing cleanup workflows and approval flows, so action happened without friction. And on top of that, they started tracking all high-risk configuration in our Cost Overruns Forecast dashboard — broken down by project, service, and owner — so they could course-correct before the month closed.
Once FinOps became part of the config baseline, overruns weren’t surprises. They were signals — early, actionable, and visible to the right teams. The change was cultural too — treating spend as part of good software configuration management, not a separate finance task."
Prioritize configuration compliance
You’re running fast, spinning up infra through Terraform, tweaking IAM roles, patching as you deploy. Then in the first demo with us, someone says, “_Yeah… we’ve got compliance policies, but no one really watches them unless there’s an audit._” That’s when the stories start rolling in: missed CIS benchmarks in prod, SOC 2 delays, open ports discovered by pentesters, or unencrypted EBS volumes hiding in staging for months.
Nobody’s ignoring configuration compliance on purpose — it just gets buried under everything else. But when no one owns it in real time, it turns into a shared blind spot. That’s why we always say: strong configuration management isn’t just about visibility — it’s about accountability across the organization.
Here’s how Daria, ITAM expert at Cloudaware lays it out when helping teams harden their environment without slowing it down:
- First, define your non-negotiables — encryption at rest, logging enabled, IAM least privilege, backup tagging — mapped to your CIS controls and internal baselines. Don’t go generic; scope them by CI type, SLA, and environment so you're not holding dev to prod-level standards.
- Then get ownership right. Tag every CI with business owner, workload type, lifecycle, and SLA tier. Now when something fails a policy — like an EC2 with no encryption or an RDS missing backups — Cloudaware flags it, scores it by severity, and routes it straight to the team that owns it.
- Push those alerts into Jira with context (rule violated, config diff, timestamps) and Slack for real-time heads-up. Then give leadership a compliance roll-up by business unit and control family — so they see what’s working and what’s slipping.
You’re not building a security wall — you’re wiring software configuration management best practices into your daily change process. Quiet, continuous, no surprises.
Continuously monitor your configuration management processes
One of our clients showed up to the demo straight from a postmortem — DNS went sideways in prod, and it took two full hours before anyone realized. Turned out someone had manually updated a Route 53 record for a dependency mapping, bypassing their CI/CD flow. The config change happened. The blast radius happened. What didn’t happen was any alert — because no one was continuously watching the config layer for unapproved changes.
And that’s the trap: you’ve got baselines, tagging standards, hardened templates… but if your product configuration management processes aren’t being monitored in real time, your organization is trusting everything’s working just because it worked last week.
Here’s how Anna, ITAM expert at Cloudaware explains how to get ahead of it:
- First, map the config-sensitive processes across AWS, Azure, and GCP — provisioning, backup tagging, IAM policy enforcement, DNS hygiene, patch visibility. Then use Cloudaware to monitor the configuration state those processes should leave behind.
- Build rules to flag missing backup tags, public DNS zones, excessive IAM permissions — anything that signals drift or skipped steps. If someone makes a manual change outside your CI/CD process, Cloudaware picks it up from the config layer and flags it.
- Push alerts to Slack with CI-level context, and use dashboards to track which policies are failing most often, and where. That’s how you move from reactive cleanup to continuous oversight — a core part of product configuration management best practices in any cloud-driven software environment.
Optimize your cloud infrastructure configuration management with Cloudaware
Cloudaware CMDB is a multi cloud configuration intelligence platform built around real-time visibility, policy automation, and configuration management best practices. It helps you manage your cloud infrastructure, security posture, and cost exposure across every environment, at the speed your teams actually operate.
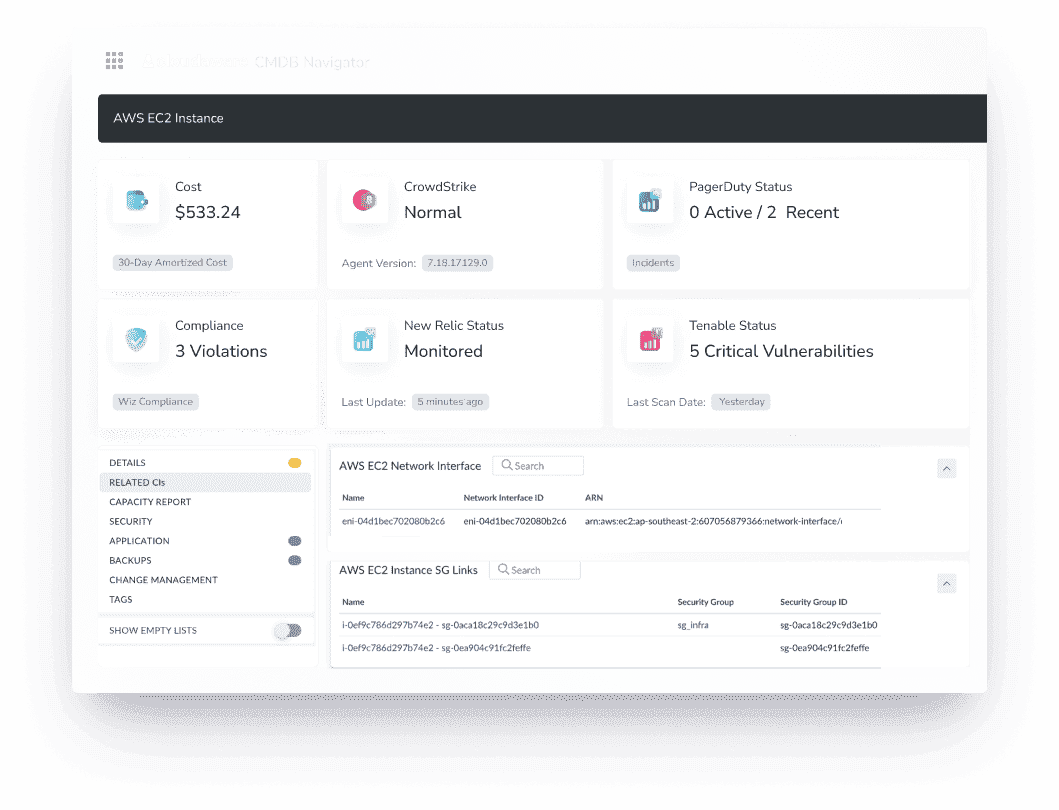
And it’s battle-tested. NASA and Coca Cola use Cloudaware to keep some of the most complex, high-stakes infrastructures on Earth under control. It integrates natively with AWS, Azure, GCP, Alibaba, and VMware, continuously pulling config data from services like AWS Config, Azure Resource Graph, and GCP Asset Inventory — no waiting, no blind spots, and no lost discovery data.
Here’s what you actually get:
- Real-time configuration discovery and change tracking, scoped to each CI — from IAM policies to load balancers.
- Cloud cost management tied to configuration state — flag untagged resources, idle spend, and cost anomalies per CI, team, or business unit.
- Software configuration management with SLA tiering, owner tagging, and lifecycle visibility.
- Compliance enforcement for CIS, internal hardening, and cloud security standards.
- Vulnerability context layered into CIs — see misconfigs and CVEs, in one view.
- SecOps support with intrusion detection signals from third-party tools mapped to exposed config.
- Slack, Jira, and ServiceNow alerts enriched with CI data, ownership, and remediation metadata.
- Dashboards by org unit, workload type, and control category — for audits, ops, and business leadership.
- Policy engine that helps you enforce good hygiene — config state, change velocity, and compliance in one place.
