If you’re responsible for security in a modern engineering organization, you’ve likely run into the same tension: security needs to move earlier in the pipeline, developers resist new gates, and compliance still expects clear evidence.
That’s where the idea of a DevSecOps framework becomes practical. Not as a definition, but as a way to answer a harder question: what does “good security” look like across a cloud-native delivery pipeline?
Most teams don’t adopt a single framework end-to-end. They combine NIST guidance for baseline expectations, OWASP controls for CI/CD, and supply-chain practices like SLSA. The challenge is turning those pieces into a coherent operating model.
This guide focuses on exactly that. It explains why any DevSecOps framework even emerged, how the major frameworks differ, and how cloud security engineering leaders apply them in real cloud environments — with clear trade-offs, not theory.
What a DevSecOps framework actually is (and what it is not)
For security engineering leaders, a DevSecOps framework is not a manifesto and not a toolchain. It’s a shared operating model that defines how security is embedded across the software delivery lifecycle, without relying on heroics or manual reviews.
A real framework answers questions teams argue about in practice: where security controls belong, which checks are mandatory versus contextual, what artifacts must exist at each stage, and how outcomes are measured. It creates consistency across teams and pipelines, especially in cloud environments where architectures change faster than policies.
 DevSecOps framework view showing how security integrates continuously across Dev and Ops workflows.
DevSecOps framework view showing how security integrates continuously across Dev and Ops workflows.
What it is not is a list of best practices or a vendor reference architecture. Best practices describe what could be done; a framework defines what must be done, by whom, and how it is validated continuously. Likewise, a framework does not prescribe specific tools. It defines control objectives and evidence expectations that tooling should satisfy.
For DevSecOps to scale, security needs to behave like part of the delivery system, not an external checkpoint. A framework is the mechanism that makes that possible.
Read also: DevSecOps Architecture (A Practical Reference Model Teams Actually Use)
Why the DevSecOps framework was developed
DevSecOps frameworks emerged when it became clear that security could no longer function as a late-stage review in modern delivery environments. As organizations moved to continuous integration and continuous delivery, the assumptions behind traditional security processes stopped holding.
What changed was not only speed, but the nature of risk itself. Security controls that worked in slower, centralized environments could not keep up with distributed cloud systems, automated pipelines, and third-party dependencies. The result was growing exposure combined with declining visibility.
At that point, teams did not need more best practices. They needed a structured way to decide where security must happen, what can be automated, and what evidence should exist by default. That need is what led to the development of DevSecOps frameworks.
Drivers behind DevSecOps frameworks:
- CI/CD eliminated the feasibility of end-of-cycle security reviews
- Cloud-native architectures increased blast radius and configuration risk
- Software supply chain attacks turned build systems into attack surfaces
- Compliance expectations outpaced manual controls and documentation
These pressures made incremental process tweaks insufficient. Security had to be redesigned as part of the delivery system itself.
Why DevOps alone could not scale security
DevOps optimized for speed, reliability, and repeatability, but it assumed security could be layered on through reviews, exceptions, and post-deployment fixes. That assumption breaks down under regulatory pressure and cloud velocity.
As infrastructure became ephemeral and environments changed daily, security teams could no longer rely on static approvals or point-in-time assessments. Without a framework, DevOps pipelines moved faster than security could observe, let alone influence. DevSecOps frameworks exist to close that gap by making security controls and evidence generation native to the pipeline, not external to it.
Read also: How to Build a Secure DevSecOps Toolchain Without Alert Fatigue
Core stages of a DevSecOps framework (pipeline view)
In practice, a DevSecOps framework only works if it follows the way software is already built and shipped. As soon as security introduces its own parallel lifecycle, teams stop treating it as part of delivery and start treating it as overhead.
That’s why most frameworks are built around the delivery pipeline itself. Not to prescribe tools or exact implementations, but to make expectations explicit: where security decisions are made, where controls apply, and what proof needs to exist afterward. When those expectations are clear, automation becomes possible and reviews become the exception, not the rule.
DevSecOps stages in a typical framework:
- Plan: security requirements, assumptions, and constraints are defined before work starts
- Code: expectations around code quality, dependencies, and secret handling are enforced early
- Build: the integrity of artifacts and the build process itself becomes a security concern
- Test: controls are validated automatically, not through ad-hoc reviews
- Release: decisions about trust, approval, and traceability are made explicit
- Deploy: environments enforce identity, configuration, and access boundaries by default
- Operate: runtime behavior is monitored and security signals feed back into the system
 Core stages of a DevSecOps framework, with security controls and evidence flowing across the pipeline.
Core stages of a DevSecOps framework, with security controls and evidence flowing across the pipeline.
What turns this into a framework is not the list of stages, but the discipline behind them. Each stage produces evidence that something was checked or enforced. Over time, those artifacts add up to a continuous security record that can keep up with cloud-native delivery.
Read also: Inside the DevSecOps Lifecycle: Decisions, Gates, and Evidence
Popular DevSecOps frameworks for cloud security
When teams look for DevSecOps frameworks in a cloud context, they are usually trying to solve a specific problem: how to apply consistent security controls across fast-moving pipelines, ephemeral infrastructure, and shared platforms without losing visibility or auditability.
There is no single dominant framework that covers everything. Instead, most cloud security programs rely on a small set of widely accepted frameworks, each addressing a different layer of the problem. Understanding what each one actually provides is more useful than trying to adopt any of them wholesale.
NIST and the DevSecOps framework confusion
Searches for a “NIST DevSecOps framework” often assume that NIST publishes a single, end-to-end DevSecOps model. In reality, NIST approaches DevSecOps indirectly, through a collection of standards and reference guidance.
For most teams, this usually means the Secure Software Development Framework (SSDF) as a baseline for required practices, combined with applied guidance from NIST’s DevSecOps and cloud-native work.
NIST focuses on what outcomes must be achieved and what risks must be addressed, not on prescribing pipeline design or tooling. This makes it well suited for regulated environments, but less prescriptive for day-to-day engineering workflows.
OWASP, SLSA, and SAMM in cloud-native environments
Other frameworks tend to be more pipeline-oriented and easier to map directly to CI/CD.
OWASP’s DevSecOps guidance concentrates on where security controls belong in the pipeline and how they evolve as delivery matures.
SLSA narrows in on software supply chain integrity, defining levels of assurance for build provenance and artifact trust.
OWASP SAMM, by contrast, provides a maturity model that helps teams assess how far their practices have progressed across governance, design, implementation, and operations.
Commonly used DevSecOps frameworks for cloud security:
- NIST SSDF and related DevSecOps guidance for baseline expectations and compliance alignment
- OWASP DevSecOps Guideline for pipeline-level security controls
- SLSA for software supply chain integrity and provenance
- OWASP SAMM for measuring and improving security maturity over time
In practice, strong cloud security programs combine these frameworks, using each where it is strongest rather than forcing one to fit every use case.
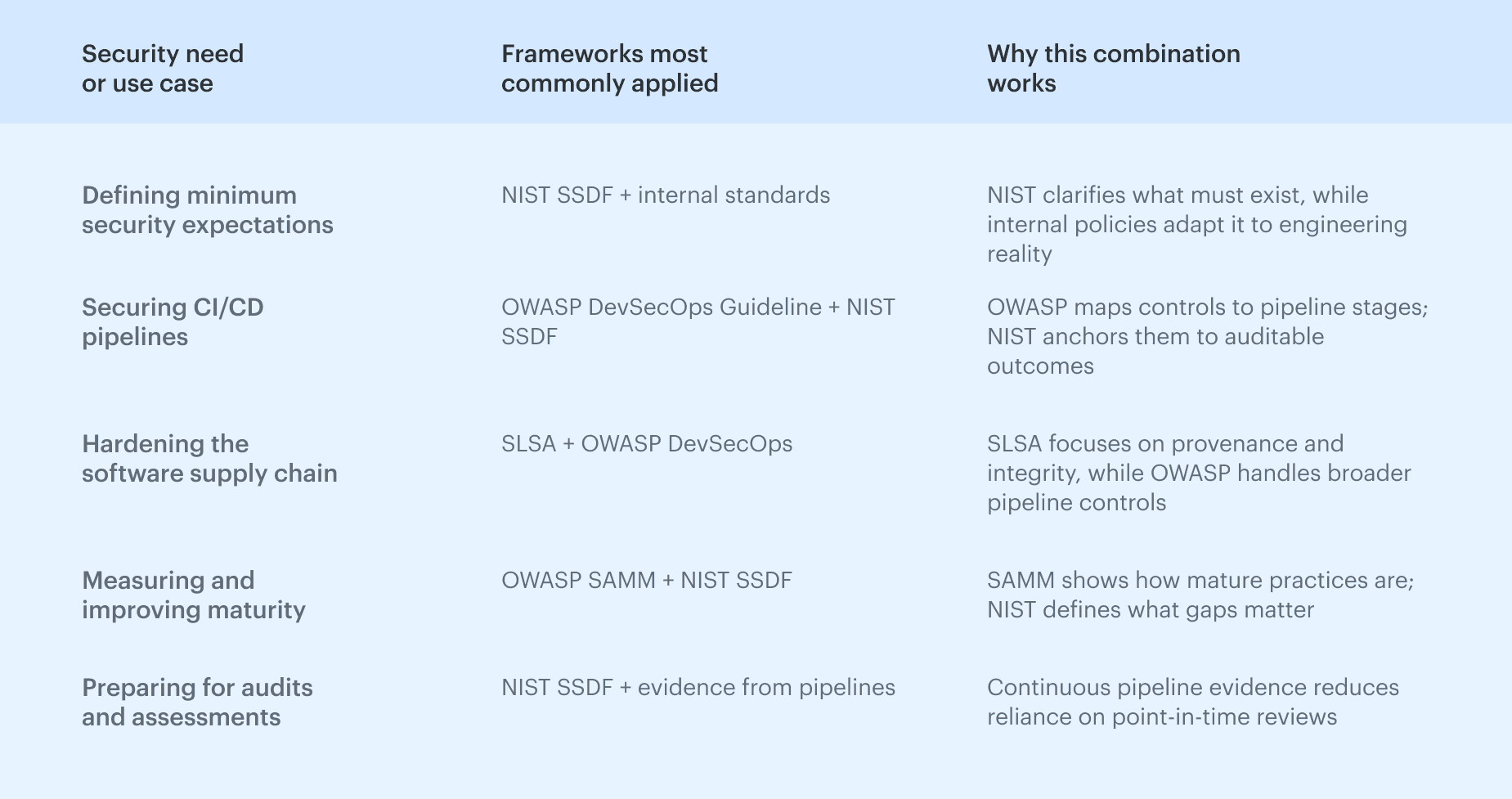 How teams combine DevSecOps frameworks like NIST, OWASP, SLSA, and SAMM for specific security needs.
How teams combine DevSecOps frameworks like NIST, OWASP, SLSA, and SAMM for specific security needs.
Read also: Top 13 Cloud Monitoring Tools Review (Pros/Cons, Features & Price)
Mapping DevSecOps frameworks to cloud security controls
Frameworks start to matter only when teams can point to real controls and say, “this is where it lives.” Until then, DevSecOps stays theoretical, and security decisions drift back into one-off reviews or tool-driven debates.
Cloud environments force this issue. Infrastructure is short-lived, permissions change constantly, and deployments happen far too often for manual oversight. If a security control is not tied to the pipeline or the platform, it will be missed sooner or later.
Different frameworks approach the problem from different directions. NIST is concerned with outcomes and expectations. OWASP focuses on where security belongs in the delivery flow. SLSA narrows the scope to build integrity and trust. In practice, security teams end up stitching these perspectives together into a single control map that engineering teams can actually follow.
Cloud security controls commonly mapped across the DevSecOps pipeline:
- Identity and access rules enforced as part of build, deploy, and release workflows
- Infrastructure-as-code checks that catch configuration issues before they reach production
- Container and Kubernetes controls applied consistently, not per team or cluster
- Secrets and key management handled through the platform, not embedded in code
- Policy checks that run continuously and leave an auditable trail
- Runtime monitoring that ties alerts back to deployments and owners
When controls are mapped this way, arguments tend to disappear. Teams stop debating whether security belongs in the pipeline and start focusing on whether controls are effective and visible. The same mapping also makes audits easier, because the evidence already exists as a byproduct of normal delivery.
Read also: What Breaks in Delivery When DevSecOps vs SDLC is Misunderstood
What DevSecOps framework is best for teams in 2025 and 2026
This is usually the point where articles dodge the question. There is no universally “best” DevSecOps framework, because frameworks exist to solve different problems. The better question is which framework fits your delivery model, risk tolerance, and regulatory reality.
In 2026, most teams are not starting from scratch. They already have CI/CD, cloud platforms, and some security tooling in place. The decision is less about adopting a framework wholesale and more about choosing which framework sets the rules, and which ones fill specific gaps.
Choosing the best DevSecOps framework by team type
Framework selection guide:
- Regulated enterprises. NIST SSDF usually becomes the anchor. It provides clear expectations that map well to audits and external assessments. The trade-off is that teams need to translate outcomes into pipeline controls themselves.
- SaaS and scale-ups. OWASP DevSecOps guidance tends to resonate more. It aligns naturally with CI/CD and allows teams to evolve controls as automation matures, with less upfront process weight.
- Government and defense. In government and defense settings, teams usually anchor on NIST-based guidance and extend it with additional control catalogs.
- Platform teams. Platform teams rarely stick to a single model. OWASP guidance tends to shape what happens in CI/CD, SLSA strengthens the build and artifact chain, and NIST sets the floor everyone has to meet. The hard part is not picking a framework, but keeping these pieces aligned as platforms and teams evolve.
In the end, the “best” framework is simply the one teams can use day after day, explain without hand-waving, and stand behind when questions come from engineering, auditors, or leadership.
Read also: 4 DevSecOps Implementation Steps That Hold Under Release Pressure
How to operationalize a DevSecOps framework (beyond theory)
Most DevSecOps frameworks fail at the same point: they are agreed on, documented, and then quietly bypassed once delivery pressure returns. The gap is rarely the framework itself. It’s the lack of an operating model that fits how teams actually work.
Operationalizing a DevSecOps framework means turning expectations into defaults. Controls have owners. Evidence is produced automatically. Decisions are visible without extra meetings. When that happens, security stops feeling like a separate initiative and starts behaving like part of delivery.
Frameworks provide structure, but execution depends on how clearly responsibilities are defined and how consistently signals flow back into engineering. Without that, even well-designed frameworks drift into shelfware.
Operating model: roles, evidence, and governance
What mature DevSecOps looks like:
- Clear ownership of controls and outcomes, so security responsibilities do not disappear between teams
- Continuous evidence generated by pipelines and platforms, not assembled manually for reviews
- Metrics tied to risk, focusing on exposure and impact rather than tool activity
- Audit-ready artifacts available at any time, without special preparation cycles
- Feedback loops into engineering, where findings influence design, backlog priorities, and platform decisions
At this stage, a DevSecOps framework is no longer something teams “implement.” It becomes the way security is run day to day across pipelines and cloud platforms, adapting as systems evolve rather than being revisited only during audits.
How this looks in practice with Cloudaware
One of the hardest parts of operationalizing a DevSecOps framework is keeping intent and reality aligned over time. Frameworks define what should happen, but cloud environments change constantly, and drift appears quietly.
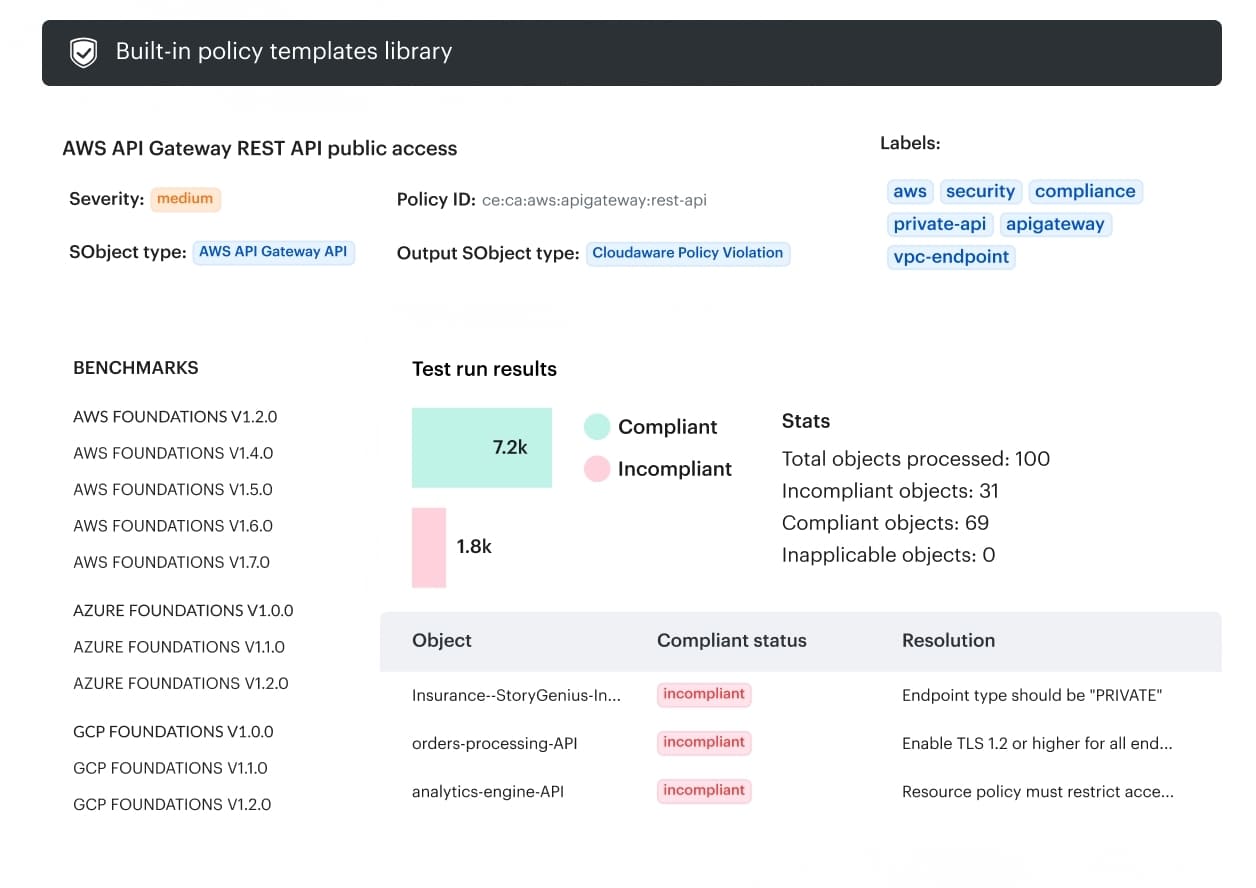 Example of Cloudaware interface: continuous policy checks and evidence.
Example of Cloudaware interface: continuous policy checks and evidence.
In practice, Cloudaware is used to help teams close that gap by providing visibility and traceability after changes occur:
- Maintains a CMDB-backed inventory of cloud resources, identities, and configurations
- Tracks changes across cloud environments, including what changed and when
- Preserves approval and change history so decisions remain traceable over time
- Evaluates current configurations against defined policies and standards
- Surfaces configuration drift as environments evolve
