An IT Asset Lifecycle Management Policy is your north star for how every asset — cloud-native, on-prem, hybrid, whatever — gets tracked, controlled, governed, and eventually retired across its entire lifecycle. From the minute someone submits a provisioning request to when that asset is decommissioned and scrubbed clean from the CMDB, this policy lays out the who, what, when, and how.
And I’m not talking just laptops and mobile devices. I mean configuration items tied to real workloads. Think ELBs, Kubernetes clusters, Cloud SQL instances, or custom microservices wrapped in Docker. All the juicy pieces that make up your distributed architecture.
Because without lifecycle governance, your CMDB turns into a junk drawer. Full, messy, and totally unusable when it’s time to troubleshoot or audit.
But let’s zoom in. Because this policy isn’t just some dusty PDF nobody reads. It actually threads through every layer of your operational fabric.
Think:
- CI onboarding workflows. Automated discovery mixed with human approval steps — especially for non-cloud-native assets that don’t show up clean in your discovery tools.
- Change management processes. Every modification flagged, logged, and matched against approved baselines.
- Asset tagging strategies. Enforced naming conventions that play nice with FinOps, security audits, and service mapping.
- Ownership handoffs. When project teams rotate out or infra shifts from dev to prod, this policy makes sure accountability doesn’t vanish.
Now that we’ve set the stage — let’s get into the good stuff. Here’s what IT asset management policy actually includes and how it’s structured to keep your CMDB from becoming a graveyard of unknowns 👇
1. Clear scope and asset classification
This is where the chaos starts getting names, roles, and responsibilities. Because let’s be honest — if you don’t know what you’re managing, you’re not managing anything. Defining the scope means laying out exactly what counts as an asset in your environment. And I don’t mean in vague, high-level terms.
We’re talking about:
- Cloud resources like EC2s, S3 buckets, Cloud SQL, Load Balancers
- Containers running across your EKS, AKS, or OpenShift clusters
- VMs still holding critical legacy apps
- Serverless functions triggered by events or pipelines
- Physical devices humming quietly in the colo or edge sites
- Anything running software, delivering a service, or moving data
Here is an example of how the result may look like:
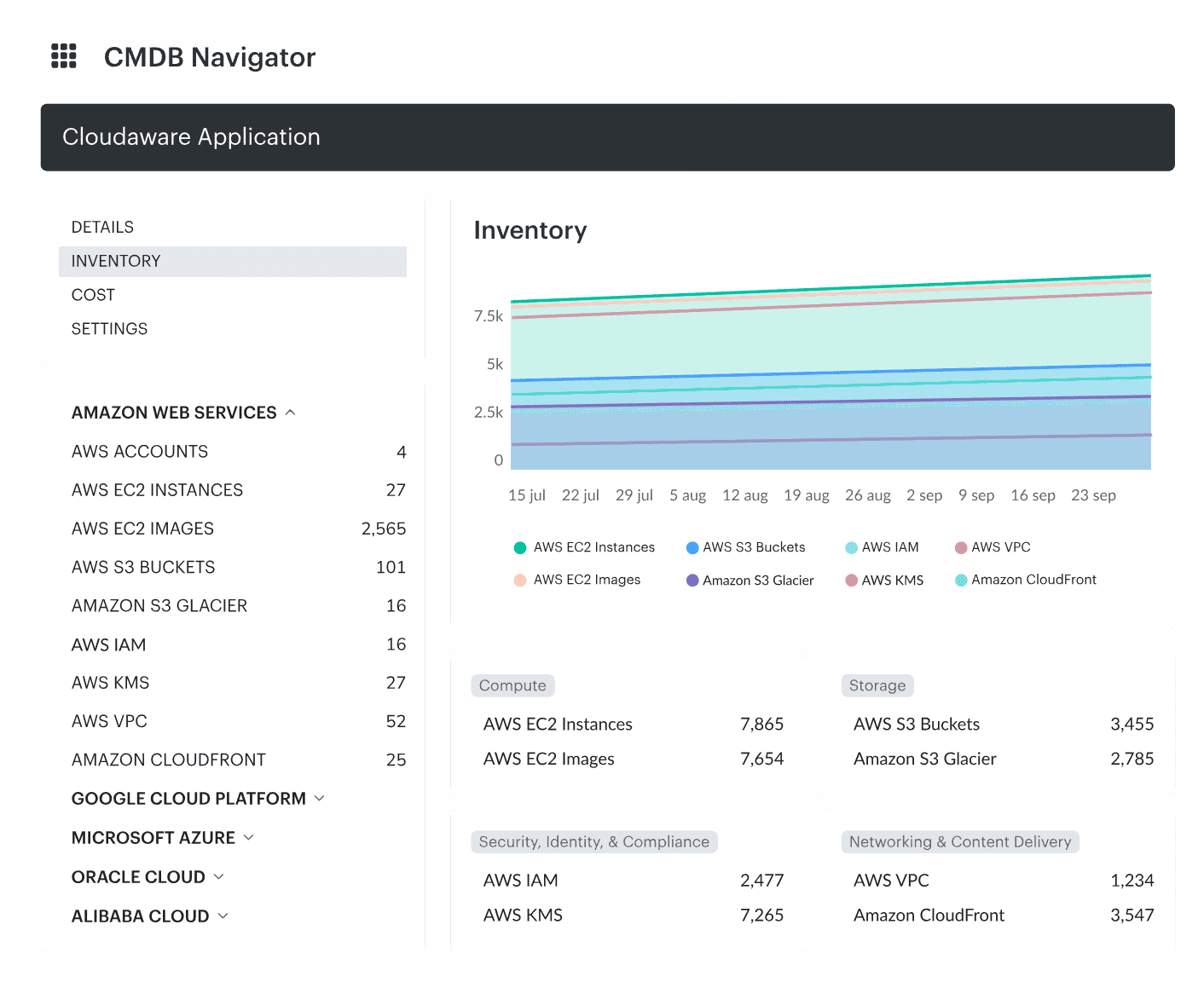
Wanna have the same for your setup? Talk to an expert.
If it consumes compute, stores information, or impacts a business process — it’s in scope.
Then comes the real power move: classification. Not just labels for visibility. I’m talking about a consistent taxonomy, built on top of strict tagging strategies, enforced naming conventions, and cloud-native standards. And it’s gotta work across clouds, regions, accounts, and team boundaries.
Why? Because classification unlocks automation, cost allocation, security context, and clean lifecycle tracking. It also fuels smarter discovery, gives clarity around ownership, and helps every downstream management policy stay aligned with reality.
Anna, ITAM expert at Cloudaware, shared this gem from a recent engagement with a Fortune 500 client juggling AWS, Azure, and on-prem Citrix beasts:
So yeah, scope and classification? Total game changers. They’re the foundation for accurate information, clean CI relationships, effective incident response, and zero-surprise audits.
Next up — let’s talk lifecycle statuses and how they shape the entire operational reality of your CMDB.
2. Lifecycle management across clouds
This is where things get real. You’ve got assets spinning up across AWS, Azure, GCP, and on-prem like it’s a global music festival. But without clear lifecycle stages — provisioning, active use, reassignment, decommissioning, and retirement — you’re basically letting those assets do whatever they want. For however long they want. And that’s exactly where cost spikes, security gaps, and compliance nightmares start creeping in.
This step is all about putting structure behind chaos. It means defining and enforcing asset lifecycle states across the board. Every Configuration Item — whether it’s a transient Lambda function, a persistent GKE node pool, or an old-school Linux VM running a core business service — needs a start, a middle, and an end.
And that end part? It matters more than most people think. That’s where cleanup happens. Where access is revoked. Where data is archived or deleted. And where your CMDB finally reflects what’s real.
For lifecycle to work across multi-cloud environments, you need a few key ingredients:
- Automated discovery across cloud and on-prem
- Clear ownership at every stage
- Integration with provisioning tools like Terraform, CloudFormation, or Bicep
- Lifecycle-driven policies for termination, reassignment, and archival
- Alignment with your management policy and internal standards
Without those, your services keep running long after the business needs have shifted. And your CMDB turns into a museum instead of a real-time control panel.
Kristina S., Senior Technical Account Manager at Cloudaware, dropped this story during a post-mortem of a client cleanup project:
That’s the power of lifecycle discipline. It’s not about bureaucracy. It’s about real-time information, cost control, and making sure your policy reflects actual infrastructure truth.
Up next? Let’s talk ownership and accountability — aka who’s responsible when things break, drift, or quietly rack up spend.
3. Ownership and accountability
Let’s talk about the moment nobody wants but everybody’s had — something breaks online, alerts go off, and the war room fills up fast. Someone drops the question: “Who owns this?” And suddenly, it’s a silent staring contest with the CMDB.
That’s why Ownership and Accountability isn’t just a checkbox in your IT asset management policy. It’s the part of your management policy that keeps incident response from turning into detective work.
When ownership is vague, everything slows down — MTTR, tagging compliance, even data classification reviews. And any hope of tracing issues across critical services? Gone.
You need to tie every asset — cloud, on-prem, SaaS — to a real team or person.
Not just a tag.
An accountable owner with escalation access, security context, and visibility into the software or service that asset supports. That’s what gives structure to lifecycle decisions, cost control, and operational clarity.
Mikhail Malamud, our GM, shared this from a Cloudaware rollout for a fintech company managing multi-cloud environments:
That’s what turns a messy CMDB into a business-ready platform. Ownership isn’t just for audits — it’s the glue that holds your information, security, and services together when it matters.
4. Asset discovery and inventory automation
This is the step that either keeps your infrastructure clean… or turns your CMDB into a pile of half-truths. Most IT asset management policies talk a big game here, but unless you’re wiring discovery into the way infra actually gets built, it’s just busywork.
Cloudaware changes the game by pulling fresh asset data directly from your cloud providers — across AWS, Azure, GCP, and on-prem — so your inventory stays current without relying on brittle spreadsheets or outdated scripts.
But here’s where it gets powerful: if you tag right during provisioning, Cloudaware ingests that information and instantly connects it to the correct configuration item, lifecycle stage, and business service.
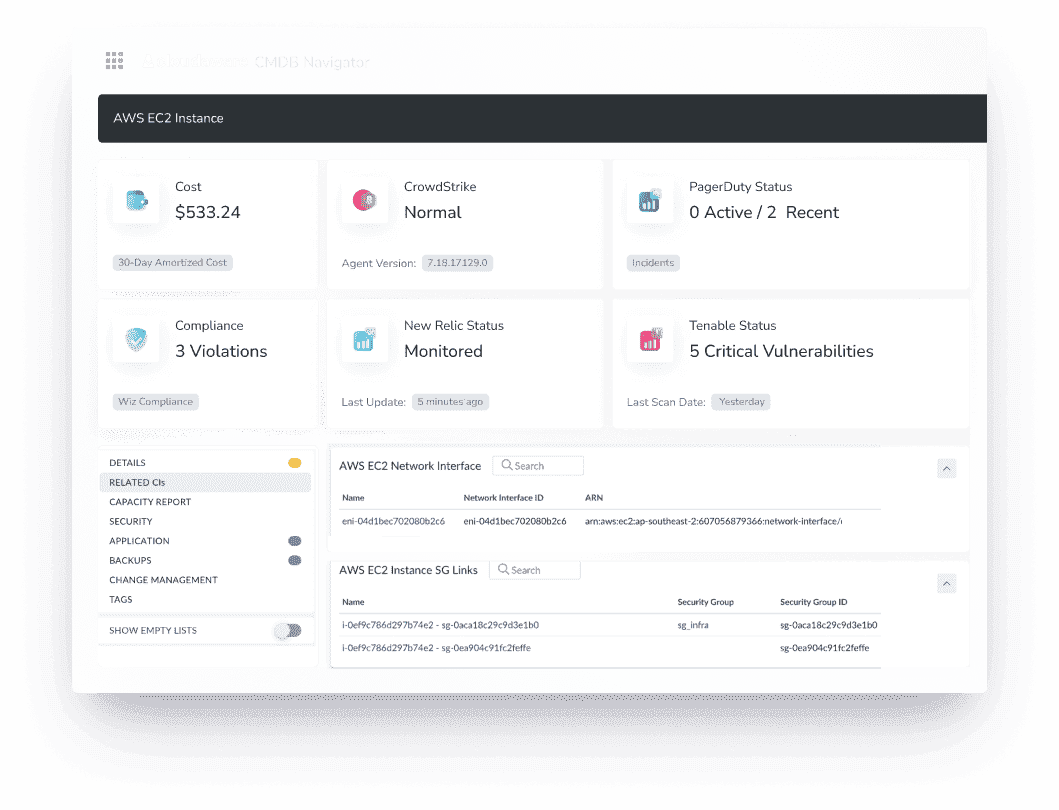
Wanna have the same for your setup? Talk to an expert.
And it’s not just about what’s online. You’re getting full visibility into what software is running, who owns it, what team deployed it, its security status, and how it fits into your services landscape. All that data feeds into your CMDB automatically, keeping your management policy grounded in real-world infrastructure — not assumptions.
Daria, our ITAM, dropped this advice during a Cloudaware rollout for a DevOps team juggling Terraform and CloudFormation:
That’s how you turn your management policy into an engine. Automate what matters, enforce your tagging standards, and let Cloudaware keep your assets, services, and data aligned without the overhead.
5. Cost visibility and optimization
The moment your IT asset management policy either saves your cloud budget… or makes your team look like they left the lights on for six straight weeks.
You’ve probably had that moment. The AWS bill spikes. Azure spend looks off. GCP cost anomalies. Suddenly, your team’s stuck in a blame spiral trying to match costs to owners — and all you’ve got is a mess of poorly tagged assets, and dashboards that don’t line up.
Here’s where Cloudaware steps in. It pulls multi-cloud billing data and overlays it with enriched information from your CMDB. That means every dollar spent is tied back to a real service, owning team, lifecycle state, even software type or usage. You stop guessing. You start knowing what’s costing what — and why.
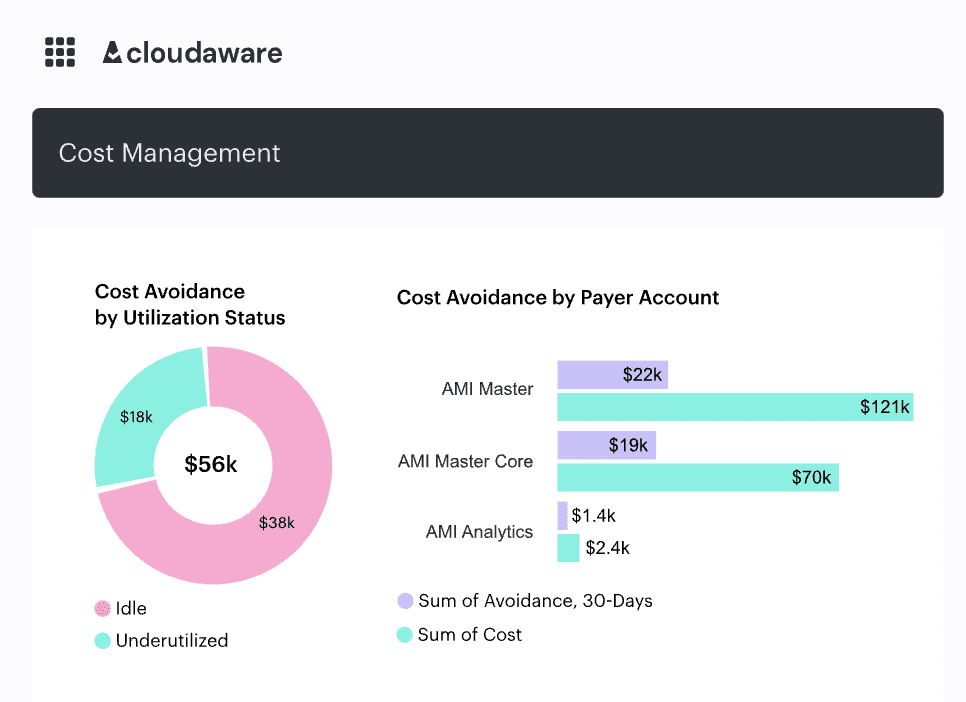
Here is an element of the Cost management report at Cloudaware. To see it live, schedule a demo.
And no, this isn’t just about finance. It’s about management policy enforcement, smarter budget reviews, and identifying gaps in security or compliance. If an asset is running but not attached to a known business service, you’ll see it. If something’s been forgotten in dev-east since last quarter? Yep, that too.
Mikhail Malamud, Cloudaware GM, shared a case from our FinOps-heavy SaaS client:
When your cost visibility is aligned with actual infra, policy, and information — your DevOps workflow doesn’t just look smarter. It is smarter.
6. Information security, risk, and compliance alignment
Infra gets deployed, and two hours later security is in your Slack asking who owns the public S3 bucket tied to that new service. Meanwhile, GRC is chasing a compliance export. They want a full list of every asset that handles regulated data, runs outdated software, or wasn’t built from an approved pipeline.
This is where your IT asset management policy either saves you — or throws you into a two-day scramble.
Information security alignment is about having structure that works before things get risky. Your management policy needs to track every asset’s lifecycle, tag it with sensitivity, and link it to a real person — not a generic team or mailbox. That’s what enables real visibility. Not just for audits, but for daily operations.
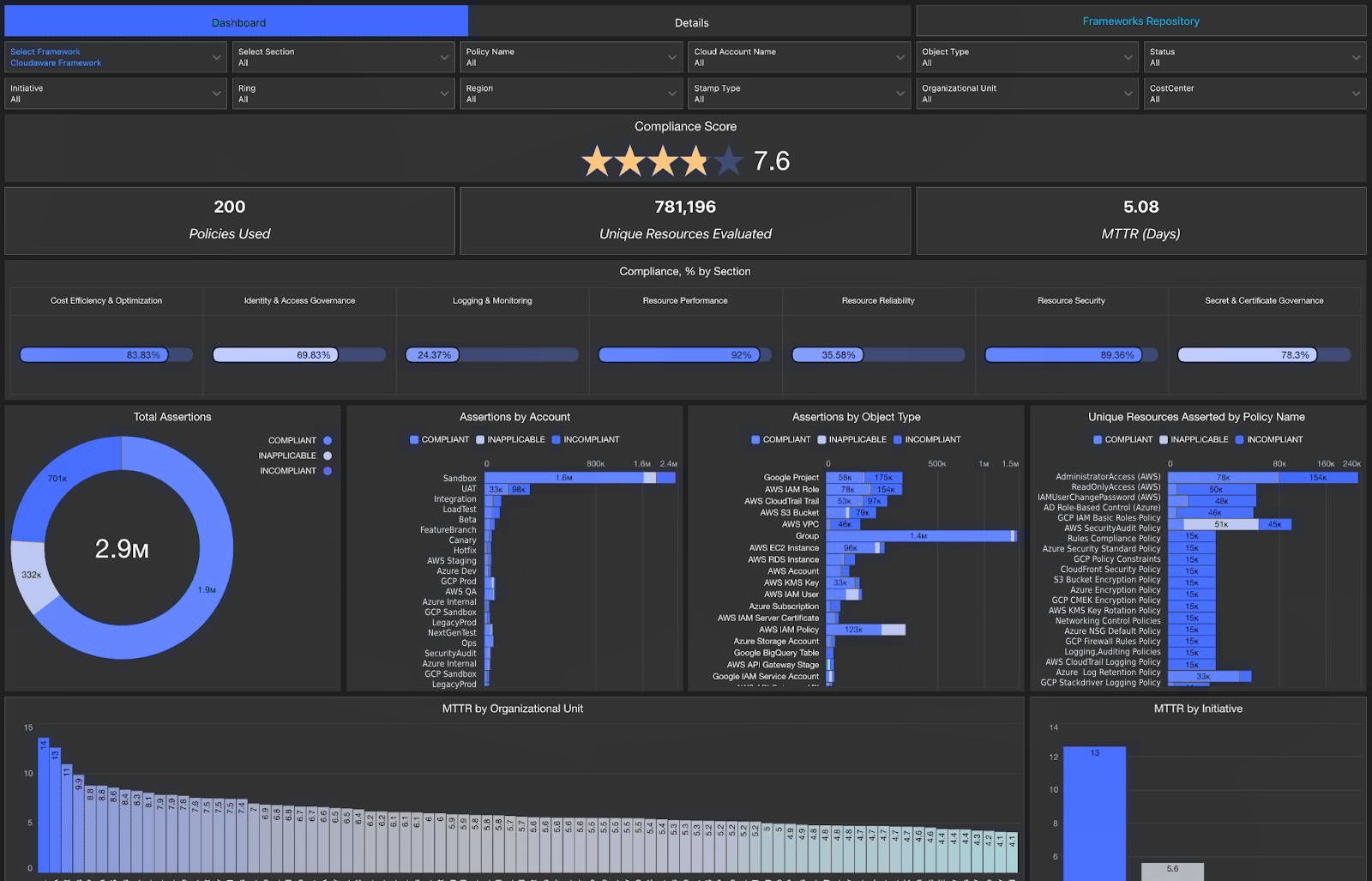
This is how the compliance audit report looks like in Cloudaware. Schedule a demo to see ti live.
And DevOps shouldn’t be retrofitting this stuff. It should be built into your flow — from IaC modules to discovery sync.
One of our ITAM experts Iurii shared this story after working with a fintech DevOps team prepping for a PCI review:
That’s what real alignment looks like. Your it asset management policy isn’t just for documentation. It’s a working map that makes information security, DevOps, and compliance actually function together.
7. Policy enforcement and automation
This is where the theory becomes practice. Where rules don’t just sit in a PDF, they show up in every deploy, every CI run, and every asset discovery event. Writing a policy is one thing. Enforcing it without slowing down your pipelines or overwhelming your teams? That’s where the engineering finesse comes in.
And DevOps doesn’t have time to play compliance babysitter. You need enforcement wired into how your infra gets built and managed — through pipelines, Git workflows, and metadata validation.
The goal isn’t to block progress. It’s to make sure every asset that lands in your environment carries the right tags, reports to the right service, and shows up with clean information in your CMDB. You’re not chasing violations.
You’re catching drift before it creates downstream issues. Automation does the heavy lifting so your platform and software delivery teams can focus on building — not fixing what was missed.
Kristina S., Senior Technical Account Manager at Cloudaware, shared this story from a media-tech client juggling AWS and GCP across dozens of active pipelines:
That’s what this step is really about. Clean policy execution. Quiet enforcement. And infrastructure that follows the rules — without constant reminders.
8. Data hygiene and accuracy
It starts small. A few assets marked “active” that were actually shut down last month. Tags missing on critical CIs. A terminated VM still showing up in your cost reports. And suddenly, your CMDB is full of ghosts. You're relying on information that looks right but hasn’t been right in weeks.
That’s why Data Hygiene and Accuracy deserves its own spotlight in your IT asset management policy. This isn’t a “set it and forget it” kind of thing. It needs to live inside your ops calendar. Because if the data behind your automations, software inventories, and service maps isn’t accurate, then every tool built on top of it starts to drift.
Anna told me about a client who ran a DR test and nearly faceplanted because nothing matched up.
That’s the goal. Not just clean records, but clean confidence. When the policy enforces the truth, your information becomes something you can actually use — not question.
9. Continuous improvement and feedback loops
Your policy needs versioning. It needs input from the engineers pushing software, the architects maintaining reference architectures, and the compliance leads mapping to new controls. You want structured reviews that pull real-time information from your ecosystem — so you're not debating hypotheticals, you're fixing what lagged in reality.
Mikhail, our GM, walked me through how they built that loop into a client’s ops rhythm:
That’s what makes the system hold up. A feedback loop that keeps your CMDB aligned with how your infra evolves — one piece of software, one asset, one deploy at a time.
How to write IT asset management policy
In this no-fluff interview, she breaks down exactly how to structure your policy, get buy-in, automate enforcement, and make it stick. Let’s jump in.
Me:
So, where do you even start?
1. Gather Requirements
Daria (ITAM Engineer):
Always with requirements.
You don’t start in a doc. You start in Slack. I schedule quick syncs with the people doing the work — DevOps, cloud architects, SecOps, GRC. The goal is to hear what’s failing in the field. One client’s platform team told me their IaC pipeline was getting blocked on compliance tags no one had access to. Another said their discovery tools were logging assets with zero service context, so cost reports were useless.
That stuff? That’s your base layer.
How to do it: Use a short form to collect input from each role.
Ask:
- “What’s the most painful part of tracking assets today?”
- “What do you wish the CMDB could answer for you automatically?”
- “What gets ignored or worked around?”
2. Define Scope & Objectives
Me: Okay, so you’ve got the raw feedback. How do you start shaping the actual document?
Daria: Scope first. You’ve got to be explicit. We list what the policy covers: all multi-cloud compute, storage, IAM policies, Kubernetes clusters, serverless, on-prem VMs, and SaaS services we integrate via SSO or agentless discovery. I also clarify what it doesn’t cover — like dev sandboxes or bring-your-own tools unless they touch regulated data.
Pro tip: Write the objectives like you’d write Terraform outputs. Clear, declarative.
- Ensure 100% of deployed assets are discoverable within 15 minutes
- Map each asset to a cost center and service owner
- Automate tagging and classification in all IaC workflows
3. Draft the Policy Sections
Me: Let’s talk structure. What does the draft actually look like?
Daria: Each section maps to a process. We write one for Discovery, Classification, Ownership, Lifecycle, Cost Tracking, Compliance Alignment, and Drift Detection. Each section includes:
- The standard
- Who owns enforcement
- What tools do the work (e.g., Cloudaware discovery, Terraform pre-checks, OPA policies)
- What happens if something goes out of bounds (Jira ticket, alert, automatic quarantine)
Example: In the Ownership section, we define that every deployed compute resource must have owner, team, and business_unit tags, with values validated against GitHub org and IAM. If the tags are missing at deploy, the merge request fails.
4. Review & Iterate
Me: This is where most policies go stale. How do you make it evolve?
Daria: You build it into the sprint. We set quarterly policy retros. It’s a 30-minute working session where we check what’s broken or noisy. DevOps flags fields that don’t match IaC reality. GRC checks if audit trail gaps are still unresolved. We show real metrics — like assets discovered with incomplete tags or misaligned lifecycle states.
How to do it: Run an internal dashboard with:
- Percentage of assets discovered but missing classification
- Assets without a control_owner
- Average time from deploy to CMDB visibility
If those numbers slip? It’s time to change the policy — not blame the team.
5. Approval & Sign-off
Me: And how do you get people to take it seriously?
Daria: Make it official. We route the final version through whoever’s responsible for asset governance — usually a combo of the IT Director, the Cloud Security Lead, and Compliance. If your org uses CAB (Change Advisory Board) for internal policies, it can go through that too.
Pro tip: Keep an audit log of who signed off and when. That way, when enforcement starts, no one’s surprised.
6. Implement & Automate
Me: Alright, final mile. How do you put it into motion?
Daria: Automation, always. We build policy enforcement into CI/CD, IaC, and discovery.
- Use Terraform modules with required_tags
- Apply OPA or Sentinel policies in GitLab/GitHub workflows
- Cloudaware auto-links related items and lifecycle data so you’re not stitching things by hand
- Build asset classification rules that trigger alerts when misaligned with expectations
Example: We worked with a client who created a CMDB rule that flagged any asset with env=prod and no security_owner. That triggered a Jira issue in their SecOps board automatically.
7. Communicate & Train
Me: Now how do you make people care?
Daria: Treat the rollout like a feature release. Short videos in Slack. 15-minute live demos with engineers. Targeted follow-ups with folks who own IaC libraries or service catalogs. The fewer assumptions you make, the better.
Hot tip: Create a Notion or internal wiki page called “How to Stay Compliant Without Thinking About It.” Link to the tooling, tag rules, CMDB view filters. Show, don’t just tell.
8. Track Metrics & Refine
Me: How do you keep the feedback loop alive?
Daria: Simple. You track the right KPIs. No vanity stuff — only what helps you fix friction and expose value.
Metrics I always include:
- Percentage of assets with full metadata (owner, env, service)
- Mean time to CMDB registration after deployment
- Volume of policy violations auto-resolved without human intervention
- Total drift events caught before impacting production
If you don’t measure it, your policy turns into shelfware. But if the numbers tell a story? You’ve got a policy that evolves with your stack.
Fix your IT asset lifecycle management policy with Cloudaware
If your IT asset lifecycle management policy looks great on paper but falls apart in practice — Cloudaware is built to fix that.
It keeps your asset data clean, current, and mapped to real ownership. From discovery to decommission, Cloudaware helps DevOps, SecOps, and cloud architects track everything without relying on spreadsheets or tribal knowledge.

Teams — including Coca Cola — use Cloudaware to gain full visibility into asset states, reduce audit chaos, and enforce lifecycle policies without manual chasing.
Key capabilities:
- Continuous multi-cloud asset discovery
- Lifecycle tracking and drift detection
- Policy-aware CMDB with related item mapping
- IaC and pipeline integration
- Automated ticketing and compliance reporting
