You ever look at your asset inventory and think... how did we get here? Half the EC2s don’t have tags, someone forgot to update a license, and that old Redis box in Virginia? Nobody owns it but it’s still serving traffic.
This is what happens when ITAM isn’t a strategy — it’s just a bunch of disconnected tools and panic scripts.
So I took everything I’ve learned working with enterprise clients at Cloudaware — all the chaos, the patchwork tooling, the last-minute audits — and turned it into 11 clear, tactical steps of IT asset management strategy.
This isn’t theory. It’s how we help DevOps and cloud teams go from asset anarchy to full-stack visibility.
1. Anchor everything to business risk & visibility
Okay, before you even think about tagging a single resource or syncing another discovery tool — pause. You need to lock in why you’re doing this in the first place. Not for the dashboard. Not for the spreadsheet. For risk and visibility that actually mean something to your business.
I’ve seen this step skipped so many times in large orgs.
The result? You’ve got AWS Config feeding into a CMDB, SCCM tracking endpoints, maybe even JAMF on laptops — and still, your CIS Control 1 posture fails because nothing ties back to real-world ownership or business relevance.
So before you dig into asset classification, define your visibility goals based on the biggest risks in front of you right now. Here’s what that usually looks like in the wild:
- “Every internet-facing asset must have ownership, purpose, and lifecycle metadata visible in the CMDB within 24 hours of provisioning” — This protects against unmanaged exposure and makes incident response faster and cleaner.
- “All systems handling sensitive or regulated data must be mapped to their associated business processes and tagged with compliance scope (e.g., PCI, ISO, FedRAMP)” — This reduces audit friction and helps isolate scope during remediation.
- “Every asset must be tied to an identity — either a team or CI/CD pipeline — and auto-expire if it goes untagged or unused for X days” — This prevents ghost infrastructure and reinforces accountability.
- “All cloud cost anomalies above a set threshold (e.g., 15% week-over-week) must be traceable to a named asset group and business unit” This aligns FinOps with ITAM and eliminates surprise invoices.
- “Any asset created via infrastructure as code must include injected tags for owner, environment, criticality, and expiry — enforced at the pipeline level” — This helps DevOps move fast without breaking visibility.
How it works in practice
Here’s how one of our clients actually anchored their it asset management strategy to business risk and visibility:
They kicked things off by reviewing their risk register — not the generic GRC-level one, but the operational version built from incident history, audit findings, and SecOps escalations. That surfaced a few key IT asset management risks:
- Unauthorized changes in regulated VPCs
- Unknown assets with access to customer PII
- Long-lived cloud services with no audit trail or change history
From there, they looked at which systems and services had poor visibility — places where discovery tools weren’t reaching, or where context was too thin for decisions. Think unmanaged Lambda, orphaned EBS volumes, or workloads in staging environments that never made it into reporting.
Instead of jumping into tagging, they defined visibility goals per risk. Like:
- “Critical cloud services must have owner context and purpose visible in the CMDB within 24 hours.”
- “Resources operating in regulated environments must be discoverable and linked to known change pipelines.”
- “Any asset outside of CI/CD must be reviewed and justified through manual intake.”
Here’s my teammate Anna, ITAM expert advice at this step:
Here is how Cloudaware provides visibility on all aspects of the CI:
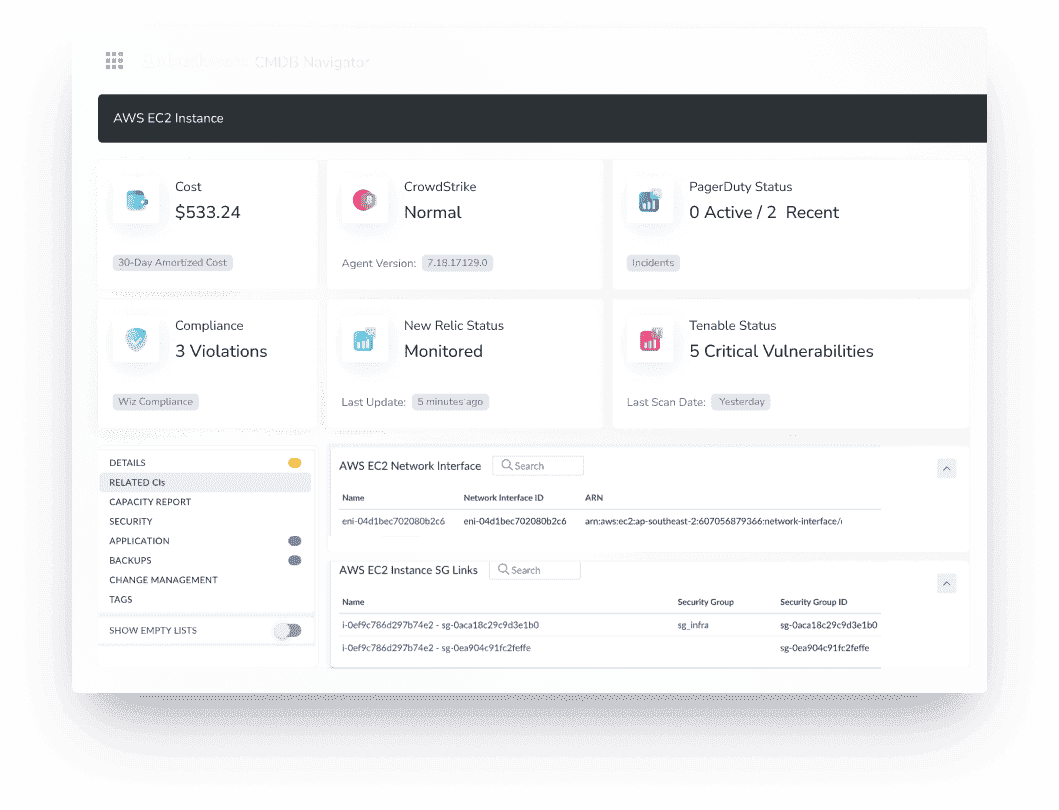
Wanna have the same for your setup? Talk to an expert.
This step is your key to making the rest of your strategy actionable. Get it wrong, and your ITAM just becomes another ticket backlog. Get it right? You’re already winning before you name your first asset.
2. Scope what ‘assets’ actually mean to you
At this point, your job is to define what should be included in your it asset management strategy based on business risk, technical relevance, and operational need. You’re not tagging yet, not prioritizing — you’re just drawing the lines.
Here’s how to approach it: look at your infra, processes, and audit requirements, and ask:
What assets need to be visible for us to stay compliant, secure, and cost-aware?
That includes the obvious stuff
- physical devices,
- VMs,
- storage
but also the slippery ones
- ephemeral containers,
- IAM roles,
- KMS keys,
- unmanaged SaaS accounts,
- networking rules,
- build pipelines,
- DNS records.
If it can store data, access data, route traffic, or cost money? It's in scope for asset tracking.
How it works in practice
One of our enterprise clients ran into this exact problem. Their CMDB was technically “complete,” but it excluded anything ephemeral or not running for more than 24 hours. That included Lambda functions, AKS pods, and spot instances.
During a red team engagement, they realized an unscanned AKS cluster exposed an internal API — no tags, no logging, no alerts. They had scoped by what was easy, not by what was risky.
So they redefined their scope. Anything that could hold or transmit sensitive data, escalate privileges, or punch out to the public internet was now considered in-scope — regardless of lifespan or how hard it was to track. That meant bringing in not just compute, but also:
- Short-lived workloads from AKS and ECS
- Serverless functions (Lambda, Azure Functions, Cloud Run)
- IAM roles with admin or cross-account permissions
- Cloud-native storage (like unmanaged S3 buckets and Azure blobs)
- KMS keys, security groups, API gateways, and third-party software integrations
They prioritized what had the most potential business impact and built visibility requirements around those assets — not just the ones the CMDB already knew how to find. Everything was aligned with existing service management practices, ensuring operational ownership wasn’t disconnected from risk.
Here’s what my teammate Technical Account Manager Iurii Khokhriakov always tells clients at this stage:
Read also: What Is Asset Management Software Doing Behind the Scenes?
3. Classify & prioritize your IT assets
This step is all about giving structure to the madness: classifying what’s out there, tagging it with purpose, and deciding what gets your attention first when things go sideways.
And let me say this upfront: if you skip proper naming and tagging, you’ll spend your life chasing mystery resources and praying someone left a breadcrumb trail in Git. This step saves you from that pain.
Start by setting tagging standards as a part of your asset management strategy
This isn’t just for show — it’s core to your it asset management strategy. Your tags should answer three things:
- Who owns it?
- What’s it for?
- What risk surface or business function does it touch?
We help clients define a baseline schema that covers ownership (owner, team_email), environment (env, tier), criticality (data_class, impact_level), and cost tracking (cost_center, project_code). Everything is aligned with your existing naming conventions in Terraform, Ansible, and your CI/CD pipelines — and integrated with ITSM platforms for downstream workflows.
Name & Tag assets
Once you’ve got standards, name and tag your assets like you mean it — and make it sustainable. That means building a smart mix of automated and manual tagging.
Automation should hit everything flowing through your pipelines. Your Terraform, CloudFormation, and GitLab/GitHub Actions should inject tags at deploy time — env, team_owner, data_class, cost_center, expiry_date. You can bake that right into IaC modules or use OPA policies and CI linter rules to enforce tagging before merge.
Here is an example of how it looks in Cloudaware:
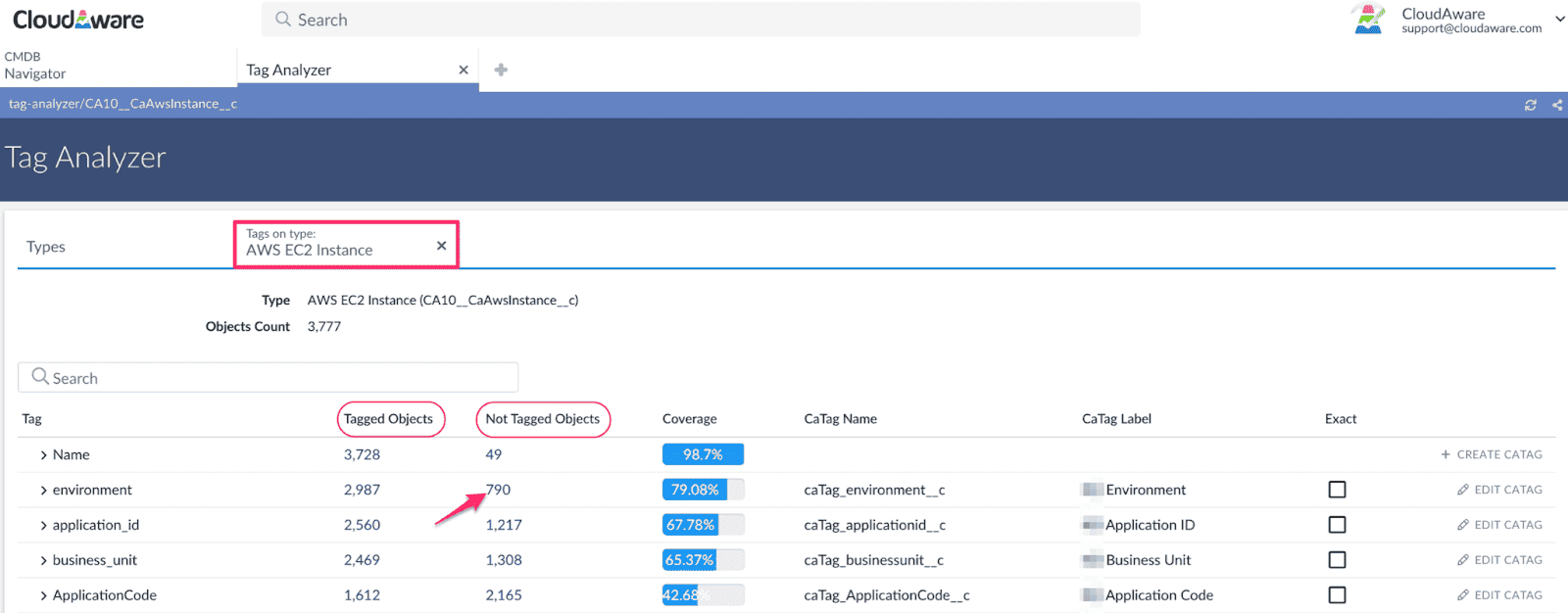
Wanna have the same system for your setup? Talk to an expert.
But automation alone won’t catch the messy stuff — like one-off console deployments, legacy VMs, or random SaaS tools someone expensed last quarter. That’s where you lean on manual tagging with context. Tie it to your intake process or change requests. Make it part of your operational hygiene — just like adding a runbook link or a monitoring config.
And yes, tag everything that runs, stores, routes, or authenticates:
- AWS: EC2s, RDS, EKS, S3, IAM roles, KMS keys, CloudFormation stacks
- Azure: VMs, SQL DBs, Logic Apps, resource groups, NSGs
- GCP: Compute Engine, Cloud Functions, Pub/Sub, IAM bindings
- Cross-cloud: SaaS services, DNS zones, third-party integrations
Asset tracking doesn’t stop at compute. Tag your DNS records, GitHub orgs, monitoring agents, even the bastion boxes no one admits are still around. The second it touches prod or regulated data, it’s worth tagging — whether the tool handles it or someone has to.
Read also: From Tag Spaghetti To Clean Inventory: Automated Asset Management
Then comes prioritization
Not everything needs full visibility on Day 1. Use business impact, compliance scope, and incident exposure to classify:
- Mission-critical (customer-facing, revenue-driving)
- Compliance-relevant (PCI, ISO 27001, HIPAA)
- Operational backbone (DNS, CI/CD, IAM, networking)
- Non-prod / sandbox / ephemeral
One client used this approach to identify that only 12% of their infra carried 80% of their business risk. That case showed how tagging and classification, when aligned with actual business goals, can transform ITAM from a reporting function to a proactive practice.
They focused tagging enforcement and CMDB reconciliation efforts exactly where it mattered — making their service management flows cleaner and more intelligent.
If your asset doesn’t have a name and a purpose, it doesn’t exist. You can’t secure it, you can’t track it, and you sure as hell can’t prove it’s compliant. Classify it. Tag it. Prioritize it. That’s where real control starts.
Next up: who actually owns this stuff.
4. Establish ownership & governance
You can have beautifully tagged EC2s, perfect Terraform modules, even a compliant CIS Control 1 report… but when something breaks, or a cert expires, or a misconfigured bucket gets flagged, someone’s going to ask: “Who owns this?” And if your answer is “we’re still checking” — you’re already behind.
This step is about making ownership a first-class field in your it asset management strategy. Every asset — from a Lambda function to a GCP firewall rule — should be traceable to a team, a service owner, or a CI/CD pipeline. And ownership shouldn’t live in a spreadsheet. It needs to be actionable, queryable, and enforced through policy.
How it works in practice
One of our clients — a fintech scaling across AWS and Azure — had dozens of internal teams spinning up infra weekly. They had tagging policies, sure, but enforcement was weak and ownership was...optional. During an incident, they discovered two critical S3 buckets with no linked owner, no logging, and no lifecycle policy — just leftover from a proof-of-concept.
So we helped them formalize ownership and bake governance into their delivery flow. Here’s what it looked like after we got things on track:
- Every asset had an assigned service_owner, linked to a team distribution list and an active Slack channel.
- Git repos were mapped to the software services deploying infra, and CI/CD pipelines pushed ownership metadata directly into Cloudaware’s CMDB.
- Changes required a valid team ID from a centralized registry — if it didn’t exist, the deploy failed pre-check.
- Infra teams had access to dashboards showing which assets had stale ownership, missing contacts, or expired credentials — with escalation flows wired into their service management tooling.
- Governance policies were codified via OPA rules and enforced org-wide through Terraform Sentinel and Azure Policy.
Now when someone asked, “Who owns this?”, the answer wasn’t buried in a wiki or an old Jira comment. It was one query away, in a system that everyone trusted. That’s ownership — established, enforced, and operationalized as a best practice across the business.
Here’s what Kristina S., Senior Technical Account Manager at Cloudaware always tells clients when they talk about setting ownership:
5. Standardize the lifecycle
This is the part where we stop pretending infra just “exists” forever. Every asset — from that EKS node someone spun up at 2 AM to that ancient IAM role no one wants to delete — has a lifecycle. The problem is, most orgs skip the part where they define what that lifecycle actually is.
This step is where you build the muscle to stop asset sprawl before it starts. You’re standardizing how assets get requested, approved, deployed, monitored, modified, and eventually retired. Not ad hoc. Not “we’ll clean it up later.”
You bake the lifecycle into the system. It runs as part of your pipelines, your ITSM, your change requests, and your offboarding routines.
And it matters. Because if you’ve ever paged through your CMDB and found thousands of “active” EC2s with no log activity, no recent patching, no known owner — yeah, you know the pain. Or when a surprise PCI audit hits and you can’t prove which assets are still authorized per CIS Control 1.
That’s when lifecycle chaos shows up in the real world — and disrupts more than just IT. It puts the business at risk.
Read also: Hybrid IT? 10 Asset Lifecycle Management Software You’ll Love
How it works in practice
One of our clients had this exact mess. Leftover POCs, half-migrated workloads, forgotten dev clusters. We helped them roll out a five-phase lifecycle model:
Requested → Provisioned → Active → Retired → Expired.
Cloudaware flagged assets that stayed idle too long or hadn’t been touched since creation. If you didn’t validate it, it didn’t stay running. If it wasn’t monitored, it was flagged for review.
They wired lifecycle tracking into their Git workflows, Terraform state checks, and service management approval paths. Just like that, “infra cleanup” went from a quarterly panic to a quiet, daily practice. Lifecycle became a core piece of their it asset management strategy, fully integrated with cost control, audit readiness, and ITAM ops.
This is what Mikhail Malamud, Cloudaware GM, always says when teams ask how to fix the chaos:
Read also: Top 10 Enterprise Asset Management Software Features & Pricing
6. Automate discovery & reconciliation
Let’s be honest: no one has time to track assets manually anymore. Teams are launching environments from GitHub runners, tweaking IAM policies at 3 a.m., and deploying functions that live for 20 minutes but expose real risk. If discovery isn’t automated — and reconciliation isn’t constant — your CMDB will always be behind, and so will you.
This step is about plugging in everything. AWS, Azure, GCP, VMware, Alibaba Cloud, even the odd on-prem fleet that still runs critical workloads — all of it. You connect your cloud accounts to Cloudaware, and we start listening. We pull state from every API that’ll talk, and feed it straight into the CMDB with context: owner, region, lifecycle state, and configuration drift.
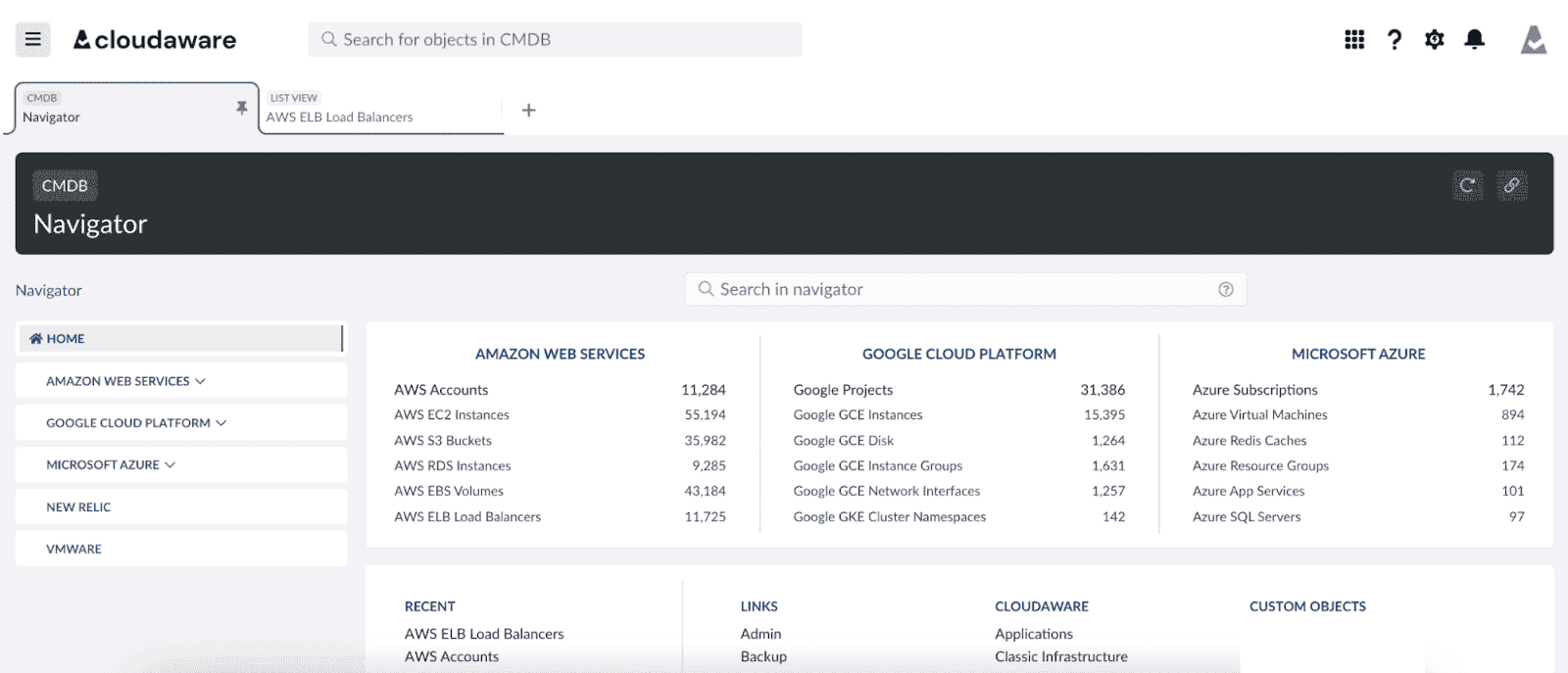
Wanna have the same view for your setup? Talk to an expert.
Anna, ITAM expert who handles these integrations for clients daily, puts it best:
Here’s how you get it working without writing custom scripts on a Sunday night:
- Connect accounts via secure API auth
- Enable discovery with native services like AWS Config, Azure Resource Graph, GCP Asset Inventory
- Normalize the data into your CMDB with lifecycle and policy metadata
- Reconcile against IaC, CIS Control 1 baselines, and your internal asset management strategy
- Alert or escalate anything misaligned — before it becomes a ticket (or worse, an incident)
This gives your organization more than just inventory. It gives you a real-time, policy-aligned map of what’s actually running. That’s the key to proactive governance — and the only way your software and infra teams can make clean, confident decisions at scale.
In case you’re wondering if it’s worth it: the teams who automate this stop firefighting. They start managing. And the business feels it.
Alright. Now that the machines are talking, let’s follow the money.
Read also: Find It, Track It, Own It: Multi-Cloud IT Portfolio Management
7. Track costs & contracts
When your automation is enabled, and you see all IT assets within your infrastructure, it’s time to talk about what they are doing to your budget. Whether that spend makes any operational sense?
This step is where your ITAM program starts pulling its weight in front of Finance. Because tracking cloud spend in a silo doesn’t work. What matters is connecting usage to ownership, aligning contracts to consumption, and making cost behavior visible where decisions actually happen — inside engineering and ops.
Here is an element of the FinOps report from Cloudaware:
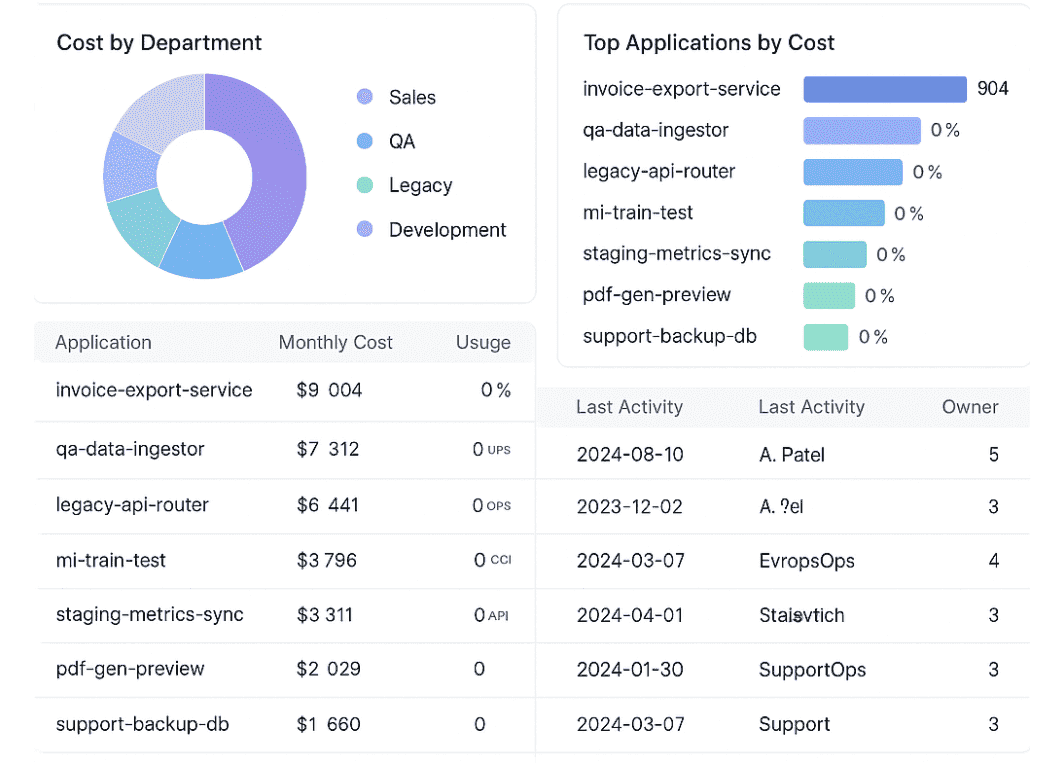
The good news? You don’t need a dozen spreadsheets to make this happen. Just wire your cloud billing into your it asset management strategy, and let the tooling do the heavy lifting.
Daria, our ITAM who lives in FinOps dashboards and drinks coffee out of a billing export — lays it out like this:
How it works in practice
Here’s a real case: one client used Cloudaware to forecast usage across their dev and staging environments ahead of quarterly planning. The system flagged an environment spiking IOPS for no reason. Turns out a forgotten CI job was hammering storage for two weeks straight. They killed the process, avoided network throttling issues, and saved on costs tied to unnecessary I/O. That one alert spared them both performance headaches and awkward budget convos.
Now your cost data is working for you — not haunting you. You’ve got control, clarity, and a contract view that’s finally aligned with your actual software, service deployments, and long-term maintenance plans.
This is how your organization turns passive billing data into proactive tracking. Let’s roll into risk next. It’s about to get spicy.
8. Monitor compliance & risk
This is the spine of a healthy asset management strategy. You’re not just tracking what you own — you’re monitoring how it behaves over time. Whether it’s a forgotten S3 bucket, an unscanned container image, or a stale IAM role with admin privileges — these aren’t static problems. They’re signals waiting to escalate if your organization isn’t watching.
So what do you actually do at this step? You turn risk monitoring into a daily motion. That means:
- Aligning each asset class to compliance requirements — like PCI, SOC 2, ISO 27001, or CIS Control 1.
- Mapping those controls to concrete checks — open ports, insecure protocols, missing encryption, failed patch SLAs.
- Defining what “non-compliant” looks like per environment — prod vs test, internal vs external, PII-handling vs non-sensitive.
- Setting up real-time alerting and escalation for anything that drifts from baseline.
- Feeding that data back into your CMDB, ITSM tooling, and compliance dashboards — so your service teams can take action.
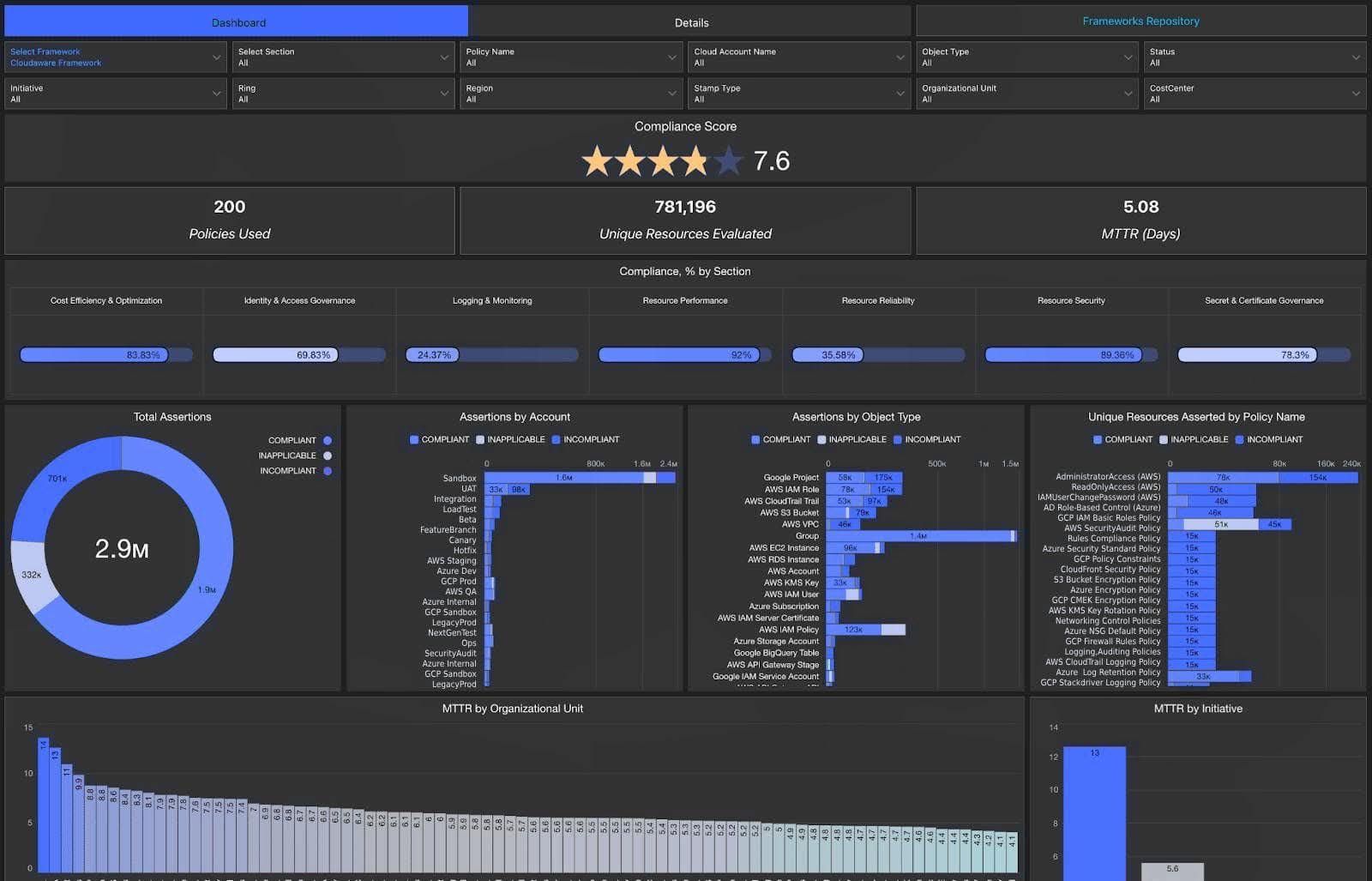
This is how the compliance audit report looks like in Cloudaware. Schedule a demo to see ti live.
Mikhail Malamud, Cloudaware GM, lays it down like this:
One case that nailed it: a client used Cloudaware to monitor open ports against CIS baselines. It flagged an exposed RDP port in a PCI-scoped VNet — something manual checks had missed for months. Because that asset was linked to the CMDB and tagged under “critical,” it triggered a SecOps workflow within minutes. Auto-ticketed, auto-routed, auto-closed.
No panic. No breach. Just governance, working the way your business expects your software and systems to behave.
Read also: Software Asset Management for Hybrid DevOps Done Right
9. Define ITAM KPIs & report like a boss
This step is where you stop just tracking assets and start measuring how well your organization is managing them. KPIs make your IT asset management strategy real — not just operationally, but politically. They’re the proof that your tagging isn’t just for decoration and your lifecycle rules aren’t just wishful thinking.
Some key KPIs I always recommend:
- % of assets with valid owner, environment, and lifecycle metadata
- % of services tied to business units and cost centers
- Time to remediate high-risk misconfigs (CIS Control 1, PCI scope, NIST tags)
- Drift volume between deployed state and IaC
- Volume of unmanaged or orphaned software by cloud and region
Iurii, our Technical Account Manager, lives in reports and says it like this:
One case I’ll never forget: a client was mid-FedRAMP audit when the reviewer asked for asset ownership proof — tied to lifecycle status and remediation logs.
They pulled up their Cloudaware KPI dashboard on the spot.
Every critical asset, tagged with owner and policy context. Remediation timelines. Last change source. The auditor actually said, “This is what we wish more organizations had.” No delays. No scrambling. Just clean, accountable data.
10. Train, evangelize, repeat
ITAM isn’t a one-and-done rollout. It’s culture work. If your teams can’t tell the difference between lifecycle tagging and logging, your strategy’s gonna fall flat by Q2.
So here’s the play: bake training into every process that touches organization infrastructure. New hire onboarding? Add it. Sprint kickoff? Do a 10-minute spotlight. Monthly engineering all-hands? Showcase your latest ITAM win.
We recommend quarterly deep dives for platform and SecOps leads — and lighter monthly refreshers for service owners. Use real incidents, audit flags, IaC drift, and CIS misses to make it stick.
One client built a “Why It Broke” series — short debriefs after every misconfiguration. It became a Slack hit. Their CMDB adoption doubled in six months.
If you want governance to live past next quarter, don’t just document. Preach. Celebrate. Build the muscle. Repeat until it’s muscle memory — or at least meme-worthy.
CMDB - your single source of truth
Without a single source of truth, all those beautiful ITAM steps? Just slides in a deck. Cloudaware CMDB makes your entire it asset management strategy click into place — across clouds, across teams, across your entire organization.
It connects natively to AWS, Azure, GCP, VMware, Alibaba Cloud, and even your crusty on-prem stack. One link. Instant visibility.
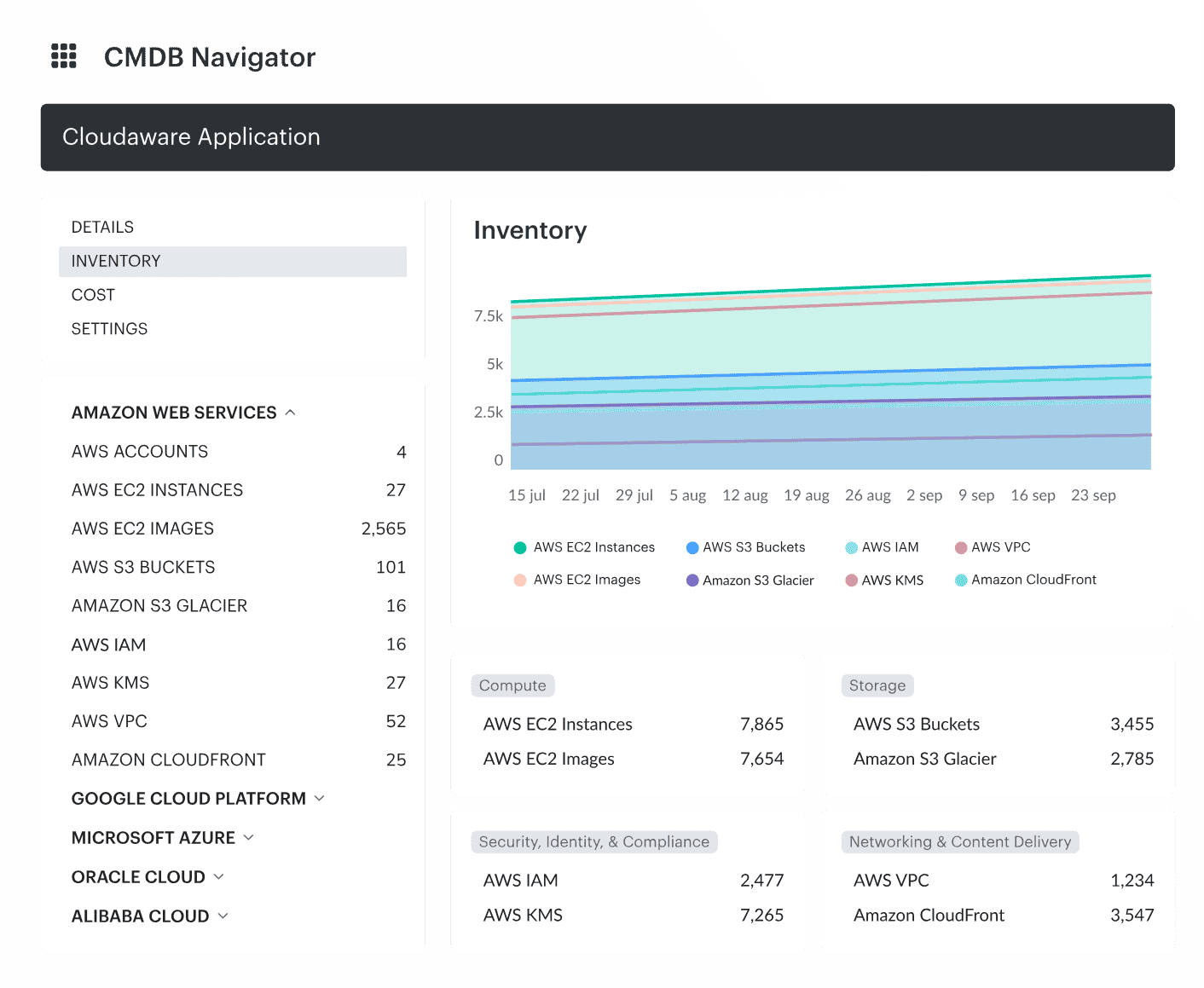
Once discovery runs, it’s not just raw data. Cloudaware auto-enriches your assets with change history, open tickets, vulnerabilities, related configs — and yes, tracking who touched what, when, and why. Tagging? Automated and manual. Grouping? Done — by service, team, function, you name it.
You can build out virtual apps, connect dependencies across your network, and turn chaos into clean, auditable maps. No more guessing during change reviews or security escalations.
Teams use it to:
- Discover all the IT assets in their hybrid setup
- Enrich them with data about related CIs
- Tag and group them automatically or manually
- Track change history
- Manage CIs compliance
- Identify vulnerabilities
- Detect intrusion
- Manage patches
- Streamline security audits and SLA-based maintenance
- Optimize cloud costs
- Control every aspect of their environment with custom dashboards and reports
Want to see how it fits into your stack? Start with a 30 days free trial — zero pressure. Or book a demo, and we’ll walk you through your exact use case. Whether it’s PCI scoping or service onboarding flow cleanup, we’ve got you. Hell, bring the weirdest asset mess you’ve got — we’ll untangle it together.
