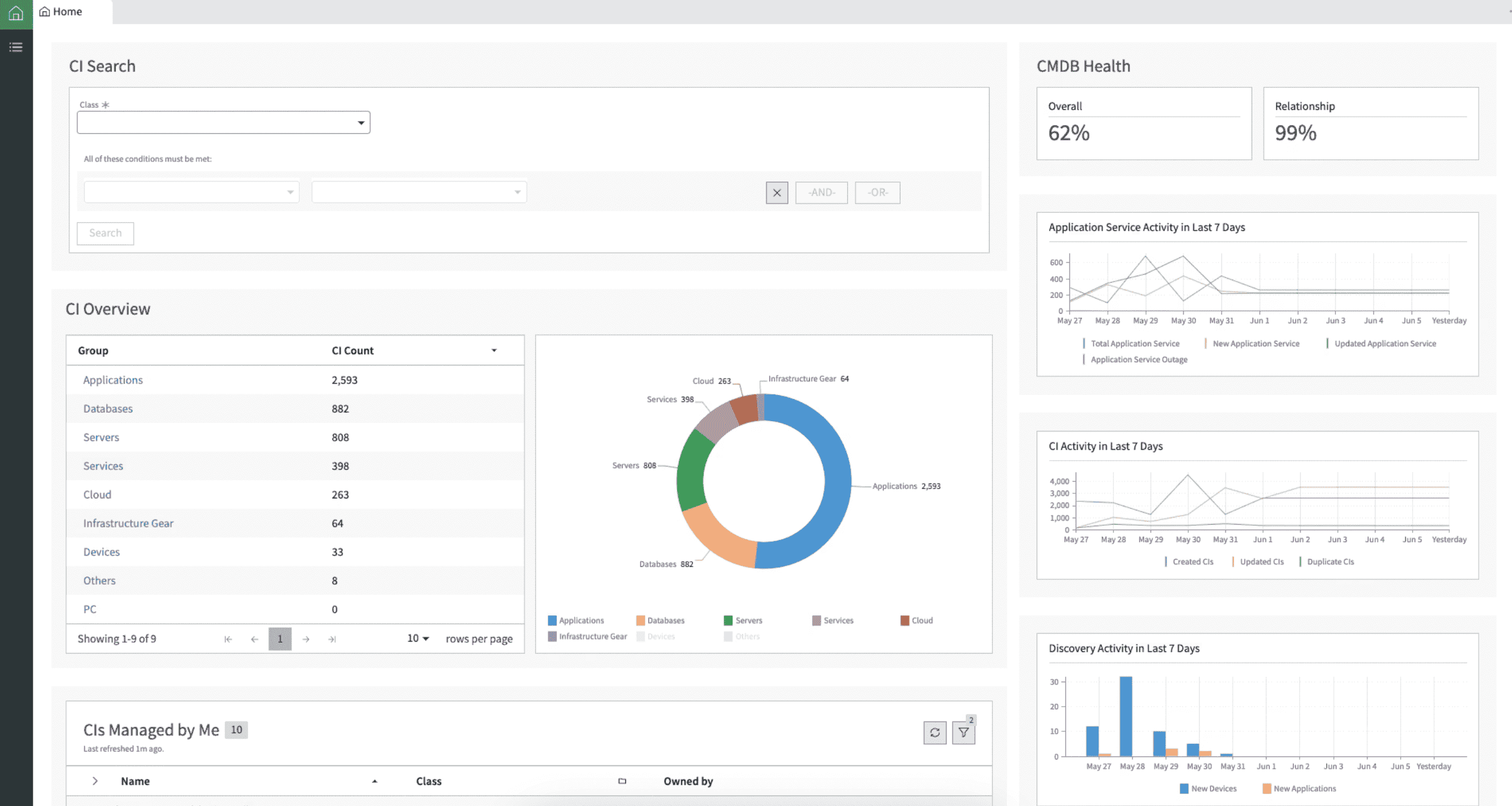
Cloud configuration management is the process of defining, enforcing, and maintaining consistent settings across multi-cloud and hybrid environments. When configurations drift, it leads to security risks, compliance gaps, and unexpected costs.
It combines principles of Infrastructure as Code (IaC), Cloud Security Posture Management (CSPM), and policy-as-code automation. Together, these practices ensure every resource configuration aligns with compliance baselines and cost-efficiency goals.
In this guide, Cloudaware ITAM experts share five real fixes that strengthen your configuration management process and help you regain visibility across AWS, Azure, Google Cloud, and on-premises resources to build a configuration management cloud strategy that scales.
What is cloud configuration management
Think of cloud configuration management as your cloud’s GPS. In essence, it’s the backbone of multi-cloud governance — preventing drift, reducing human error, and keeping every deployment compliant by design.
With strong configuration management in the cloud, you gain visibility, faster remediation, and cloud security.
Definition and core concept
In traditional IT, configuration management focused on servers and applications. In turn, configuration management in the cloud extends across dynamic, API-driven services that can be created or modified in seconds.
Cloud configuration management therefore means continuously discovering, tracking, and enforcing configuration states using automation and policy-as-code. It underpins both security and FinOps initiatives by ensuring that every resource, tag, and policy remains consistent with your baseline configuration.
Example of Cloud Configuration Management
At Cloudaware, we once helped an enterprise juggling AWS and Azure. Their dev team was struggling with out-of-sync configurations between their environments. One side had strict IAM policies, while the other was wide open — a glaring security risk.
We centralized their configurations. With Cloudaware’s platform, we:
- established a single source of truth for all their cloud resources,
- implemented automated monitoring to catch any drift
- synced their environments, aligning IAM roles, cluster configurations, and security policies across clouds.
The result? Their team spent less time firefighting and more time innovating. And they slept better knowing their cloud was no longer a ticking time bomb. Beyond cloud security, the company saw a 15% drop in cloud spend and achieved faster audit readiness thanks to real-time configuration visibility.
Read also: IT Asset Management Process: 6 Workflow Steps You Can’t Ignore!
Core components of a cloud configuration system
Cloud configuration management touches everything. Here are the key components it keeps in check:
- Virtual machines
- Storage buckets
- Kubernetes clusters
- IAM policies
- Security groups:
- Load balancers
Cloud CMDB: single source of configuration truth
Cloud CMDB, like Cloudaware, continuously discovers and catalogs every configuration item, from virtual machines, storage buckets, Kubernetes clusters, IAM policies, and more.
It maps relationships between assets, highlights dependencies, and detects configuration drift in real time.
Infrastructure as Code and Policy-as-Code
IaC templates tell you how to build infrastructure, and policy-as-code makes sure it stays compliant after it's been set up.
They work together to set up baseline configurations and make sure that tagging, security, and network standards are followed automatically.
When teams connect IaC pipelines to a CMDB, they can see the difference between what they wanted to happen and what actually happened. This is an important step for ongoing governance in multi-cloud environments.
CSPM and Continuous Misconfiguration Detection
A Cloud Security Posture Management (CSPM) layer checks changes to configurations against compliance frameworks like CIS and NIST.
It automatically marks violations like open ports, public buckets, and over-permissive IAM roles, and it puts fixes in order of risk.
CSPM, when used with Cloudaware's CMDB and FinOps analytics, lets teams see the full picture of how misconfigurations affect both security and costs.
Top 3 cloud configuration challenges (and the messes they create)
Over the past few months, working with IT teams across every cloud flavor, I’ve heard some wild stories. Here are three of the most chef’s kiss painful challenges I keep seeing with cloud configuration management — and the lovely messes they leave behind.
1. Visibility gaps in cloud configuration
A lead cloud architect from a fintech org swore their tagging policy was solid. They even had automated enforcement in Terraform modules. But things started going sideways when one region’s resources weren’t showing up in the dashboard.
Turned out, someone manually spun up resources during a fire drill, and since their Config Rule wasn’t set to remediate, just detect, they missed it until the bill came in.
Their AWS Config and Azure Policy setup couldn’t reconcile data between providers (a visibility gap only a centralized CMDB could close).
2. Shadow inventory and tagging inconsistencies
This came from a DevOps lead at a healthcare SaaS platform — HIPAA-bound, zero room for slip-ups. We were reviewing their asset inventory pipeline ahead of a CIS.
Benchmarks audit, and from the outside, things looked solid:
- EC2s deployed via Terraform, labeled and versioned
- GCE instances tracked through Google Cloud Config Controller
- CMDB fed by a combo of AWS Config, GCP Asset Inventory, and some custom scripts
Their shadow inventory had quietly grown outside of official channels. Tagging inconsistencies and untracked assets break more than dashboards — they break compliance.
3. Multi cloud misalignment and configuration drift
This story came from a cloud security architect juggling both AWS and Azure environments for a global logistics company. Their AWS side was pristine, but Azure? Well… that was handled by a different team.
When they finally looked across both clouds, they assumed their ARM templates were mirroring the AWS baselines. Except — they weren’t. Azure VMs were being spun up from an older image that hadn’t been patched in 3 months.
They only caught it because a SOC analyst flagged a traffic pattern anomaly. All because their CMDB couldn’t reconcile config definitions between providers.
Moral? With a consistent configuration management cloud approach, automation, and a unified CMDB, you can eliminate drift, strengthen compliance, and reclaim visibility.
5 reasons companies use multi cloud configuration management
Me: Mikhail, why are enterprises suddenly prioritizing multi cloud configuration management?
Mikhail: Honestly? Enterprises are running AWS, Azure, and GCP like they’re three separate planets. But the audit, the breach, the cost overrun? That hits everything. Configuration management cloud strategy is how they finally bring it all into orbit.
Security & compliance: Unified baselines reduce drift by up to 73%
Me: So what's the first “aha” moment that hits them?
Mikhail: Baseline enforcement. Every cloud has its own configuration tools but none of them talk to each other. Each tool enforces its own baseline configuration, but without a cross-cloud CSPM layer, configuration drift sneaks in.
One fintech client had “golden images” in AWS… and half-patched VMs in Azure. Once we built unified cloud configuration baselines into the CMDB, their drift incidents declined by 73% in just one quarter.
Operational reliability: Audit prep gets faster and less painful
Me: What’s the cost of not having this in place?
Mikhail: Time. Especially during audits.
Coca-Cola’s cloud ops team had AWS Config, Prisma Cloud, Azure Defender — plus a spreadsheet to fill the gaps. They were burning weeks reconciling configuration reports.
We pulled everything into Cloudaware’s CMDB, normalized the configuration management data, and boom — 60% faster PCI audit prep and zero critical findings!
Read also: Coca-Cola case study
Security posture & incident response: Real-time misconfiguration detection
Me: Is this mostly about compliance, or are there ops benefits too?
Mikhail: Oh, it’s way deeper than compliance. Let me give you NASA.
Their security team needed to flag publicly exposed S3 buckets, Azure Blobs, and GCP buckets — as they appeared. They were relying on scans that ran every 6–12 hours.
We built real-time cloud configuration management ingestion pipelines across clouds. These CSPM-driven pipelines continuously scan for drift and misconfiguration detection across all environments, enforcing baseline rules automatically.
Change control & CMDB visibility: Versioned config data enables root cause analysis
Me: What about cloud security incidents — how does config data help there?
Mikhail: Root cause analysis is where cloud configuration management snapshots shine.
A pharma client had a production breach — nothing major, but enough to trigger panic. Turned out, their CI pipeline had been inserting unapproved AMIs with exposed SSH ports. Nobody noticed until the logs got weird.
Because their configuration state was versioned and mapped to the CMDB, we could see exactly when that CI definition changed. We rolled back in 20 minutes. Without that? They’d still be guessing.
This kind of change control tied to a cloud CMDB creates an auditable trail for every change, timestamp, or user action.
FinOps impact: Automation only works when config is clean and normalized
Me: Let's talk automation. Does config management actually help there?
Mikhail: Only if you like automating the right things. Most teams automate chaos — like enforcing tag policies before they’ve even defined what “good” looks like across clouds. Clean, normalized data fuels FinOps automation and ensures that your configuration management cloud workflows drive real cost efficiency.
Once you’ve got unified configuration states feeding into your CMDB, then you can trigger real automations:
- Quarantine non-compliant VMs
- Auto-tag orphaned resources
- Flag workloads missing backup configs
And the real kicker? 54% of cloud misconfigs by 2026 will be from lack of visibility — not human error.
You don’t fix that with hope. You fix it with configuration management cloud workflows that actually know what’s going on.
5 real fixes for cloud configuration management (from ITAM pros)
Here are 5 life hacks for surviving configuration management in the cloud, straight from their client war stories, favorite discovery tools, and deeply earned wisdom.
💬 Fix 1. Normalize configuration data before automation
“Everyone’s excited about automation — but without normalized cloud configuration data across providers, you're basically wiring alarms to three different clocks and hoping they sync.
Normalization isn’t just a cleanup step. It’s the foundation of every cloud configuration management workflow, ensuring consistent data structures across AWS, Azure, and GCP.
We always run a normalization layer first — usually via Lambda, Azure Functions, or a lightweight ETL process — before ingestion. Saves everyone’s sanity downstream.”
Mikhail, CMDB expert at Cloudaware
💬 Fix 2. Treat configuration state like source code
“I had a client running golden AMIs for prod workloads in AWS. Everything was solid… until a junior engineer updated the launch template without approval. Drift wasn’t detected because there was no versioned config diff.
We built a pipeline that snapshots config state at every deploy, linked to CI pipeline stages, and backed it with Cloudaware’s CMDB for searchable deltas. This approach brings IaC principles directly into configuration management in the cloud, improving traceability and rollback confidence.
Result? Debugging time went from 4 hours to 15 minutes.”
Daria, ITAM expert at Cloudaware
💬 Fix 3. Tie every configuration to a lifecycle stage
“Map every CI to lifecycle metadata and snapshot its configuration management at major state changes. That’s what lets us say, ‘this rule mattered when it was running customer-facing workloads,’ and not just flag everything red.
Lifecycle-driven config state is how you avoid alert fatigue. Mapping configuration to lifecycle metadata strengthens baseline configuration control and reduces configuration drift across environments.”
Anna Maeva, Technical Account Manager at Cloudaware
💬 Fix 4. Don’t rely on native tools alone — unify multi-cloud visibility
“AWS, Azure, GCP — they all have decent config tools, but each one is looking through a keyhole. You won’t see the full room until you centralize.
True multi-cloud configuration visibility only happens when all providers feed into a unified cloud CMDB, giving you a single configuration truth across AWS, Azure, and GCP.”
Mikhail, CMDB expert at Cloudaware
💬 Fix 5. Make configuration data queryable (CMDB + APIs)
“We worked with a media company that had great intentions — they exported weekly config reports for audit... as PDFs.
We built them a config API layer inside the CMDB. Now their security team can run real-time queries. That shift? It turned cloud configuration from ‘compliance checkbox’ to actual operational intelligence.”
Daria, ITAM expert at Cloudaware
Read also: 9 Configuration Management Best Practices for Multi-Cloud Setups
Top tools for multi cloud configuration management
1. Cloudaware
Cloudaware is a CMDB tool designed for organizations navigating multi-cloud and hybrid environments. Cloudaware supports a broader range of resources than most competitors. It seamlessly integrates with AWS, Azure, Google Cloud, Oracle, and Alibaba, as well as on-prem environments, bridging the gap between cloud and legacy systems.
Our CMDB enriches your CIs with relevant data from clouds and third-party tools and tags them creating meaningful relationships between objects.
For example, take an EC2 instance. With Cloudaware, this instance can be enriched with metadata to provide a complete picture:
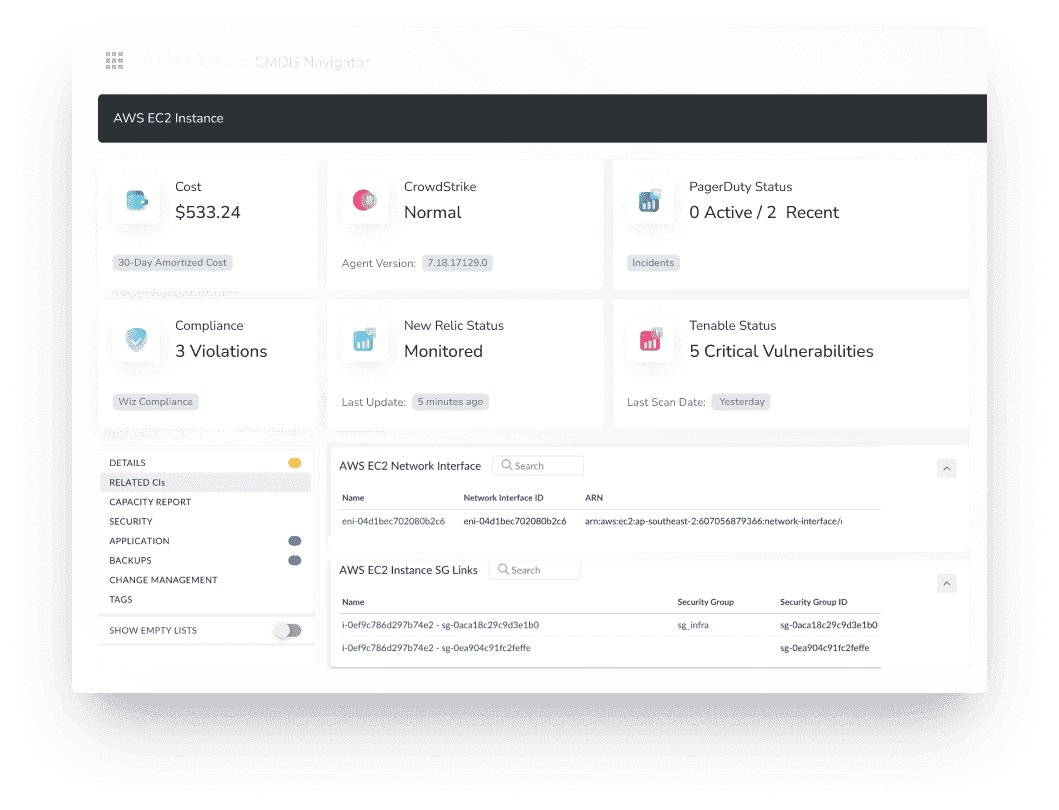
With Cloudaware, you can:
- Navigate and search with ease, filtering through hundreds of CIs in seconds.
- Manage tags across environments, making your data more organized and accessible.
- Implement Approval Workflows, ensuring that changes go through proper channels.
- Dive into analytics with visual dashboards and reports, turning raw data into actionable insights.
- Handle change management effortlessly by tracking configurations and ensuring consistency.
- Benefit from ready-made API integrations, easily connecting Cloudaware with your other tools.
Still not sure? Here is what Cloudaware users say about CMDB on G2:
✅ Pros
- "One of the standout features of Cloudaware is its ability to handle multiple cloud providers... enabling unified management across different environments."
- "Asset management, ease of integration, and endpoint cloud security."
- "User-Friendly Interface, its scalability, and its reporting capability."
❌ Cons
- "Integrating Cloudaware with existing systems or workflows was challenging for me, especially when I was in complex IT environments."
- "Cloudaware can be slow at times, and the user interface can be overwhelming and difficult to navigate."
2. ServiceNow CMDB
ServiceNow is a popular brand in the ITSM and CMDB space, known for centralizing and managing configuration items across diverse IT environments. It provides a comprehensive tools for tracking everything from server devices to security configurations.
Here is what its users say about the tool on review websites:
✅ ServiceNow Pros:
- "ServiceNow Now Platform is easy to use and saves time with automation. Also, it's very flexible, you can change it how you want for your work. Really helpful." - G2
- "Its versatility and designed to integrate smoothly.. it helps to track assets, manage licenses and ensure compliance." - G2
❌ Cons
- "Sometimes it is complex to configure or customize workspaces. Also the impact in upgrades to existent customizations." - G2
- "In large environments, there can be occasional performance lags when handling high volumes of data." - G2
3. BMC Helix CMDB
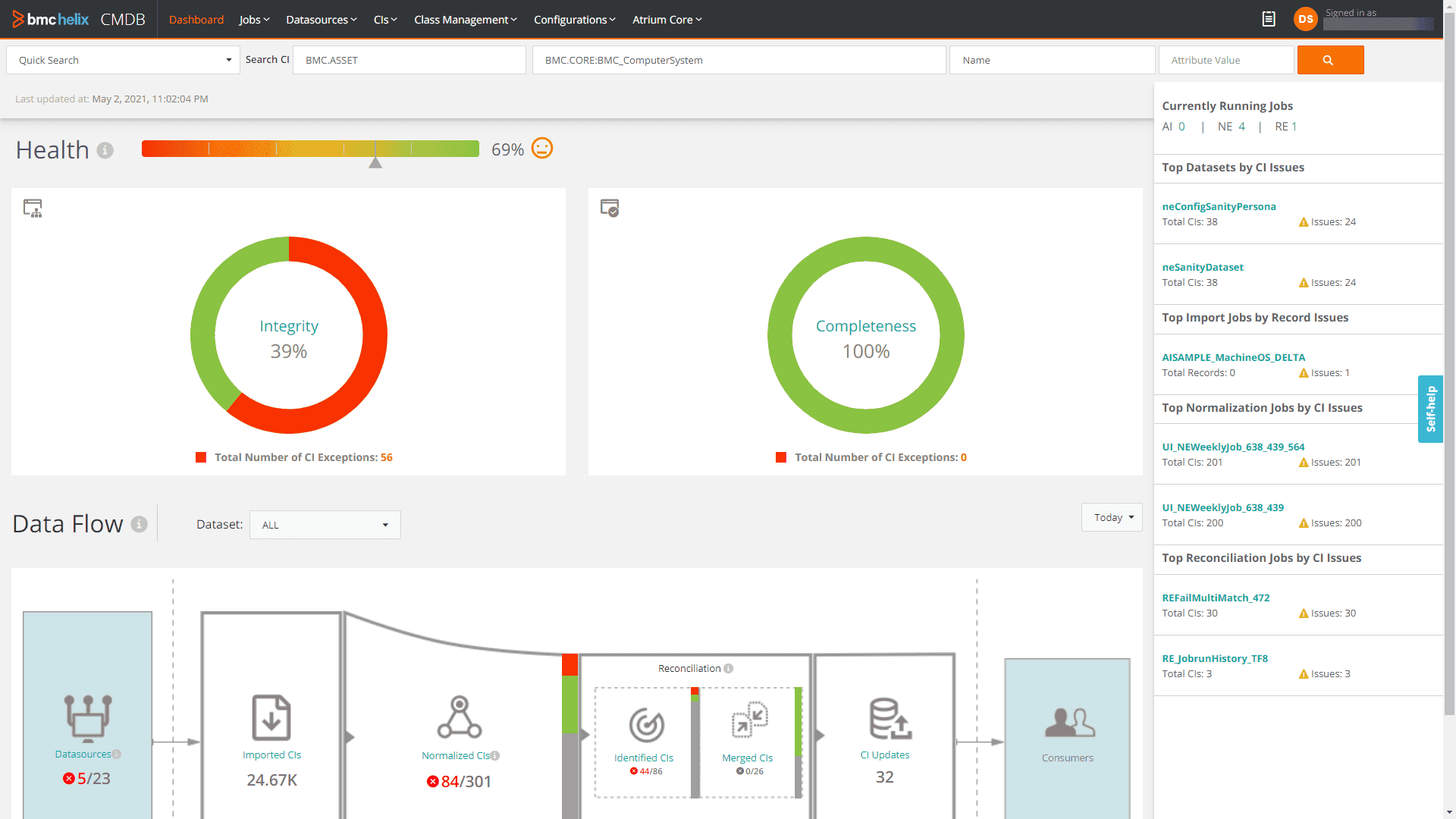
BMC Helix is another top contender. It offers powerful capabilities for organizations managing complex cloud and on-prem environments. It’s built to help businesses improve service delivery and align their configurations with business goals.
With a focus on AI-driven insights, BMC Helix’s CMDB goes beyond tracking assets. It helps you make smarter decisions based on real-time data.
Here is what BMC Helix users say about this CMDB solution on G2:
✅ Pros
- "BMC Helix Discovery is a cloud-native discovery and dependency mapping solution for visibility into hardware, software, and service dependencies across multi-cloud environments." - G2
- "A lightweight footprint allows IT to map applications with up to 100% accuracy in 15 minutes or less."
❌ Cons
- "Sometimes it is complex to configure or customize workspaces. Also the impact in upgrades to existent customizations."
- "In large environments, there can be occasional performance lags when handling high volumes of data."
Comparison of top CMDB tools for cloud configuration management
| Solution → Tool ↓ | Cloudaware | ServiceNow CMDB | BMC Helix CMDB |
|---|---|---|---|
| Multi-Cloud & Hybrid Support | ✅ | ✅ | ✅ |
| Real-Time Discovery | ✅ | ⚠️ | ⚠️ |
| Data Normalization & Tag Governance | ✅ | ⚠️ | ⚠️ |
| CSPM & Compliance Automation | ⚠️ | ⚠️ | ⚠️ |
| Integration with IaC & DevOps Pipelines | ✅ | ⚠️ | ⚠️ |
| FinOps & Cost Visibility | ✅ | ⚠️ | ❌ |
| Ease of Deployment & Scalability | ⚠️ | ⚠️ | ⚠️ |