Every time I join a new project, it’s the same story: unmanaged assets, compliance drift, and no one knows what’s in the environment until something breaks — or Finance calls.
This isn’t theory. It’s real-world cleanup after cleanup. Working with infra teams drowning in inconsistent tagging, broken discovery tools, and CMDBs that never reflect what’s actually out there.
We’ll walk through how to build a full-stack asset lifecycle. One that’s aligned with your CIS controls, integrated with provisioning workflows, and automated just enough to reduce ticket clutter.
All without handcuffing the devs or triggering another Slack war over ownership.
From Day One to Done isn’t fluff. It’s how Cloudaware ITAM experts stop treating IT asset lifecycle management like a graveyard and start turning it into a system that actually works.
But first, let’s check if we’re on the same page about basics 👇
What is an asset lifecycle?
An IT asset lifecycle is the end-to-end flow of an IT asset. From its initial request and provisioning, through its use, updates, audits, maintenance, and eventual retirement. It’s how you track the who, what, where, and why of every configuration item (CI) that enters your environment.
Sounds simple. But in a hybrid, multi-cloud setup, it rarely is.
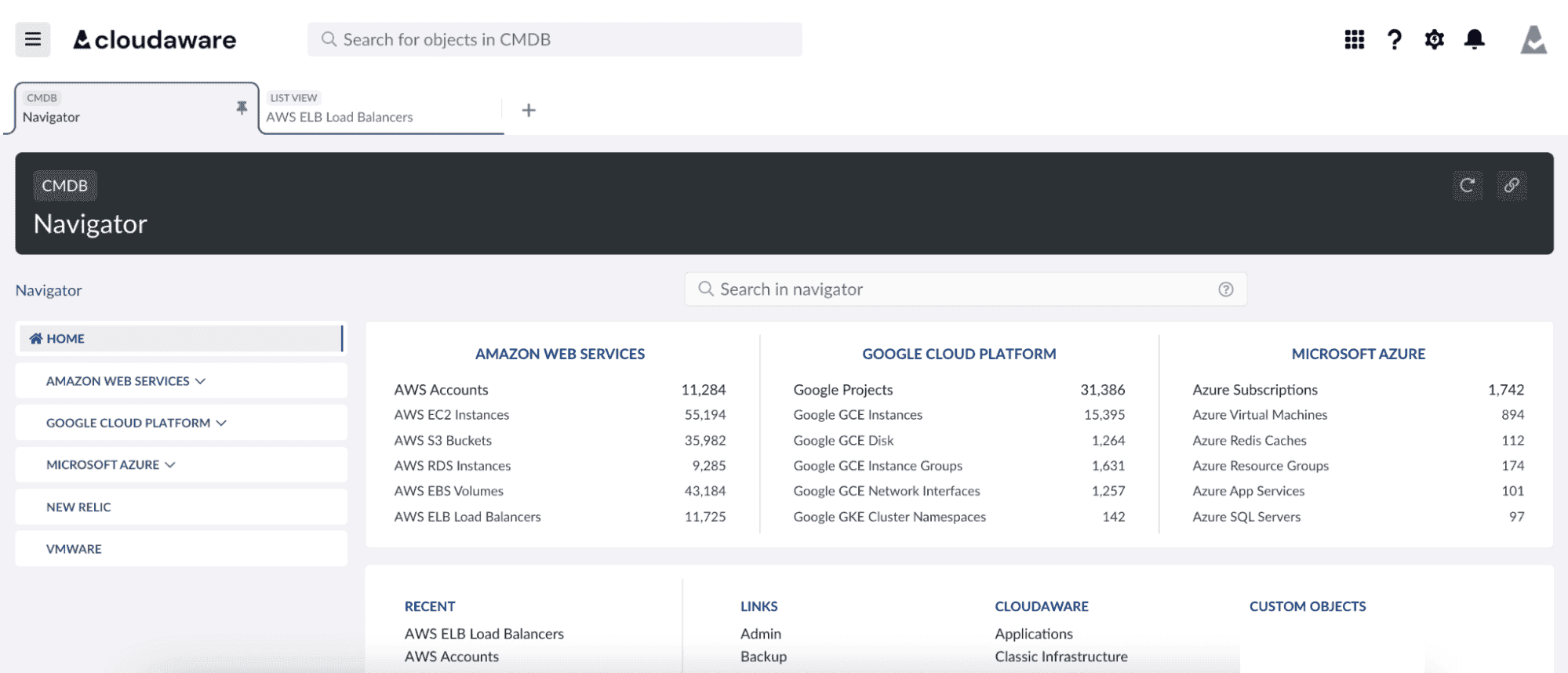
IT asset management lifecycle process example
Let’s say a dev team requests GPU-optimized VMs in GCP for a new ML workload. Someone provisions them manually. They get partial tags — project name, region, no owner. No one updates the CMDB because discovery is lagging again. The team also spins up blob storage in Azure to offload training data. Then adds an S3 bucket in AWS for some cross-region testing. Fast.
None of these assets are tied back to cost centers. No CIS policy enforcement is applied. The IT asset lifecycle management process is skipped entirely. The assets are running. But they’re invisible to audit, vulnerable to drift, and already non-compliant with Controls 1 and 2.
A few months in, the ML workload fails. The engineer who built it leaves. Nobody decommissions anything. IAM roles stay open. Storage costs climb. Shadow IT spreads.
Now you’ve got three clouds. Ten assets. Zero ownership. And a bunch of half-configured CIs floating outside your structured asset lifecycle.
And this is where the real issues stack up.
- Security has no idea what’s been exposed.
- Finance can’t trace the charges.
- Ops is blind to dependencies.
- Devs can’t move fast without triggering more chaos.
IT asset management is what keeps that from happening. It creates structure. It enforces accountability. It makes sure that every asset — whether it’s spun up through Terraform, CLI, or some rogue portal click — has a home, a purpose, and an exit plan.
For organizations, real IT asset lifecycle management means building repeatable, scalable, and automated processes. And that’s exactly what this guide will unpack. How to bring clarity to your asset management stack and close the gaps in your IT asset management lifecycle.
5 reasons to manage asset lifecycle in 2025
I can talk half an hour about the benefits of managing asset lifecycle. But I know you have limited time, so here are the major advantages companies enjoy:
Visibility that doesn’t lie
Before Cloudaware, a major U.S. federal agency (yeah, that one — NASA) was running blind across dozens of AWS accounts. Their CMDB was incomplete, CI sprawl was real, and the infrastructure team was wasting hours chasing asset data across disconnected tools.
Once we got asset lifecycle tracking in place — discovery feeding into the CMDB, lifecycle status normalized, ownership mapped — they had complete coverage across every CI in every region. That wasn’t just visibility. That was confidence.
87% of organizations say poor asset visibility increases security risk (IDC). A structured IT asset management lifecycle makes sure that every CI has a name, a purpose, and a plan.
Smarter decision-making, backed by data
Charles Schwab was drowning in request tickets and rogue cloud deployments. No one had a real view into how assets were being provisioned — or decommissioned. Cloudaware gave them a single pane of truth that tied software licenses, cloud spend, and asset health into one place.
With full-stack visibility across the software asset management lifecycle, they started optimizing usage, reclaiming underused resources, and flagging assets with no business owner. Suddenly, decisions were driven by facts — not assumptions.
It’s not just cost savings. It’s reducing attack surface, tightening compliance, and aligning infra to business goals.
Read also: IT Asset Management Process: 6 Workflow Steps You Can’t Ignore!
Compliance that doesn’t break things
ServiceChannel needed to pass audits with their head held high — and with infrastructure moving faster than most compliance teams could follow. They used Cloudaware to bake management checkpoints into workflows: patching, access reviews, license renewals, and decommissioning.
Elements of the Cloudaware compliance report
That meant every asset aligned with CIS Controls 1, 2, and 4, automatically. No manual chasing. No last-minute panic. Just policies that actually worked because lifecycle stages were enforced in real time.
And it’s not just them. Gartner found that organizations with automated asset lifecycle management reduce audit failures by 70%. That’s not a stat — that’s a lifeline.
Cloud spend that finally makes sense
Coca-Cola had assets across AWS and Azure — lots of them. And tagging? Inconsistent. Ownership? Undefined. Lifecycle states? Missing in action. Cloudaware’s CMDB pulled everything into a single structure, mapped dependencies, tracked lifecycle states, and tied assets to cost centers.
That gave them clean cost visibility, proactive rightsizing, and clear accountability when bills came in. They didn’t just reduce spend — they understood where it was coming from and how to control it.
Because let’s face it: you can’t optimize what you can’t see. And you can’t defend what you don’t own.
Ops without the guesswork
When maintenance data flows into every part of the tool chain — monitoring, provisioning, compliance, cost — you stop firefighting. You start building.
Every ticket becomes traceable. Every CI becomes contextual. Every service gets tied to a business purpose. That’s what asset management is supposed to do.
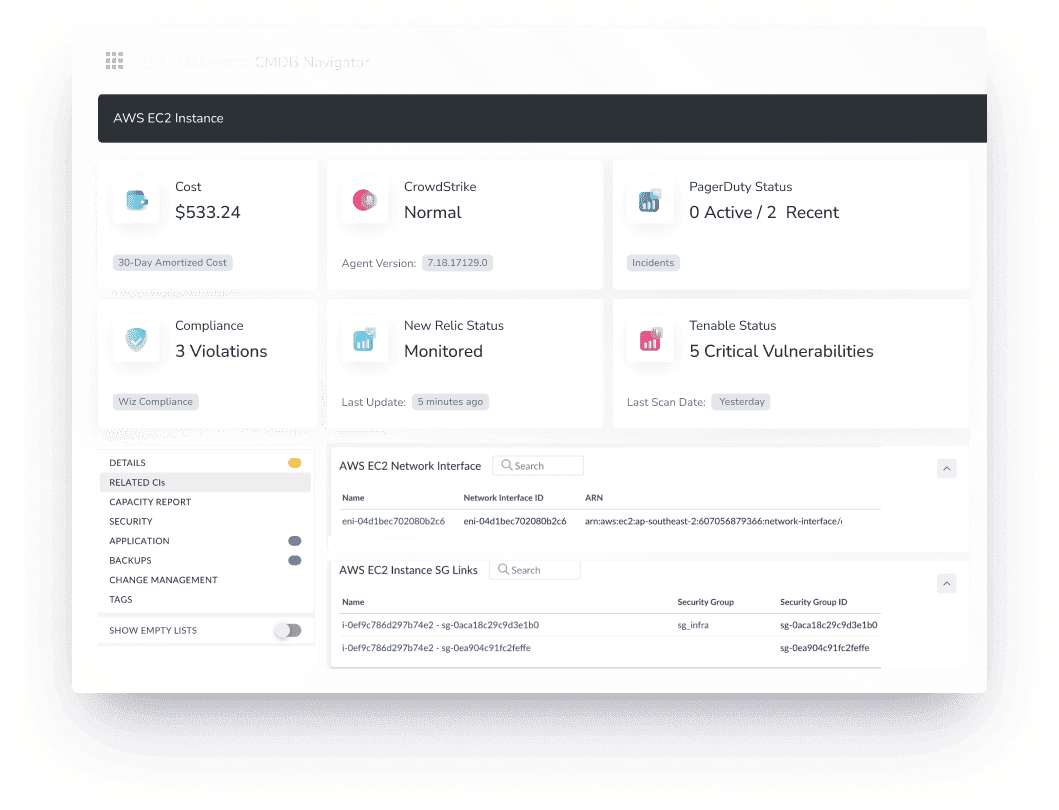
And when it’s done right? You don’t need twenty tools and a tribal memory to figure out what’s in your environment. You’ve got it all, live, in one place.
Ready to break down what the IT asset management lifecycle actually looks like in practice? Let’s walk through every stage — what happens, what breaks, and how to keep the chaos in check.
Read also: IT Asset Management Audit For Hybrid Setup: 9-Steps Checklist
6 phases of IT asset management lifecycle
You ever look at an asset and think: Who even spun this up?
Same.
I’ve seen far too many environments where infra gets deployed fast, but tracking? Ownership? Cleanup? That’s a mystery left to future-you or audit season. And honestly, that’s when the cost, risk, and compliance debt starts stacking.
The thing is, most teams do have lifecycle processes… just not end-to-end. Not enforced. Not visible. What I’ve learned at Cloudaware is this: when the IT asset management lifecycle phases are tight, everything else gets easier — CMDB accuracy, FinOps, security controls, even onboarding new teams.
Here’s how I break down the IT asset management lifecycle in the real world. Not as theory, but as an actual operational rhythm that keeps assets clean, owned, and traceable from day one to done.
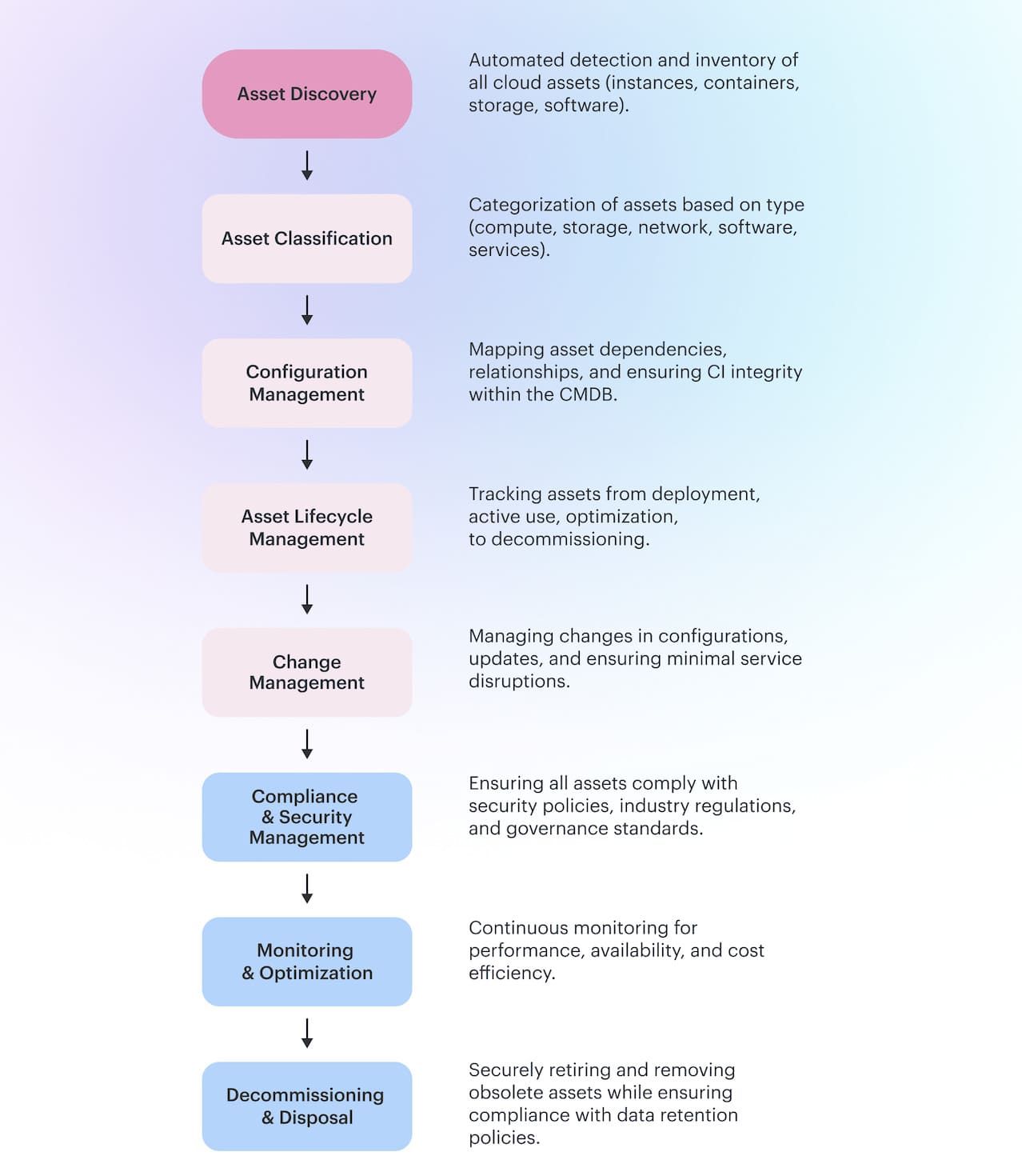
IT asset management lifecycle phases
1. Request & approval
It starts before anything exists. Someone needs a thing — a VM, a container, a license, a SaaS tool. Ideally, that request comes through a service catalog or IaC pipeline tied to approvals. No Slack messages, no backdoor clicks in a cloud console.
This is where you capture intent: why this asset is needed, who owns it, what it’s tied to. In Cloudaware, we sync this with metadata and track it straight into the CMDB. If this step’s sloppy, you lose the thread before the story even starts.
Asset management begins before anything is deployed.
2. Procurement & provisioning
Next comes the spin-up. Whether it’s an EC2 via Terraform, an EKS cluster, or a bulk SaaS license order — it gets provisioned. This is where your tagging policies, naming conventions, and initial relationships kick in.
This is also where most organizations trip. If tags aren’t auto-applied or normalized, discovery tools won’t catch it cleanly. In Cloudaware, we pipe everything through discovery and normalize titles on the fly. It’s also the best place to kick off CIS Control 1 — inventory of authorized devices.
You’re building the foundation for good management.
3. Onboarding to CMDB
Now the asset lives. And it better land in the CMDB. This means identifying the CI type, assigning ownership, mapping dependencies, and linking it to business services or cost centers.
If it’s not in the CMDB — or worse, duplicated — it’s already out of scope. This is where asset lifecycle management needs strong normalization rules and automation. And where CIS Control 2 — authorized software — gets activated.
This is one of the most critical lifecycle handoffs. Miss it, and the rest falls apart.
4. Usage & operations
The asset’s now in active use. Deployed, connected, doing its job. This is where monitoring, security, patching, backup routines, access reviews, and cost tracking come into play.
Every one of those touches the asset lifecycle. If your ops team isn’t feeding alerts or status back into the CMDB, you lose visibility. And when the lifecycle is blind, so are your audits.
Think CIS Controls 3–6: secure configurations, privilege controls, log management, and system maintenance.
5. Maintenance & optimization
Now we get into ongoing care. Patching schedules. Usage analysis. Reassigning licenses. Rightsizing cloud resources.
In Cloudaware, we use policy-based automation to flag underused assets, out-of-policy configs, and lifecycle misalignment. This is where smart teams reclaim spend and tighten up drift — without micromanaging every CI.
This is one of the most overlooked IT asset management lifecycle stages — and one of the most valuable.
Read also: Top 10 IT asset discovery tools: software features & pricing
6. Offboarding & decommissioning
Last phase. The goodbye. The asset is no longer needed — it’s terminated, archived, or reallocated.
Most orgs forget this step. Which is how you end up with S3 buckets still live, IAM roles open, SaaS users with access months after they’ve left. That’s not just bad hygiene — it’s a breach waiting to happen.
Lifecycle-based offboarding should trigger workflows: revoke access, delete resource, update CMDB, close ownership loop. Bonus points if it’s timestamped and traceable for audits.
Because real lifecycle management means you know how every story ends.
When all six IT asset management lifecycle stages are dialed in, your lifecycle doesn’t just protect your infra — it powers it. Let’s walk through the guardrails that keep every phase consistent, clean, and actually followed.
Asset lifecycle policy should include
Me: Alright, let’s get straight to it. For teams managing thousands of assets across hybrid environments, what should an asset lifecycle policy actually include?
Anna: First off, if your IT asset lifecycle management policy only lives in a PDF or a wiki, it’s already too weak. The policy has to guide behavior. It should drive automation, enforce accountability, and sync across your entire tool chain.
At minimum, it should define:
- Lifecycle phases and transitions
- Ownership and accountability
- Mandatory metadata and classification
- Tooling and integration points
- Automation rules
- Compliance checkpoints (hello CIS Controls)
- Offboarding and retirement process
This isn’t about theory — it’s how organizations prevent chaos from creeping into their asset management practice.
Me: Let’s break that down. What do you mean by lifecycle phases?
Anna: I’m talking about clearly documented ITIL asset management lifecycle stages — from request to retirement. The core phases are:
- Request & Approval
- Procurement & Provisioning
- Onboarding to CMDB
- Operations & Monitoring
- Maintenance & Optimization
- Offboarding & Decommissioning
Each one needs a handoff mechanism. If you can’t trigger lifecycle transitions automatically, your asset just floats in “Active” status forever. That’s where audit gaps and shadow spend hide.
Me: And what about ownership? Who’s actually responsible?
Anna: Ownership is non-negotiable. A good lifecycle management policy defines both the technical owner (who manages the CI) and the business owner (who’s accountable for the cost, access, and risk).
If your asset lifecycle doesn’t have names and escalation paths attached to every phase, you’re basically crowdsourcing responsibility — which never ends well.
Me: Okay, let’s talk metadata. Is it just tags?
Anna: Tags are the bare minimum. The IT asset management lifecycle runs on data. Your policy should define required metadata for each CI type. That includes:
- Business service mapping
- Environment classification
- Owner fields (not just an email alias)
- Lifecycle status
- Cost center
- Source (provisioning method)
All of that should sync cleanly across systems — IaC, ticketing, CMDB, discovery. If the data’s misaligned, asset lifecycle management grinds to a halt.
Me: What kind of automation should be in the policy?
Anna: If your policy doesn’t trigger action, it’s just wallpaper. Every phase should come with automation rules:
- Auto-expire unused assets
- Flag stale lifecycle states
- Create tickets for patching or reapproval
- Reassign ownership if someone leaves
- Notify finance when usage spikes
In Cloudaware, we use lifecycle-based rules to tie provisioning, CMDB, and compliance together. It keeps management workflows lean and predictable.
Me: How do you connect this to CIS Controls?
Anna: This is where the magic happens. Your IT asset lifecycle management policy should map to:
- Control 1: Hardware inventory
- Control 2: Software inventory
- Control 4: Vulnerability management
- Control 6: Access control
- Control 11: Data recovery
Lifecycle checkpoints are the glue. If your CMDB reflects the real-time lifecycle state of every asset, audit prep becomes a process — not a panic. And the policy becomes your safety net.
Me: Final thoughts?
Anna: Your policy isn’t just documentation. It’s alignment between tech, process, and people. When done right, it becomes the quiet engine behind clean infra, predictable costs, and lower risk.
And trust me — if you’re managing at scale, you need that kind of calm.
Want to walk through how to write one next? Because I’ve got a field-tested checklist that gets adopted, not ignored.
The dark side of the software asset management lifecycle
Let’s be honest — software asset management is where everything that’s “someone else’s problem” goes to hide. Especially when the stack spans multiple clouds, CI pipelines shift weekly, and no one really owns the full lifecycle.
Here are three situations which together with Cloudaware clients lived through — messy, real, and way too common.
1. The surprise audit that wrecked a sprint
One client had a mix of on-prem workloads, cloud VMs, and containers running in ECS and AKS. Java was used across multiple services — some updated, some legacy, some embedded in Docker images no one had touched in a year.
They got hit with an Oracle audit. The infra team was convinced everything was fine. Turned out, four services were still running outdated Java SE on bare metal nodes. No patches. No license tracking. The CMDB didn’t know those servers existed because discovery was scoped to cloud.
Finance had no purchase records. Security hadn’t flagged it because the agents were missing. The org spent two weeks trying to backtrack entitlements and explain how those builds got into prod. It all unraveled because the software asset lifecycle had no clear enforcement or visibility across environments.
2. Marketplace madness and unused licenses
At another org, a dev team purchased an ML modeling platform through the AWS Marketplace. It was spun up quickly for a proof-of-concept. Great tool. But no one linked the license to a cost center. No ownership was assigned.
After the PoC was abandoned, the software kept running. Eight months later, it was still live — incurring charges and holding IAM permissions that granted access to S3 buckets storing client data.
There were no offboarding workflows, no alerting, and the CMDB didn’t track marketplace assets. The tool was invisible to governance processes. A perfect storm: cost leakage, potential compliance risk (hello CIS Control 4 and 6), and zero accountability. All because that IT asset lifecycle management flow didn’t cover cloud marketplaces.
Read also: Everything You Must Know About ITIL Asset Management in 2025
3. SaaS sprawl in plain sight
In a fast-scaling org, every team picked their own tools. Marketing had Figma. Design had another Figma account. Product had Notion. Engineering had Notion. Finance had no idea.
When the CFO tried to cut costs, they found six duplicate SaaS subscriptions — some still billed monthly, some yearly, none linked to users. Deprovisioning was a nightmare. Offboarding didn’t catch SaaS tools because the identity lifecycle wasn’t integrated.
And discovery? It didn’t even touch SaaS. So these assets never made it into the CMDB, never went through the IT asset management life cycle, and never hit any compliance checkpoint. Shadow IT wasn’t even in the shadows — it was sitting right there, live, and still pulling spend.
If this sounds familiar, it’s because most organizations don’t have real structure around software. The lifecycle exists — tools are spun up, used, and abandoned — but it’s unmanaged, untracked, and often invisible.
Now that we’ve aired out the mess, let’s talk solutions. Real ones. Not more spreadsheets or disconnected tools pretending to be a strategy 👇
4 IT asset lifecycle management best practices
Below you’ll find secret insights from the experience of my teammates - ITAM experts, and Cloudaware clients: companies with multi-cloud hybrid infrastructure like Coca Cola or Nasa.
1️⃣ Provisioning is easy. Normalization is the battle
This is the direct quote of our client after a brutal week he spent syncing data from AWS, Azure, and CMDB. Discovery was easy, the issue was garbage that came in.
Together with Anna - Cloudaware ITAM expert, they built a normalization layer that runs every discovered CI through title cleaning, type classification, and deduplication logic. That means:
- collapsing identical compute instances created under different naming patterns,
- resolving SaaS titles from multiple sources (API, agent, SSO),
- and enforcing service-to-asset mapping before anything touches the CMDB.
Here is Anna advice:
“If you skip building a normalization layer, your CMDB turns onto a pile of partial truths. One of the main IT asset lifecycle management best practices is a normalized clean data. Otherwise, your asset lifecycle logic will break before a start. Normalization is a foundation of any ITIL asset management lifecycle model I’ve seen succeed at scale.”
2️⃣ The CMDB should reflect real-time usage, not just existence
Daria, my peer working with Cloudaware clients focused on FinOps pushed this hard:
“Track asset based on operational signals, not the fact of their existence. See cost delta in 30+ days? No active sessions? No inbound traffic? That means your asset is drifted.
My advice is to tie lifecycle states to usage signals within cost analytics, monitoring, and identity activity. Let’s say, a GCP VM that hasn’t had traffic in two months gets moved into a "Review for Decommission" state. No questions.
*Visibility tied to relevance lies at the core of any IT asset life cycle management process. From my experience, organizations don’t need more data. They need better signals inside lifecycle management logic.*”
Read also: Top 10 benefits of IT asset management in 2025
3️⃣ Manage offboarding as an incident response scenario
That’s insight from Mikhail, CMDB expert at Cloudaware. He works with clients focused on security aspects of ITAM.
“Treat missing offboarding as a security event, not an ops gap. You risk a lot by leaving a terminated user access to a SaaS asset or cloud role.
_The fix? Built auto-remediation flows triggered by asset lifecycle states. Thus, when an asset is marked as “Retired,” IAM roles are revoked, attached volumes are wiped, and the CMDB logs the full removal sequence with timestamps and user IDs._”
A strong IT asset management framework prevents exposure at the end of the maintenance window. On top of this, it enforces your IT asset lifecycle management policy at the most neglected phase.
4️⃣ Log every lifecycle transition like a change event
And this is insight from my personal experience:
Governance lead’s rule: every state change — provisioned, in use, deprecated, retired — gets logged with full context. That includes the triggering system (Terraform, Jenkins, ServiceNow), the actor (manual or automated), and the delta in CMDB attributes.
Why? Because asset management isn’t real unless it’s traceable. If an auditor — or your own CISO — asks who decommissioned a high-privilege CI and why, you should have the story in two clicks.
That level of traceability is at the heart of modern asset lifecycle management. And for management to scale, it has to be baked into your tooling — not left to tribal memory or spreadsheet audits.
These aren’t hypothetical ideas — they’re IT asset lifecycle management best practices built for complex, multi-cloud environments. We’ve tested them, tuned them, and watched them save teams from total lifecycle collapse. Every single one is how we keep asset management sharp with Cloudaware CMDB 👇
Automate your lifecycle asset management with Cloudaware software
Tired of tools that throttle your visibility, miss half your assets, or fall apart under hybrid complexity? Cloudaware is built for full-speed, full-spectrum IT asset lifecycle management — no throttling, no vendor lock-in.
With 200+ integrations (including AWS, Azure, GCP, VMware, Alibaba, and on-prem), high-security standards, and policy-driven automation at its core, it gives organizations total control over their CMDB, lifecycle states, workflows, and compliance posture. Whether you're managing the ITIL asset management lifecycle, the software asset management lifecycle, or a hybrid stack that does it all — Cloudaware supports every phase, end to end.
This isn’t just another dashboard — it’s your ops command center.
✅ Real-time automated discovery across your full ITAM lifecycle
✅ A live CMDB with asset lifecycle states, clean metadata, and ownership trails
✅ Tagging and normalization enforcement that actually sticks
✅ Lifecycle-based automation — notifications, cleanup, and offboarding flows
✅ Out-of-the-box CIS compliance alignment (Controls 1, 2, 4, and 6)
✅ Full cost visibility tied to business services and environments
✅ Audit logs that tell the whole asset life story, from request to retirement
✅ Asset management workflows across clouds and teams
✅ Built-in support for proactive maintenance, patching, and policy tracking
Whether you’re trying to get control over thousands of CIs or just want your CMDB to finally reflect the truth — Cloudaware can help.
Let’s make lifecycle management something your team doesn’t have to fight with. From provisioning to decommissioning, Cloudaware simplifies IT asset management at scale.
