You ever open your CMDB, scroll through a hundred “unknown” CIs, and think: who greenlit this disaster? Meanwhile, infra keeps spinning like nobody's watching — dynamic scaling, ephemeral workloads, new GitOps pipelines popping up faster than you can say “compliance drift.”
As an ITAM expert I’ve been the one digging through Terraform state files, tracing down EC2 instances with zero tags, praying that asset isn’t part of a critical workload. I’ve sat through asset review meetings where even the cloud security team’s unsure who owns what.
And the lifecycle status? 🤷
Let’s get this straight: IT portfolio ≠ project portfolio. This isn’t about budgets and Gantt charts anymore. It’s about knowing what exists, why it exists, and whether it’s in the right state right now.
This guide is for the ops minds like yours — the ones who keep cloud inventory just stable enough for auditors and still sleep at night. We'll dig into real multi-cloud IT portfolio management: how to build visibility across snowballing infrastructure, tie lifecycle events to real processes, and actually make your CMDB useful.
Let’s fix the mess, one CI at a time.
But first, ensure, that we’re on the same page about the basics👇
IT portfolio management definition
IT Portfolio Management (ITPM) is the discipline of tracking, governing, and optimizing everything in your tech ecosystem — cloud, on-prem, containers, functions, VMs, SaaS, shadow IT, and the weird stuff no one admits exists.
It’s not just about what you deployed, but what’s still alive, who owns it, how it's behaving, and what lifecycle stage it’s in.
I’m talking about EC2s, GKE clusters, EBS volumes no one's touched in 8 months, Azure VNets with broken NSGs, orphaned S3 buckets with public access still turned on. It’s all part of the portfolio now.
And managing that? That’s the real job.
You’re not just a cloud architect. You’re the air traffic controller of dynamic, distributed, high-speed infrastructure. And unless you’ve got a system that tells you what’s live, who owns it, where it came from, and when it needs to go, you’re basically running blind.
That’s where real IT portfolio management kicks in. Not in the PMO. Right here, in your CI lifecycle chaos.
Now let me show you what this looks like done right.
What an IT Portfolio process Really Looks Like
Managing an IT portfolio isn’t just about tracking assets — it’s about understanding how every piece of tech supports your business. That means knowing what you own, where it runs, how it’s configured, and who’s responsible for it.
One of our clients was struggling with exactly that. With services spread across AWS, Azure, and GCP — and a mix of Terraform, manual provisioning, and custom pipelines — their CMDB was chaotic. Disconnected data made it impossible to get a clear view of applications, costs, or ownership.
So, they hooked Cloudaware CMDB into their discovery stack. Now it pulls from native APIs, Terraform state files, and even custom-built tools.
The result? CI records aren’t just dumped into the CMDB — they’re enriched. With real metadata. Tags. Environment. Cost center. Owner. Even relationships to parent services and downstream dependencies.
When someone spins up a GCP instance with no label? Cloudaware flags it. When that EKS node group gets decommissioned but the CI is still marked “active”? Lifecycle automation kicks in and corrects it. No ticket. No human bottleneck.
You’ve got retention policies wired into status transitions. You’ve got business services mapped down to the pod level. And compliance teams can run audits straight from live data — not month-old exports that miss half the ephemeral infra.
That’s not theory. That’s a working, breathing, IT cloud portfolio.
But Here’s the Thing...
Most people are still managing projects. Not portfolios.
That’s the disconnect.
It’s the difference between planning delivery timelines and managing the full lifecycle of infrastructure. Between looking at business initiatives and looking at real-time asset sprawl.
Project portfolio management was built for strategic alignment of business goals, resources, and timelines.
But IT portfolio management?
That’s built for organizations running fast, hybrid, and cloud-native. Where data flows across accounts, and resources — compute, storage, security controls — change state by the minute.
This isn’t about deliverables anymore. It’s about portfolio management that reflects what’s actually running inside your infrastructure. And that requires automation, continuous discovery, and full-stack visibility.
If your company still sees IT portfolio management as a planning exercise, it’s time for a serious alignment check.
How does ITPM differ from project portfolio management?
They both talk about portfolios. They both talk about alignment. And they both have the word management hanging off them like a badge of structure.
But here’s the real tea:
| 👉 Project Portfolio Management (PPM) is about managing investments in active projects. Think budgets, timelines, resource allocation, stakeholder reporting. It’s what the PMO lives in. | 👉 IT Portfolio Management (ITPM), is about governing everything that already exists in production — your infrastructure, applications, services, tools, licenses, cloud spend, compliance risk, you name it. |
|---|
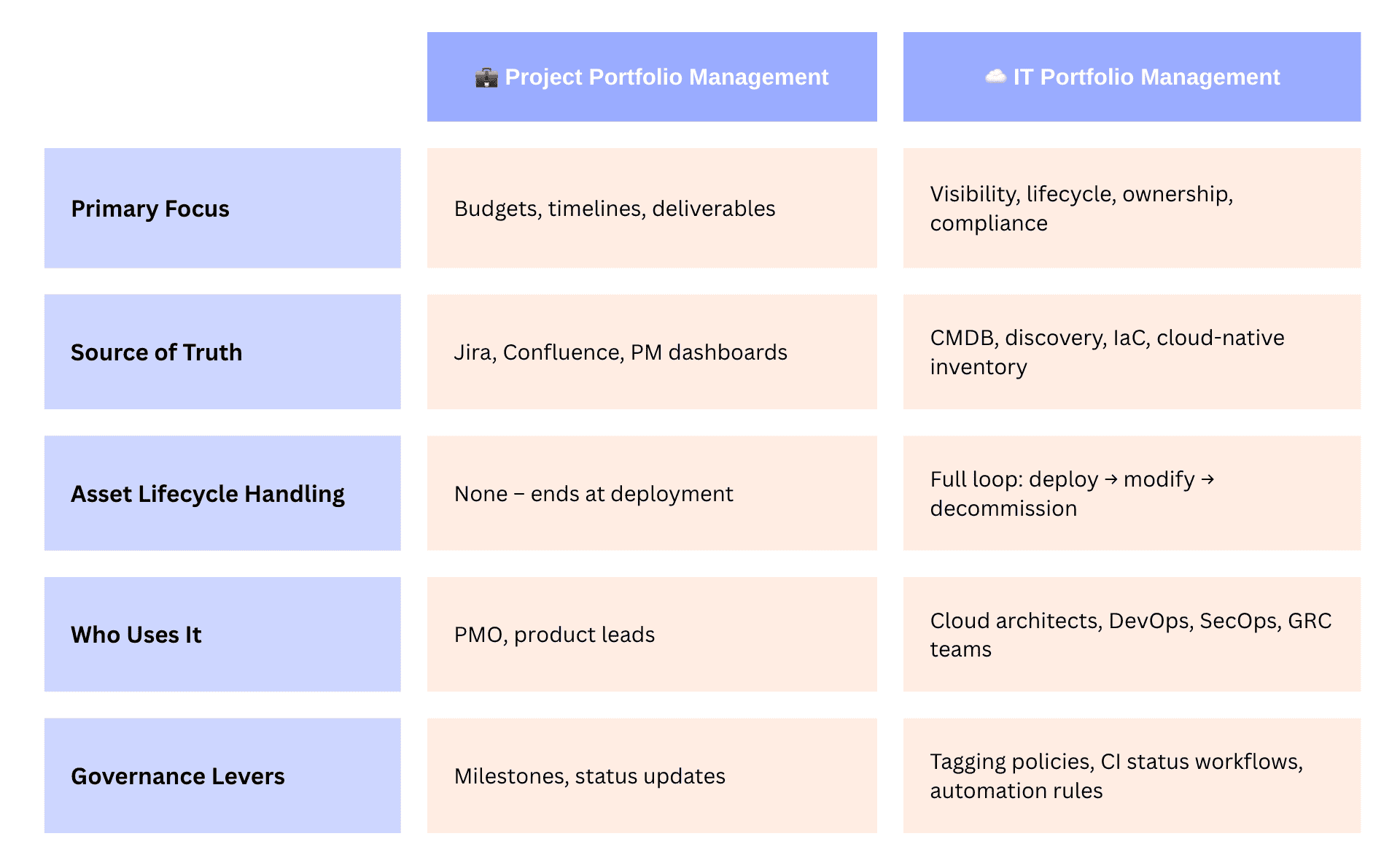
In IT Portfolio Management case, you’re answering: “What’s running? Who owns it? Why is it here? Is it still needed? Is it secure? What’s it costing us?”
See the difference?
PPM is about change.
ITPM is about control.
PPM stops when the project ships. ITPM begins the moment something gets deployed — and it sticks with it until that CI retires.
In practice, though? These two have to talk. Because if your CMDB and your project portfolio aren’t aligned, you end up with deployed infra no one tracks, projects no one maintains, and business services no one owns.
So if you’re knee-deep in lifecycles, tag policies, asset reviews, or orphaned EC2s… you’re living in the ITPM world.
And trust me — you want that portfolio mapped before someone asks, “*Why are we still paying $2K for this thing no one’s touched since 2021?*”
Why IT portfolio management isn’t just for the PMO crowd anymore
You and I both know portfolio management used to be a PMO thing. Deadlines. Budgets. Executive status updates. But now? It’s showing up in our world — in the middle of broken tagging standards, flaky CMDB syncs, and that eternal question: “What the hell is this running in us-east-1?”
That’s because IT portfolio management (ITPM) has quietly become one of the most powerful tools in our toolkit. Not theoretical. Not high-level. I mean daily-use, ops-critical.
Let me show you how it plays out.
1. Visibility that’s not just visual
We’re talking real visibility. You run a Cloudaware-discovery job and within minutes, your CMDB has new CIs mapped to business services, environments, owners, and even the provisioning source — whether that’s Terraform or a rogue UI deploy.
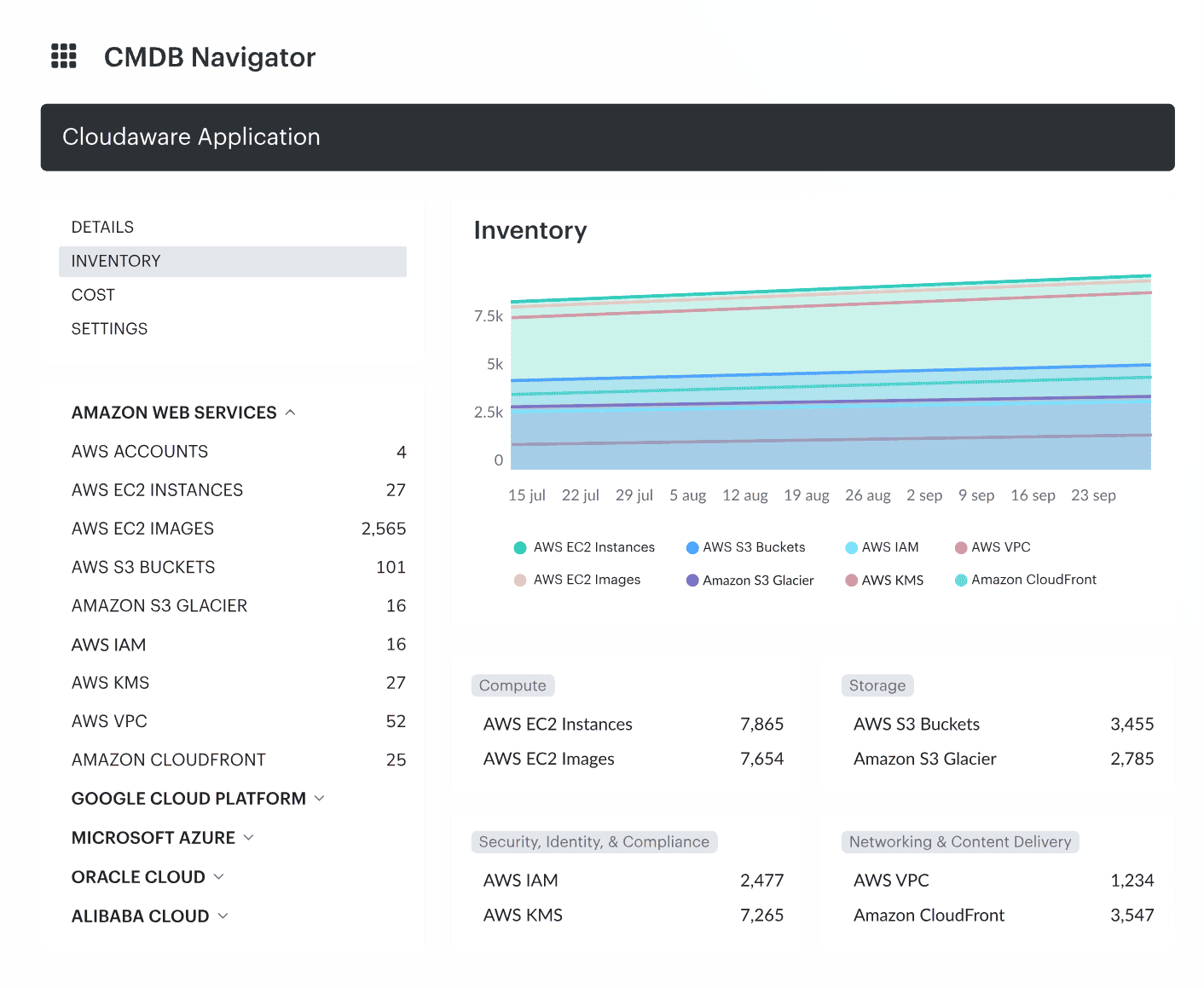
Element of the Cloudaware inventory dashboard.
You’ve got CI metadata syncing from AWS Config, Azure Resource Graph, GCP Asset Inventory. You’ve got live relationships: EC2 → ASG → App Tier → Business Service. You know when a container spun up, when it was last modified, and what policy it violated when it got flagged.
That kind of visibility doesn’t just help infra teams. It keeps SecOps, FinOps, and compliance folks off your back.
2. Actual cost control through lifecycle awareness
Cloud waste is brutal when you can’t see what’s idle.
ITPM lets you tie usage and lifecycle status together. You’ve got “Retire Pending” assets that trigger decommission workflows. You’ve got orphaned volumes moving to a cold storage tier. You’ve got cost center tags traced to owner-level reports through Cloudaware’s cost explorer integration.
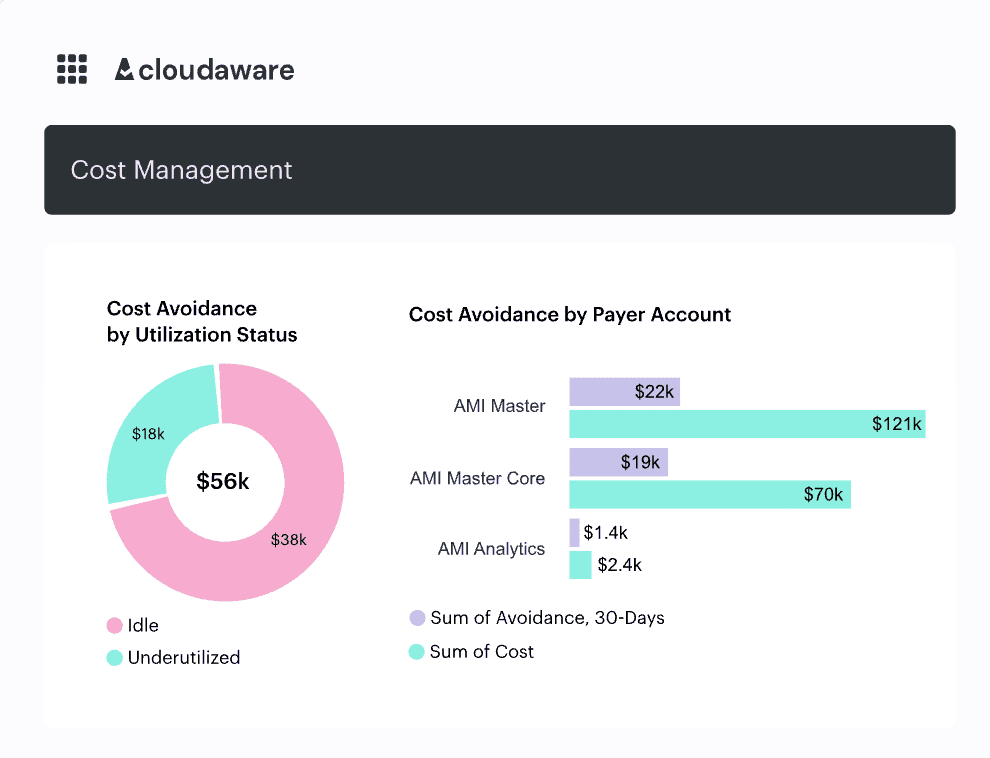
Element of the Cloudaware FinOps dashboard.
And it’s not reactive. You can schedule cleanup policies, auto-expire temporary environments, and monitor cloud-native budgets per portfolio slice.
Suddenly, your monthly report isn’t “where did this bill come from?” It’s “here’s where we saved, here’s who needs to optimize.”
3. Governance that doesn’t break pipelines
Tag enforcement shouldn’t block deploys. But it should prevent someone from launching a public S3 bucket with no owner.
That’s where ITPM comes in. You’ve got auto-tagging rules that fire on discovery. Policy checks baked into CI status transitions. Alerts when a resource violates data residency or encryption standards.
And your CMDB? It’s not stale. It’s tied into ServiceNow, Jira, Slack, and GitHub. So when something breaks policy, the right team gets notified with context. Not just noise.
4. Automation that actually understands lifecycle
Think about your “Modify” state. How many assets are stuck there because no one updated the record?
With Cloudaware ITPM, lifecycle states shift based on events:
- Instance terminated? Status auto-updates to “Retired.”
- CI untagged for 30+ days? Flagged for review.
- Deployment passed security review? Moved to “Production.”
You’re not relying on manual CMDB hygiene. You’re wiring lifecycle to real infra behavior — whether from cloud events, IaC pipelines, or GitOps metadata.
5. Alignment that doesn’t require a presentation deck
You want to show business alignment? Pull up the App Service Map. You’ve got:
- CI relationships by service
- Ownership by team
- Compliance by status
- Cost by project or initiative
When the CIO asks “what infra supports this customer-facing app?” — you don’t build a slide.
You send a live link.
That’s what ITPM does. It connects the cloud you built to the business you serve. And it does it in real-time, without pulling you into a dozen update meetings.
This isn’t a wishlist. It’s what modern ITPM looks like when your tools stop treating ops like a black box.
When to implement an ITPM system
It is one of those questions that sounds simple — until you’re knee-deep in asset sprawl, lifecycle spaghetti, and “why is this S3 bucket still alive” energy.
Here are the signs you need it portfolio management — like, yesterday:
👉 When your CMDB has more “Unknown” CIs than trusted ones
If “Active” and “Unknown” are your most common statuses, something’s off. Lifecycle states should move. CIs should flow through Provisioned → Operational → Retired.
If they’re not, your system isn’t aligned with actual infrastructure behavior.
👉 When nobody can confidently answer “who owns this?”
You’ve got assets live across regions, clouds, and VPCs — but the owner field says “TBD” or “DefaultUser.” That’s not just bad hygiene. That’s an operational risk.
Ownership should come from IaC metadata, repo history, or tag automation — not memory.
👉 When your cloud bills spark surprise and blame
If your FinOps lead asks “what’s this $3,000 charge?” and nobody knows — you’re missing a portfolio view. Spend should tie back to projects, environments, and business services.
Not be a wild guessing game every month.
👉 When test environments are alive long after the sprint ended
You thought QA killed that EKS cluster two weeks ago. Turns out it’s still running. That one zombie workload could be costing you thousands, creating security exposure, and blocking compliance.
👉 When audit prep takes a week — and multiple people
If you scramble every time there’s a policy check, it means compliance data isn’t embedded. You should be able to answer:
- Is encryption enabled?
- Who owns this CI?
- What’s the change history? — on the spot, not after digging through four systems and two humans.
👉 When you’re automating everything except lifecycle and tagging
You’ve got CI/CD humming, infra-as-code, auto-scaling groups, and container orchestration… but tagging still depends on engineers remembering to do it.
That’s a gap.
👉 When compliance isn’t just annual — it’s hourly
One enterprise company I worked with had to prove encryption and ownership across 240 assets in under 24 hours.
They couldn’t.
Now? Their CIs carry compliance metadata, linked to tag policies and active state rules. Violations trigger automated alerts, not a PDF report no one reads. That’s governance built into the lifecycle.
I once heard an ITAM lead say: “If your CMDB isn’t operationally connected, it’s just a historical archive.”
That stuck with me. Because it’s true.
You implement IT portfolio management the moment your environment stops feeling predictable. When infrastructure scales faster than your team can track. When ownership fades. When alignment between IT and business strategy breaks down.
That’s when you need clarity.
You need lifecycle-integrated CMDBs. You need portfolio management that aligns people, projects, and policies.
Not for the sake of process, but for survival. Because in this world of hybrid, fast-moving, cross-cloud complexity — real-time IT asset management isn’t a nice-to-have. It’s what lets you breathe.
Inventory & categorize
You know the drill — your company’s infrastructure is spread across AWS, Azure, GCP, maybe even a few on-prem vSphere clusters no one talks about. Terraform’s deploying half your infra, some of it still gets built in the console, and there's a Jenkins job from 2019 that quietly provisions IAM roles every Thursday.
Your CIs? They’re everywhere. In various states. With inconsistent metadata, missing owners, and zero traceability back to business services.
I had a client — a global SaaS company running CI/CD across 130+ dev teams — who hit that wall hard. CMDB looked “full” but meant nothing. CI lifecycle states weren’t used. Their project portfolio management team was making infra decisions based on assumptions, not actual data.
We reset and started with Cloudaware discovery and auto-classification.
Here’s what we did:
- Connected native cloud APIs: AWS Config, Azure Resource Graph, GCP Asset Inventory.
- Discovered and normalized CI types:
EC2,S3,AKS,SQL MI,Cloud Function,Firewall,IAM Group, etc. - Associated each asset to:
- Environment (based on tags + deployment metadata)
- Lifecycle phase (
Provisioned,Operational,Retire Pending) - Business service (via dependency relationships and app/service mapping)
- Owner (via IaC annotations, repo maintainers, or org directory mapping)
- Cost center, region, project association, and deployment source
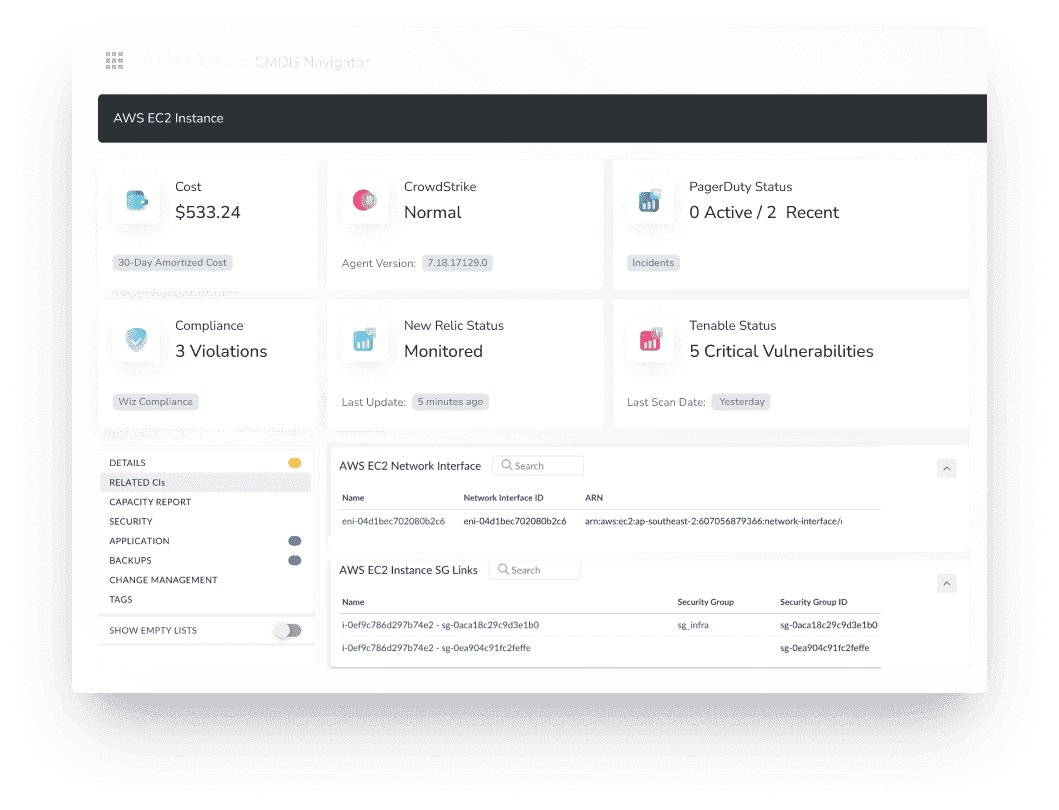
This wasn’t just a cleanup. It was portfolio alignment in real-time.
Because the minute you can group resources by business purpose, cost accountability, and lifecycle phase — you’re not just doing infra ops. You’re enabling strategic portfolio management at the architecture level.
That’s what organizations actually need from IT. Not “how many EC2s do we have,” but “what’s powering this app, who owns it, and is it still needed?”
Inventory & Categorize step isn’t glamorous. But it’s the foundation. Nail it, and you’ll finally have a CMDB that reflects the real state of your infrastructure — not just what was deployed last quarter.
Read also: Everything you should know about IT hardware asset management in 2025
Align with strategy
Once your inventory’s clean — your IT assets are discovered, categorized, and tagged — step two in the IT portfolio management journey is all about alignment.
And not just alignment for the sake of a slide deck.
I’m talking real-world, architectural-level portfolio alignment with the business objectives your company actually cares about.
Because here’s the pattern I see too often: Infra is humming, CIs are deployed, engineers are moving fast — but no one can trace which projects, applications, or services actually map back to strategic goals.
So here’s where we shift. We go from “what do we have?” to “why do we have it — and what is it helping us achieve?”
In Cloudaware CMDB, we start by anchoring to business initiatives. Usually, these come from enterprise architecture teams, the CIO roadmap, or the project portfolio management office.
Think:
- “Improve customer retention through digital experience”
- “Reduce cloud cost by 20% this fiscal year”
- “Replatform legacy workloads to Kubernetes”
- “Ensure regulatory compliance for all external-facing systems”
Next, we map resources — VMs, containers, load balancers, secrets, storage buckets — to these business objectives.
We build relationships across the stack: CI → Application → Business Service → Initiative
We tag with project codes.
We layer in cost centers.
We align compliance and risk data across the portfolio.
And we let the CMDB become the single source of truth not just for infra — but for how that infra powers the business.
The result? You stop thinking in assets. You start thinking in value streams.
Now every engineer, architect, or security lead can answer:
- “Which projects are these assets tied to?”
- “What strategic outcome is this cluster supporting?”
- “Why are we still funding this service if the initiative closed last quarter?”
That’s what portfolio management looks like when it’s connected. And when organizations reach that point, they stop reacting to infra, they start using it to drive the company’s next move.
Once you've aligned your infrastructure with actual business objectives, the next step in the IT portfolio management strategy is where things get spicy 😈
Optimize & rationalize
This step is about assessing your current resources — apps, services, infrastructure — and deciding what to consolidate, what to replatform, and what to decommission.
Here’s how we do it with enterprise clients using the CMDB:
1️⃣ Group CIs using virtual applications, environment tags, and initiative metadata
Start by organizing your infrastructure using Virtual Applications. These groupings let you cluster CIs based on app boundaries, platform teams, or product domains — even if the assets span multiple cloud providers.
→ Use environment tags (dev, stage, prod) pulled from discovery and IaC metadata.
→ Leverage custom fields or label policies to assign initiative names, project codes, or internal tracking IDs.
→ Identify stray CIs not tied to any Virtual Application or initiative — these often signal technical debt or legacy drift.
This gives your IT portfolio structure: defined service boundaries, environment visibility, and a baseline for business alignment.
2️⃣ Enrich CIs with operational & lifecycle data
Cloudaware auto-enriches each CI with data from AWS Config, Azure Resource Graph, GCP Asset Inventory, and tagging frameworks.
You’ll want to layer in:
- Lifecycle status (
Provisioned,Operational,Retire Pending, etc.) - Cost center, region, and business unit
- Owner or responsible team (from tags, pipelines, or org sync)
- Security posture (public endpoints, encryption status, vulnerability tags)
- Usage insights via integration with billing and activity metadata
This makes it possible to assess which CIs are actively delivering value — and which are just taking up space.
3️⃣ Apply rationalization logic based on real conditions
Here’s how Cloudaware customers define action triggers:
- CIs in “Retire Pending” for >30 days → ready for automated cleanup.
- No associated Virtual Application or initiative metadata → tag for review.
- Idle compute/storage (no usage or cost spikes in 60+ days) → rationalization candidates.
- Redundant services across Virtual Applications (e.g., duplicate queues, schedulers, databases) → target for consolidation.
- Tagging drift, incorrect lifecycle state, or missing ownership → trigger remediation workflow or alert.
The goal isn’t just cost optimization. It’s strategic portfolio management — ensuring that what’s live in your cloud reflects the business priorities of your organization, not just the leftover results of past projects.
Once you’ve cleaned, categorized, aligned, and optimized your infrastructure, it’s time to ask a hard question: Where are we exposed — and how bad could it get?
Assess & mitigate risk
This step of IT portfolio management puts every resource, every project, every business-critical app under a magnifying glass — and asks: What’s vulnerable? What’s non-compliant? What’s quietly threatening uptime, security, or trust?
The theory is simple:
Risk = Likelihood × Impact.
Your job is to lower both — through visibility, automation, and strategic alignment.
But in complex environments, that means going beyond CVEs and security groups. You need to assess risk by context: lifecycle state, ownership, criticality, exposure, and drift from policy. And then build automated mitigation workflows that tie directly back to your portfolio management model.
How we do it in practice with Cloudaware CMDB:
- Surface vulnerable or misconfigured assets using filters & rules
→ Public-facing resources without encryption
→ “Operational” CIs with no owner or outdated lifecycle status
→ Assets failing CIS Benchmarks, PCI-DSS, or org-specific controls
→ Unused IAM roles with elevated privileges - Map risk across Virtual Applications and business services
→ Use related items and CI metadata to understand blast radius
→ Prioritize mitigation based on exposure vs. business value (e.g., is this a forgotten dev pod or a production payment API?)
→ Flag resources tied to high-priority projects or regulated environments - Feed risk signals into the portfolio
→ Tag risky CIs with severity levels
→ Link them to ongoing projects and initiatives in your project portfolio management workflows
→ Trigger workflows: notify owners, open remediation tickets, or auto-update CI status
I’ve worked with organizations where a single CI — an untagged S3 bucket with a vague name — ended up exposing company customer data.
No one knew it existed.
No one knew who owned it.
It wasn’t in the CMDB at all.
IT portfolio management isn’t just about structure or visibility. It’s about resilience — making sure your infrastructure reflects the real risk posture of your business.
But governance isn’t a finish line.
It’s that part of IT portfolio management that either becomes a living rhythm or quietly fades into background noise while shadow infra multiplies behind your back.
Read also: Choosing asset management software? These 15 Features Are a Must
Continuously govern & adapt
It is where all the cleanup, alignment, optimization, and risk work you’ve done either sticks... or slips.
I’ve seen this in real setups — asset lifecycle workflows carefully defined, cost policies rolled out, CI ownership rules enforced for a sprint or two.
Then a re-org happens. Or someone launches a new pipeline with no tagging hooks. Or worse, you onboard a new vendor, and 42 unmanaged containers show up across three clusters.
This step is about building the muscle to respond — at the portfolio level.
Here's how we make it stick:
1. Set governance boundaries that flex without breaking
Start by documenting actual rules — lifecycle triggers, tagging standards, cost center tags, owner attribution requirements, etc.
Not in a doc nobody reads. In logic your systems recognize.
Structure these policies so they adapt:
- If a CI is marked “Operational” but hasn’t been active in 45 days, trigger a lifecycle review.
- If a container is spun up without owner tags or repo metadata, it’s non-compliant — flag it before it’s forgotten.
- If a resource’s region or cost center conflicts with the project’s config file, it’s a signal, not a failure — escalate accordingly.
2. Tie governance to change, not just audits
Lifecycle doesn't live in a spreadsheet. It flows through provision → change → retire, and it has to move with actual events.
That means:
- CI status updates tied to IaC changes, not Jira tickets
- Ownership reassignments triggered on team transitions
- Policy checks embedded into pre-deploy checks or GitHub Actions
- Real-time visibility into drift between actual state and expected state
This kind of continuous governance generates meaningful data — not just audit trails, but behavior patterns. It shows where project portfolio management efforts are misaligned with live infrastructure and where you need to re-sync.
3. Adapt your portfolio to reflect business evolution
This is where it gets strategic.
- When teams replatform from EC2 to EKS, are you retiring the right resources?
- When a business unit is sunset, do their services get flagged for decommission?
- When a new initiative is spun up, are the services, CIs, and budget lines reflected in the CMDB?
If not — you’re already drifting. And what looked like a clean portfolio last quarter? It’s out of sync with your organization.
Continuously Govern & Adapt isn’t glamorous. It’s config rules, tagging audits, Slack alerts, and tracking down lifecycle violators. But it’s what makes your IT portfolio management resilient.
So the next time you look at an EC2 tagged “Default,” you already know what process failed — and what happens next.
Top 7 IT portfolio management lifehacks from ITAM experts
Here are the proven tactics from my teammates who every day work with hybrid multi-cloud enterprises:
Tagging without enforcement is noise
Anna, ITAM expert at Cloudaware: “One of the most overlooked portfolio management practices is treating tags as passive labels. We flipped that. Our provisioning flow enforces a strict schema — ci_owner, service_id, cost_center, lifecycle_state, business_unit. These aren't for reports — they drive automation, lifecycle transitions, and cost accountability.
Every tag feeds into broader IT portfolio management workflows across the company. If metadata is missing, deployment fails. That’s how organizations move from visibility to strategic alignment.”
If you’re still assigning ownership after deploy, you’re already behind
Iurii Khokhriakov, Technical Account Manager: “In well-governed portfolio management, ownership isn’t an afterthought — it’s provisioned like any other infra setting. We pull owner IDs from GitHub CODEOWNERS or Terraform modules and inject them into every CI.
This ties infrastructure directly to teams, not just generic business units. When something breaks or violates policy, data from ownership fields routes alerts and remediation back to the source, fast.”
Virtual Applications are your guardrails in the chaos
Mikhail Malamud, GM @ Cloudaware: “One of the best portfolio management practices we use is grouping resources not just by type, but by purpose. Virtual Applications let us define service boundaries and enforce policies, lifecycle states, and cost guardrails inside those boundaries.
When a service spans clouds or is shared across projects, this structure ensures accountability stays aligned with the business service — not just the platform.”
Nothing should sit in ‘Retire Pending’ more than 30 days — ever
Kate, ITAM expert at Cloudaware: “That status should trigger action. Our rule? At 15 days, alert the owner. At 30, archive the resource, apply deletion_candidate:true, and open a ticket. This reduces noise and keeps our IT portfolio clean and reflective of current projects.
When every state is tied to real process, your management system doesn’t drift — it evolves.”
Lifecycle drift is your hidden CMDB rot — and it spreads
Kristina S., Senior Technical Account Manager at Cloudaware: “We monitor lifecycle-state mismatches daily. CIs marked “Operational” but inactive for 60+ days get flagged. Terminated resources still marked “active”?
We dig into the provisioning data, revalidate status, or auto-sync. Stale records mislead project portfolio management reviews and weaken governance. Freshness is truth. You either manage change, or your CMDB becomes fiction.”
Stop scoring risk like it’s isolated. Score it like it’s networked
Iurii Khokhriakov, Technical Account Manager: “A misconfigured resource means something different depending on where it lives. We assess severity by linking CIs to business services, strategic initiatives, and lifecycle phases. If a public endpoint touches prod systems tied to customer-facing projects, the risk score gets bumped.
Organizations that ignore alignment between technical risk and business impact miss critical exposure points.”
Governance should feel like a pipeline, not a policy doc
Kristina S., Senior Technical Account Manager at Cloudaware: “We codified governance into our CI/CD tooling. Tag enforcement, ownership checks, lifecycle validation — it’s all wired into GitHub Actions. No tag? No merge. No owner? No deploy.
These aren’t blockers; they’re accelerators for safe, scalable portfolio management. They keep our teams compliant without slowing velocity.”
If your CMDB freshness is over 30 days, you’re not managing reality
Mikhail Malamud, Cloudaware GM: “It’s better to log last_updated_at for every CI and track stale resources weekly. If 35% of the portfolio hasn’t been touched in over a month, we investigate.
Sometimes it’s drift, sometimes it’s dead infra. Either way, it’s not portfolio truth. And in enterprise management, trust in your data is the bedrock of every decision.”
The tech stack you’ll need for real IT portfolio management
When folks say they want “IT portfolio visibility,” what they really mean is: “I want to know what we have, what it’s costing us, who owns it, and whether we still need it.” But none of that works without the right stack underneath.
Not just tools — solutions. The kind that move with your cloud, not behind it.
Here’s how the core layers come together to deliver real portfolio management at scale — supporting your infra, your projects, your teams, and your company’s long-term goals.
1️⃣ Your real-time CMDB
Everything starts with a living, breathing CMDB. It’s the heartbeat of IT portfolio management — pulling in discovery data from AWS Config, Azure Resource Graph, GCP Asset Inventory, and Terraform state files.
Each Configuration Item (CI) is enriched with:
- CI type (
EC2,AKS,CloudSQL, etc.) - Tags:
owner,business_unit,project_id,lifecycle_state,compliance_status - Related items and logical associations
- Tied to actual business services and strategic initiatives
This builds your baseline of data — clean, contextual, and actionable.
2️⃣ FinOps intelligence
You can’t manage what you can’t quantify. Your stack needs cost attribution down to the CI level — rolled up by projects, business units, and service boundaries.
We’re talking:
- Budget thresholds based on
cost_centertags - Alerts for idle or over-provisioned resources
- Spend tracking aligned to project portfolio management plans
- Anomaly detection across clouds and services
Now your organizations aren’t just seeing numbers — they’re making decisions.
3️⃣ Governance that moves with the code
This is where policy enforcement becomes real. Ownership, encryption, tagging, lifecycle rules — these can’t live in PDFs. They need to live in GitHub Actions, Terraform validators, and deployment pipelines.
This layer includes:
- Tag validation at deploy
- Lifecycle state tracking tied to IaC
- Auto-alerts for drift, non-compliance, and data exposure
- Slack or Jira integrations to surface violations instantly
It’s governance, but frictionless — baked into every change your teams make.
4️⃣ Lifecycle intelligence engine
Every CI should move through lifecycle states. Provisioned → Operational → Modified → Retire Pending → Retired isn’t a theory — it’s how you reflect truth in your portfolio.
Lifecycle transitions are triggered by:
- IaC state changes
- CloudTrail events (e.g., termination)
- CI aging thresholds (e.g., 45+ days inactive)
This keeps your data fresh, your workflows aligned, and your CMDB relevant to current business priorities.
5️⃣ Strategic alignment lens
This is what turns infra into insight.
You link CIs to:
- Applications
- Business services
- Strategic initiatives
- Active or archived projects
So when someone from leadership asks, “What infrastructure supports this initiative?” — you’ve got the full lineage. And when a project sunsets, your system can flag orphaned infra tied to that initiative, ready for retirement.
This is the crown jewel of portfolio management: Context + traceability + clean handoffs = true alignment across tech and the company.
This stack isn't just about control — it's about clarity. It turns chaos into context, costs into signals, and infrastructure into an asset that reflects how the business really runs.
Finally, make your cloud portfolio make sense
Disconnected data. Unknown owners. Bloated spend. Compliance risk around every corner.
Cloudaware brings it all together.
Our platform acts as your real-time, always-current CMDB — purpose-built for hybrid and cloud-native complexity. We go beyond simple discovery. With 200+ integrations including AWS, Azure, GCP, VMware, Alibaba Cloud, and on-prem tools, Cloudaware gives you full-spectrum visibility across your entire ecosystem.
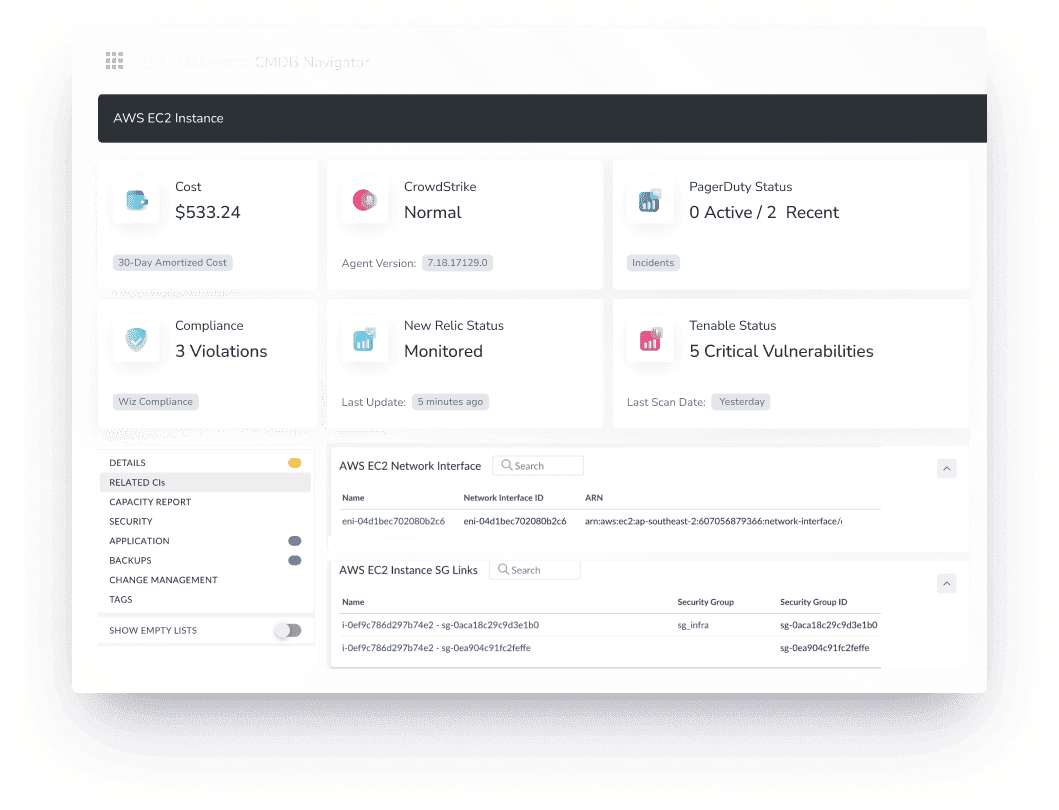
What you’ll get:
✅ Unified, real-time asset discovery across clouds and datacenters
✅ Dynamic grouping into Virtual Applications for governance, cost, and lifecycle control
✅ Full IT lifecycle tracking — Provisioned to Retired, automated by events
✅ Ownership, tagging, cost center, and compliance policy enforcement at deploy
✅ FinOps alignment with detailed cost attribution to services, teams, and projects
✅ Context-rich service mapping tied to business objectives and strategic initiatives
✅ Drift detection and proactive compliance alerts that trigger real workflows
Whether you're trying to reduce shadow IT, eliminate waste, prepare for audits, or align infrastructure with business goals — Cloudaware helps you manage your IT portfolio with confidence.
We don’t just tell you what’s deployed. We show you what it supports, what it costs, who owns it, and whether it belongs.
