“Wait — who changed that security group?”
If you’ve ever lost half a sprint chasing that question, you already know the pain. Drift. Misconfigurations. Orphaned resources. And the worst one? Infra changes with zero traceability.
In hybrid environments where CIs are scattered across AWS, Azure, on-prem, and no one owns tagging hygiene, things break silently — and ops teams are left piecing together the fallout. From IAM roles that outlive their purpose to EBS volumes with no backup policies, the risk isn’t just operational. It’s compliance-level.
That’s where configuration management steps in — not just as a concept, but as a mission-critical discipline baked into your CMDB, IT asset inventory, and change control processes.
In this article, we’ll break down:
- A clear configuration management definition
- Key processes like CI versioning, drift detection, and policy enforcement
- Where software configuration management fits into the bigger picture
- Real-world examples from DevOps trenches
- How to embed it across your stack without slowing anything down
Let’s unpack it.
What is configuration management?
Let’s define configuration management the way it actually plays out in real-world DevOps: it’s how you stop your infrastructure from becoming a giant “who did this?” meme. The configuration management meaning isn’t just about inventory — it’s about maintaining control over dynamic, distributed, constantly changing systems.
It’s the discipline of identifying, tracking, and maintaining the state of every configuration item (CI) in your environment — from autoscaling groups and Helm charts to that one zombie EC2 instance that keeps respawning like it’s in a bad reboot loop.
It’s not just about tracking assets. It’s about capturing the entire lifecycle of your stack:
- Who spun it up
- What changed
- What it’s connected to
- Why it even exists in the first place
Configuration management in DevOps workflow ties into everything. You’re pulling in metadata from Terraform state files, AWS Config, GitHub Actions, Jenkins, ArgoCD, maybe even Jira tickets if you’re feeling fancy. You’re mapping your infra across clouds and clusters, and you’re automating that visibility so you’re not manually reconciling state like it’s 2009.
This is your foundation for:
- Change management workflows that actually reflect reality
- Incident response that doesn’t start with “okay but what’s even running in prod?”
- Compliance that doesn’t make your team cry during audits
If you’re running ephemeral infra, spinning environments on demand, and using GitOps or IaC — then you need a config layer that’s version-aware, real-time, and context-rich.
Because real talk? You can have flawless pipelines, beautifully linted YAML, all the GitOps you want — but if your configs are chaotic, you’re just deploying into the unknown and hoping nothing explodes.
That’s where solid configuration management flips the script. It turns daily chaos into something you can actually reason with.
You get to:
- Catch drift early, before a quiet staging tweak derails your next release
- Know who owns what, without spelunking through 15 Slack threads
- Uncover critical dependencies — like that "temporary" Redis someone’s quietly built half the data pipeline around
- Build guardrails right into your delivery flow, so misconfigured services never even make it to staging, let alone prod
When config stops being an afterthought and starts being a source of truth, you stop firefighting and start shipping with confidence.
And that’s just warming up.
Next, let’s look at how configuration management actually accelerates your team — better visibility, fewer blockers, and smoother, safer deploys every damn time.
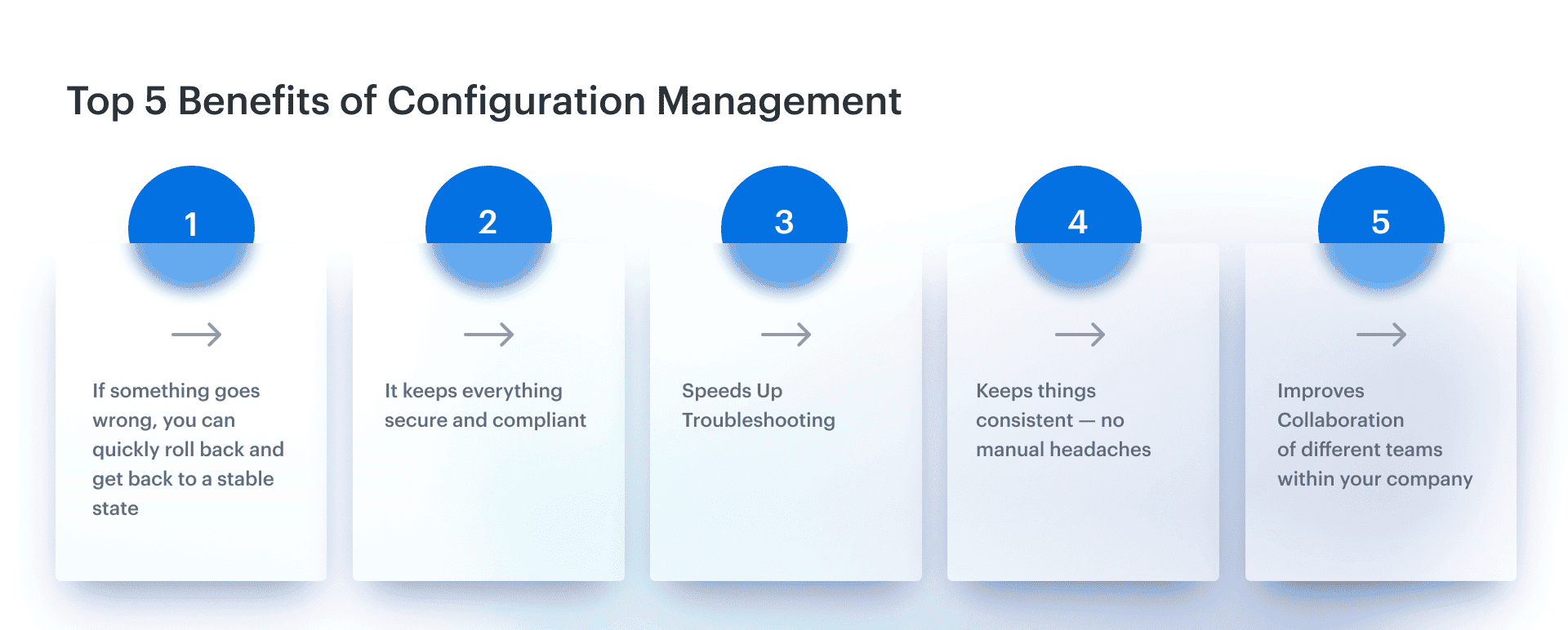
What are the 5 benefits of configuration management?
It’s the backbone of stability, security, and efficiency in complex IT environments. Managing hundreds of assets across hybrid systems? Chaos. Staying on top of every configuration is the only way to avoid it.
Here’s why configuration management matters for enterprise environments — and what are the benefits of configuration management you actually feel day to day:
- Reduces Downtime. One of the biggest configuration management benefits is its ability to give you control over every change. So, if something goes wrong, you can quickly roll back and get back to a stable state. I’ve seen teams slash their downtime by half just by keeping track of their updates and changes. It’s like having a safety net that catches you before things go south.
- Improves Security. Let’s face it — security is always a big deal. With configuration management software, you can see who’s making changes. Simple. It keeps everything secure and compliant. This matters big time in regulated industries, where staying on track can be a real pain. Having that single source of truth for all configurations? Total lifesaver. This is one of those software configuration management benefits that gives both SecOps and auditors peace of mind.
- Speeds Up Troubleshooting. When stuff breaks, knowing exactly what was changed and when can be a huge time-saver. If there’s a problem, you can pinpoint it way faster, saving both time and frustration. Companies using configuration management tools fix incidents 30% faster — and that’s not just a nice-to-have, it’s a serious edge.
- Supports Scalability. Trying to scale without a solid process? That’s a nightmare. One of the biggest benefits of configuration management is how it automates the boring stuff. As you grow, it keeps things consistent — no manual headaches, no snowflake environments.
- Better Collaboration. When all your teams — DevOps, security, ops — are synced, things run smoother. You don’t waste time sorting through miscommunications, and projects get done faster. Trust me, I’ve seen it in action.
When you look at the full picture, the configuration management benefits stack up fast. Visibility, control, traceability, speed — it all adds up to smoother operations and fewer fire drills.
Configuration management makes IT sprawl manageable. It's a must-have for enterprise teams.
Read also: IT asset Lifecycle Management From Day One to Done
How configuration management supercharges your team's workflow
You know, after diving deep with all these big enterprises, I can hands-down say that configuration management is the quiet MVP of keeping everything sane. Especially when you’re juggling cloud plus on-prem, different regions, a dozen app teams, and that lurking compliance audit.
So here’s the story.
- For the DevOps crew? Configuration management is like their secret safety harness. It keeps environments — dev, staging, prod — aligned, so rolling out updates doesn’t feel like launching a rocket with your eyes closed. It cuts the “worked on my laptop but nuked production” drama. And with a solid CMDB as the backbone, you’ve got your config management nailed down and can roll back cleanly if something goes sideways.
- Infra folks? They’re the unsung heroes trying to scale without tripping over a thousand loose cables (metaphorically). A good configuration management system centralizes everything — no more clunky spreadsheets or hopping between portals. Scaling clusters, patching servers, tweaking load balancers — it’s all tracked, versioned, and auditable. That’s some serious infrastructure configuration management magic.
- Security teams live for this stuff. Because real-time configuration management processes mean they can see changes as they happen, catch misconfigs before they become CVEs, and sleep better at night. A CMDB gives them that crystal-clear trail — so no sneaky port left open or rogue admin account flying under the radar.
- Ops? Configuration management means fewer war rooms at 2 AM. With everything documented and visible, troubleshooting becomes less “detective mystery” and more “follow the breadcrumbs.” That’s priceless for uptime.
- Devs? They get consistent environments every time. That means fewer bugs from mismatched configs, faster testing, smoother deployments. With software configuration management locked in, you squash so many headaches before they ever show up.
- And compliance? It’s a lifesaver. All those standards and audits love a neat audit trail. Configuration management hands you that on a silver platter. Your CMDB software becomes the ultimate receipts folder — every change, who did it, when, why.
Long story short: if you ever wonder “what is configuration management and why is it important?” — it’s this. It keeps your tech universe in sync, your teams working off the same playbook, and your auditors off your back. A solid CMDB just makes the whole thing hum. That’s the real benefit of configuration management — less chaos, more flow.
Read also: Find It, Track It, Own It: Multi-Cloud IT Portfolio Management
6 steps of configuration management process
This isn’t your vendor's PowerPoint version of config management. This is the in-the-weeds, real-life, DevOps-after-dark breakdown of how configuration actually gets handled when you’re juggling IaC, compliance, shadow cloud, and “just one more pipeline tweak” that wrecks prod.
I’ve worked with Cloudaware customers who’ve tried to manage config chaos with spreadsheets, tribal knowledge, and Slack archaeology. Spoiler: that doesn’t scale. But when your CMDB speaks fluent Terraform, tags, and API drift? That’s when configuration management stops being overhead and starts being your control tower. This is the real software configuration management process in action — automated, integrated, and tied directly to delivery.
So here’s the deal.
These are the 6 steps that make or break the configuration management process when you're flying at enterprise scale. Whether you’re looking to tighten your configuration control practices or build an ITIL configuration management framework, these are your foundational plays.
1️⃣ Align on strategy before you discover anything
Before you sync your first resource, pause. Define what a “configuration item” even means for your stack. Is it a Helm chart? A container image? An abandoned EBS volume chewing up budget? You need clarity — or you’ll collect noise, not data.
This step is about defining the scope and purpose of your CMDB. It’s where you align with your stakeholders — DevOps leads, cloud architects, security teams, and IT operations — on what counts as a CI, what attributes matter (like environment, ownership, or lifecycle status), and what your end goal is.
Are you doing this for compliance? For visibility? For automating delivery pipelines?
You also need to decide how deeply to model relationships: will you track parent-child links, dependencies, or change history?
Are you aligning with frameworks like ITIL or NIST?
These strategic questions drive how your CMDB gets built — and whether it actually helps your team or becomes another dusty dashboard no one opens.
2️⃣ Find what’s really out there
Once you know what you care about, now it’s time to go full detective. Inventory every CI — cloud, on-prem, Kubernetes, even your Ansible-managed oddities still humming under someone’s desk.
But let’s be clear — this isn’t a manual sweep. A modern CMDB like Cloudaware integrates directly with your environments to automate discovery. You plug in your AWS, Azure, and GCP accounts; connect your Kubernetes clusters; hook up your Terraform backends, Git repos, and config management tools like Puppet or Chef — and the CMDB does the rest.
It ingests data via APIs, parses infrastructure-as-code artifacts, listens to deployment events, and correlates everything into structured configuration items. You get one normalized, continuously updated view of all your assets, with context like environment, ownership, provisioning method, and deployment source stitched in from the start.
This step isn’t just about grabbing resources from AWS Config or Azure Resource Graph and calling it a day. It’s about letting the CMDB automatically surface what’s out there — so your team can skip the scavenger hunt and get straight to managing risk and velocity. This is the core of process configuration management at scale.
3️⃣ Group the chaos into something useful
Discovery gives you a haystack. Now we sort the needles. Classification is what lets you slice your CMDB in ways that match how your org operates — by environment (prod vs staging), by team, or by service layer.
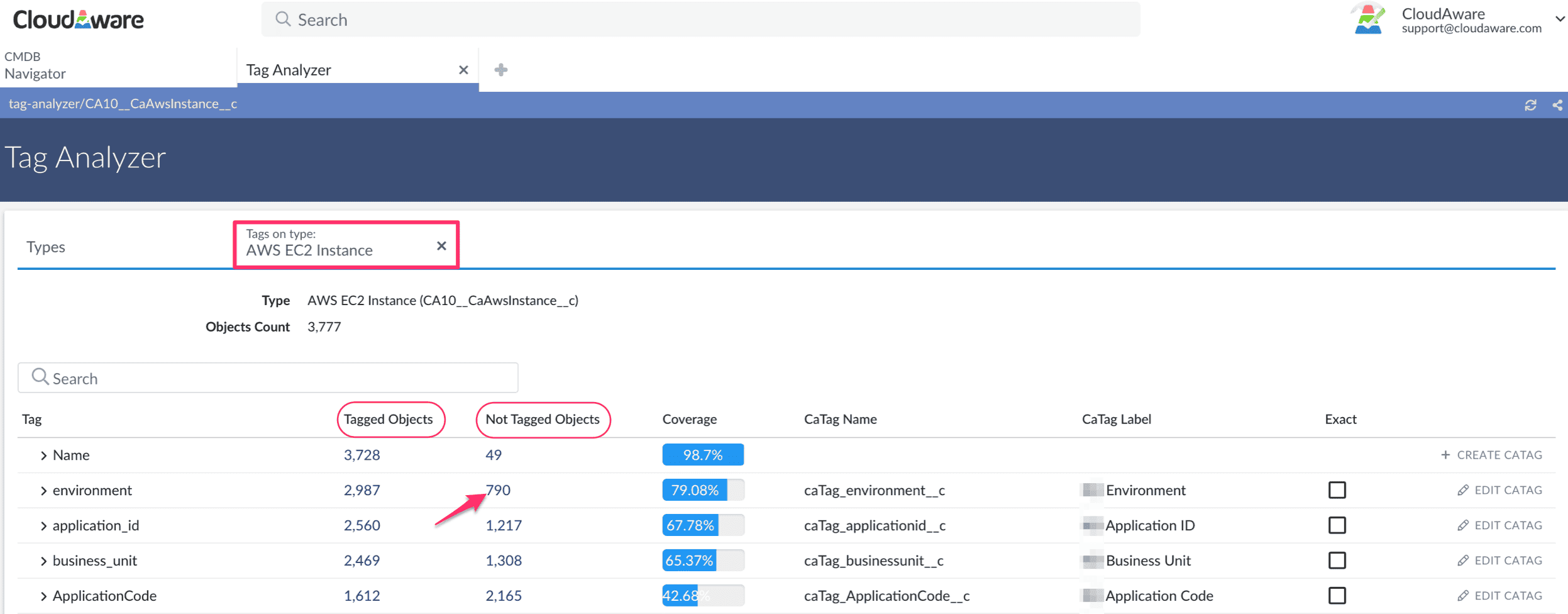
Element of the tag management dashboard at Cloudaware. Schedule a free demo to see how it works
This isn’t just tagging — it’s assigning the right CI types, mapping parent/child relationships, and applying context from your CI pipelines. Misclassifying a container host as a standard VM can tank your drift detection downstream or trigger false positives in compliance dashboards.
Accuracy here = trust later. It's also the foundation of repeatable configuration management processes.
4️⃣ Track every change with context
Once you’ve got everything mapped and sorted, it’s time to get serious about versioning. You need to know what changed, when, why, and by whom — and be able to trace it back to a pipeline, a PR, or a human who clicked the wrong thing.
For example, one Cloudaware customer caught an unauthorized IAM policy edit within minutes. The CMDB flagged a delta between CI snapshots and linked it to a rogue Jenkins job that slipped through without approval. That kind of traceability isn’t just nice — it’s a non-negotiable.
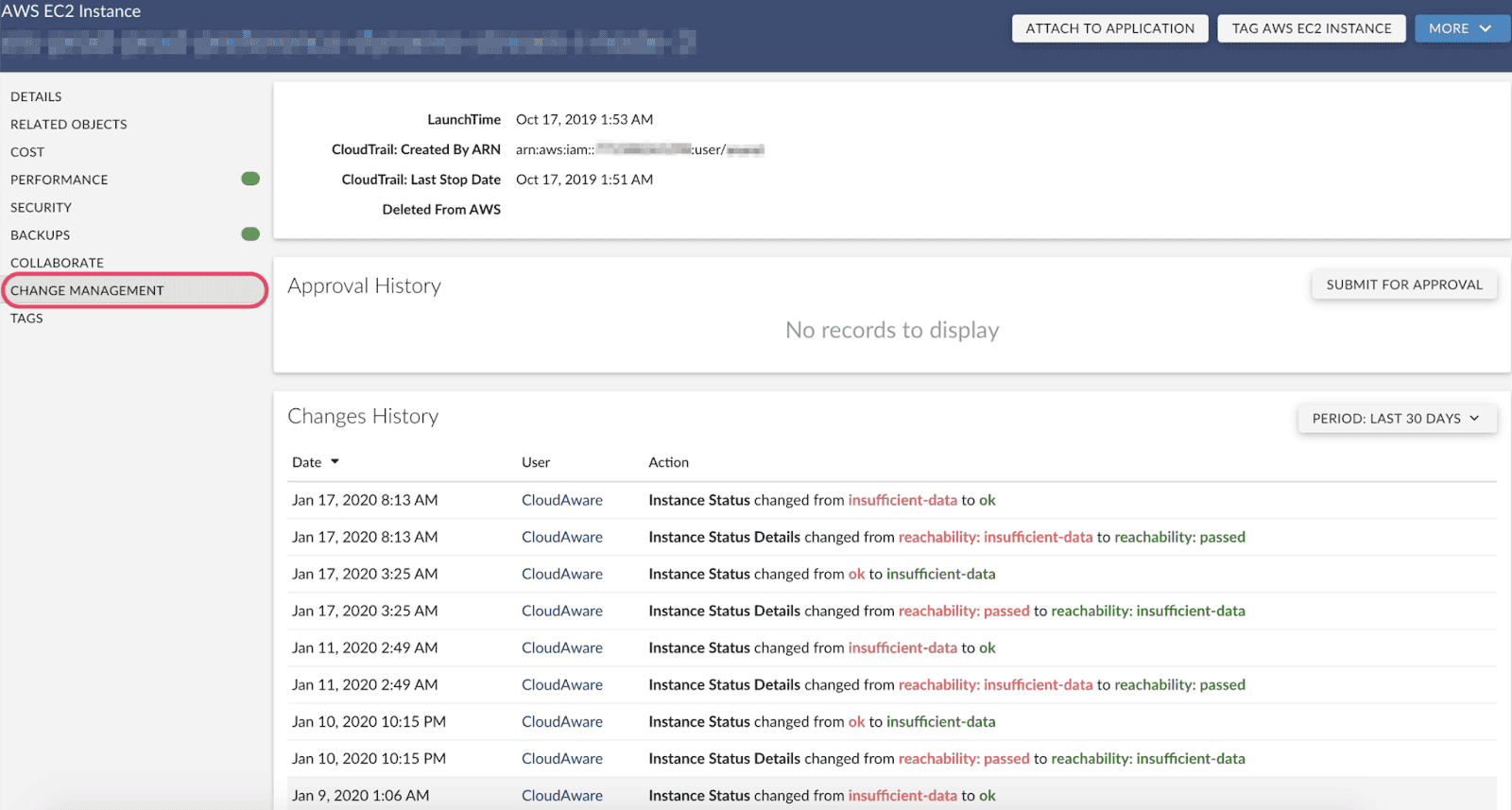
Element of the change management at Cloudaware. Schedule a free demo to see how it works
This is where Cloudaware ties CI versioning directly to change requests, code commits, and CD events across platforms. In terms of IT configuration management, this step is where configuration control lives and breathes.
Read also: Top 10 Enterprise Asset Management Software: Features & Pricing
5️⃣ Set your golden baselines
You’ve seen the landscape. Now define what “correct” looks like. Baselines are your config source-of-truth — used to flag misconfigurations, enforce policies, and lock down critical infra.
In Cloudaware, baselines can be defined for both security and operational consistency — things like encryption-at-rest, approved instance types, required tags, minimum TLS versions, IAM role conditions, or whether a resource was deployed via IaC. These aren’t static templates — they’re dynamic policies that get enforced in real time.
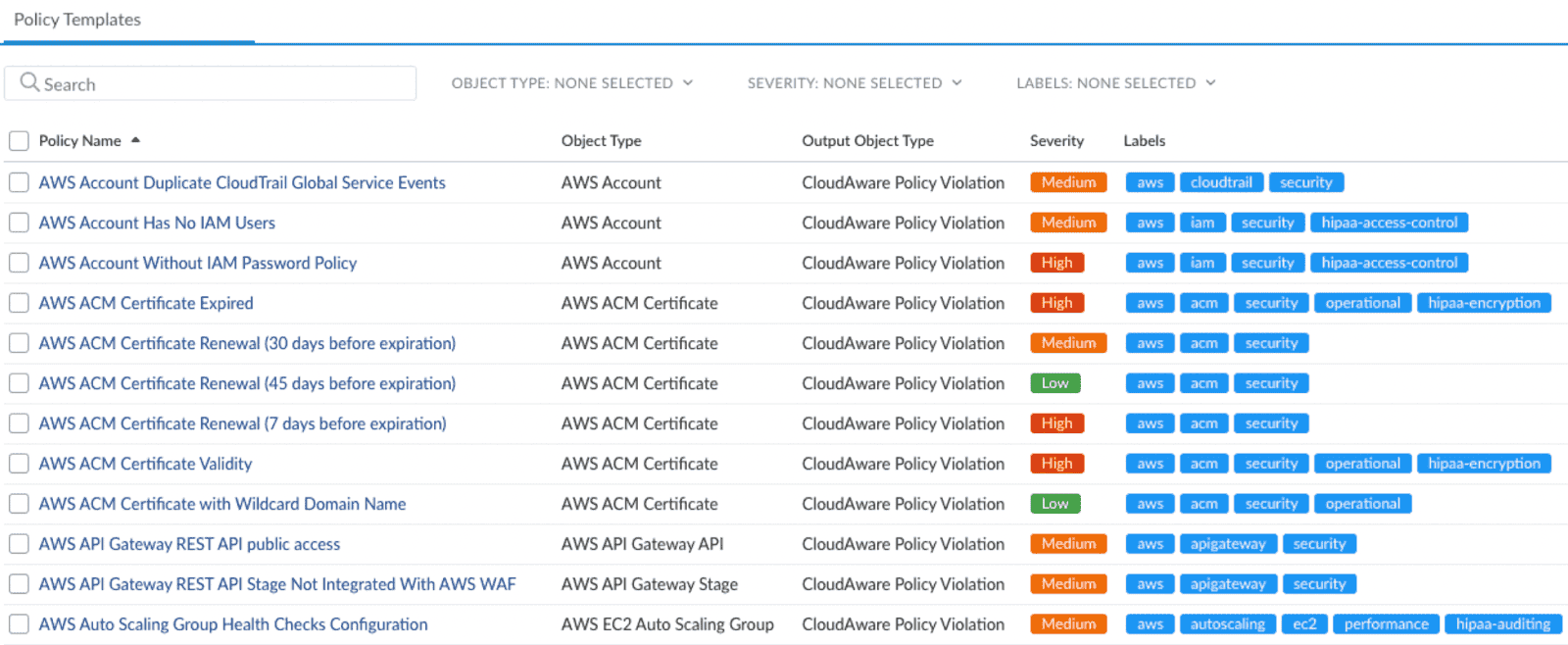
Policy templates at Cloudaware. Schedule a free demo to see how it works
In one example, a Cloudaware fintech customer embedded a baseline with required encryption-at-rest for all storage resources (AWS EBS volumes and Azure Managed Disks), mandatory cost allocation tags, and restricted instance classes for production environments. Any non-compliant infra that spun up — whether manually or via CI — was flagged immediately.
But more than that — it tied into their GitLab CI/CD pipeline, automatically blocking the merge and halting deployment. It wasn't just policy enforcement — it was preemptive control baked into delivery. That’s what real software configuration looks like in practice.
6️⃣ Catch drift before it catches you
Once your baselines are in place, it’s time to go full ops ninja. Continuous compliance checks and status monitoring let you catch drift, misalignment, and policy violations in real time.
This means checking against frameworks like CIS Benchmarks, NIST 800-53, or your own internal hardening guide. Cloudaware customers run scheduled scans that surface drift across accounts, clusters, and data centers. Violations trigger webhooks, open tickets in JIRA, and route to team Slack channels automatically — so the right folks get alerted before it hits prod or audit season rolls in.
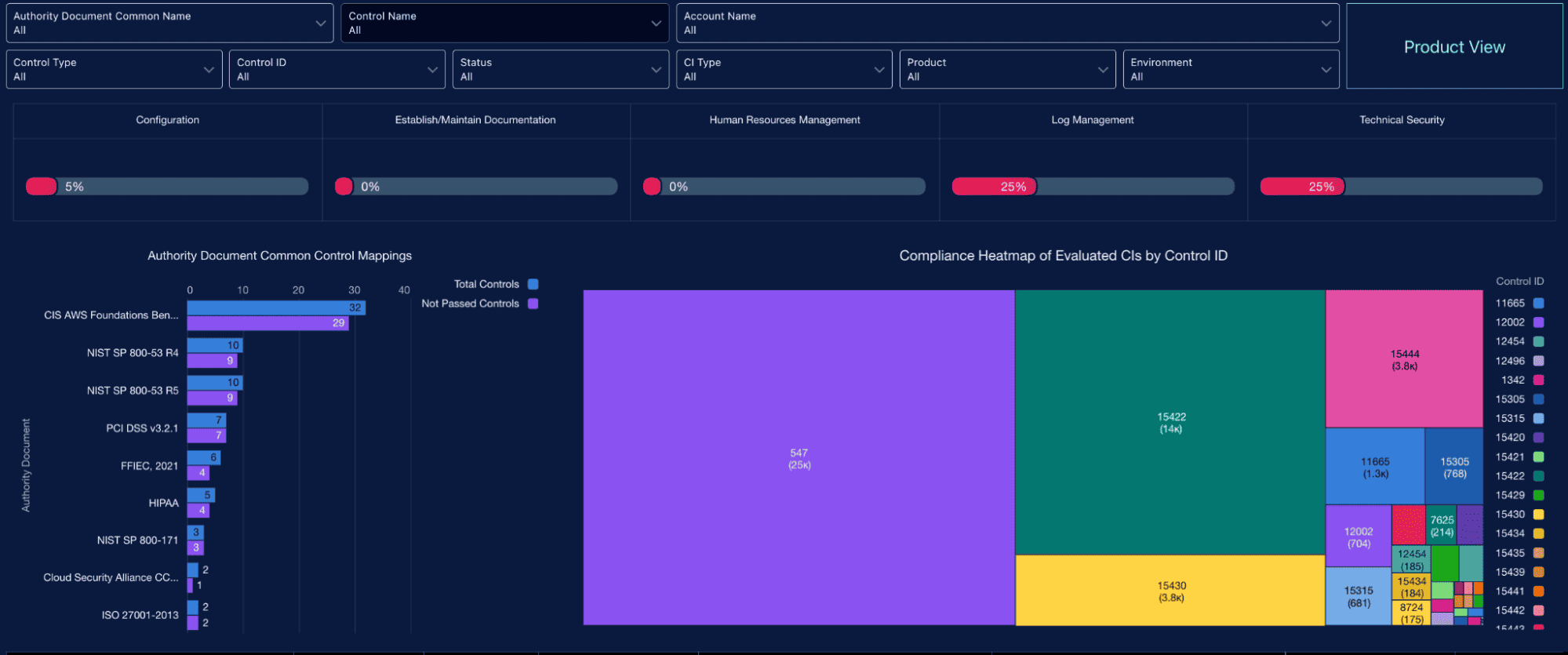
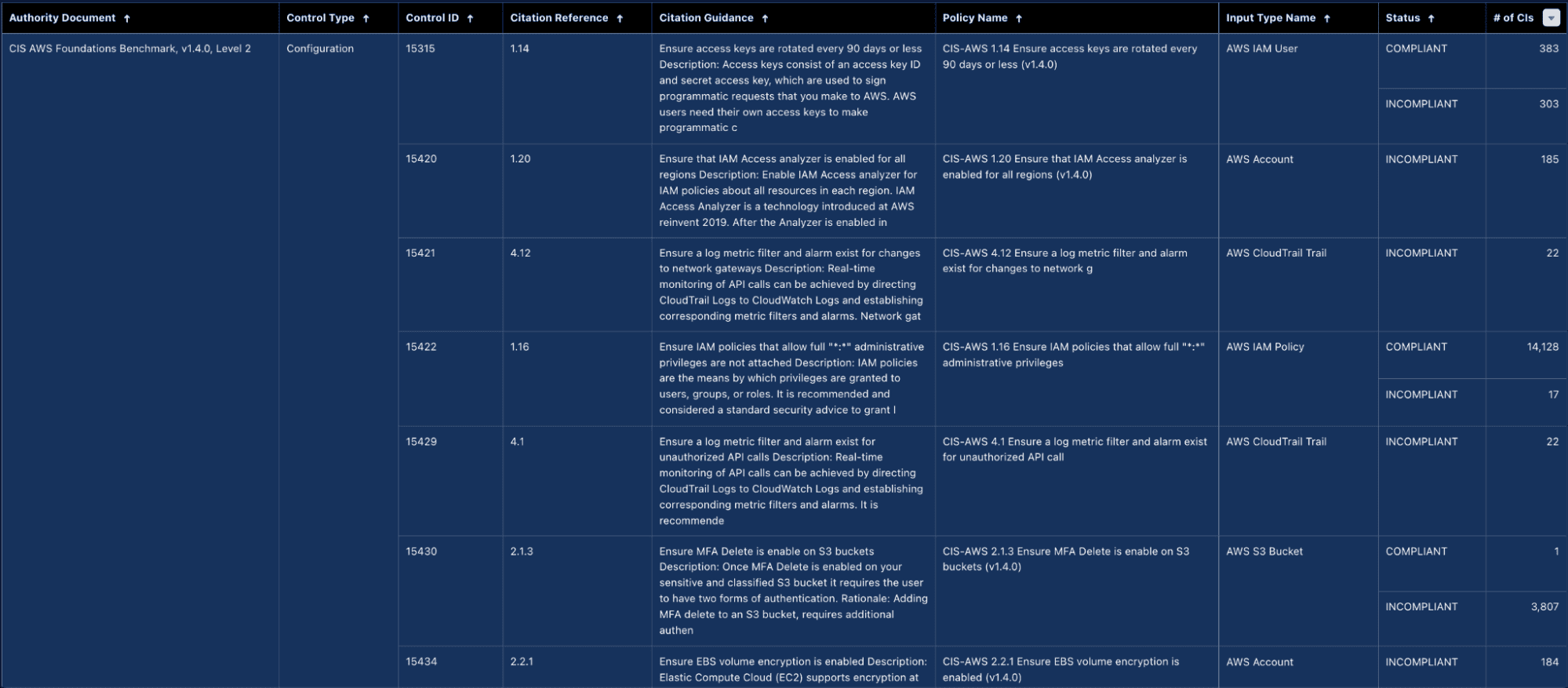
This is how configuration management processes become continuous, auditable, and enforcement-ready.
That’s the config management process, front to back. Not a static list, but a living, breathing feedback loop between your infra, your CI/CD flow, and your team.
So yeah, next time someone says, “We’re good on config,” hit them with a smile and ask: Are you baselining, versioning, and catching drift in real time? Or just running blind and praying nothing breaks?
Top 3 configuration management examples
There are many ways organizations use configuration management in their IT environment. To show how powerful it is, here are three key configuration management examples of its most important functions:
IT Asset Management at Coca Cola
Let me tell you how we helped Coca Cola tame their asset jungle without messing with their pipelines.
They had the usual: AWS, Azure, on-prem, Terraform all over the place, Jenkins in the mix — and tagging? Optional at best. No one knew who owned half the infra. The CMDB couldn’t keep up. Prod incidents meant digging through Slack and guessing who last touched that RDS.
So we flipped on Cloudaware discovery. That pulled in real-time config data from AWS Config, Azure Resource Graph, vCenter, GitHub, Terraform state files — everywhere. Resources turned into versioned CIs with full context, instantly.
Then we cleaned up tagging with custom policies and auto-attribution. We mapped:
- Owners via IAM principals, Git commits, Jira tickets
- Business units via account metadata
- Provisioned-by from Terraform modules
- Environment, app name, region — you name it
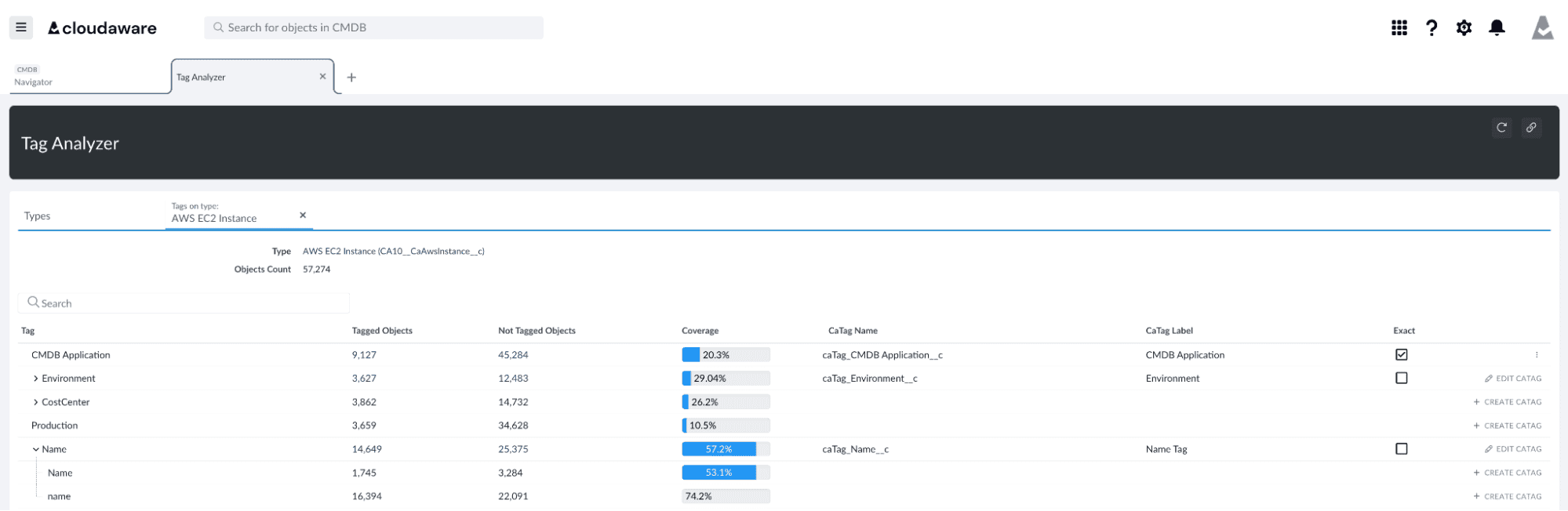
Didn’t matter if it was spun up last week or 14 months ago. We enriched it and made it traceable.
Any asset missing a tag? Auto-flagged. Owner notified in Slack or Jira — no manual review queues. We plugged right into their CI/CD flow, no changes needed.
Now they could:
- Trace every deploy back to source and owner
- Clean up zombie infra by lifecycle and usage
- Map app dependencies in seconds
- Spot drift and enforce tag policies automatically
This was a real-world example of configuration management done right — automated, accurate, and built for how DevOps actually works.
The CMDB finally reflected reality. No more mystery assets. No more “who owns this?” during an outage.
Cloudaware just sat in their workflows, made everything smarter, and let DevOps keep shipping without chaos.
Read also: Key Differences CMDB Vs Asset Management (ITAM): Why You Need Both
Change detection case from Nasa
You ever get that gut feeling something changed in prod — but you’ve got no log, no ticket, no clue who did it? Yeah. That feeling.
That’s exactly what NASA was dealing with. Too many moving parts, too many teams, and no reliable way to track infra changes in real time. It was a perfect storm: cloud-native speed without centralized visibility.
What we gave them was a battle-tested example of configuration management, focused on change detection — the kind that doesn’t just log changes, but actually tells you what matters and who’s behind it.
We deployed Cloudaware Change Detection across their AWS org. Pulled in config state from AWS Config, CloudTrail, GitHub, Terraform state — you know, all the usual suspects. Every configuration item got versioned and tracked automatically. If someone updated a security group or manually pushed a change that didn’t match the Terraform plan, boom — flagged, logged, attributed.
The platform showed:
- Who made the change
- What exactly changed (line-level diffs, not vague summaries)
- When and where it happened
No guesswork, no "he said, she said" on war room calls.
We piped risky changes straight to Slack, kicked off Jira workflows, and fed the whole timeline into their compliance reports and incident response runbooks.
For NASA, this wasn’t just governance — it was control, clarity, and accountability baked right into the CI/CD rhythm.
It’s one of the cleanest, real-world examples of configuration management actually working for DevOps — not against it.
Compliance management: Staying on-top of regulations
You know that feeling when Security pings you for the fifth time asking, “Hey, do we have any public S3 buckets?” and you have to dig through Terraform, AWS Console, and someone’s half-dead Excel tracker?
Yeah — ServiceChannel was living that chaos.
They had teams shipping fast — new infra spinning up in AWS, Azure, GCP like clockwork. But while the code was flying, compliance was kind of… wheezing to keep up.
No one had a clear picture of what was running where, let alone whether it was all playing by the rules.
We plugged into all their cloud accounts, pulled real-time config data straight from AWS Config, Azure Policy, and GCP Security Command Center — and started building a single, clean view of every resource out there. Every resource became a CI, enriched with tags, owners, relationships, and change logs.
Then we brought their SOC 2 controls and CIS Level 1 benchmarks to life with Cloudaware’s policy engine. That gave them real-time eyes on:
- Public access violations
- IAM drift and over-permissioned roles
- Unencrypted storage
- Outdated patch levels
- Deviation from IaC baselines
Violations triggered Slack alerts, spun up Jira tickets auto-assigned to owners, and pushed updates into their SIEM.
Everything rolled up into a live compliance scorecard — one dashboard, real numbers, no panic.
Suddenly, audit readiness went from “give us two weeks” to “give us 15 minutes.”
No more guessing. No more retroactive cleanup. Just compliance embedded in their delivery pipeline, not duct-taped to the side.
And yep — they caught a public S3 bucket before it hit prod. That’s compliance management when it’s done DevOps-style — with Cloudaware running the show.
3 Configuration management lifehacks from the field experts
I know you’ve seen the mess — config drift no one noticed, tags that mean nothing, “who changed this?” becoming a daily ritual. And don’t get me started on the Slack alerts that go nowhere while non-compliant resources party in prod.
So I hit up our ITAM and CMDB crew here at Cloudaware — the folks who live inside Terraform state files, AWS configuration management rules, and multi-account spaghetti — and asked them for their most real-world, battle-tested lifehacks.
Here are three gems they swear by — whether you’re knee-deep in DevOps configuration management, auditing your hardware baseline, or trying to lock down enterprise configuration management across teams.
💡 Lifehack #1: Turn tags into tactical triggers
Iurii Khokhriakov, Technical Account Manager:
“Most teams treat tags like polite labels. But in fast-moving cloud infra, they should be tactical — automated policy levers. We tell teams to bake tagging into their Terraform or CloudFormation modules right from day one. Then, let those tags power real actions.
Want Env:Prod to block open security groups? Done. Need Owner:TeamX to auto-receive Jira tickets when their EC2s miss CIS patching benchmarks? Easy. Want to use DataClass:PII to trigger daily config audits or enable encryption enforcement? Absolutely.
This isn’t about CMDB hygiene — it’s about making your tags act like switches in a control system. The more intentional your tagging taxonomy, the more power you hand to your automation and service configuration management engines.”
💡 Lifehack #2: CI Versioning = Your Infra Time Machine
Kristina S., Senior Technical Account Manager at Cloudaware:
“Your git repo has git log. But your infrastructure? Usually a black box. Until something breaks.
Cloudaware version-controls every CI field — IAM policy changes, subnets, public access, encryption flags, even tagging updates. That means when Security drops the classic ‘who disabled encryption on this S3 bucket,’ you’ve got the answer: who did it, when, what changed, and how it impacted related items.
It’s not just about point-in-time views. It’s about full-blown forensic visibility, cross-account and cross-cloud. We’ve had teams use it to prove their environments were compliant before a CVE dropped, or to rewind and validate Terraform drift without re-running plans.
Whether you're auditing database configuration management or responding to a zero-day across hybrid workloads, this level of traceability is your safety net.
If your infra can change at the speed of a PR merge, you need the ability to roll back visibility just as fast.”
💡 Lifehack #3: Quarantine Non-Compliant CIs Before They Hurt You
Mikhail Malamud, Cloudaware GM:
“Security alerts without action are noise. So one of the most impactful patterns we’ve helped teams build is auto-quarantine.
When Cloudaware detects a critical compliance fail — like a public RDS instance, overly permissive IAM role, or disabled encryption — we trigger a Lambda that locks it down immediately. The CI gets tagged Quarantine:True, networking rules are restricted, and the owner is auto-notified with a link to the policy violation and remediation guide.
No bottlenecks, no ambiguity, no waiting on approvals. It’s not just enforcement — it’s resilience baked into the workflow.
Bonus tip: connect those auto-quarantine flows to your change management logs, so every action is audit-ready and traceable across systems. From AWS configuration management policies to your internal hardware configuration management records, full alignment makes life easier across teams.
Your SecOps team will love you for it.”
Achieve 100% visibility with Cloudaware configuration management system
here’s the truth bomb no one says out loud — most CMDBs are either too slow, too shallow, or way too focused on pretty diagrams no one actually uses. You know what I’m talking about: tools that say they do configuration management, but crumble the second you scale across clouds or ask them to handle actual DevOps velocity.
That’s why I swear by Cloudaware.
It’s the only configuration management system I’ve used that doesn’t just keep up with enterprise-scale environments — it actually makes them manageable. Cloudaware turns messy, fast-changing infrastructure into structured, contextual, audit-ready Configuration Items you can trust.
And it’s not just some glorified asset tracker — it’s a full-blown CMDB platform designed for the way modern teams build, ship, and secure cloud-native systems. Even better, it plays beautifully with your performance and configuration management workflows — so your visibility isn’t just accurate, it’s operationally useful.
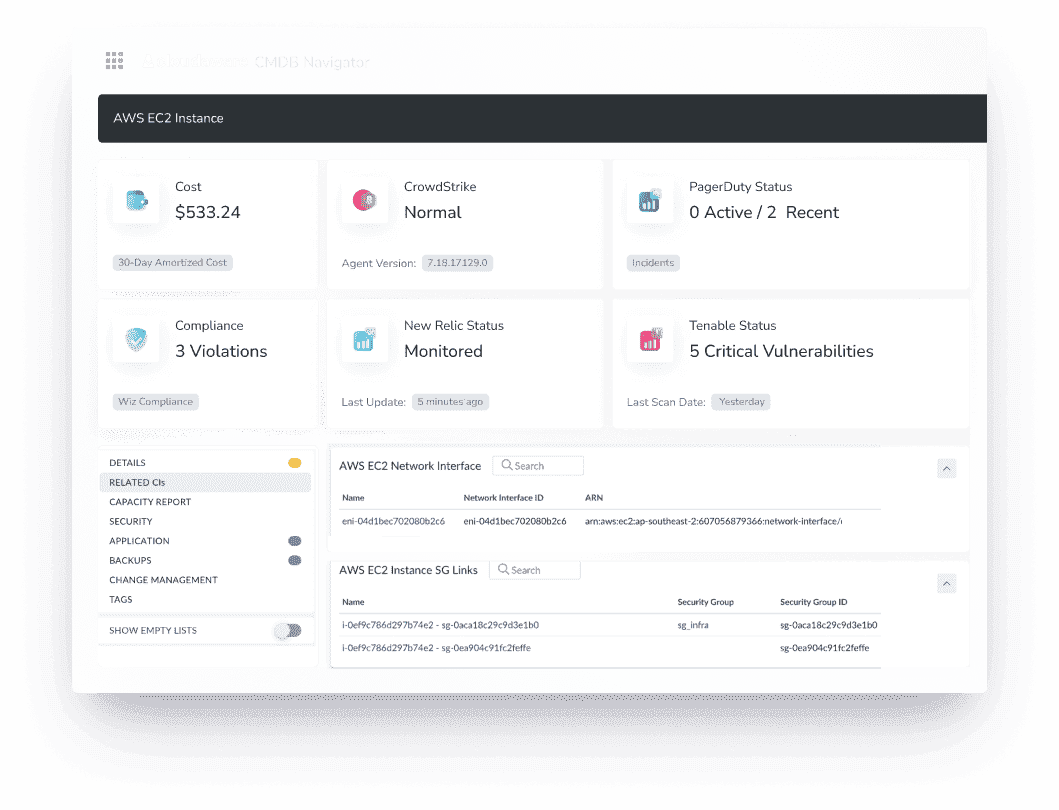
What makes it different?
- Multi-cloud & hybrid native. Pulls config data from AWS, Azure, GCP, on-prem, and SaaS — all normalized into unified CIs.
- Automated CI discovery & relationship mapping. No manual linking. Automated configuration management detects dependencies, ownership, and change history across environments.
- Policy engine for real-time compliance. Define CIS, SOC 2, internal rules — and enforce them with alerts, tickets, or automated remediation.
- Version control on every config field. Roll back or investigate changes like you would in git. Full historical diff on every CI.
- Security, cost, and operational context in one place. View tagging, ownership, IAM posture, and cost attribution right inside each CI.
- Integrates with your stack. Hooks into Jira, Slack, GitHub, ServiceNow, Terraform, and your CI/CD toolchain.
You want visibility that goes beyond static spreadsheets. You want config data that’s alive, actionable, and baked into your delivery pipeline.
That’s Cloudaware.
